Table of Contents

Share this entry

So you’ve identified your most critical assets. You know your super users. Your highest privileged identities. You know the applications that are the backbone of innovation. You know the datastores holding private customer information.
Now it’s time to lock those entities down and detect suspicious or risky changes in access or permissions.
Sonrai’s Cloud Anomaly Detection is the critical final step in your defense-in-depth strategy.
What is Sonrai cloud anomaly detection?
Anomaly detection refers to identifying unusual activity that falls outside of a typical baseline of access or permissions in your cloud. Security is a continuous process, not a destination. Once you’ve ‘cleaned up’ your cloud, Sonrai’s anomaly detection helps you maintain that posture by alerting on and remediating new changes that create critical risk, or anomalous behavior signaling attacker activity.
Our anomaly detection comes in a two-prong approach.
Monitoring Datastores
For changes in:
- Who can access it
- Who did access it
- The geographic location it’s accessed from
Monitoring Identities
For changes in:
- Resources they can access
- CLI or console access
- The geographic location of activity
- Effective permissions.
And all of this monitoring is done down to the specific action. Sonrai can translate the 42,000+ different permissions across the major cloud providers into action categories. These classes include actions like edit, configure resource, delete resource, read data, and 30 other access categories. Just knowing something was vaguely accessed is not enough.
See my cloud identities and their risks.
How does sonrai cloud anomaly detection work?
Typically, anomaly detection just translates into monitoring activity history and comparing that to a typical baseline for deviations. Sonrai’s goes further –
We monitor for anomalous permission and access changes – not just historical activity.
For datastores, you can monitor for changes in not only who’s accessed it in the past, but also if it’s accessed from a new geography, or if there’s a specific change in who could access it in the future.
Cloud permissions are proliferating. There are 42,000+ different permissions across the major providers. Combine all those permissions with compounding managed and inline policies, nested grouping, assumed roles, cross-account trust relationships and so much more.
The result is effective permissions creating unintended consequences. Sonrai has insight into the net effect with our patented permission analytics and is continuously monitoring for changes you don’t want.
So maybe you don’t care that there’s a new identity that can read a bucket, but you would care if there’s a new identity that could edit or delete the bucket –you can set a specific alert on that.
It’s a similar story for critical identities you want to monitor. Sonrai will see if their permissions change at the most granular level. If an identity all of a sudden has the ability to delete infrastructure or create, pass, and invoke new roles, your team would want to know.
Our anomaly detection isn’t just detection, but also response. You can set up protections around critical resources – policies that will isolate the resource if potential attacker activity is detected, such as doing recon or privilege gathering to acquire a toxic combination. This is Sonrai’s Cloud Detection and Response.
Read about a breach where anomaly detection could have helped.
How we’re different:
Like we mentioned, anomaly detection is nothing new, but here’s what Sonrai offers that is different:
Other tools can’t offer critical resource monitoring starting at the datastore level. This includes knowing changes on ‘who can access’ it. This ensures your teams know every entity that can touch your critical assets at all times.
Other tools only detect permission changes of policies directly attached to identities, but that leaves a lot of blindspots. In the cloud, effective permissions are the result of trust relationships, inheritance, and other convoluted means of indirect privilege. Identities hold privileges we never directly assigned to them. Your teams need to be alerted to anomalous changes to those too.
Other tools only see vague permission or access changes – we see at the most detailed level to tell you what exactly an identity can do whether it’s ‘read,’ ‘configure,’ delete,’ or any of the 30+ other categories. This context matters and enables your teams to filter for changes unique to your use cases.
Other tools are reactive by detecting historical activity when it may be too late. Sonrai catches changes that introduce new risks so you can remediate before an attacker can exploit them so your team can be proactive.
How can you use Sonrai’s cloud anomaly detection?
Cloud Anomaly Detection Use Cases
Let’s see Sonrai’s anomaly detection at work. Let’s start at Sonrai’s Critical Resource Monitoring feature on the platform.
