Table of Contents

Share this entry


Cloud Compliance & Passing Audits
Knowing (1) what and who’s in your cloud, (2) what they can access and (3) what they can do, is the underpinnings of passing any cloud identity and data audit. This requires security teams to have granular insight into every policy, privilege, and unique action (there’s 42,000+ across all the major CSPs) a cloud identity can take. Plus, how those identities and entitlements intermingle with other cloud resources, workloads, applications, and data. Things can get complex and messy quickly. Not only do security and cloud teams need to proactively prepare for an audit, but they need to be ready to answer any question, on-demand.
A lot of enterprises we see struggle with a current toolset that does not present a complete and accurate picture of access, making it difficult to confidently respond to audit questions, or out right fail due to hidden risks.
Sonrai Security’s Cloud Access Intelligence addresses this pain point. It helps security teams answer specific and unique-to-your-business questions that no on-prem or other cloud security tool can.
What is Sonrai’s Cloud Access Intelligence?
Cloud Access Intelligence enables your teams to know every possible access point to critical applications, resources and datastores, allowing teams to recognize unintended risks they didn’t know existed. It is backed by Sonrai’s patented identity and access analytics that recognize every possible route to your data through advanced insight into every cloud permission existing in your environment. Sonrai can start at the identity level and tell you every thing an identity can access, and alternatively, at the data level, working outwards, to confirm every thing and person that can access that data.
Cloud Access Intelligence allows you to:
- Search your cloud starting from any identity, permission, or resource – and ask any question that combines the three.
- Build complex queries to validate that your intended policies and practices are being followed.
- Receive a full history of identity actions, assisting in audit & incident investigation.
- Create custom policies to alert when an out-of-policy action or event occurs.
And you can use it for:
Audit prep: get complete evidence collection via continuous monitoring of every action and decoding of every permission. Always know who could access what, when.
Continuous Custom Compliance: enforce controls to meet unique needs and fit the shape of your cloud.
Protect audit data: ensure evidence collection best practices and protect the evidence once it’s captured.
Answer audit questions: Know everyone who can access a sensitive datastore and has the key to de-encrypt it.
3 Examples of Search Queries Cloud Access Intelligence Can Answer
1. “My employee is leaving, I need to offboard their digital footprint.”
Governing identity is nothing new to traditional IAM tools, however, these tools fall short in the cloud. When an employee leaves a company, it is best practice to govern their identity and delete the user – this can easily be done with native directories or IAM tools. What these tools don’t see are the cloud-native identities that a human user’s identity created. This is a massive blindspot, as these entities are identities themselves, increasing your attack surface and waiting to be exploited. It is even possible for the human user who created them to leave the company and still access groups or roles they made – an insider threat. So, how does Sonrai Cloud Access Intelligence help?
For this example, let’s consider any role assignments granted by an employee, Sandy. Navigating to our query, you can build a search looking at all ‘role assignments’ made in Azure from the user ‘Sandy’, as shown below.
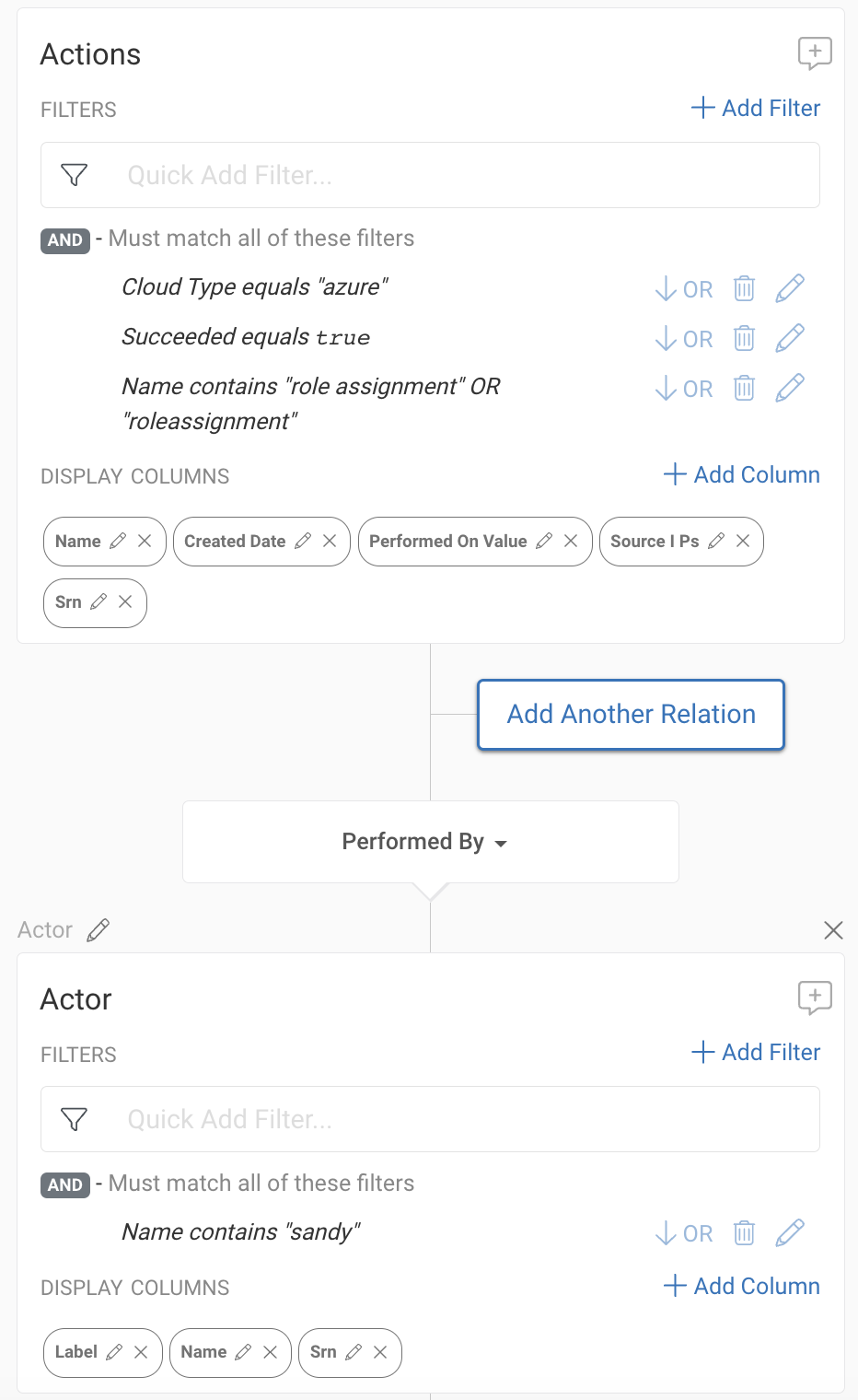
Running this search, you’ll receive every role assignment made by Sandy. Let’s explore one example specifically – a role assignment granted to a Service Principal. Because Sandy is leaving, we want to do our due diligence and look into this Service Principal.
