Table of Contents

Share this entry

Amazon Web Services (AWS), Microsoft Azure, and Google Cloud (GCP) eliminated traditional network boundaries, creating a new landscape to manage. There can be tens of thousands of identities in your cloud environment with the rise of machine identities, microservices, and Infrastructure as Code. The new boundary of cloud security is identity management. With this new perimeter, a new class of solutions is taking over, Cloud Infrastructure Entitlement Management. Let’s explore the basics of CIEM.
What is Cloud Infrastructure Entitlement Management?
Cloud Infrastructure Entitlement Management (CIEM) is cloud identity and access management. It monitors and secures cloud identities and their entitlements. Entitlements are the sum of all privilege assigned to an identity.
As per Gartner , “CIEM offerings are specialized identity-centric SaaS solutions focused on managing cloud risk via administration-time controls for the governance of entitlements in hybrid and multi-cloud IaaS.”
The goal of CIEM security is to answer all basic questions surrounding cloud identity management: what are my identities, what are the end-to-end effective permissions of my identities, and how are my identities using their entitlements?
A CIEM helps secure the middle part of a cloud attack path — any opportunities for privilege escalation, lateral movement, and ultimately unauthorized data access.

CIEM Components and How They Work
- Entitlements visibility: The foundation of CIEM is visibility into all your identity’s entitlements across all accounts, environments, and clouds. They help graph and visualize effective permissions — even those inherited and not directly assigned.
- Rightsizing permissions: With the help of entitlement visibility, a CIEM will detect risky permissions and offer remediations to rightsize permissions like alternative policies or removing toxic permissions.
- Continuous monitoring: Entitlement management solutions monitor all access and permission changes to detect new risks or even alert to possible malicious activity.
- Centralized governance: CIEM offers a centralized cloud entitlement management view across multiple clouds. This breaks down siloes and catches gaps between individual cloud-native identity management.
Why Are CIEM Solutions Necessary To Your Cloud Security Strategy?
Securing identity and access is nothing new for a cybersecurity strategy. However, if you’re in the cloud, CIEM is the way to go. Why’s that?
Privilege functions very differently in the cloud. It is more diverse, with over 40,000+ possible permissions across the major clouds and they can often be inherited in covert ways. Permission or role-chaining allows one identity to inherit privilege not directly assigned by assuming other roles or jumping from one identity to the next.
Not to mention the cloud is run on machine identities. APIs, serverless functions, pieces of compute, and more are all considered identities now. This is a new frontier to secure.
Finally, security responsibility is obscured in the cloud because the people building the cloud and these machine identities (developers, devops, engineers, etc.) are not the same as the people responsible for security (IAM teams, InfoSec, CloudSec, etc.) This makes security a grey area.
All of this makes traditional IAM solutions, like Privileged Access Management or Identity Governance and Administration insufficient for proper access control in the cloud.
