Table of Contents

Share this entry

So you just bought or renewed with Wiz – well done on kicking off your cloud security journey.
Cloud security is a multi-pronged program, requiring protection across workloads, platform configurations, cloud identities, and data and applications.
Wiz brings an agentless scanning-based workload protection approach to cloud security with CSPM-like configuration checks and inventorying – but what about securing identity and data?
Is Identity and Access Really Worth Prioritizing?
Let’s consider some hard data from recent research reports and what the implications mean.
- IBM’s X-Force Cloud Threat Landscape 2022 report cited overprivileged cloud identities in 99% of the breach incidents they studied.
- Credentials are used as an attack vector in about ⅓ of cloud security incidents in 2023 according to IBM X-Force.
- 99% of the organizations who experienced a security breach recognized identity credentials played a role in the breach in research conducted by The Enterprise Strategy Group.
Clearly, identity and entitlements are an undeniable vector in cloud breaches and attacks.
- In the same study from ESG, 73% of participants reported that overly permissive machine identities introduce security and compliance risks and 40% of respondents failed a compliance audit due to cloud entitlements with unmanaged, unneeded access permissions.
The risks of improper cloud identity management is failing audits (read: strain on your company’s resources and time) and noncompliance (read: hefty monetary penalties.)
- 68% of the respondents in the ESG study reported robust CSPM capabilities, yet the majority still faced security incidents, often involving identity and access issues.
- Finally, according to a Forrester Consulting snapshot study, the average enterprise hosted six different security tools, yet 99% still faced cloud security incidents.
We’re left to deduce that first-generation cloud tooling – CSPM, vulnerability management tools, cloud-native tools, etc. are not working.
There is no time to waste when it comes to prioritizing a proper cloud identity and access management program. This is your company’s data protection integrity, business continuity, and monetary resources on the line. If you’re responsible for cloud security, then focusing on identity is the best way to be good at your job and protect your business.