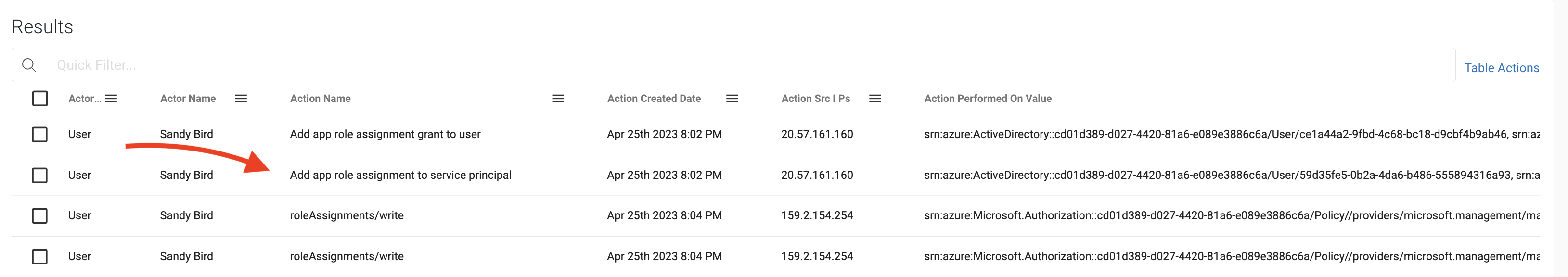
Taking the Azure ID for the ‘Performed On’ value, and inputting it into the search bar, you receive the user, in this case, ‘Sonrai Collector’, and can select ‘Node View’. This is where your team can evaluate whatever concerns it has – perhaps Least Privilege. So we want to consider 1. What privilege does this Service Principal have and 2. Is it using it? This enables your team to determine if 3. You should detach privilege or delete it entirely.
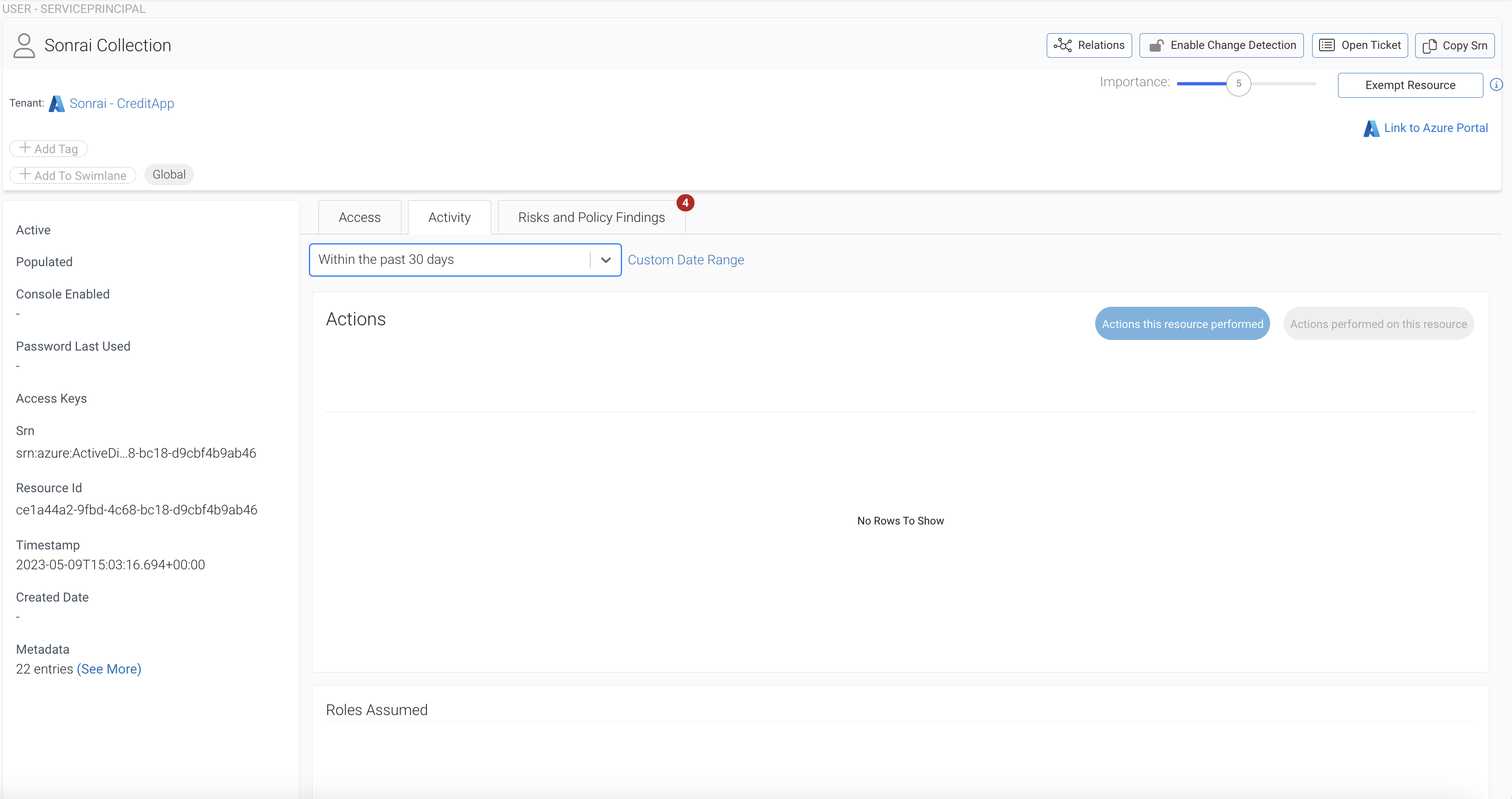
Node view reveals the activity logs – in this example, we see it is not active in the last 30 days. Sonrai’s ‘Risk and Policy Findings’ shows several concerns including, access to sensitive data & reconnaissance privilege – yet none of this is being used.
