Table of Contents

Share this entry

Cybercrime Runs Rampant
Cybercrime is not slowing down for anyone. In fact, Q2 of 2022 saw a 32% increase in global cyberattacks YoY. This brought the weekly attacks per organization worldwide to reach a peak of 1.2K attacks. What are the costs of cybercrime? Well, an obvious one is financial costs and business loss. IBM’s annual Cost of a Data Breach 2022 Report found data breach costs to surge 13% from 2020 to 2022. Outside of financial loss, if business confidential data is stolen or manipulated, it can impact business continuity, customer privacy, and business reputation.

Globally, things took a turn as the pandemic onset changed business models forever. Remote work surged as enterprises persevered in the wake of a global pandemic. However, the average breach cost was almost 1 million USD where remote work was involved. In 2022 alone, we’ve seen some high-profile attacks and breaches including the Apache Log4j vulnerability kicking off the new year, and big names like TikTok and Uber falling prey to security errors and hacks.
There are several recurring factors or vectors in a lot of these stories. IBM’s report found compromised credentials to be the most common attack vector in 2022. However other significant players in the cloud space are security misconfigurations and overprivileged identities. More information on these two later, as we discuss what measures cloud users can take to protect themselves and ultimately their confidential data.
Cloud Security Measures Add Significance
The growth of cybercrime, in general, should raise concerns for all IT and C-Suite professionals, especially as it coincides with the rise in cloud computing and reliance on Cloud Service Providers.
The public cloud market is growing at an astonishing rate, and spending is forecasted to grow 20.4% in 2022 to total $494.7 billion, up from $410.9 billion in 2021, according to Gartner, Inc. In 2023, end-user spending is expected to reach nearly $600 billion.
That migration is understandable since cloud environments are usually more agile than on-prem systems and can provide more comprehensive and updated computing capacities in quicker time and at less cost than most on-prem systems can manage. A full 60% of respondents to a survey by InfoSecurity believe that the cloud environment is more secure than their on-prem systems were.
“Cloud is the powerhouse that drives today’s digital organizations,” said Sid Nag, VP of Research at Gartner. “CIOs are beyond the era of irrational exuberance of procuring cloud services and are being thoughtful in their choice of public cloud providers to drive specific, desired business and technology outcomes in their digital transformation journey.”
Cloud Security Concerns Rise
However, IT professionals also voiced concerns about relying too heavily on their cloud service providers for all their security requirements, noting several unresolved challenges that still need attention. Areas for concern include customer controls and configurations, with Gartner predicting 99% of cloud security failures will be the customer’s fault through 2025, and resource allocation with 32% of companies saying they are spending less than they need to on cloud security, or nothing.
As organizations look to the cloud to solve many of their computing, analysis, and productivity challenges, they must also weigh the new cloud-based risks that come with those services.