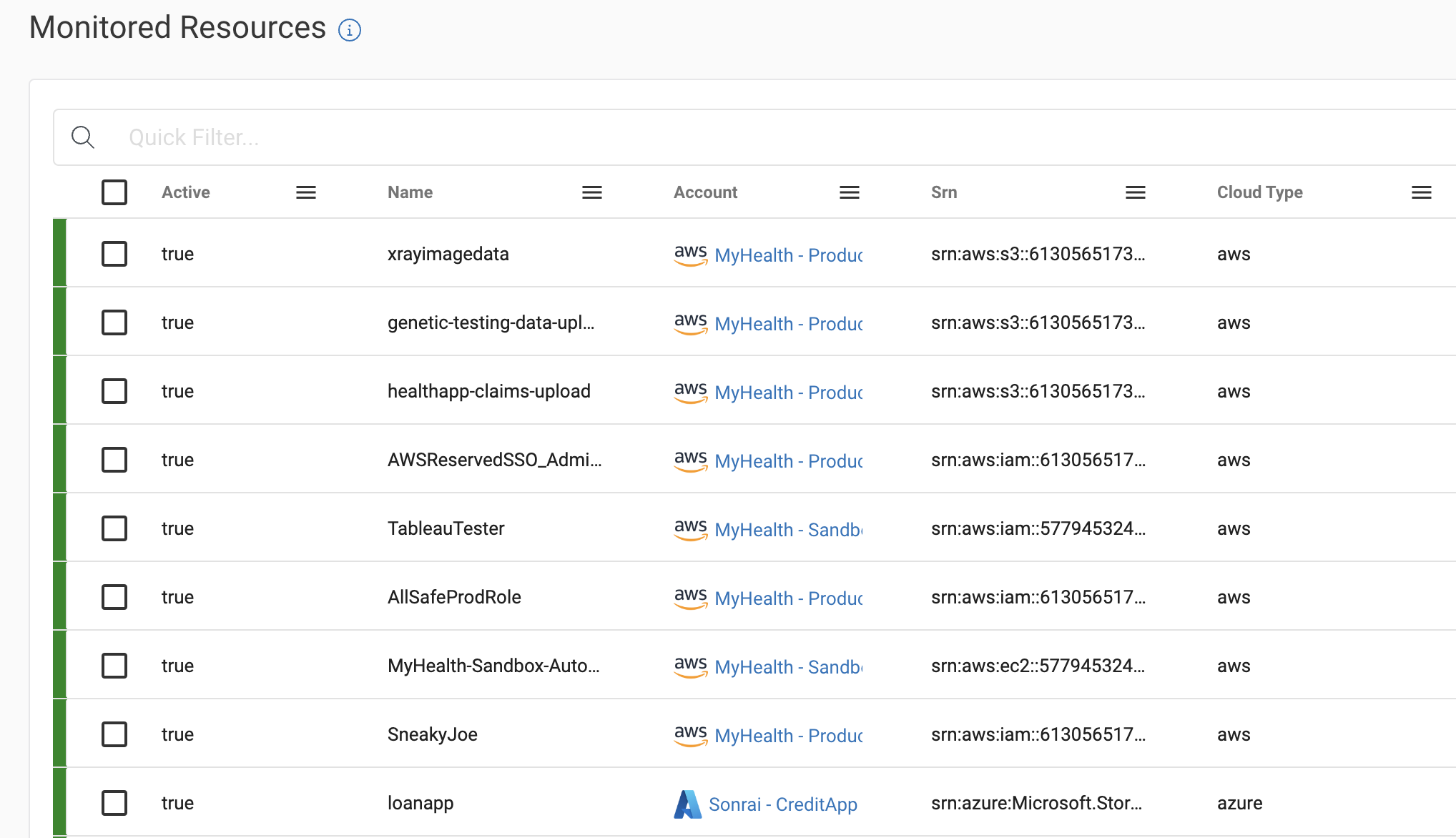
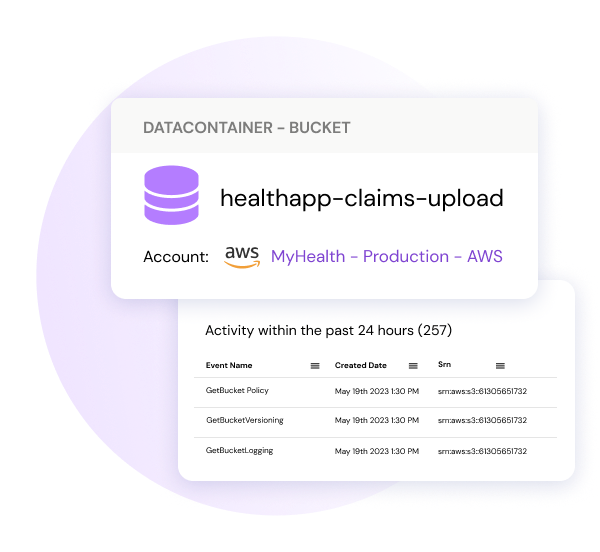
Here you have a view of every resource, datastore, application, or privileged identity that is high-value – determined by your team. These are your crown jewels.
