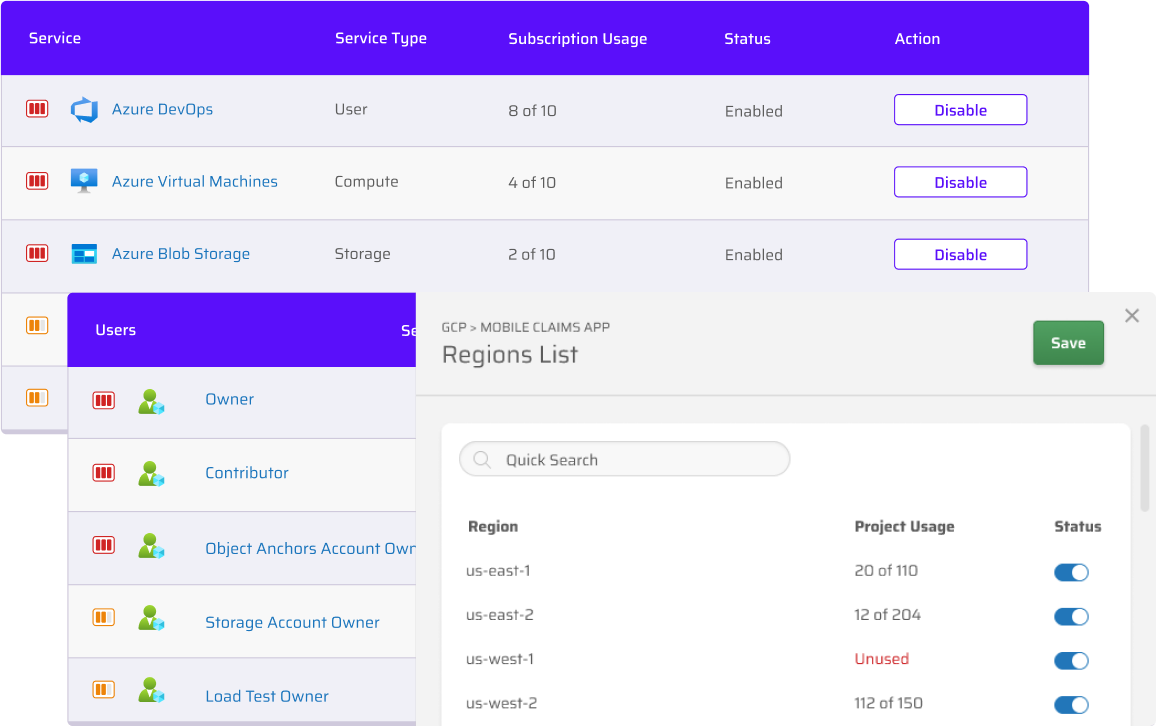
Securely remove unnecessary access and privilege for human and machine identities, while seamlessly approving temporary or long-term access as needed.
