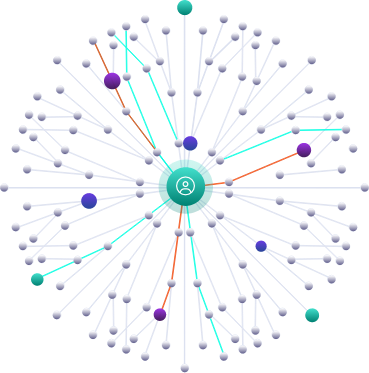
Cloud Identity Graph & Analytics
Get the only patented effective permissions engine working for you.
The cloud is a complex structure of interlocking permissions.
Understanding what identities have potential access to what data requires big data analytics that can unearth the paths leading to and exposing sensitive data.