One-Click Least Privilege. Zero Disruption.
Automate and Simplify Cloud Privilege Management
Automate centralized global policies like AWS Service Control Policies (SCPs) to accelerate least privilege management across your cloud. Continuously analyze cloud activity and instantly restrict unused privileges, identities, third-party access, regions, and services to reduce risk without disrupting workflows. Privileges remain intact and ready for reactivation through an automated ChatOps request, approval, and policy update workflow—granting access in minutes and ensuring seamless operations and flexibility.
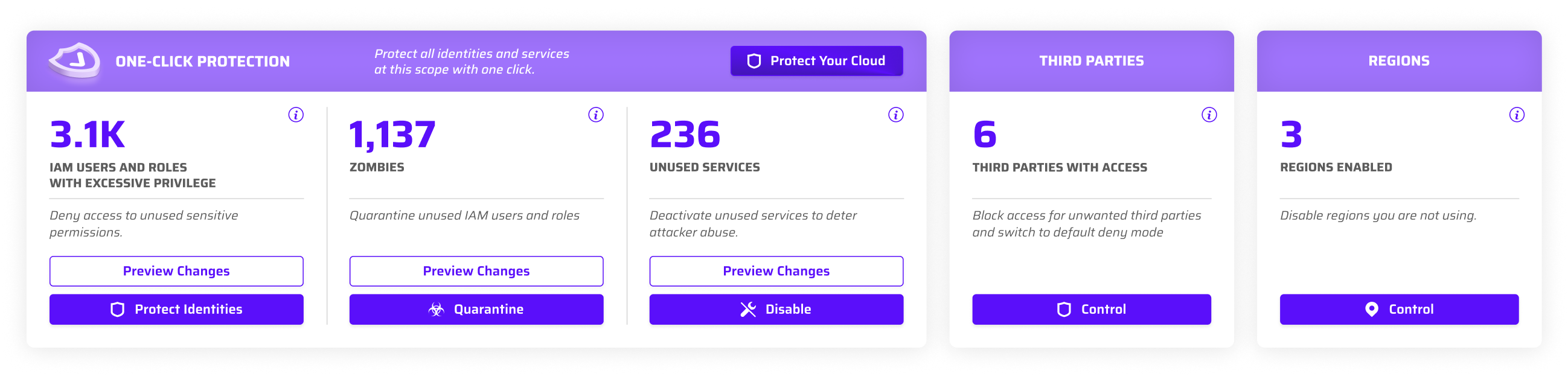
Restrict Unused Privileged Permissions
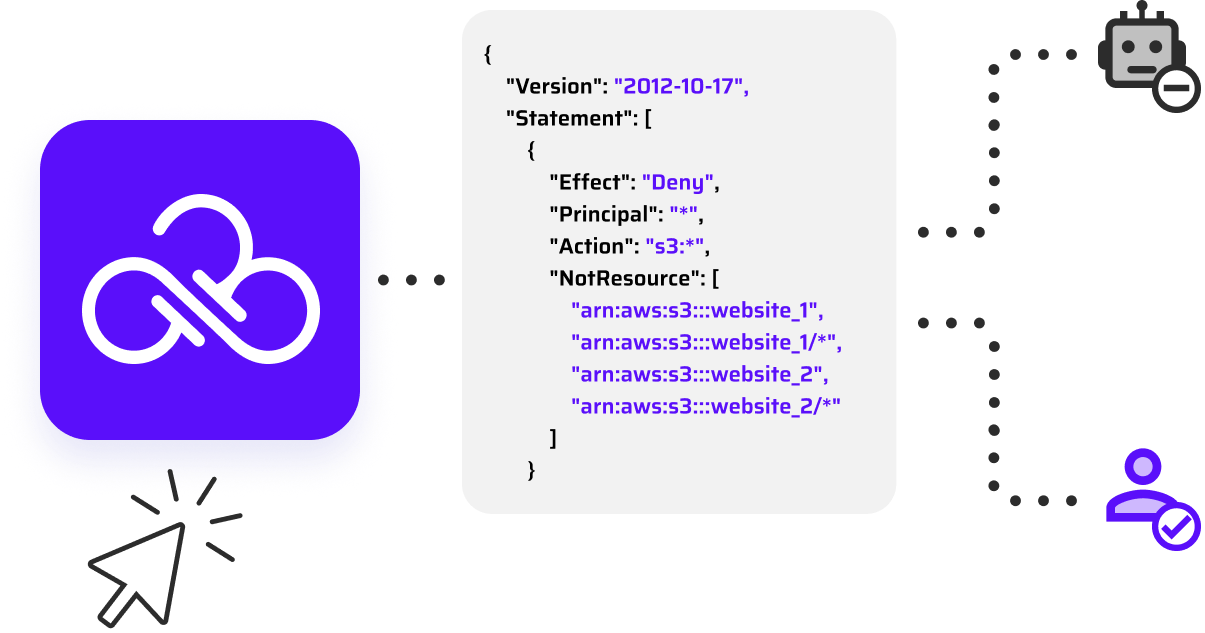
Identify which identities aren’t using privileged, high-risk permissions and automatically generate SCPs to restrict access. Identities actively using these privileges are automatically exempted to maintain essential operations. Need a restricted privilege? An automated ChatOps workflow manages the request, approval, and policy update, granting access in minutes. Effortlessly control large volumes of unused privileged permissions without the burden of manual policy writing.