Grant Access Easily When Needed
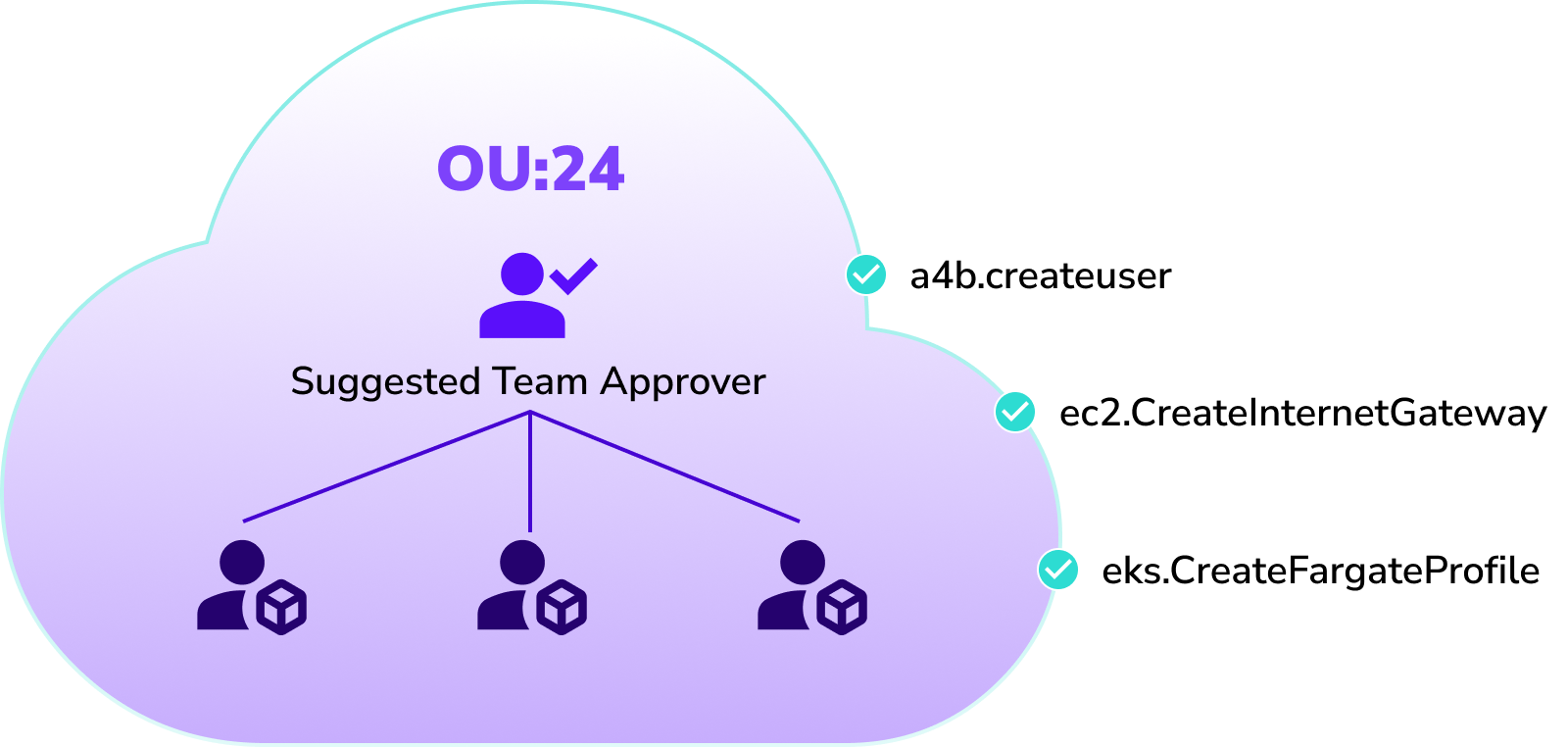
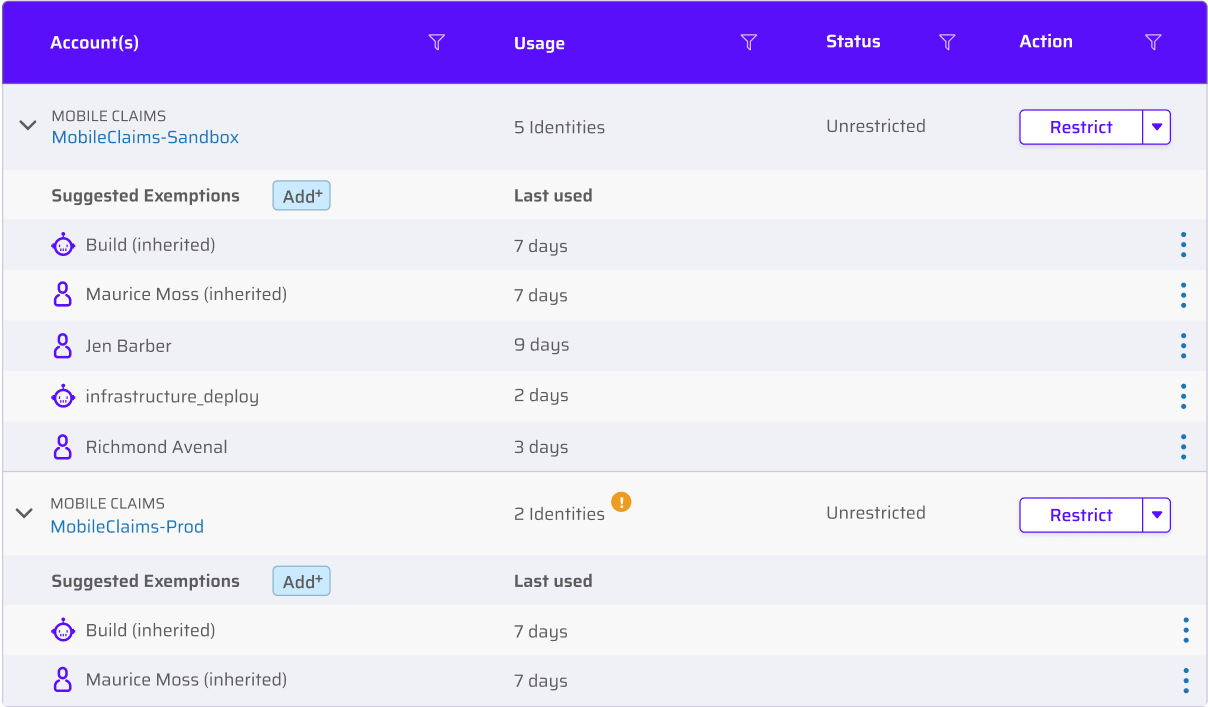
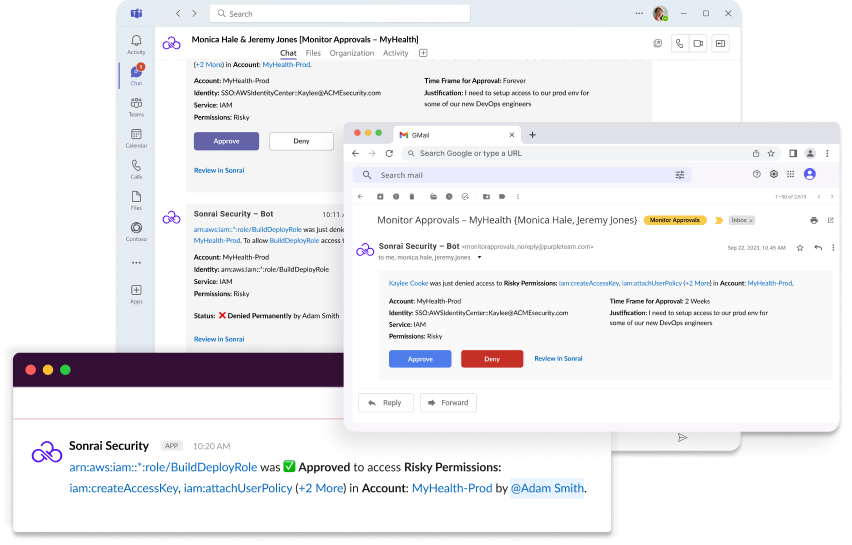
When an identity needs access to sensitive permissions that have been restricted for protection, grant them back with an easy workflow using your ChatOps tool of choice. An attempted use automatically kicks off a request workflow sent to a relevant approver so you have full control over who gets sensitive permissions and for how long.
The Cloud Permissions Firewall gives you all the control you need with the access your identities want.
Know Who, What, and When for Auditing
Track exactly which identity was granted privileged access, when, and by whom to meet all of your audit and compliance needs. Whether you view pre-built dashboards or integrate with a monitoring tool you already use, the Cloud Permissions Firewall gives you what you need to answer to stakeholders and auditors.
It’s Time to See Cloud Privileged Access Management
Get a personalized demo or start a free trial to see how the Cloud Permissions Firewall can secure privileged identities in your cloud.