Table of Contents

Share this entry

While exploiting identities and privilege isn’t always the way into an enterprise cloud, it is always involved in malicious data access or a cloud takeover. Imagine enterprise clouds as complex webs, with identities and permissions as the strings tying workloads, services, resources, datastores, and even different accounts and clouds together. These connections help cloud applications operate efficiently, but they also – if unmanaged – offer intruders pathways to access the most critical assets or privileges to a business.
Once an attacker is in your environment, proper identity and entitlement management is the only way to drive attackers to a dead end – with no lateral moves to make. Network controls, platform configurations, and vulnerability patching is no help once the ‘barrier’ is breached.
Enterprise organizations that rely on the cloud must focus on securing identities, access and permissions if they are serious about protecting sensitive data, maintaining business operations, and avoiding damaging compliance violations.
We recognized this critical security requirement in the cloud, so we built a permissions analytics engine more advanced than any other seen in the market today. It’s Sonrai’s Toxic Permissions Analyzer.
What Does Sonrai’s Toxic Permissions Analyzer Do?
Toxic Permissions Analyzer breaks the cloud attack chain, honing in on the Privilege Escalation, Lateral Movement & Exfiltration stages.
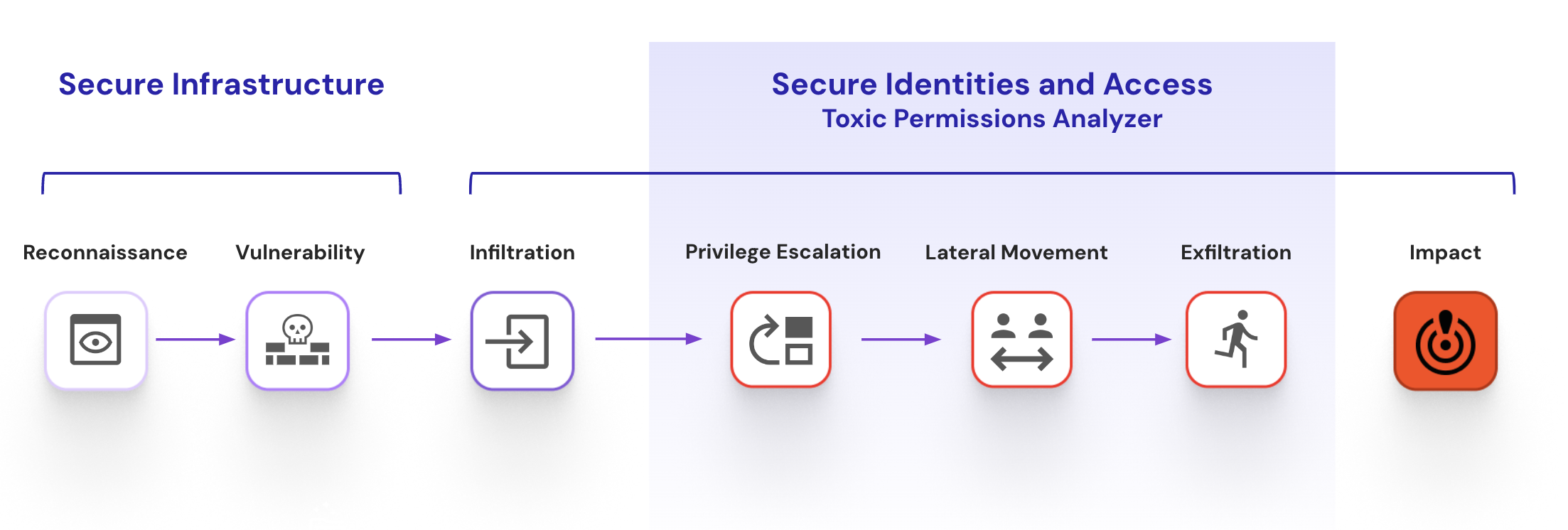
It discovers hidden attack paths by discovering the cloud relationships causing opportunities for privilege escalation, lateral movement, and inadvertent data access. These opportunities are the result of the complexity of privilege policies. Trust relationships, grouping mechanisms, and other indirect means lead to identities having abilities never directly assigned to them. Toxic Permissions Analyzer finds those high-risk permissions so your teams can remediate them to break attack paths.
