Table of Contents
Share this entry

Dear Community,
The inspiration behind our groundbreaking solution, the Sonrai Cloud Permissions Firewall, stemmed from a critical gap in the market: managing cloud permissions had become a Herculean task, bogged down with complexity and risk — and no cloud security vendor has truly solved this problem.
The Genesis of an Idea
Our journey began with a simple observation: the powerful identity access and permissions systems, the backbone of cloud and microservices applications, were being mismanaged – not to the fault of any organization. In fact, most companies we see are trying to do the right thing, but they have not been given a tool that provides results without creating more work for them. Native-cloud tooling and even more advanced IAM cloud security solutions are not working. The mountains of alerts visibility tools offer are overwhelming DevOps teams and take too long to produce actionable results. The risks remain.
However, the implications of not solving this problem are far too serious to ignore.
Here, we introduce a solution that moves beyond passive analysis. Our Cloud Permissions Firewall is action-oriented, designed not just to offer insights but to provide actionable security controls that will instantly reduce the cloud permissions attack surface.
A Focused Solution for a Pressing Problem
While the market welcomes broad security tools that with one deployment will promise data, identity, workload and network controls, we recognized the need for a specialized, best-of-breed tool focused solely on addressing access controls. The Cloud Permissions Firewall is our answer to this specific challenge, highlighting our belief that this permissions and access challenge is significant enough to warrant its own ground-breaking tool.

A New Approach to Least Privilege
With over 40,000 permissions across clouds, the sheer volume makes it virtually impossible to effectively enforce least privilege and reduce attack surface. We must acknowledge that securing this mountain of permissions is an unsustainable goal. Our approach to least privilege focuses on the most sensitive permissions, ensuring your teams spend time protecting what is most impactful. What was previously a never-ending security and operational challenge can now be done in a matter of days.

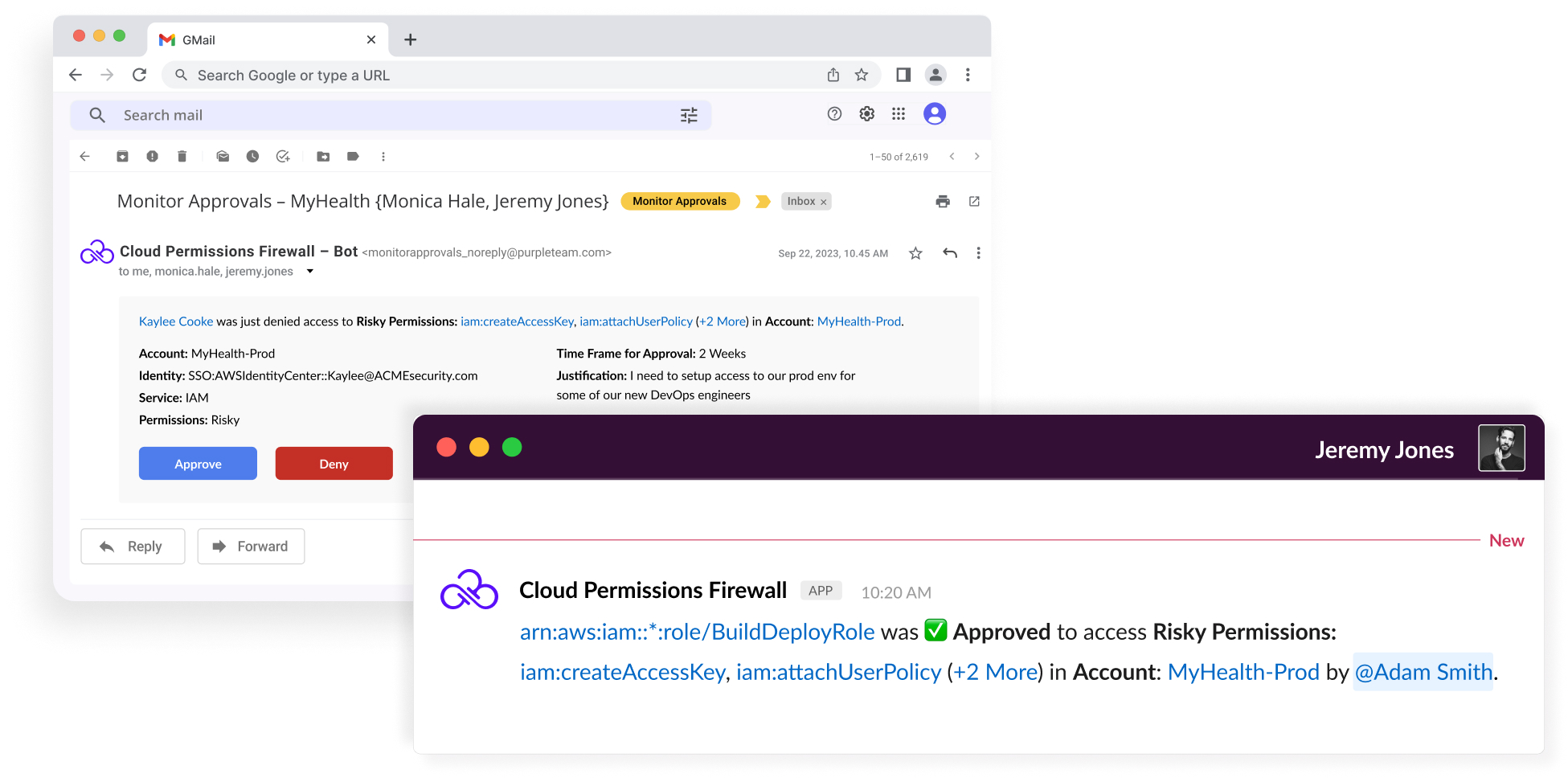
Instant Least Privilege, Zero Disruption
What sets the Cloud Permissions Firewall apart is its ability to instantly eliminate unused access to services, regions, identities, and sensitive permissions without disrupting ongoing operations. This protection comes with confidence – once our one-click solution is deployed, you know your attack surface is reduced and that nothing your identities need is taken away. Any future access needs are seamlessly granted with a Permissions-on-Demand workflow integrated into any preferred ChatOps tool.
Envisioning the Future
This solution is for every organization that seeks to bolster its cloud security posture while maintaining the agility and innovation that cloud computing promises. We believe that the Cloud Permissions Firewall will not only transform how companies manage cloud security today, but will also shape the future of cloud identity management.
To our customers and the broader cloud community, the Cloud Permissions Firewall is more than a product—it’s a commitment to security, simplicity, and innovation. We have worked alongside many dedicated customers for years and seen the trials and errors and challenges associated with securing access. It’s been too complicated, too laborious, and too slow. This product is our answer.
It is now possible to significantly reduce your IAM risk, at an extremely low cost, and regain confidence in your understanding of what is happening underneath the covers of your cloud.
Sonrai Security
P.S. Questioning whether this is truly a ‘Firewall’? Come ask us about it.



