Table of Contents

Share this entry

Organizations are adopting the cloud in growing numbers, but with this growth comes unanticipated security challenges unique to the cloud. Microservices and IaC has led to an explosion of machine identities including severless functions, role assignments, virtual machines, APIs, and more. Unfortunately, traditional security tools are ill-equipped to handle this explosion of resource management and, as a result, security risks are exacerbated and cloud access risk runs rampant. This issue begs for a new best practice — hint: it’s CIEM.
Traditional identity solutions struggle to address the cloud’s unique security challenges with its granular and ephemeral nature. Existing cloud security tools address specific aspects of cloud infrastructure security, but they generally lack sufficient identity and access controls. Manual methods to implement least-privilege do not scale, machine identities have no oversight in traditional tools, multicloud access is a blind spot for many, and so on.
Existing security paradigms cannot inherently combat the new wave of identity security. This need has resulted in a new class of tools for Cloud Infrastructure Entitlement Management (CIEM).
What Are CIEM Tools?
CIEM refers to next-generation cloud security technology that grants, resolves, enforces, revokes, and administers access. CIEM tools intend to manage identity entitlements, remediate cloud access risk, and enforce the principle of least privilege across multi-cloud environments to reduce excessive permissions, inherited access, and reveal toxic combinations of permissions.
Why is CIEM Important for Cloud Security?
The cloud attack path works looks different than on-premises. Once an attacker is in your environment — whether via a misconfiguration, vulnerability, or compromised credentials, they do recon to find the right identity with the right permissions assigned to help them execute their plan.
Identities are the entities holding access to all your critical applications and data — making sure there are as few as possible access points — and only highly monitored ones– to those high-value assets only makes sense. CIEM is a critical line of defense in securing your cloud.
Using the identity inventory and each identity’s effective permissions (full scope of cloud entitlements) from a CIEM tool, organizations can now determine what data identities can access, how they can access the data, and what they can potentially do with the data. With this continuous visibility, teams can effectively determine where they have risks and then, in turn, manage the risks to ensure that the cloud environment and the data within it stay secure.