Exfiltrating data and accessing business critical applications isn’t always the end-game for attackers. Sometimes, it’s just an accumulation of the right privileges – this is called privilege gathering. Privilege gathering refers to an attacker moving laterally through your environment, sourcing the right identities and permissions (that are seemingly unconnected) to create a toxic combination that allows them enough power to execute whatever desired outcome. Privilege gathering leads to the potential for cloudjacking, code injection, ransom-style demands or anything the attacker wants (with the right toxic combination to exploit.)
Keep reading for real-world use case examples.
Toxic Permissions Analyzer uses Effective Permissions technology to discover all net privileges any and every identity (human and machine) holds and the Sonrai patented identity graph to map it all together and discover where identities can gather enough privilege to cause harm.
How Does it Work?
The key to Toxic Permissions Analyzer is Sonrai’s ability to analyze the full stack of the cloud permissions hierarchy.
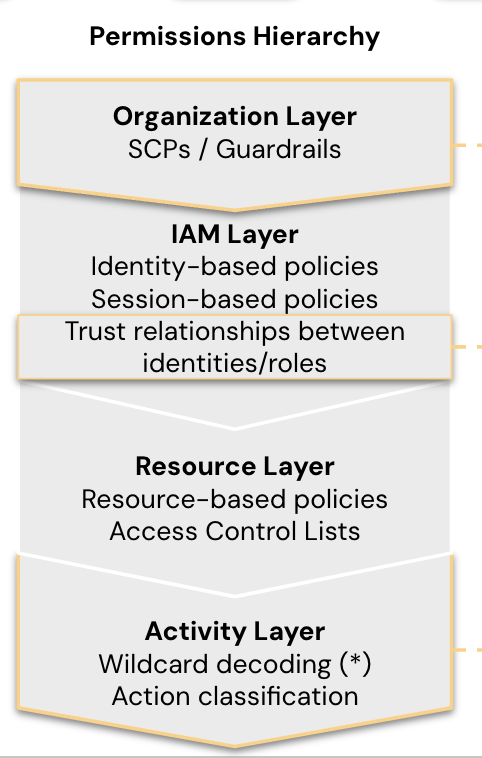
Permissions and privilege are not only directly attached to identities. In fact, the full hierarchy includes privilege provisioned at the organizational level, like Service Control Policies (SCPs) or Guardrails; the Identity level, your standard permissions or group policies; the resource level for resource-based policies or Access Control Lists (ACLs); and finally, the action level, this refers to the individual actions permissions translate into, i.e. ‘read’, ‘copy’, or ‘delete’ – and there’s 42,000+ across the major cloud providers.
Evaluating all policy types to determine which identities have access to what is a daunting task. AWS describes the process in their documentation using this diagram:
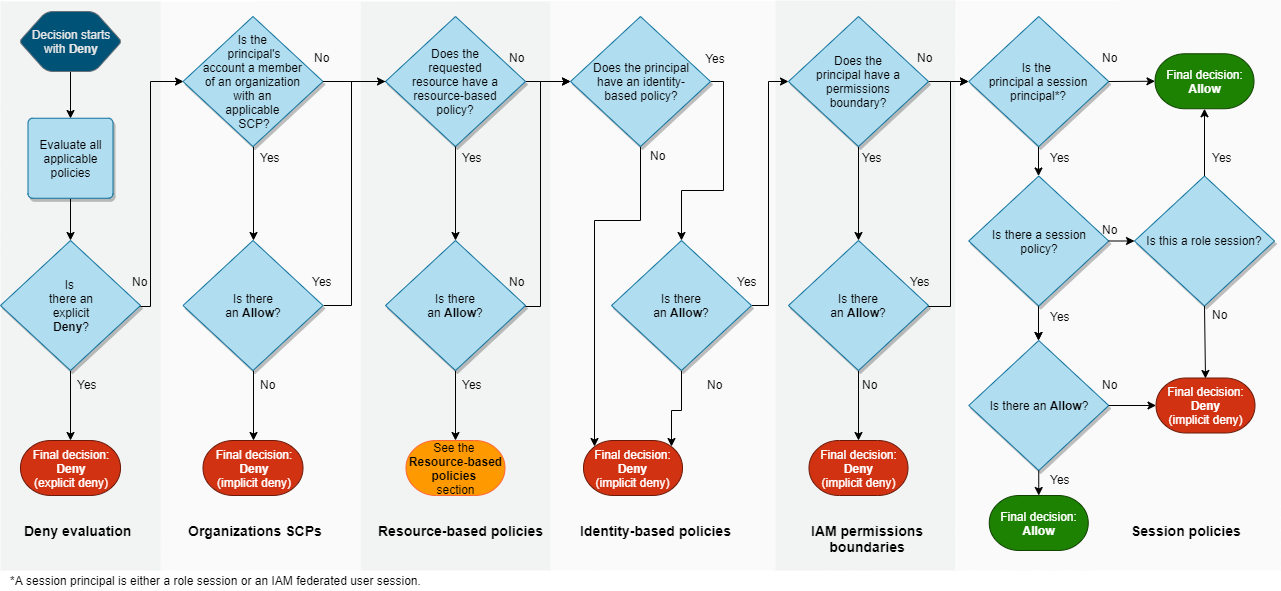
If the diagram makes your head hurt, it’s important to note it doesn’t even include the impact of resource-based policies and implicit denials in other types of policies.