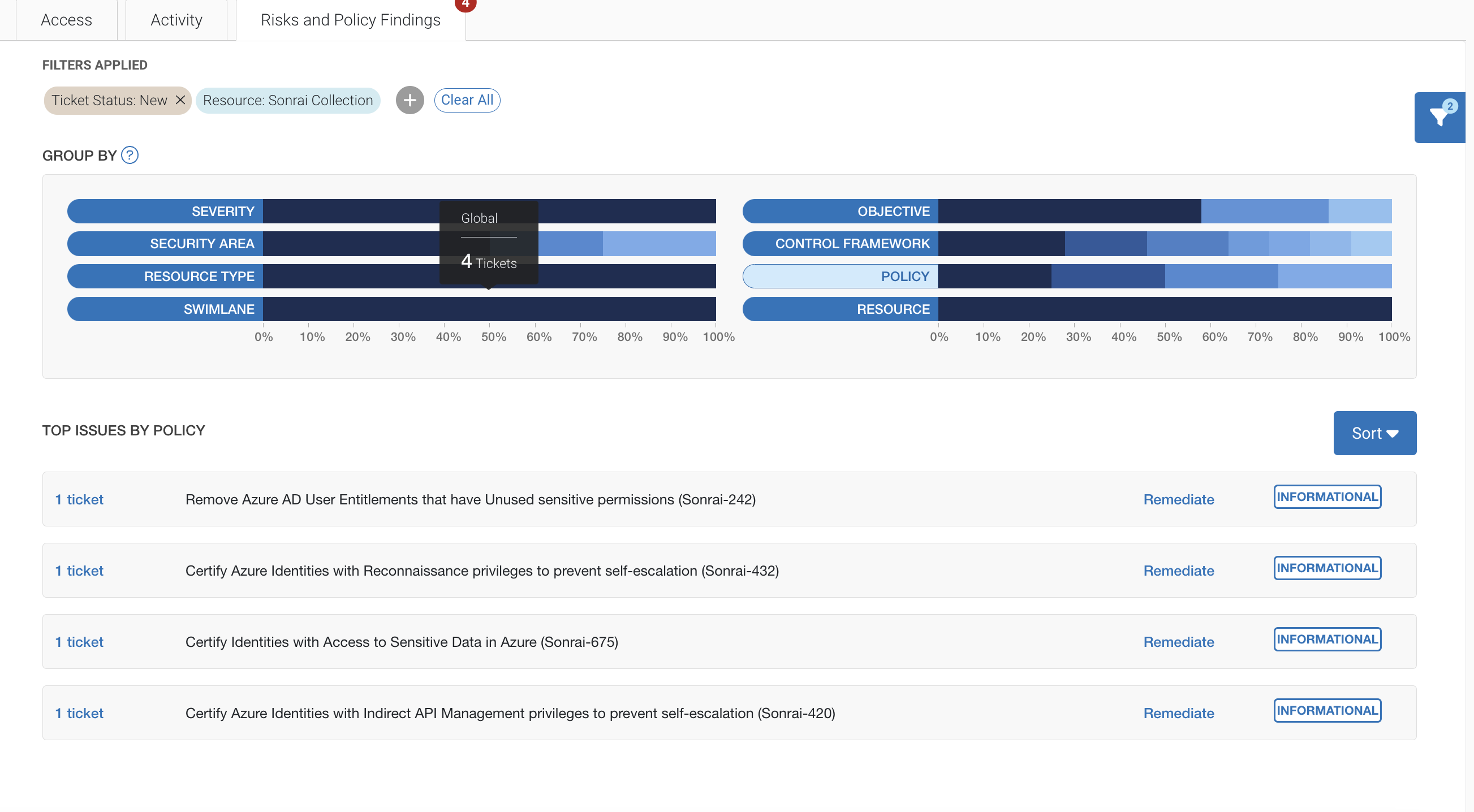
From here your team could navigate to each security ticket for remediation steps — either prescriptive guided remediation or automated bot remediation in some cases.
2. I need to ensure nothing from outside Production can access my Prod data.
In order to meet your compliance regulation, you need to ensure that nothing from outside your Production environment can access the datastores in Prod hosting various sensitive information. Navigating to Sonrai’s search functionality, we can build a query searching for any actors not in the AWS Production account, but that do have the ability to create, delete, change, modify, or update AWS Prod data containers.