We’ll focus on the ‘xrayimagedata’ bucket in the top row for these use cases. Clicking into the node view of the bucket, we receive a lot of information.
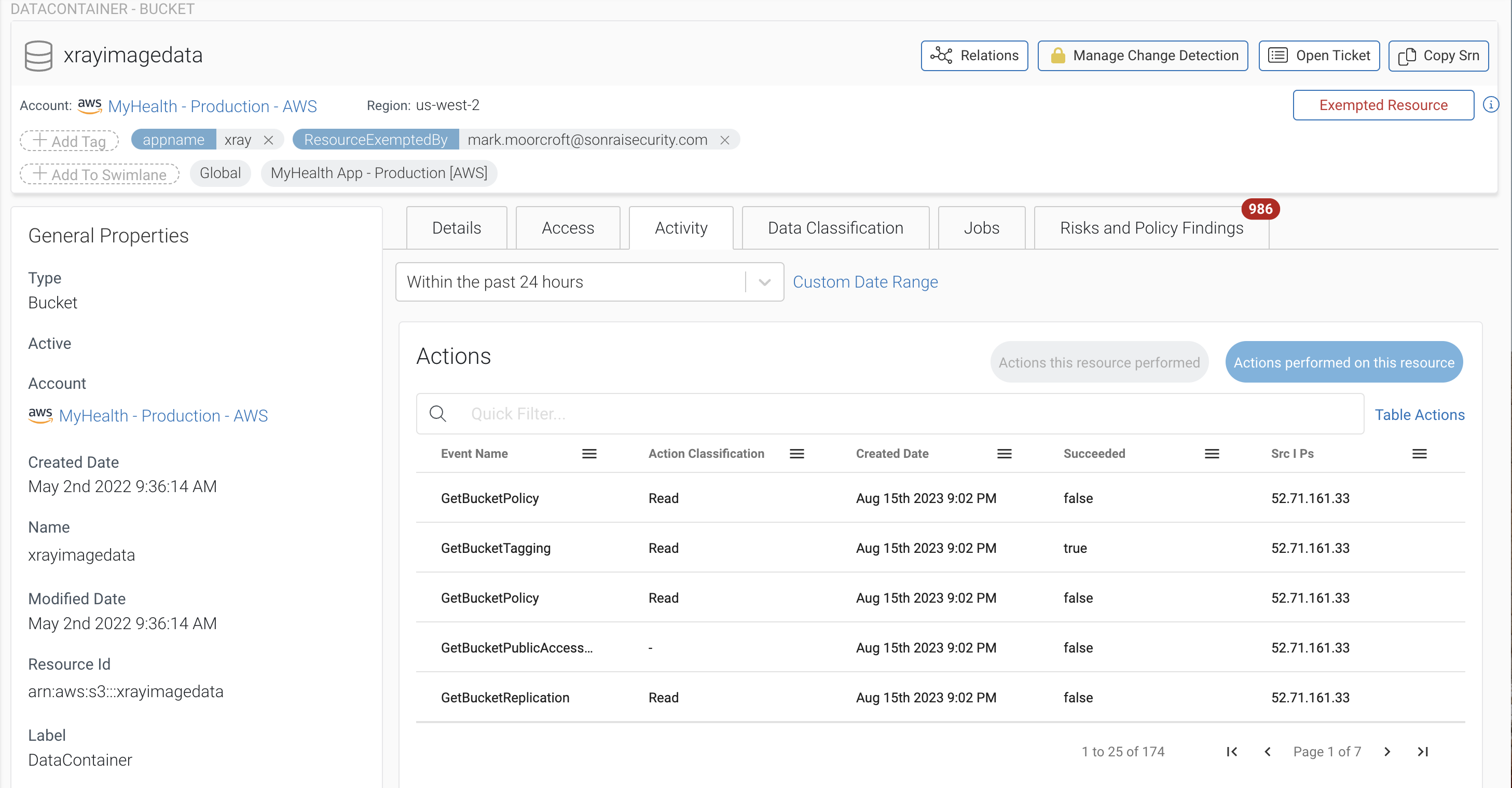
Sonrai’s monitoring offers every detail you need to keep your resources safe including, CloudTrail logs from the past 24 hours detailing all activity, every entity who can presently access the resource in the ‘access’ tab, any policies you have set to the resource, all actions (e.g. read, delete, edit) taken on the resource in the ‘activity’ tab and finally all risks and findings the platform detected.
