Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.
Trusted by security leaders to secure their cloud
Sonrai allows us to track where every identity may be overused or over-exercised within our environment, and that allows us to develop from the beginning a secure environment.

Shawn Bowne
VP & Chief Information Security Officer
World Kinect Services
Sonrai is one of the leaders in this space, both from a product maturity perspective, and the thought leadership.
Source: Gartner Peer Reviews


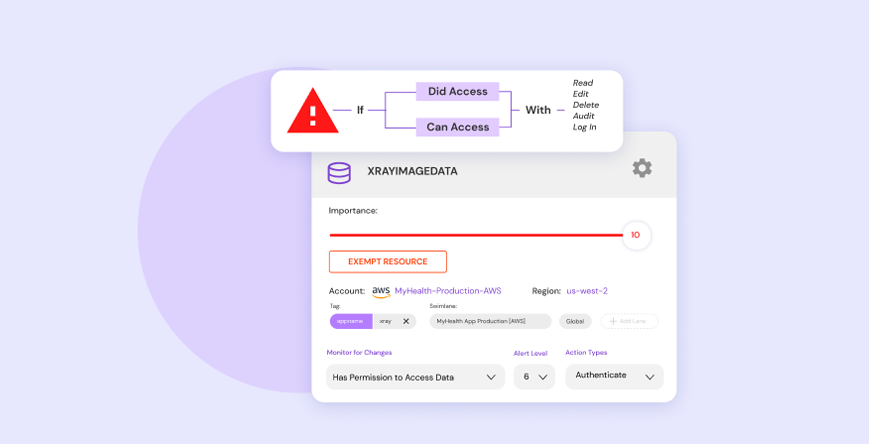
Sonrai Security provides us with complete visibility of platform, identity, and data risks across our largest AWS and Azure cloud infrastructure The platform has become the cornerstone of our cloud risk management and security program.

Kyle Watson
Security Architect
RMS
See Sonrai Security in Action
Watch a recorded demo or get a personalized demo to see how Sonrai Security can secure identities and entitlements across your entire public cloud, including Amazon Web Services (AWS), Azure, GCP and OCI.