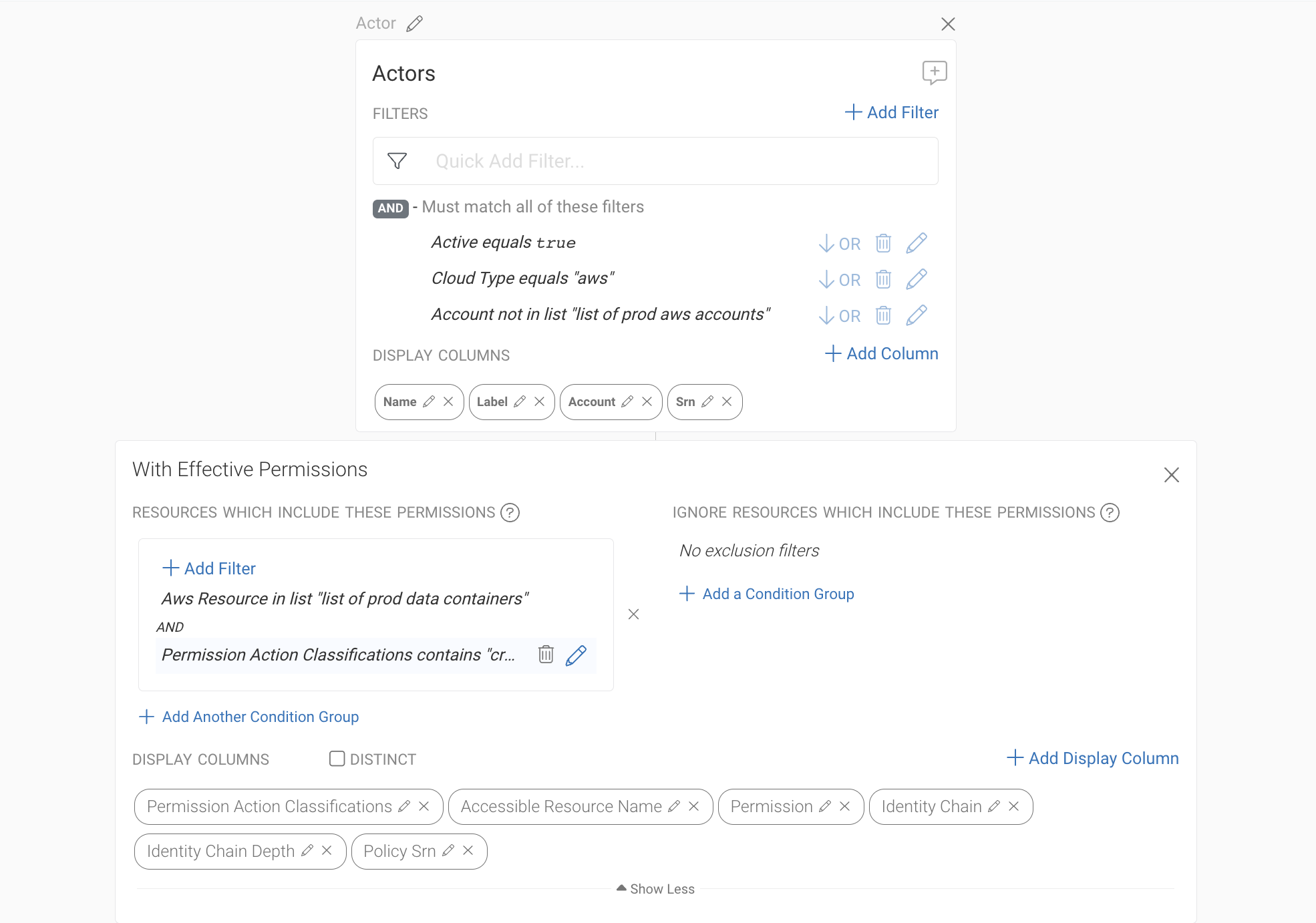
This insight is possible through Sonrai’s Effective Permission analytics. Running this search, we get back all actors with access to Prod data containers, what resource they can access, and with what permission. In this example, we see several dynamoDB tables that can be accessed using dynamod.*
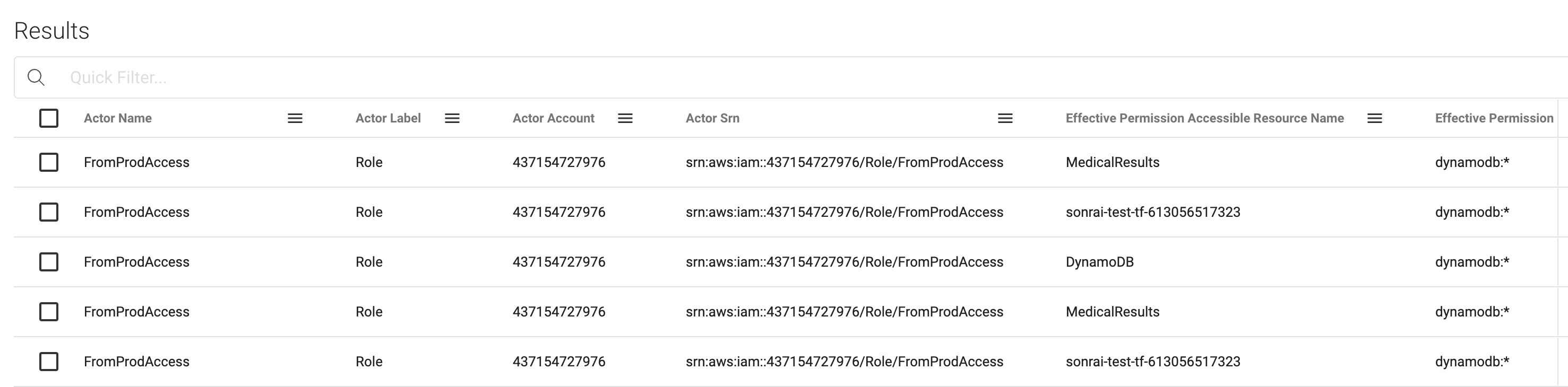
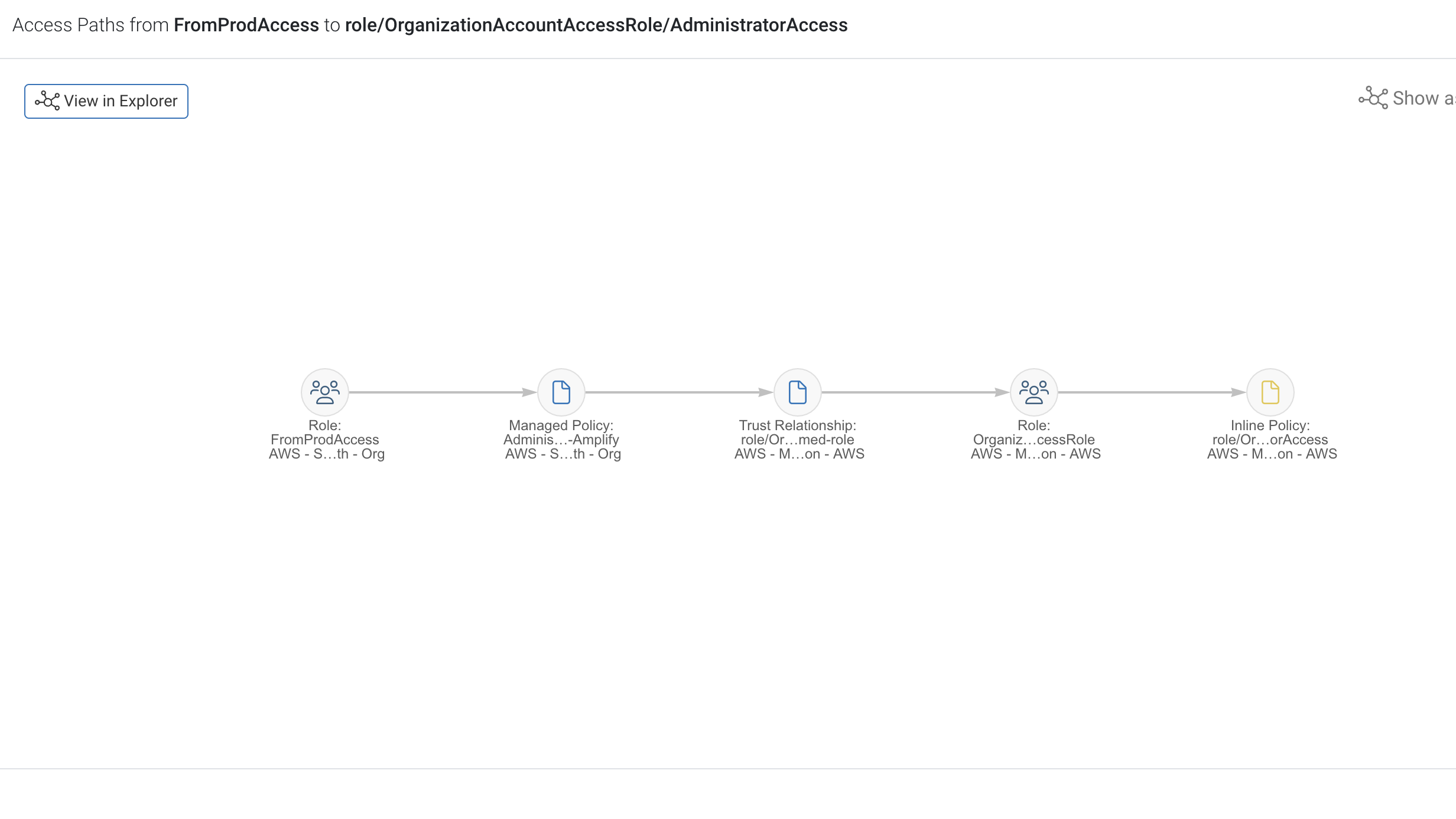
Taking a look at one table, ‘MedicalRecords,’ we can click in further to ‘show path’ and