Sonrai’s Toxic Permissions Analyzer is designed to do all of the analysis for you – in real time – maintaining a consistent map of identities, access and permissions in your cloud. Patented analytics fuel the analyzer engine and the result is visibility and risk identification you can’t get anywhere else.
To learn more about risk identification, prioritization, and remediation, learn about our Prioritized Actions.
Toxic Permissions Analyzer Use Cases
With Sonrai’s Toxic Permission Analyzer, you can:
- Secure exploitable indirect access to sensitive resources (even when multiple steps are required to achieve)
- Break toxic privilege combos that threaten your cloud where an attacker can gather privileges from multiple unrelated identities to take unauthorized actions
- Enforce least privilege & separation of duties that don’t break over time or because of unseen escalation connections
- See access paths across clouds, accounts, or any boundary normally hidden in IAM analysis
Real World Examples
Stopping attack paths & unintended data access.
Consider the example below – here we have an EC2 instance in a Sandbox account with access to sensitive medical records in Production. How is this possible?
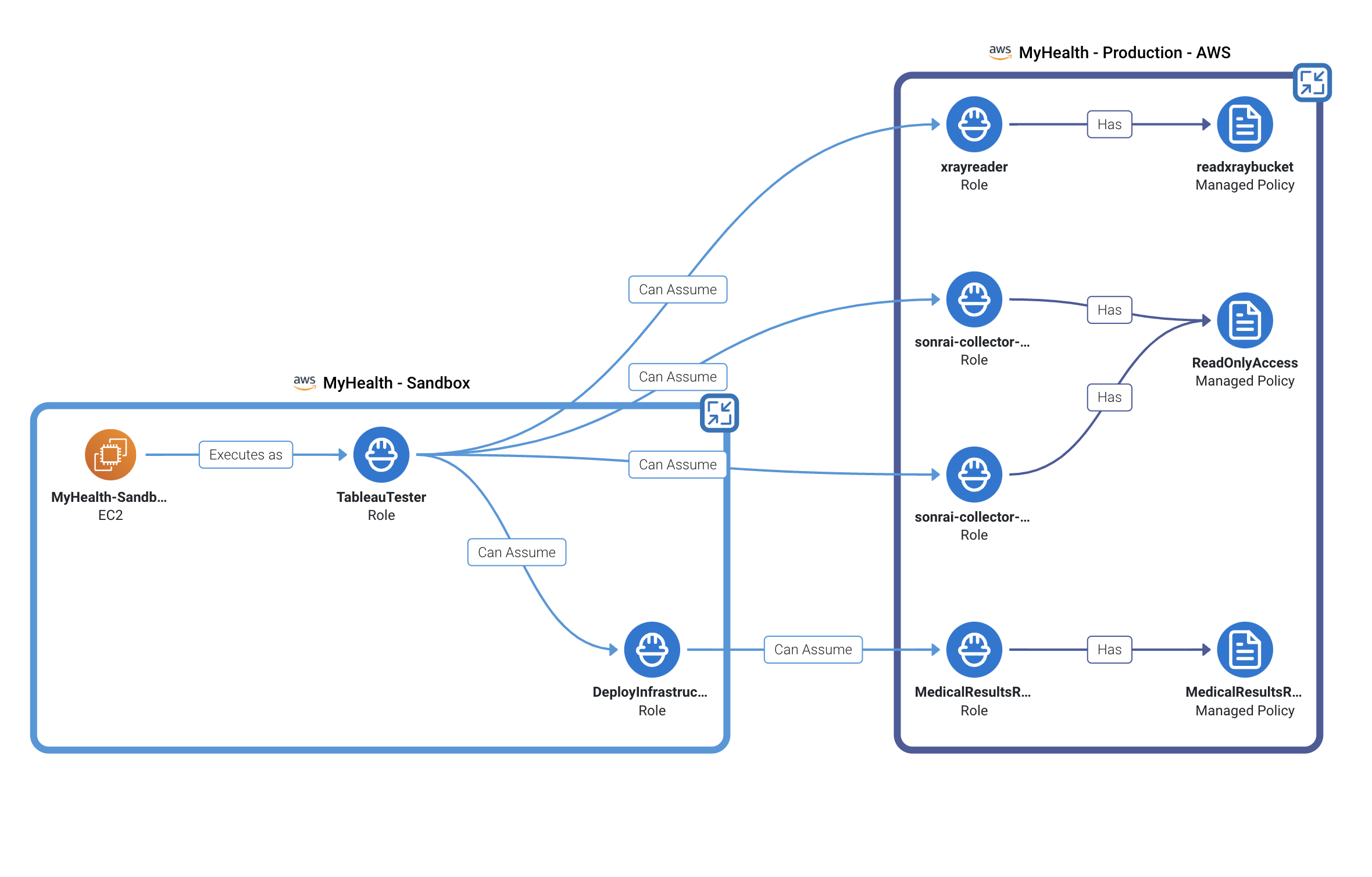
The EC2 instance is able to execute as the TableauTester role – this is where things open up. TableauTester allows the EC2 instance to assume multiple other roles including xrayreader, which has access to read the contents of an S3 bucket, sonrai-collector roles, with read access, and finally, a MedicalResults role with access to sensitive patient medical results.
If this EC2 instance is compromised, an attacker now has access to reading customer PII, leaving the company in violation of major compliance mandates and facing hefty fines and reputational damage.
Sonrai’s Toxic Permissions Analyzer does not just reveal these risks, but also provides prescriptive remediation steps. In this case, the recommendations are: certifying this identity should have this privilege, and if not, restricting the identity’s permissions, or adding a resource policy protecting the datastore. Sonrai offers both detailed AWS Console and AWS CLI instructions for modifying the EC2 instance’s permissions to block access.
This example may seem like a difficult path for an attacker to find, but with persistence and especially time on their side to do recon, they will find a way to reach their target.
Stopping cloudjacking, code injection, ransom and more.
As introduced earlier, sometimes attackers aren’t after data exfiltration, but instead, gathering the right accumulation of privileges. Consider the scenario below exemplifying how privilege gathering can lead to a toxic combination and unintended abilities.