Security immaturity comes at a major cost to organizations. IBM’s Cost of Data Breach Report 2022 found 43% of studied organizations to be in the early stages or having not started applying security practices across their cloud environments. These organizations with immature cloud security models faced over $660,000 on average in higher breach costs than studied organizations with mature security across their cloud environments. The call for a cloud security focus is clear.
Build Your Defense
Cloud Data Loss Prevention
Data is either at rest, in transit, or in use at all times in the cloud. Organizations need to secure data at each stage to prevent confidential data loss or theft. Data loss prevention is now applicable to the cloud. It is the effort to secure and protect the data hosted in your public cloud platform. It aims to protect the confidentiality, integrity, and use of your data. Cloud providers include data loss prevention native tools in their platforms. They are useful in beginning your data loss prevention strategy or if you’re only working out of one cloud platform. Additionally, there are third-party cloud security providers who offer Cloud DLP solutions. The core strategy of Cloud Data Loss Prevention solutions can be broken down into four pillars:
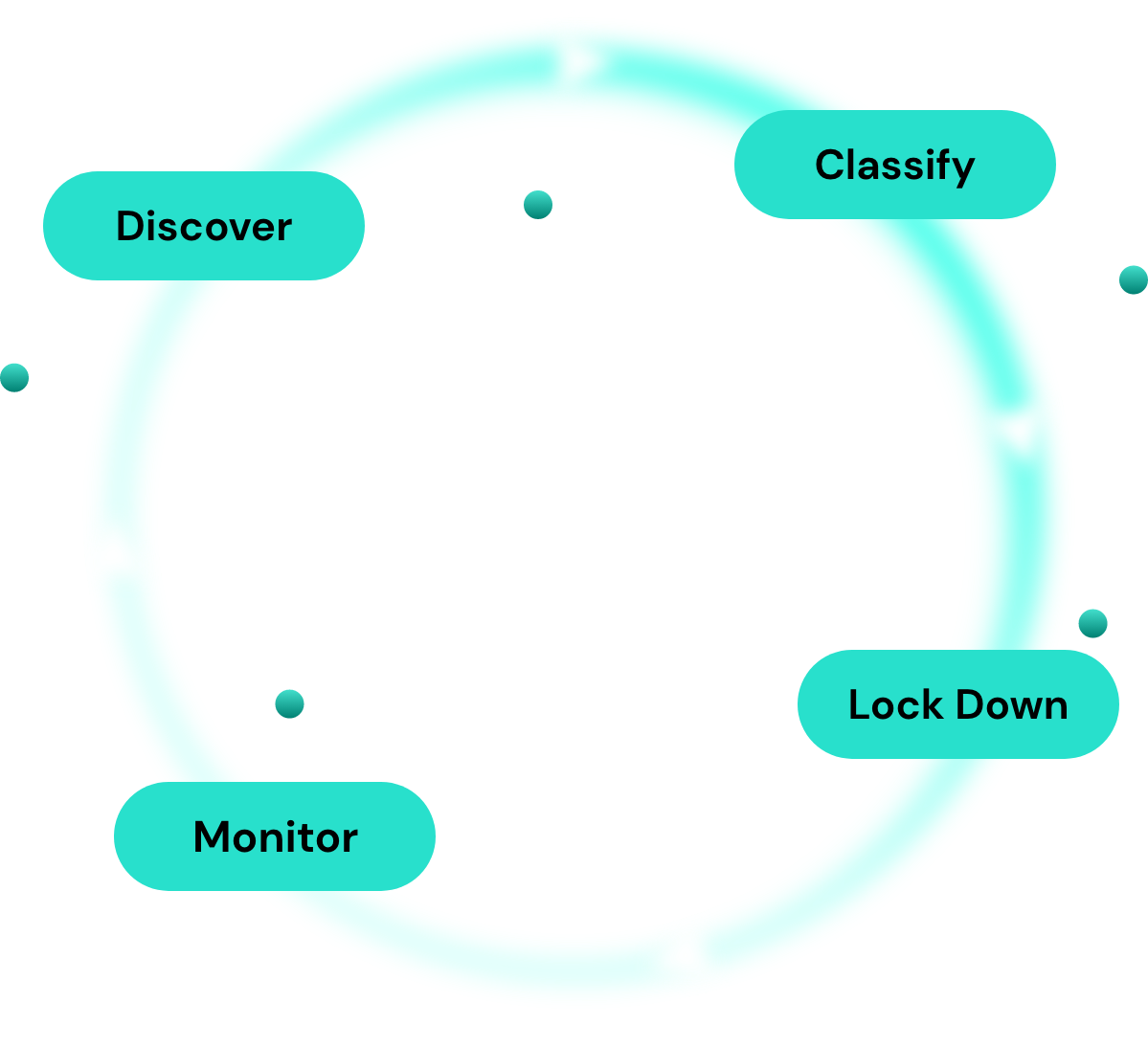
- Discover. To protect your data, you first need to know where it is, not where you think it is or where it should be. To do this, you need to continuously scan for data across all your cloud environments. This not only looks for new data but discovers when data appears in new places. A large part of the discovery process is doing a data inventory. You want a real-time picture of all the data in your environment.
- Classify. Not all data is created equal. You need to know not only where your data is but also what it is. Data classification analytics determine the data type, importance, and risk to the business. This context is key in helping you prioritize what is most important. Data classification looks like labeling your data with a ‘name tag’ and then a ‘value tag’. An example may look like DataClassification:Confidential or DataType:CustomerPII. These tags allow you to know this is highly-sensitive content and should be prioritized in protection.