One thing to note is the policy findings are all possible from the customizable change detection settings. Navigating to the top right ‘Manage Change Detection’ node, we see the following table:
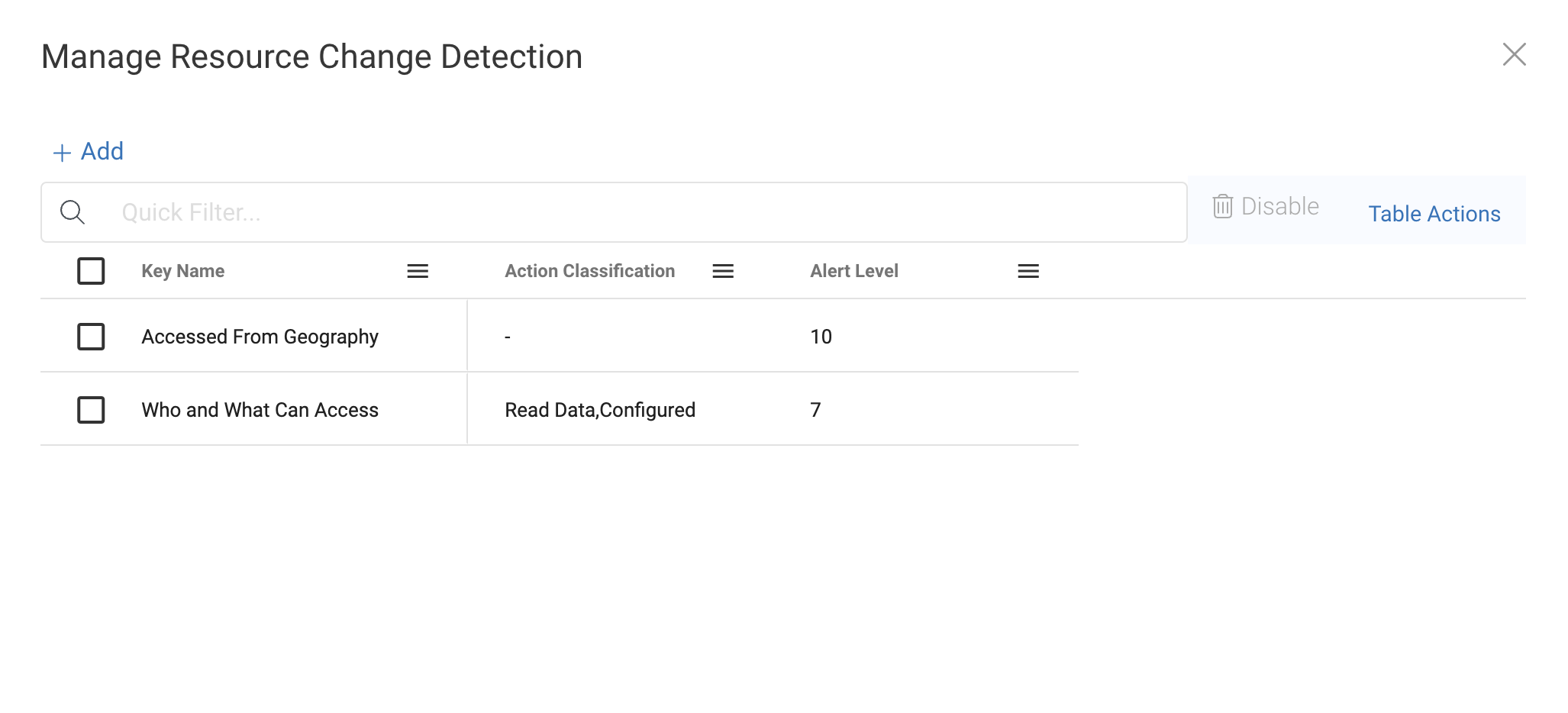
Here, your teams can set exactly what you want to be alerted on. This includes 1) access from a specific geography 2) changes to who and what CAN access and 3) suspicious activity related to who and what DID access a resource.