Benefits of CIEM
Scalable Cloud Identity Management
The sheer number of identities in the average enterprise cloud is hard enough to govern sufficiently — and that’s not even considering all the permissions assigned to them. Microservices and IaC lend to creating more and more machine identities, as well as best practices like role-based access.
More identities each having less privilege assigned is generally more secure, but then there are more granular entitlements to manage. This is where manual efforts, traditional IAM tools or PAM alone cannot suffice. CIEM solutions leverage automatic inventorying and effective permissions analytics to keep your records straight 24/7.
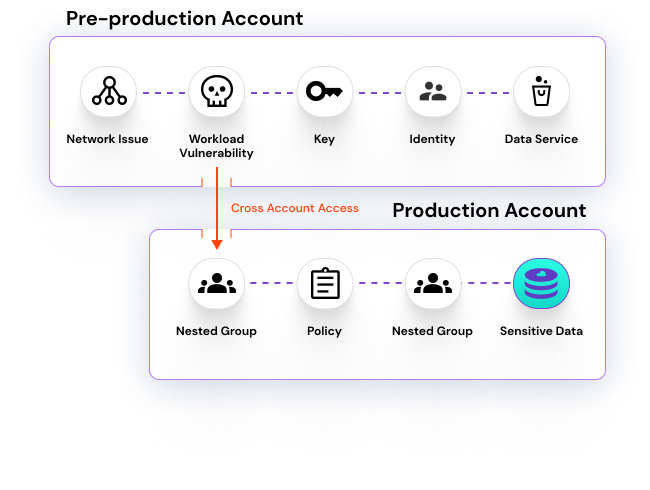
Cross-Cloud & Cross-Account Visibility
Most enterprises are operating out of more than one cloud. A lot of identity solutions cannot track access that works across clouds which can leave dangerous blindspots. Even within the same cloud, it can be difficult to track identities that hold cross-account access via unintentional inheritance or compounding permissions. The right CIEM has the technology to see at the most granular level every permission an identity holds and what that permission allows it to do (e.g. ‘read’, ‘edit’, ‘delete’.)
Governance of Machine Identities
Machine identities significantly outnumber human identities so properly securing them is a great priority. They are often overprivileged and desirable targets to be exploited by attackers. Machine identities are a massive blindspot for traditional IAM or PAM tools. Even cloud service provider native tools like Azure’s Active Directory cannot govern these entities — yet they comprise the foundation of cloud infrastructure.
Consider a developer accounted for in AD, who creates several machine identities during their tenure, but then leaves the company. Their identity is properly governed in AD, but the machine identities tied to them are not tracked and therefore unaccounted for, leaving unnecessary attack surface. CIEMs have visibility into these identities.
Anomaly Detection
CIEM tools will understand an environment’s secure baseline, once it’s been fully inventoried, ‘cleaned up’, and least privileged is enforced. With continuous monitoring of identity permission usage and asset access, unusual behavior or risky changes are detected helping you either fix a change introducing risk, or catch attacker activity.
Checklist to Find the Best CIEM Solution
The following questions will help cloud security teams comprehensively evaluate CIEM solutions.
Account and Entitlements Discovery
- What level of visibility does your CIEM solution provide? (Identity risks, entitlements, trust relationships, specific exposures, etc.)
- What issues can your platform identify? (Excess entitlements, unused entitlements, dormant accounts, over-privileged identities, etc.)
- How customizable is the risk dashboard?
- What identity exposures does it include? (people, non-people, machines, etc.)
- What does it show or visualize risk?
- How extensive is the coverage? (Across cloud, across accounts, etc.)
- What visualization does the solution provide?
- What entitlement changes does it track?
- What events does it create when there is a risk?
- How often does your CIEM update? (continuous, real-time,)
Entitlements Remediation
- What remediation options do your CIEM solutions offer?
- How much automation do your tools provide?
- What mitigation information does the solution provide if remediation is not an option?
- How actionable are the alerts?
- How does it present findings?
- What analysis tools does it provide?
- How much data sharing and context does it offer?
Entitlements Optimization
- How are effective permissions enforced?
- Does it alert to Separation of Duties risks?
- Does it prevent toxic combinations?
- Does it provide visibility into who and what can access your cloud resources?
- Will it replace time-consuming intervention to remediate overly permissive access and entitlements?
Entitlements Protection
- Does your CIEM solution enforce your policies through automation?
- Does it protect access to sensitive data?
- Does it prevent overly permissive or unintended privileged access?
- Does it enable and empower audit and compliance functions?
Entitlements Detection
- What attack detection capabilities does it offer?
- Can it detect atypical behavior?
- How quickly does it alert on detection?
- Do its detection capabilities work across clouds?
CIEM Security Deployment
- What are the deployment requirements?
- What privileges or rights does it require?
- How easy/intuitive is it to deploy?
- How well does it scale across multi-cloud environments?
- Where is the management console located: on-premises or in the cloud?
Best Practices for Implementing CIEM Tools
Start With an Inventory
Knowing what is in your cloud sounds easier than it is. Gone are the days of just human users easily tracked in directories. Now, with microservices and infrastructure represented as code, machine identities are everywhere. New identities come and go every day, and can only be in active for seconds at a time. This can be difficult to inventory.
A CIEM is built to have proper insight into all identities, allowing your organization to get a proper inventory. This is a foundational step as you can only secure what you can see. It is important to highlight IAM tools often are insufficient and leave cloud identity blindspots.
Know Effective Permissions
Effective Permissions refer to the net privilege any given identity has, including every action it can take. Not all privilege is directly assigned in the cloud. Identities can inherit privilege unintentionally or face toxic combinations as privilege is assigned over time and their role changes. This is extremely hard to see to the human eye. Understanding all your identities Effective Permissions is a difficult, but very important step.
CIEM helps by constantly having a clear picture of identity permissions, not just checking every 90 days like on-prem IAM programs enforced. CIEM tools help by seeing what your teams can’t — every possible action any identity can take or data they can access.
Least Privilege
Knowing identity Effective Permissions then allows cloud and security teams to strip away or remediate risky entitlements. A common best practice to follow is a Least Privilege policy. The Principle of Least Privilege enforces that each identity only be granted entitlements it absolutely needs to complete its job — and nothing more. This is not a one-off task, but instead a nonstop journey to maintain, as cloud entitlements are always changing.
Continuous Monitoring
The only way to maintain proper identity security or policies like Least Privilege is with continuous monitoring. Continuous monitoring means your cloud environment, and specifically its identities, their entitlements, and the usage of those entitlements is always monitored. Every 30-90 days is no longer sufficient as things change quickly in the cloud.
If an attacker breached your environment, your teams need the ability to detect if a machine identity modified another identity’s privileges, and then assumed those privileges in effort to move laterally through the environment — a CIEM can do this.
Sonrai is Your CIEM Solution: Manage Thousands of Identities Effectively
The Sonrai Security Platform is an advanced CIEM tool at its core. It provides constant visibility into cloud identities, but more importantly the full extent of their entitlements. Sonrai’s patented identity analytics and cloud graph maps every possible privilege and access point any given identity holds — revealing the ones posing risk to your organization. Enforce Least Privilege, shut down attack paths to data, and continuously monitor for threats with Sonrai’s CIEM solution.
Sonrai is a Gartner recommended CIEM solution.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.