- Lock Down. Once you have a program in place allowing you to understand and detect security risks, the next step is actually protecting your data. This means stripping away access to your most sensitive assets. Data locating and classification enables your teams to work towards achieving Least Access. Least Access enforces data protection from the inside out, meaning, starting with the data, and working outwards to determine who and what can access it. Then stripping that access to only those that need it. The next step for effective data loss prevention is to work with operations managers to create controls for reducing data risk. Data controls may be simple at the beginning of a DLP initiative, targeting the most common risky behaviors while generating support from operations. As the data loss prevention program matures, organizations can develop more granular, fine-tuned controls to mitigate specific risks to protect data over time.
- Monitor. Once you have visibility into your data, and enforce Least Access, you must continuously monitor data activity to detect anomalous access. Not all data movement represents data loss. However, many actions can increase the risk of data loss. Organizations should monitor all data movement. Periodic or sporadic auditing doesn’t cut it when Non-Person Identities are accessing your data for seconds at a time, at multiple moments a day. Audits include ensuring that basic platform settings like encryption and logging are enabled and understanding who or what has access to your data. Auditing starts with defining a secure baseline you have a comparison. Once you lock that in, you can effectively monitor for deviations on that baseline. An example might be detecting that an Internet-connected VM in Dev, which has a vulnerability on it, has access to your most sensitive data in Prod. Basically, you need to understand when data is at risk. A critical component of protecting your data is leveraging automation and organized workflows. The scale and speed of the cloud is unmanageable without automating the process of detecting concerns and notifying the right team, at the right time, in an organized manner. Automation also comes into play for remediation efforts. Some security solutions include pre-set remediation and prevention bots to pick up where people left off.
Identity and Entitlements Management
If protecting enterprise or confidential data is the goal, you must consider identity management. Identities, person and non-person, are constantly coming into contact with your data. There are over 37,000 actions across the major clouds, and all of them are tied to data. Identity is now the vehicle attackers exploit to get to your data, and often consider the new ‘perimeter.’ All this being said, locking down identities and their entitlements (i.e. abilities) is critical to protecting data.