Each of these selections are customizable to set the alert level from 1-10 and to be notified on specific action classes – meaning, you might not care that a new identity can read data, but you might want to be alerted on a new identity able to delete, or configure a datastore. This level of specificity is only possible with Sonrai.
In our current examples we care about access from a new geographic location and specifically if a new identity can read data or configure a datastore.
In the Risks and Policy Findings we see alerts on both concerns.
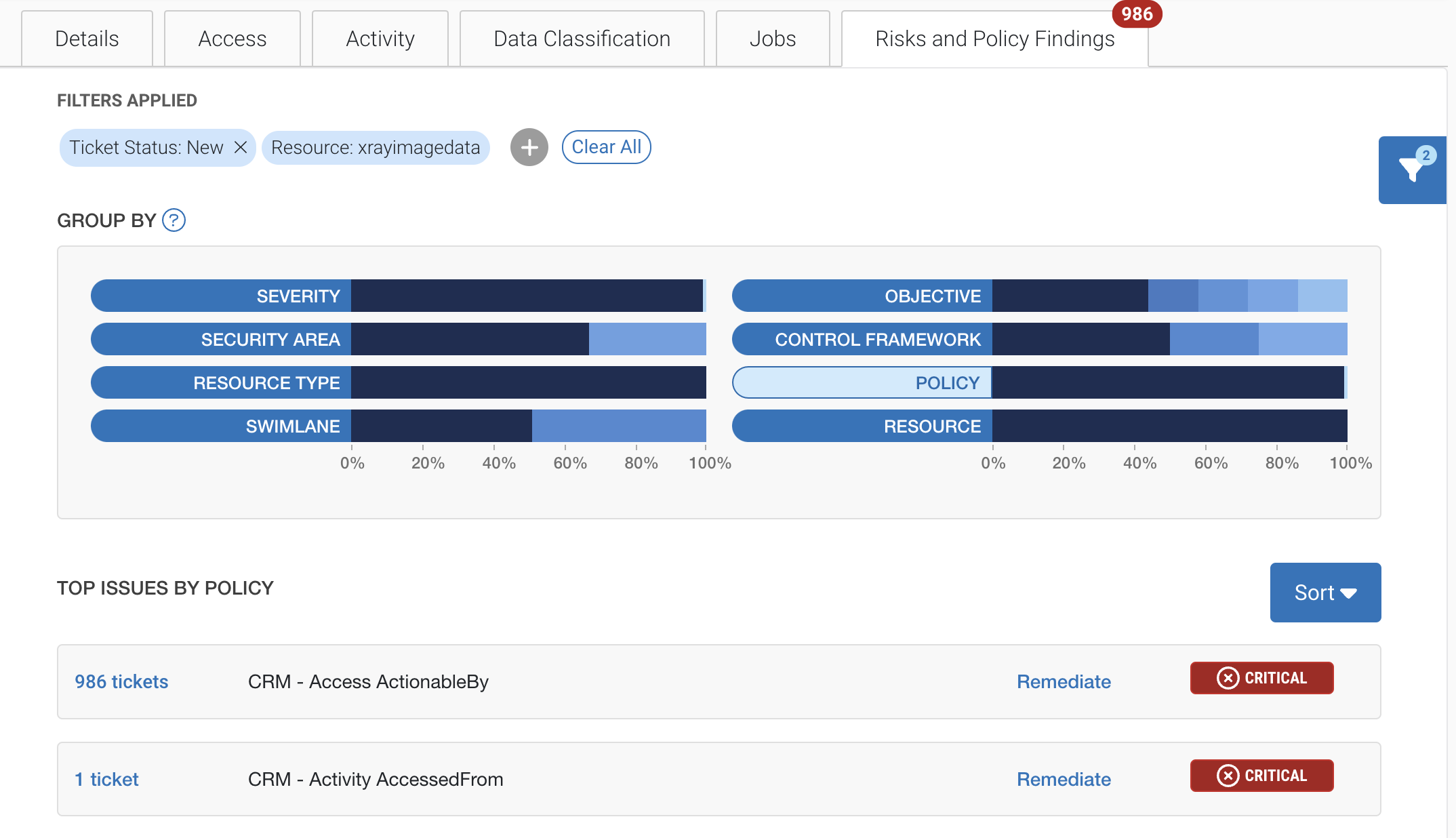