examine how exactly this actor, in this case a role, can access Prod data. It appears that a role, via a trust relationship, can assume a role that’s in Production, that allows them the dynamodb.* permission.
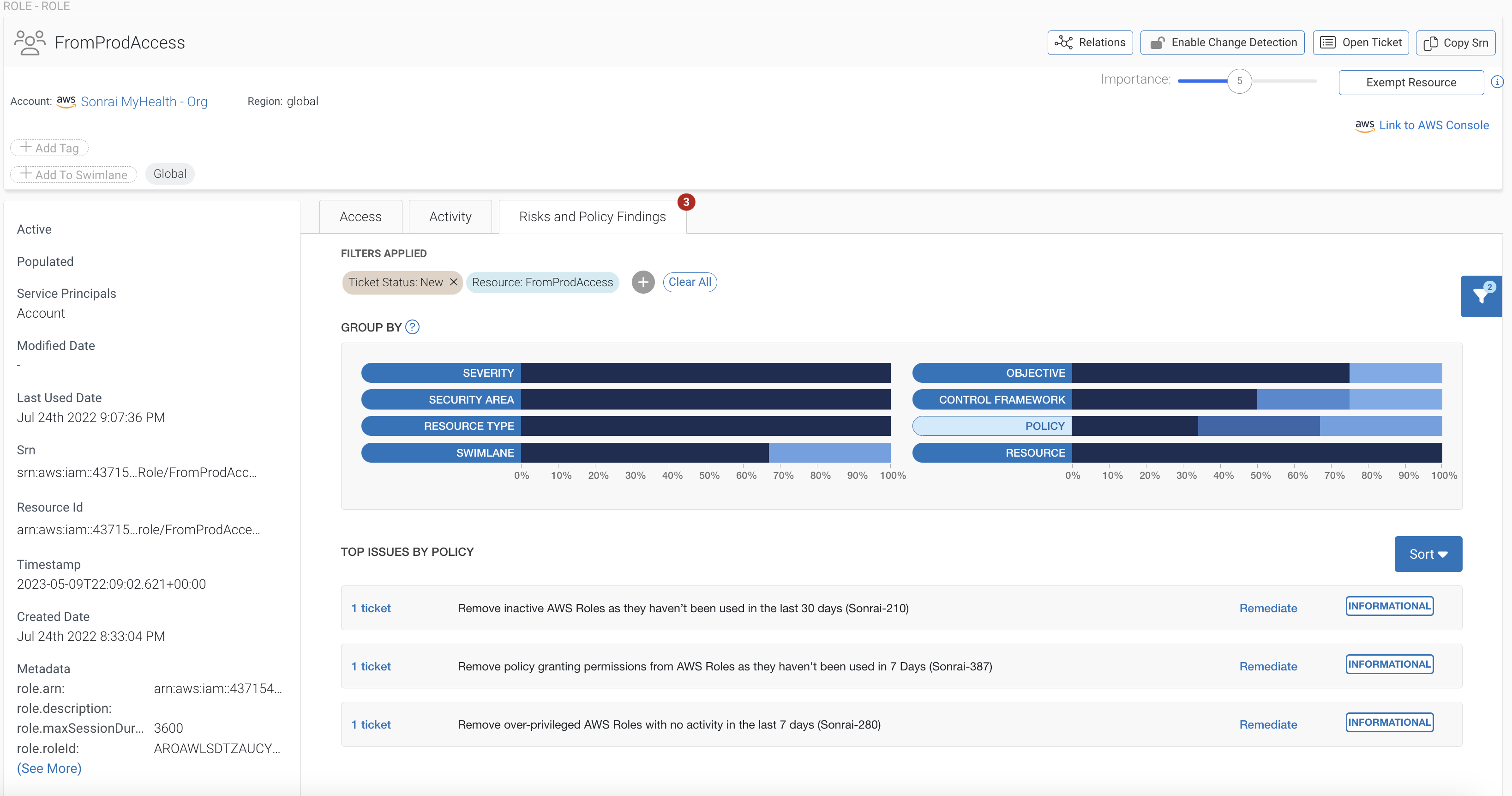
From there, your team can click into the Node view of each actor with access and navigate to ‘Risk and Policy Findings.’ From there, individual security tickets each offer remediation options – either prescriptive guided remediation or automated bot remediation.
