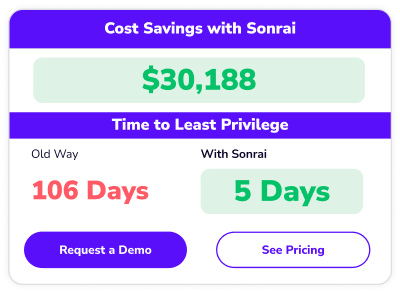
We believe gaining control of access in your cloud is possible. By focusing on the most critical permissions and automating policy management, you can achieve security at scale. Controlling cloud access is complicated, time-consuming, and easy to cause friction with DevOps. So we built a solution to fix that.
No Dev Friction
Everything being used is allowed.
No WASTED TIME
Global policies written for you.
No ALERTS
Less monitoring and more action.
No LATERAL MOVEMENT
Attack paths to data are broken.