Quarantine
Unused Identities
Safely quarantine unused identities by automatically restricting all permissions with an SCP while keeping their permissions intact. Reactivate these harmless ‘zombie’ identities in minutes through an automated ChatOps approval and policy update when needed. No more fear of deleting identities —deactivate them without the risk of future disruptions.
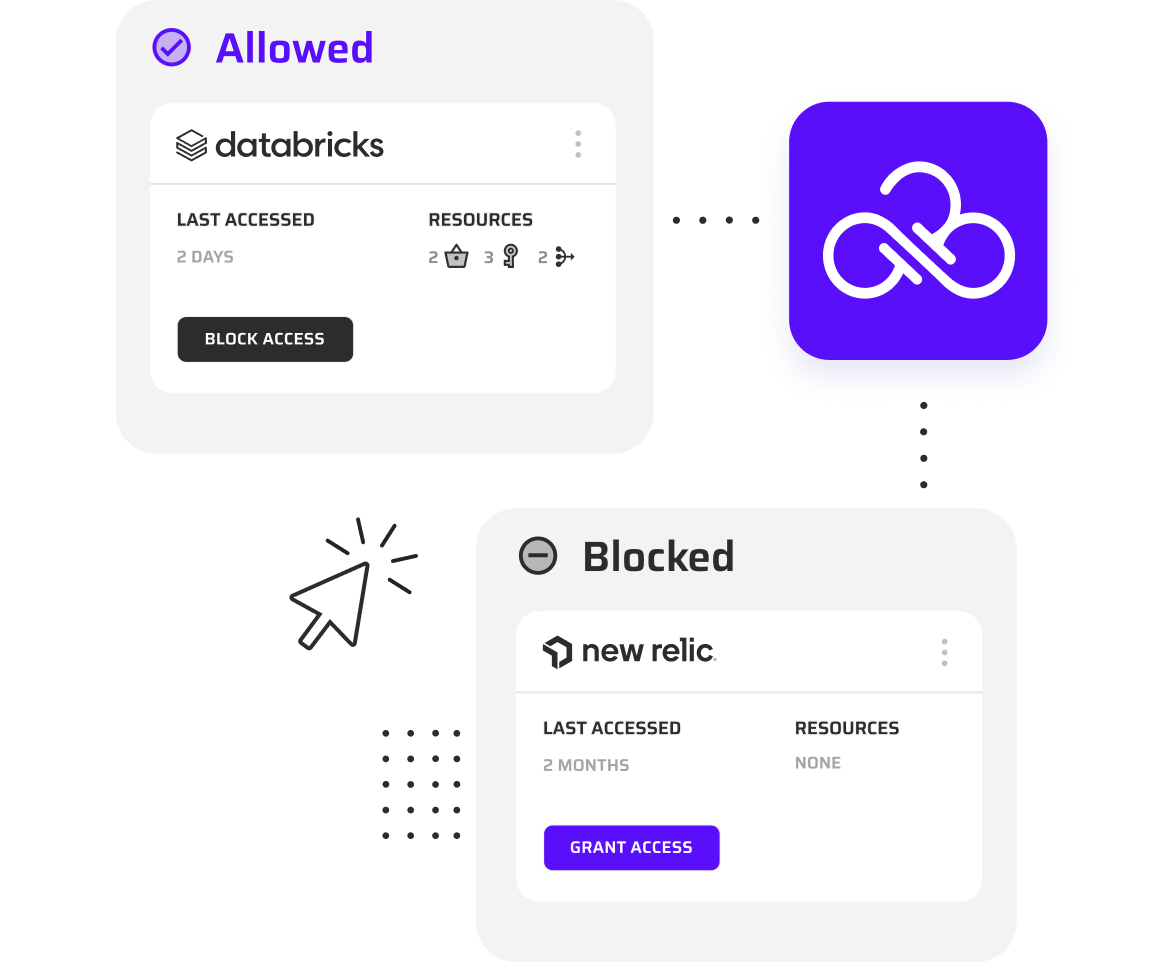
Take Charge of
Third-Party Access
Identify and block third-party access to any org, OU, or account with automated AWS-native Resource Control Policies (RCPs) deployed via CloudFormation. Maintain centralized visibility and one-click control, whether third parties access your cloud through roles or resource policies. Set a default deny state to automatically block future access, with approvals and policy updates handled in minutes through an automated ChatOps workflow.
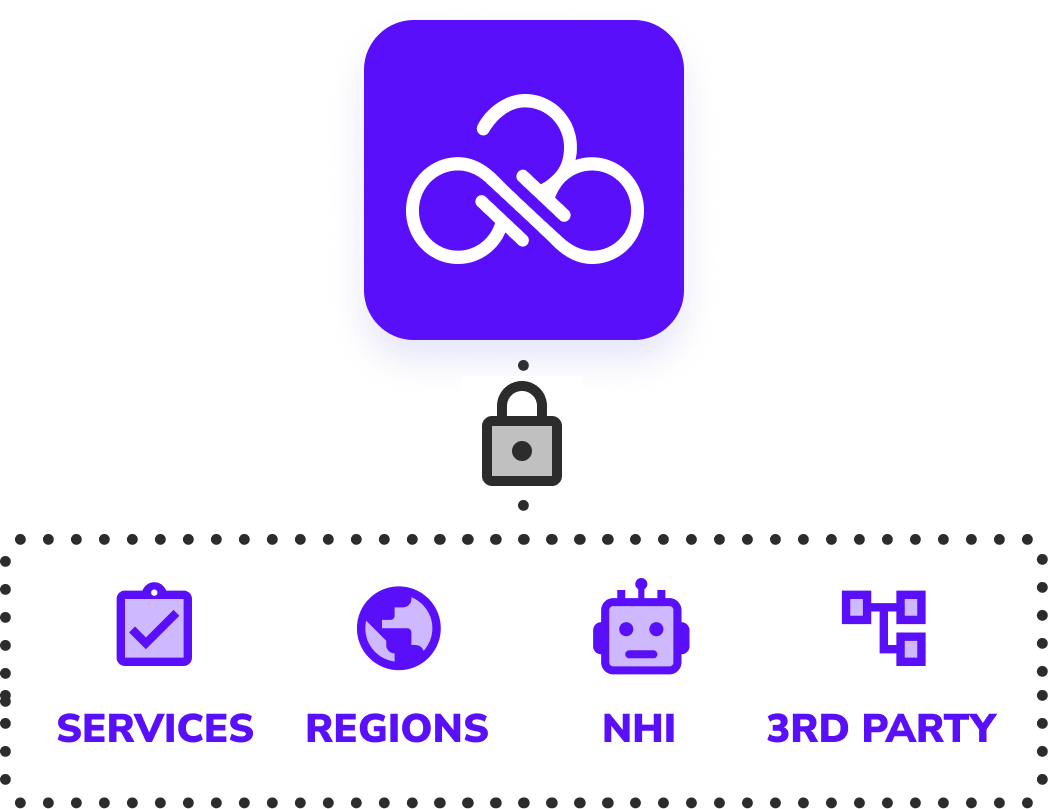
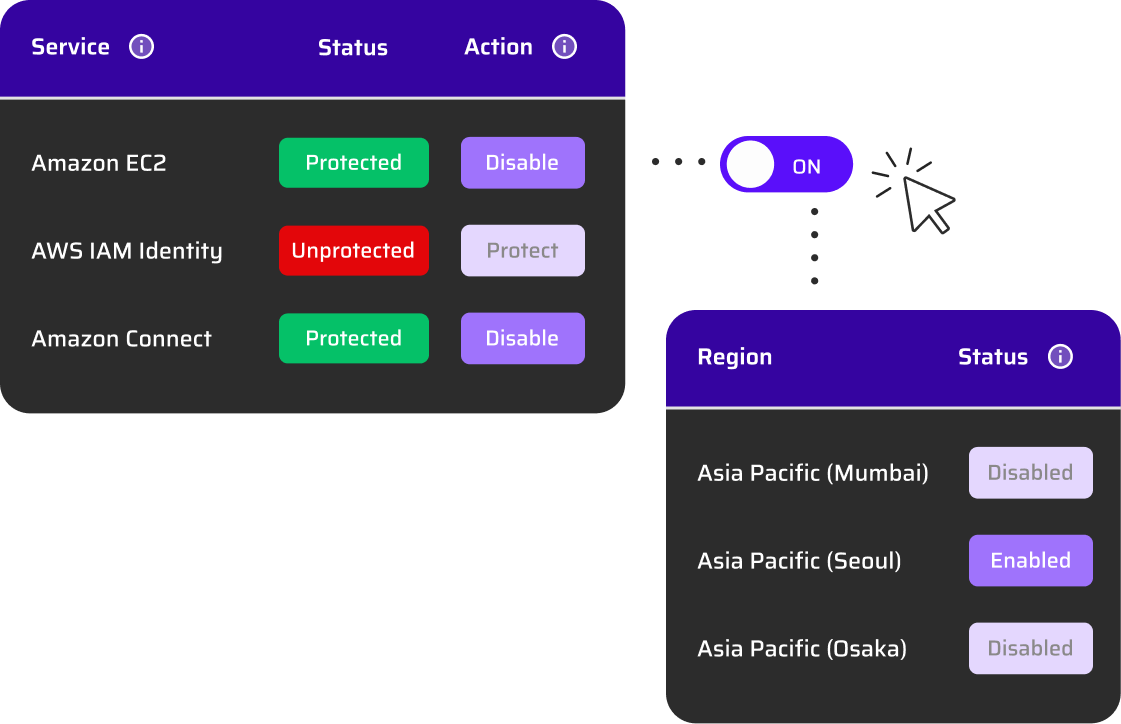
Remove Access to Unused Services and Regions
Block unused or unwanted services and regions in your AWS environment with automated centralized policies based on usage analytics. Reactivate any service or region with a simple click in the UI, instantly updating the policy. Users can request access via ChatOps, streamlining approvals and policy updates. Further control risk by enabling services while restricting access to the privileged permissions. This proactive approach safeguards against data sovereignty risks and surprise costs, keeping your cloud secure and efficient.
Seamless Action Without Breaking Anything
When a human or non-human identity needs access to a restricted permission, service, or region, Privilege-on-Demand steps in. The automated ChatOps workflow notifies the owner, routes the request to the approver, and updates policies once approved—granting access in minutes. Choose permanent or time-limited access, with instant notifications to keep everything running smoothly. Take full control of excessive privileges without worrying about breaking workloads.
What Our Customers Have to Say
Don’t take our word for it. Here’s what our customers say.