So why is Wiz not enough for identity security?
Wiz offers least privilege through their entitlement usage monitoring and auto-generated least privilege policies.
Enforcing least privilege is a foundational step, but you’re not done yet. Least privilege only considers the past – who should have access based on historical activity. But, cloud security is about more than just the past – it is about protecting the future.
It is not about who should and shouldn’t have access on paper, but who actually presently does. There’s often a gap in what teams think is in their cloud or who holds access vs. the actual reality of access due to complex permission hierarchies. It’s this gap that leaves you vulnerable and an attacker will capitalize on to execute their attack.
Here’s what we mean by ‘complex permission hierarchies’ and what makes cloud entitlement management and securing access so hard in the cloud:
- Not all permissions are directly assigned to an identity. They can be indirectly inherited or acquired through many hops along an identity-chain. Trust relationships, conditional access rights, compounding group policies and more give identities privilege you never intended for them to have.
- Permissions are not just granted at the identity level. Instead, there’s a hierarchy of places where permissions are assigned. You’re dealing with permissions at the organizational level like guardrails and SCPs, permissions at the resource-based level like an S3 bucket policy, identity-based permissions – and of course, what a permission actually translates into at the action-level (i.e. configure, edit, delete, etc.)
Consider the visual below. Let’s say you’ve got a serverless function that is totally locked down at least privilege – they’re only directly assigned what they need. A tool like Wiz, with least privilege technologies, can see that the serverless function has a permission attached to it – sts:assumerole.
This allows the function to assume several other roles that we can see on the right side of the graph below. Where Wiz’s insight cuts off is seeing what the serverless function could do once they use the sts:assumerole permission to assume the various roles on the right.
Each of the permissions on the right side are harmless on their own, but when combined together they create critically dangerous power – the ability to create a new function, pass a role to it, and invoke it (essentially they can execute whatever they want in your cloud.)
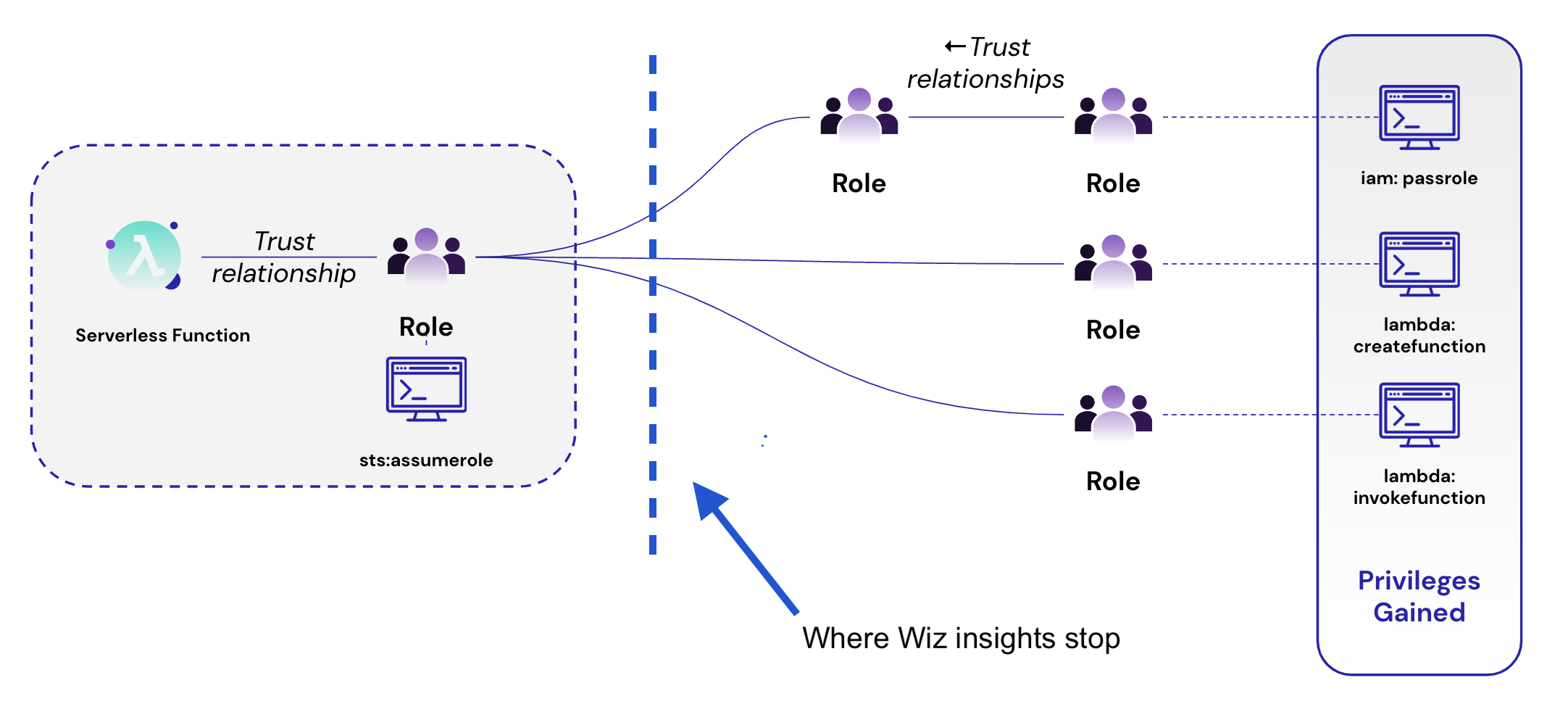
BONUS: Notice how the trust relationship actually moves backwards on top. Sonrai is actually able to not just start from the view of an identity to see its entitlements, but start at the permission itself, and work outwards to analyze who can access it. This is true effective permissions. No one else can do this. How? With our Toxic Permissions Analyzer.
The big takeaway is – you need to see what is possible in the future. What privilege can an identity access that isn’t directly assigned? What could they do tomorrow? How can an attacker hop from one identity to the next to gather a toxic combination of permissions that allows admin-level privilege? What permission-chains lead a piece of compute in Dev to end up with sensitive data in Prod? You need the answers.
Wiz is not built to answer these complex cloud entitlement and access questions. However, they’ve got your platform checks and your workloads covered.
So What Should You Do?
If you’ve made it this far, hopefully some of this has resonated or gotten your attention. And it’s worth your attention. Protecting an environment barrier has long been the primary security focus – that is, network controls and vulnerability patching. We’re still seeing remnants of this paradigm even with the shift to the public cloud – this is what we’re poking at. This is what must change.
No matter how advanced your CSPM or CWPP solution is (yes, even as good as Wiz!) attackers will find a way into your environment. CSPM and CWPP do very little for you once your ‘perimeter’ is breached. Instead, proper management of identities and their permissions, will. Bad actors navigate your cloud by hopping from one identity to the next in search of the golden permission that gives them what they want. That golden ticket is often a combination of permissions or an attack path your teams didn’t know existed or never intended for.
What can you do?
Get a true Cloud Infrastructure Entitlement Management (CIEM) tool. You can see what Sonrai’s CIEM solution looks like here and why we think you need one.
If you’re curious in learning why we’re a different solution than Wiz, you can read how the two tools compare.