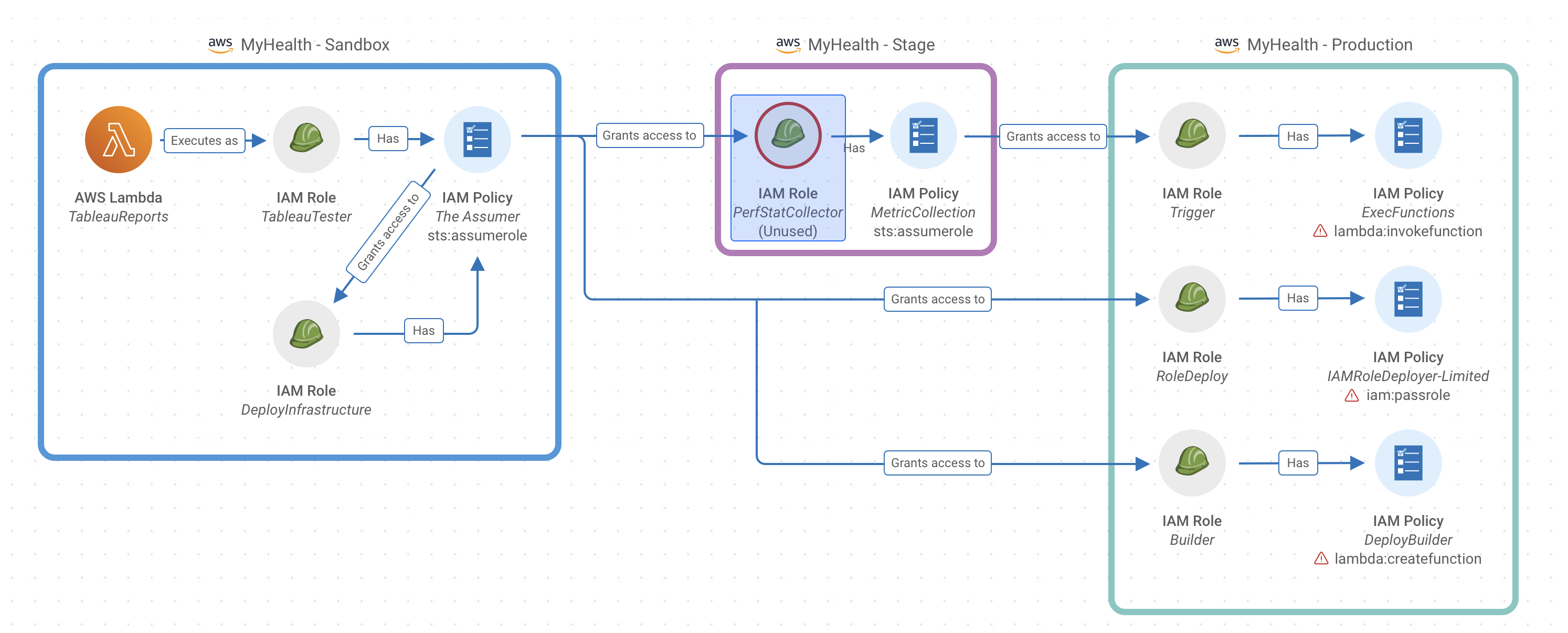
Here we see an AWS Lambda function operating in a Sandbox account. This machine identity can execute as a role, which has a policy tied to it. This policy, sts:assumerole actually grants access across environments. First, it grants access to another role, PerfStatCollector, with another policy attached to it, all in a Stage environment. This attached policy grants access to another role with an attached policy, including the lambda:invokefunction permission, now in a Production account.
Additionally, moving back to the policy with sts:assumerole in the Sandbox account, this policy grants access to two additional roles in Production– RoleDeploy and Builder. Both have attached policies with iam:passrole and lambda:createfunction permissions respectively.
While all of these permissions alone are not a risk, the end result is one Lambda function in a Sandbox account, able to create a new function, pass roles to that new identity, and invoke it. This is a significant violation of Separation of Duties, and what we call a toxic combination.
With this set of privileges, an attacker can do anything they want. They can shut down critical applications, they can inject code, delete resources, or hold your business at ransom.
In this scenario, Sonrai’s Toxic Permissions Analyzer not only identifies the toxic combination, but in combination with our Prioritized Actions recommends remediation including:
1.Apply Least Privilege to roles involved (policy automatically generated and suggested)
2.Remove the IAM role ‘PerfstateCollector’ to break the chain as Sonrai has detected it is unused and therefore unnecessary.
Reduce Risk, Protect Assets, and Maintain Business
The reality is the enterprise cloud is too complex and expansive to properly keep track of identities, not to mention all their permissions (assigned or inherited.) Malicious actors know this and weaponize identity and entitlements to exploit your cloud and breach data, or shut down operations. IAM, PAM, and native cloud tooling do not offer the granularity of insight into identity entitlements (all the inherited ones, the cross account or cloud access, the machine identities, etc.) nor the advanced analytics to interpret the actual actions these privileges translate into.
Toxic Permissions Analyzer, part of Sonrai’s CIEM solution, is built to find and break the identity chains creating attack paths your teams can’t see.
Don’t believe it? Watch the solution in action with a recorded or personalized demo.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