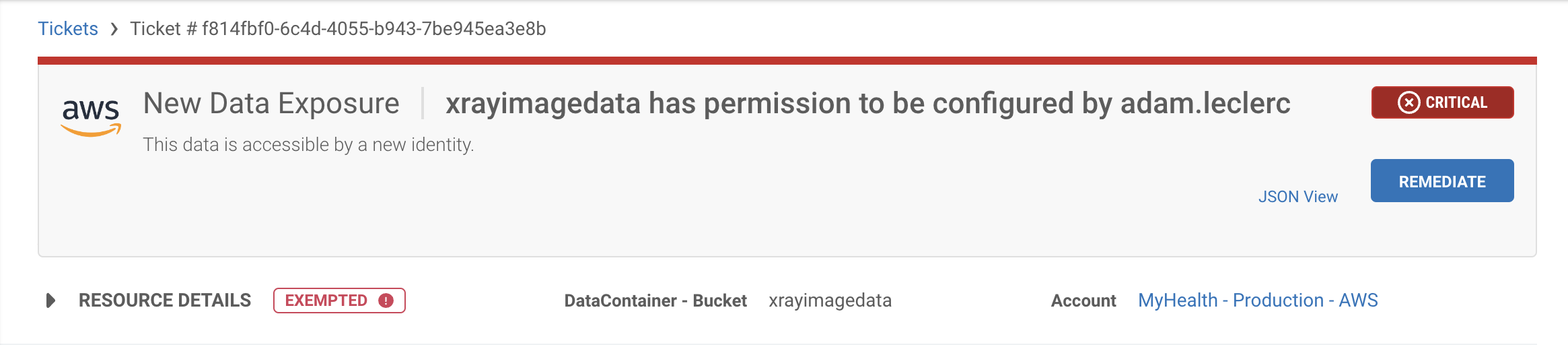
Looking into the alerts on actionable access, we see a user, Adam LeClerc, has new permissions to configure the xrayimagedata bucket (note: this is something we specifically set to be alerted on – down to the exact ‘configure’ action.)
Sonrai offers a detailed view into how this access is possible with an extensive identity and permission chain seen below. In this case, the chain is so long it’s hard to view with 13 different hops getting Adam this configure access to xrayimagedata.