Cole Horsman
AVP, Security Operations“Sonrai helped us do in days what would’ve taken months—automating identity management and achieving least privilege across AWS.”


Preetam Sirur
Chief InformationSecurity Officer
“The challenge with deleting unused identities or enforcing least privilege is that we know it’s the ‘right’ thing to do, but everyone’s afraid it’ll break something or interrupt our development cycles. We don’t have to worry anymore.”


Brendan Putek
Director of DevOps“Within five minutes I had disabled regions that were unused across my entire AWS organization.”


Kenneth Milcetich
Director of Cyber and InfoSec“Sonrai not only identified the over permissive actions granted to our identities, but also provides a least effective access policy based on the identities usage...All of this boils down to a significant increase in our cloud security posture.”


Josh McLean
Chief Information Officer“Our transition from tedious, weeks-long tasks to accomplishing Least Privilege outcomes in just a few days has been remarkable. This approach has saved us a tremendous amount of time while also guaranteeing the security of all critical permissions.”


Chad Lorenc
Security Delivery Manager“Sonrai is one of the top tools to quickly scale when you're trying to do privileged management in the cloud.”

See the Cloud Permissions Firewall
in Action
Start a 14-day free trial and see results in two hours. No agents or workloads necessary. If you’re not ready, start with a demo from our experts.