So how can enterprises approach identity management? Cloud Infrastructure Entitlements Management is an increasingly popular solution for addressing these concerns. Their approach begins with getting an inventory of all the identities in your environment – both person and non-person. Non-person identities are entities like pieces of compute, serverless functions, service principals, roles and more. Knowing who or what is in your cloud is just the first step. The heart of a strong CIEM solution is visibility into the effective permissions of all identities. This means revealing every ‘ability’ identities have, or finding all the connections between identities and data. Strong graphing and analytics will detail these relationships to help your organization find covert or indirect permissions.
Seeing all this risk then allows you to strip excessive permissions and drive your environment to meet policies like Least Privilege. Finally, a CIEM solution will keep you at Least Privilege with continuous monitoring. This means detecting anomalous behavior or access, or any new ‘out-of-policy’ permissions being allocated. Tight identity and entitlements management keeps your data safe.

Compliance and Frameworks
Data and compliance go hand-in-hand. A structured and reliable way to achieve compliance is following relevant data security frameworks. Cloud security frameworks are broad or specialized guidelines that encourage security measures for cloud use. This includes outlining the policies, tools, configurations and rules needed for secure cloud use. They can be industry specific – for example, healthcare – or offer validation and certification in different security programs. Overall, these frameworks provide a set of controls with specific guidance for secure cloud use and customer or confidential data protection.
Some common examples:
NIST: The NIST cybersecurity security framework is a template from the National Institute of Standards and Technology. It consists of five action areas we will list below. This template guides the tools you deploy and the policies you establish to guide user behavior in your cloud. Below we define each pillar of NIST compliance and the questions they cover:
- Identify: this pillar helps develop an understanding of the cybersecurity risks in systems, people, assets, data and capabilities.
- Protect: this pillar helps outline the appropriate safeguards to ensure the delivery of infrastructure services.
- Detect: this pillar helps define the activities to identify the occurrence of a cybersecurity event.
- Respond: this pillar helps establish the right processes to take action regarding a detected cybersecurity incident.
- Recover: this pillar addresses defining the processes necessary to maintain resilience and restore impaired services.
ISO 27001/ 27017: This template is by the International Organization for Standards. It is a specific set of standards for information security systems. You can view this framework as the gold standard for information security and compliance. Your company must prove it has completed rigorous security practices to protect its data.
CSA STAR: The Cloud Security Alliance (CSA) and Security Trust And Risk Assurance (STAR) paired together to create a comprehensive cloud security assurance program. By adhering to this STAR framework relevant to your CSP, your organization demonstrates strong security posture and secure cloud controls.
HIPAA: This Act aims to protect individual’s health-related information, however contains certain criteria specific to information security. Organizations under HIPAA must complete risk analyses and establish risk management policies. If you’re in the cloud, it is your duty to ensure your CSP is HIPAA compliant.
SOC 2: This is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of your clients.This is a minimal requirement when considering a SaaS provider. SOC2 defines criteria for managing customer based data based on five principles – security, availability, processing, integrity, confidentiality and privacy.
Cloud Security Posture Management (CSPM) is a market-trusted solution to help enforce compliance and detect cloud drift. The solution monitors your environment and checks it against custom secure baselines or industry compliance standards like NIST or GDPR. When deviations are detected, it alerts your teams. A next-generation CSPM tool will have automation capabilities to ensure intelligent alert triaging processes.

Automation and Remediation
IBM’s Cost of a Data Breach, a View From the Cloud Report 2021, noted that employing automation and AI was associated with a lower average cost of data breach and shorter breach lifecycle. The report formally indicates that using an AI platform was a leading factor in mitigating costs, with an average difference of $1.49 million.
Leveraging a solution that harnesses the power of automation shines when it comes to remediation and prevention. With the right tool, you can catch insecure code, vulnerabilities, identity misconfigurations and more before they come to fruition. Detecting a risk is just half the battle, intelligent workflows can automatically route alerts to responsible teams or individuals, and with a context-based solution at hand, workflows can prioritize risks by severity.
Remediation efforts can be suggested code solutions, prebuilt prevention bots, or custom bots depending on your business needs. The key to automation is configuring your solution to fit your unique business so it can auto-deploy the right policies, security sensitivity levels, and remediation efforts on its own.
The benefits are apparent, yet many organizations are still hesitant to harness the power of automation. Automating continuous monitoring, workflows, and remediation efforts prevent bottlenecks and takes a load off of manual team efforts, allowing focus on other business needs. If used correctly, automation helps the cloud secure business better than previously possible. At the end of the day, that translates to better protecting your confidential data.
A Final Thought
The public cloud is prospering, but alongside its growth, is the parallel increase in cybercrime and breaches. The cloud is a new landscape with unique challenges arising, like customer responsibility, cloud-specific need, immature security models, and the collision of security vs. development needs and processes. The cost at hand is enterprise data. Data theft, loss, and breach translates into serious business impact and often customer-involved repercussions.
One thing about the cloud is its amorphous, complex, and entangled nature. There are many layers to it, and it holds a number of entities like workloads, identities, services, compute, and more. All of these entities are coming into contact together, and touching your data. Because of this, cloud security strategy must shift to consider this reality, and approach things from a comprehensive and total view.
This article aimed to touch upon just a few of the defense angles closest to data, including data loss prevention, identity and entitlements management, compliance enforcement and automation. The cloud security conversation expands past just these solutions, and if you’re interested in learning more about a total cloud security approach, you can check out Sonrai Security’s Cloud Security Platform.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.