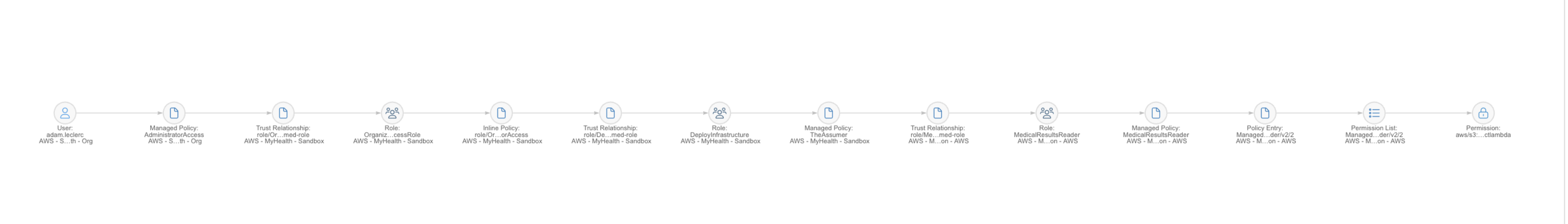
This sort of inherited access is impossible to see in native-cloud tooling or traditional IAM tools. It is the result of many managed policies, trust relationships, and assumed roles. This type of access path is real, frequent, and could be used for malicious activity if Adam’s identity is compromised.
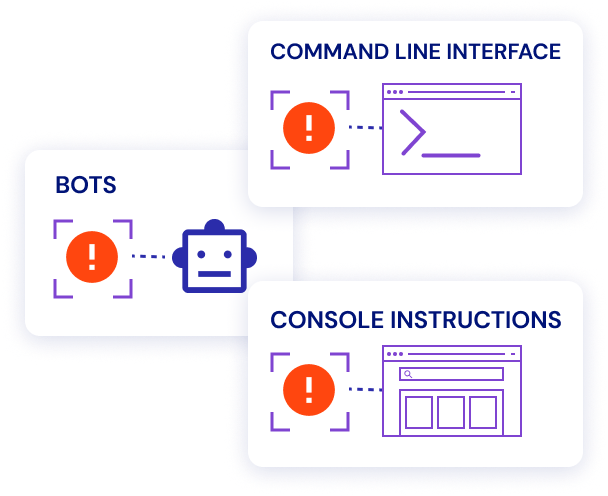
Let’s say your team evaluated the situation and confirmed this change is unauthorized – Sonrai offers remediation steps via prescriptive CLI or Console instructions or automated bot remediation to break the permission chain and secure the bucket. Remediating the alert may have just saved you a future breach, in the case Adam LeClercs’ identity was compromised.
This next use case we navigate back to xrayimagedata’s policy findings. This time let’s take a look at the ticket created because of new geo activity access.
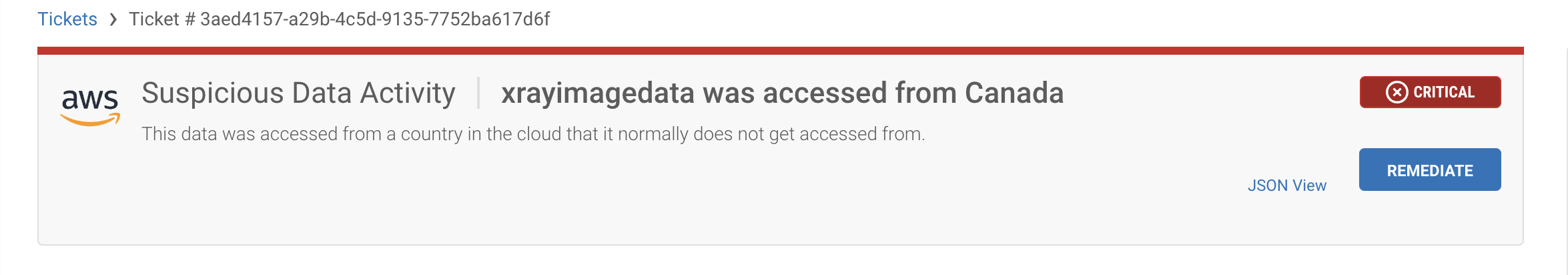
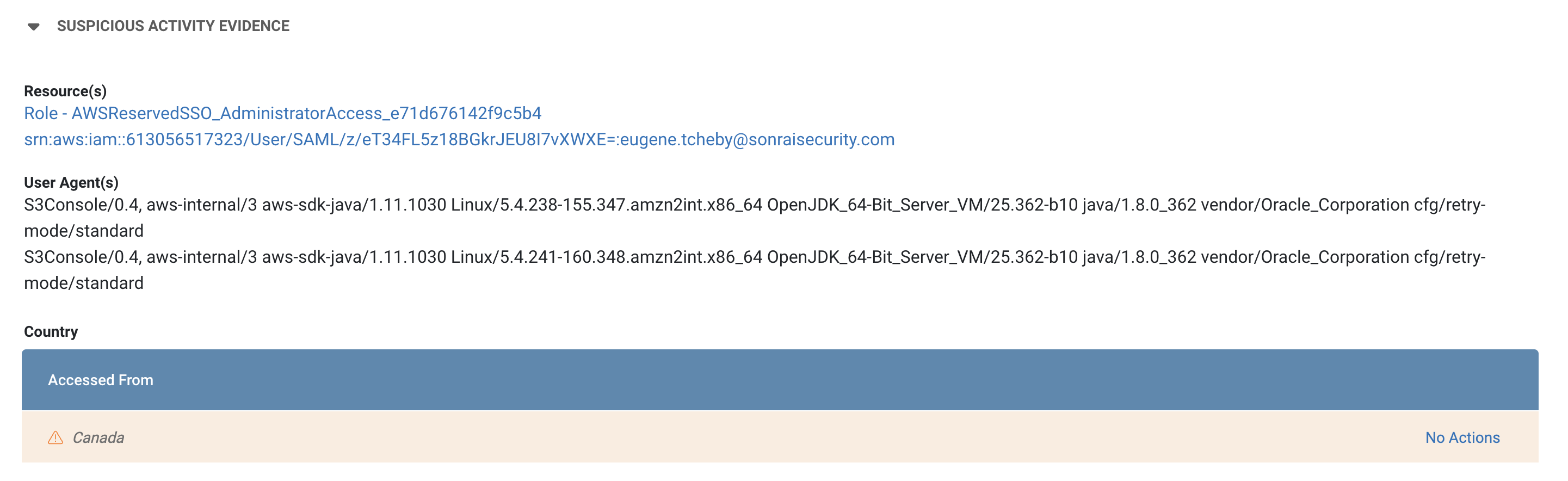
Suspicious data activity was detected due to our customized change detection features requesting alerts when a resource is accessed from a new location. Sonrai offers activity evidence so your teams can investigate the incident. If this access is of concern, remediation options allow manual CLI or Console efforts or bot remediation if you want resources to be automatically isolated in the future.
Detect Cloud Anomalies, Respond to Threats
At the core of the technology, Sonrai’s anomaly detection monitors your data patterns, cloud identities and resources and finds deviations from a secure baseline. What’s special and impactful about it is how specific and advanced that monitoring is. A lot of products can monitor historical identity activity, but what they can’t offer is a way to see permission changes that introduce risk before attackers even have the chance to act on them. This is a proactive cloud security. Plus, it’s not just about the identities – Sonrai has the technology to start at your critical resources and work outwards to see and monitor every entity that has access to it. When these resources are the heart of your business, they deserve every detail of insight so only those who should have access do, and environment compromise is detected immediately with swift remediation.
Now that you’ve seen Sonrai’s anomaly detection, consider exploring our Cloud Detection and Response solution.

FAQs
Cloud anomaly detection improves data security by monitoring access activity to detect unusual behavior that signals new risk or attacker activity.
Cloud anomaly detection use cases include monitoring for changes in who can access a critical resource, if an identity from an unusual geographical location accesses the resource, or changes in an identity’s permissions.
Sonrai’s cloud anomaly detection is different from other solutions on the market due to its ability to monitor at the resource level, detect anomalous changes in who could access resources (not just has already) and Sonrai’s ability to translate permission changes by the specific action class (read, delete, configure, etc.)
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