This is a critical capability that can’t be overlooked — the ability to start at the data, and work outwards to understand everything that can access it. No other vendor can take this approach and it is exceptionally helpful when your organization has specific applications or datastores you need to ensure are secure.
3. “Do I have any publicly accessible Virtual Machines with access to sensitive data?”
In this example, we’ll consider compute services, but limit the search to just Virtual Machines. Specifically, we’re concerned with VMs that have sensitive access (whether you intended this, or not.)
Navigating to Sonrai’s search function, we can input ‘Azure Virtual Machines’ to receive a list of relevant services. For the sake of this example, we’ll focus on the machine, ‘CreditApp-Sandbox-Automate.’
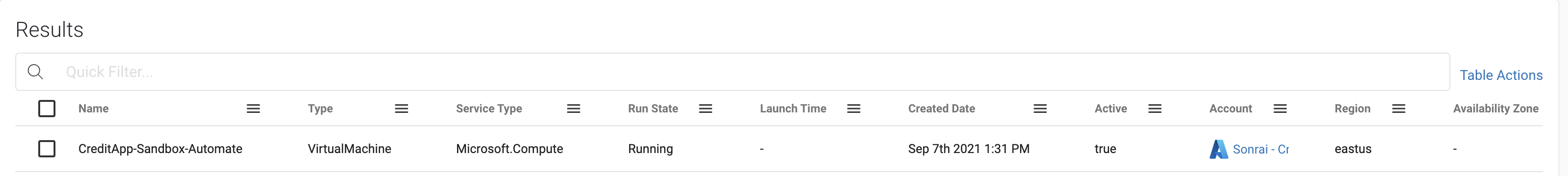
Clicking into ‘CreditApp-Sandbox-Automate’, and then navigating to the ‘Network’ tab, we can see this VM is publicly accessible via Port22 – our first concern. But not every VM is created equal, as some hold more sensitive access than others. In this example, that is the case. Moving to the ‘Access’ tab, we can see every entitlement this VM holds.
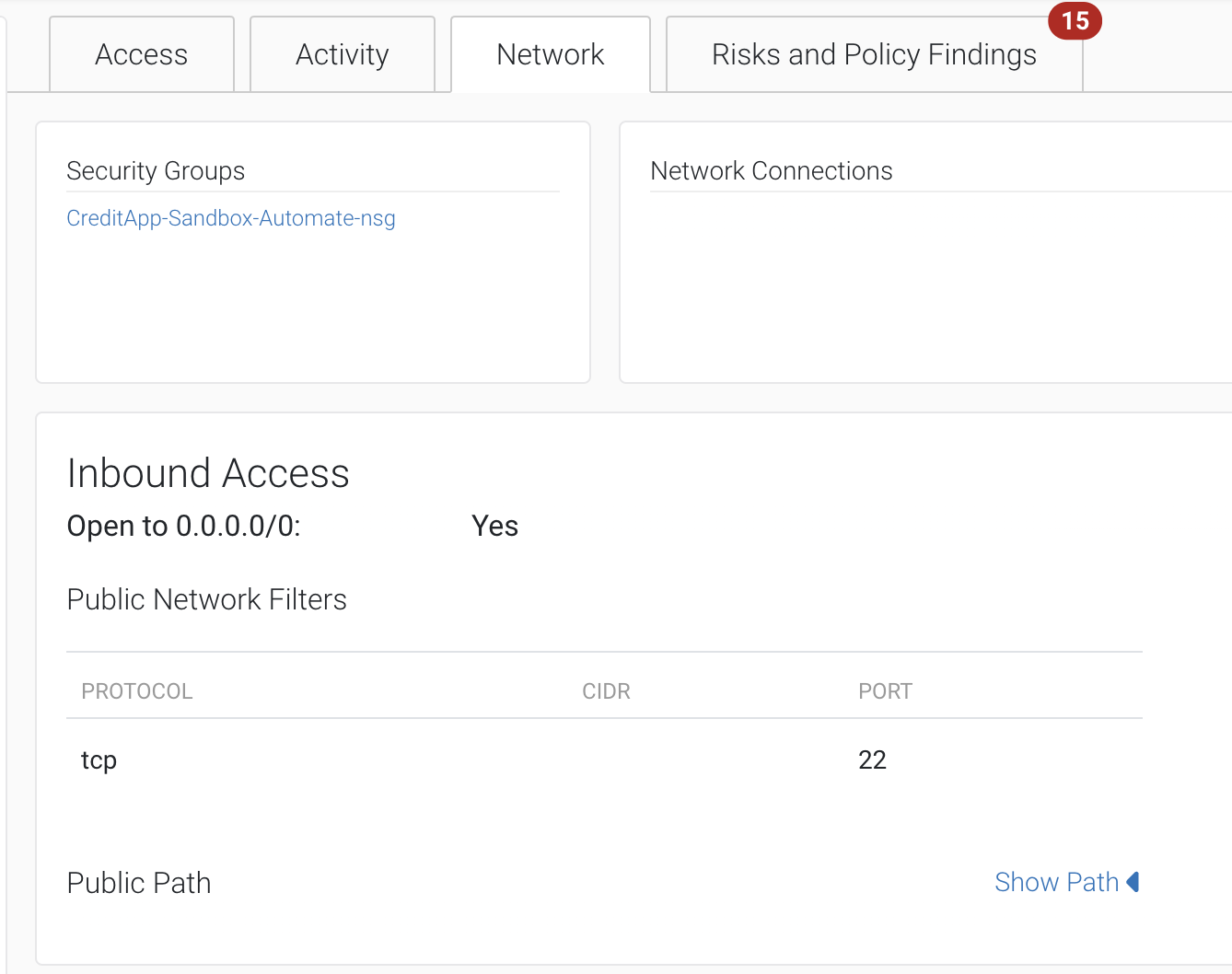
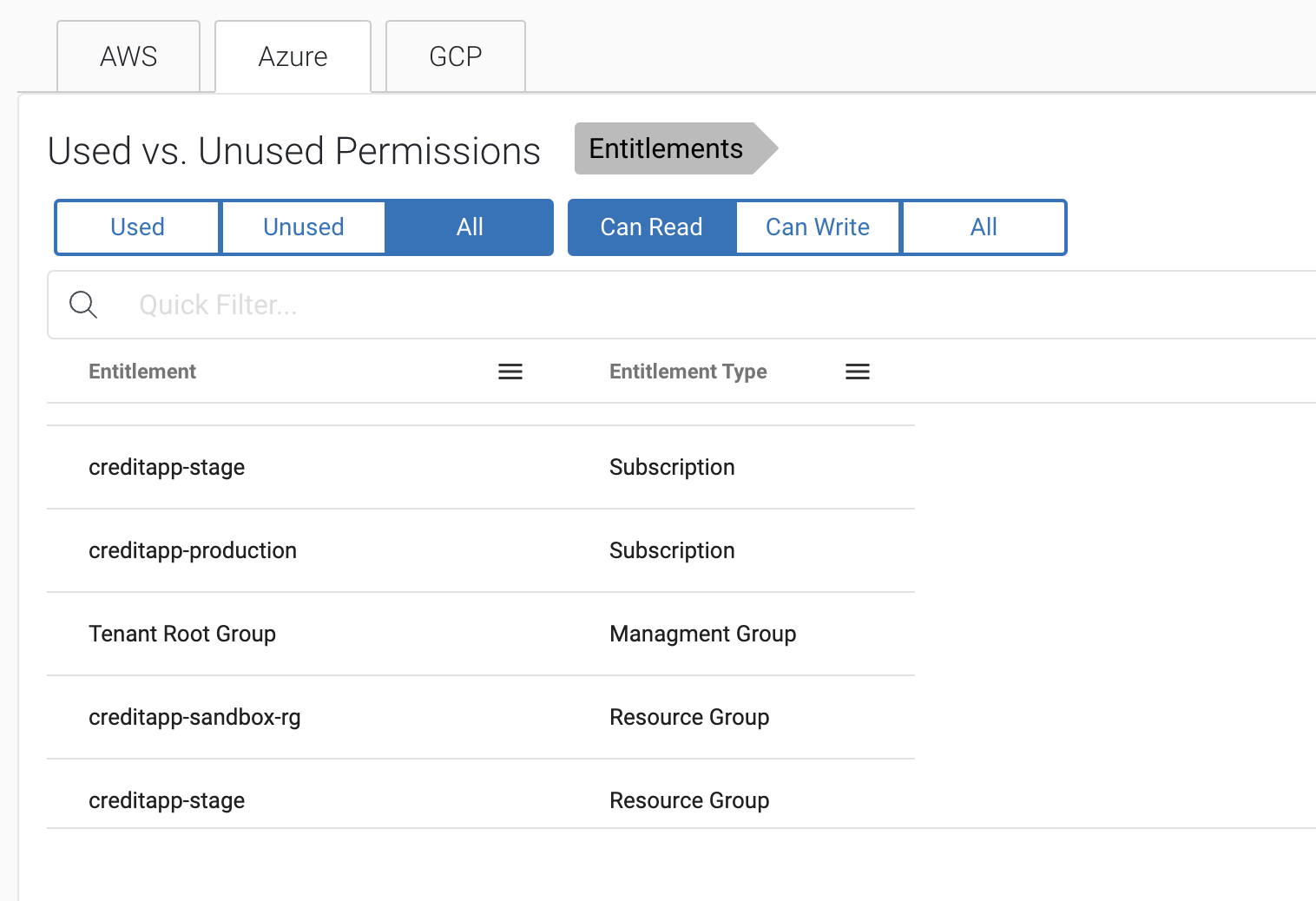
One concerns us particularly – ‘creditapp-production’ — that doesn’t sound good. Clicking through, we can see this VM has a ‘reader’ role assigned to it, digging in even deeper, it holds */read permissions lending it a variety of sensitive reading rights for a variety of things including Microsoft billing accounts.
