Sonrai Dig
For AWS Cloud Security
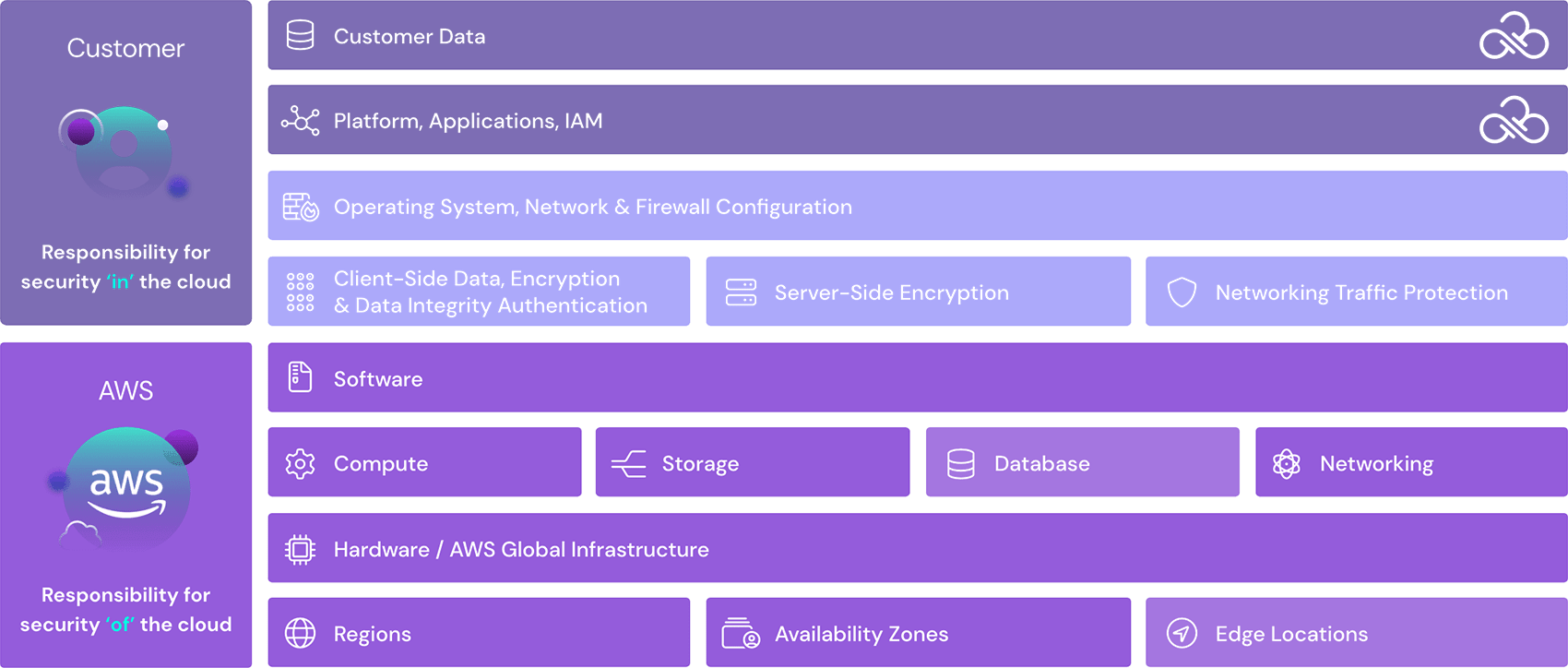
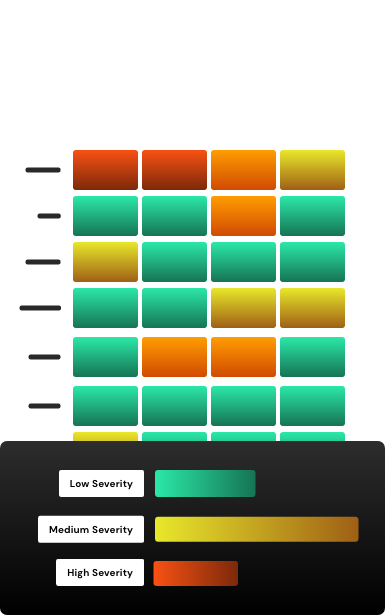
Provide Deep Visibility (CSPM), Eliminate Identity Risks and Strengthen Data Protection for your AWS Workloads – Operationalize your Cloud Security Model.
Learn how World Fuel Services securely accelerated their cloud migration with Sonrai ➡
Shawn Bowen, VP and Chief Information Security Officer
World Fuel Services Corporation