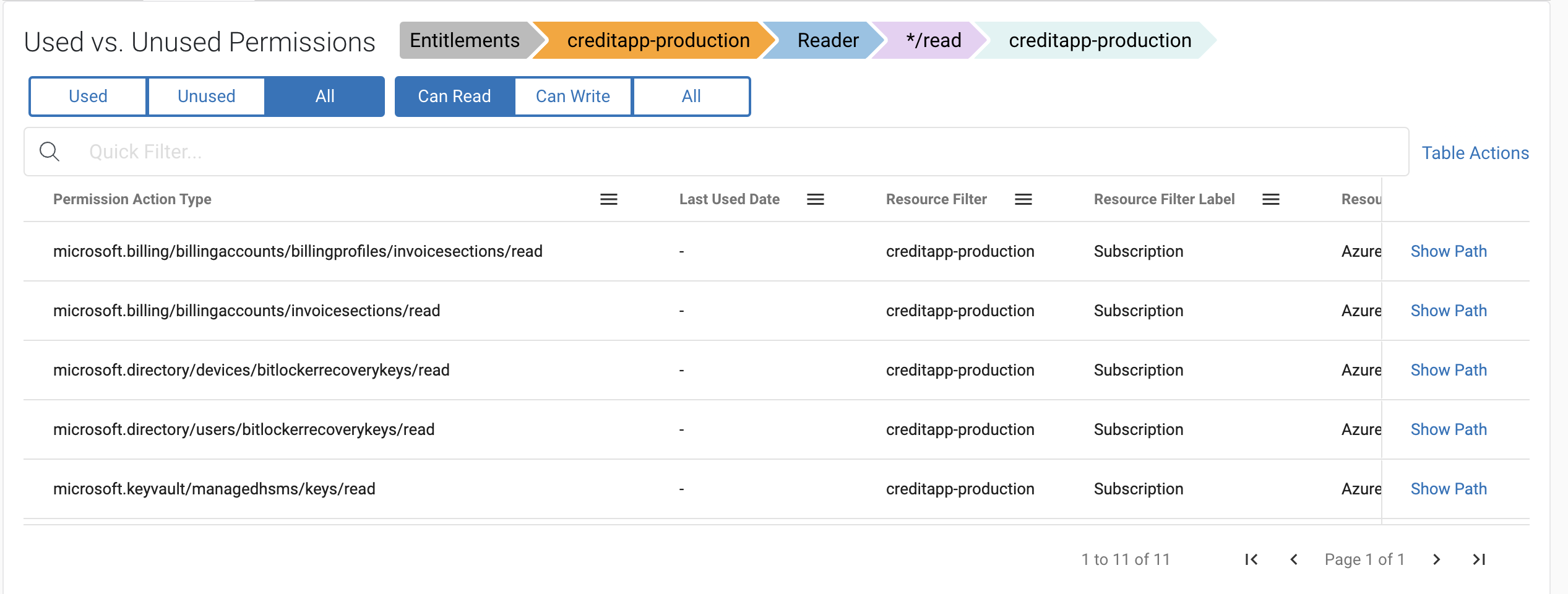
Sonrai is able to detail how exactly this VM acquired this */read permission in this identity chain below, available by clicking ‘show path.’
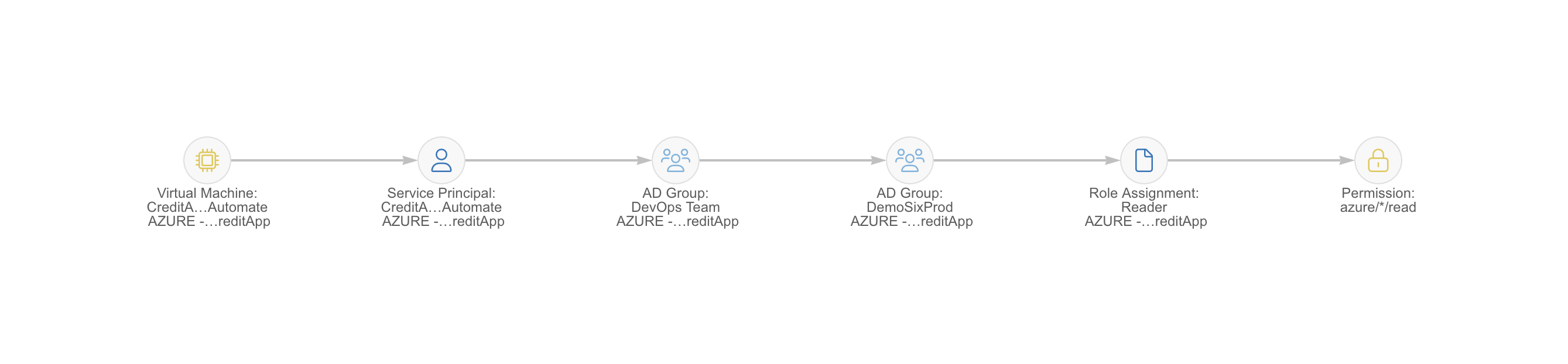
So there you have it – a Virtual Machine with access to sensitive data, including potential customer PII, that also is open via a port to the internet. This on-demand information enabled security teams to remediate accordingly, and prioritize this kind of risk (one tied to critical information) over other dead-end VM access points.
Continuous Cloud Compliance with Custom Policies
Another pain point we often hear about is maintaining compliance proactively. That is not just scrambling to pass a one-off audit, but instead, creating a security program that keeps up with your dynamic cloud to always remain ‘in check.’ Sonrai offers prebuilt compliance frameworks organized from 1000+ controls for common regulations like PCI, HIPAA, HITRUST, and more, but can also build out custom frameworks to meet your specific needs. Once in place, our platform monitors your environment to detect drift out of compliance and provide remediation steps.
Leveraging Sonrai’s Cloud Access Intelligence can help inform your organization on new controls you want to implement. For example, you want to ensure all users and roles with the name ‘Contractor’ in them don’t have access to any environment outside Sandbox. The search would return any results in violation of that, allowing your team to remediate. Once things are ‘cleaned up’ your team can build out a custom policy enforcing this over time.
Ensure Enforcement with Cloud Access Intelligence
When it comes to cloud compliance, there’s a lot on the line — regulatory fines, disruption of business, and loss of customer trust. Your organization needs 100% assurance the security policies you put in place are enforced sufficiently. In the cloud, there is often ‘stuff’ you cannot see or didn’t know existed. The ability to query any data access or identity-related question on-demand gives your teams the chance to enter your next audit without a doubt of passing the first time around.
You can think your customer data is protected, or that your environments are sufficiently at Least Privilege…but, how do you know?
Sonrai Security’s Cloud Access Intelligence can be your next answer.
Interested in seeing it in action? Consider a personalized demo or an on-demand one.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