What challenges does CIEM address?
Cloud resources are ephemeral and dynamic. Traditional identity and access management (IAM) solutions and practices are designed to protect and control access to conventional static on-premises applications and infrastructure. These solutions aren’t typically well suited for safeguarding highly dynamic, ephemeral cloud infrastructure.
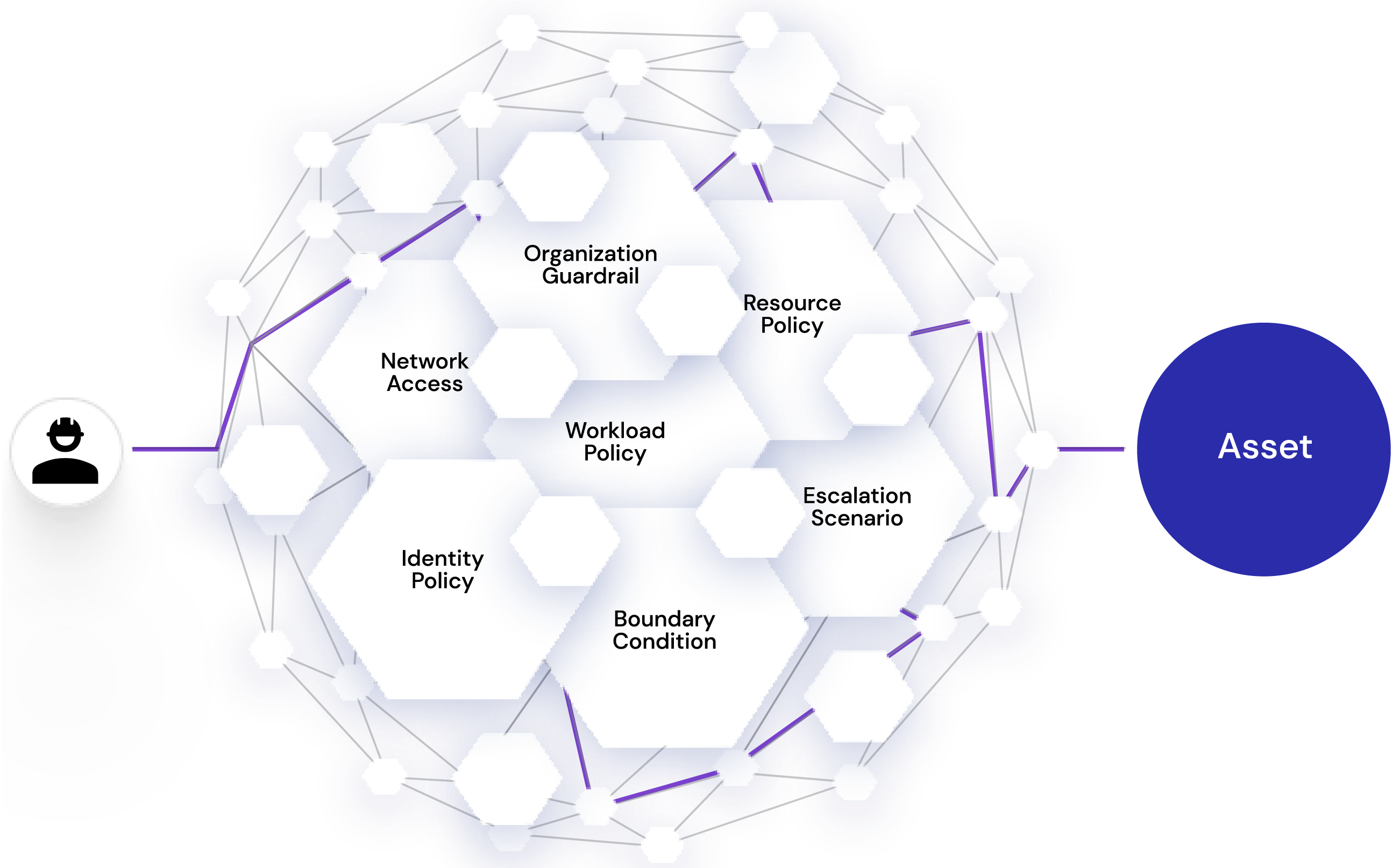
Adding to the complex nature of cloud identity management is another challenge — each cloud provider has its own approach to identity and data security with distinct roles, permission models, tools and terminology, and shared responsibility models. Enterprises utilizing multiple cloud providers are forced to use multiple provider native tools, which can lead to configuration inconsistencies, security gaps, permissions gaps, and risk.
Managing identities and their entitlements can become a resource-intensive, time-consuming, and error-filled function. CIEM addresses this disparate security by offering a central location to manage and view entitlements.
Some more challenges CIEM addresses:
- Excessive privilege
- Toxic combinations of privilege
- Unintended access/ inherited access
- Unused identities/dormant identities
- Privilege escalation and lateral movement
- Third party access
Key Benefits of CIEM
- Effective permissions: one of the best benefits of CIEM is the permission analytics. The solution is able to ‘see’ all privilege — even when it is inherited through several hops away. Manually computing the end result of security guardrails, identity policies, resource policies, group policies, and more, is very difficult. CIEM helps tell you what all your identities can do.
- Easier audits: a good tool should have on-demand querying so your teams have instant insight into all possible access. This is very helpful when preparing or an audit or answering an auditor. You’re able to confirm exactly who and what can access sensitive applications/data.
- Operationalized remediation: when risks are dected, a CIEM offers smooth remediation. Not only do intelligent workflows help route tickets to specific teams responsible, but there are automated remediation options like bots to take efforts off your team.
- Anomaly detection: continuous monitoring of access and permissions allow a CIEM to detect when there’s unusual activity. This could mean a change to an identity’s permissions or an identity accessing something it shouldn’t. You might catch a risk before it becomes an incident.
Why Does Your Organization Need CIEM?
IBM’s X-Force Cloud Threat Landscape Report found overprivileged identities to be in 99% of the breach cases they analyzed.
Cloud permissions are playing a pivotal role in successful breaches. Read our analysis of three major breaches and how cloud permissions were exploited by attackers.
Other tools don’t help secure access. Many enterprises focus on perimeter security like Cloud Security Posture Management (CSPM) and workload protection like CWPP.
68% of the respondents in an ESG study reported using a CSPM, yet the majority still faced security incidents. Trying to ‘keep attackers out’ cannot be the only part of your strategy. CIEM helps protect data for when attackers are already in.
Most enterprises are multicloud. According to Gartner, 81% of organizations report working with two or more public cloud providers. Cloud-native or manual efforts miss access gaps between clouds. A CIEM is the only way to get true visibility.
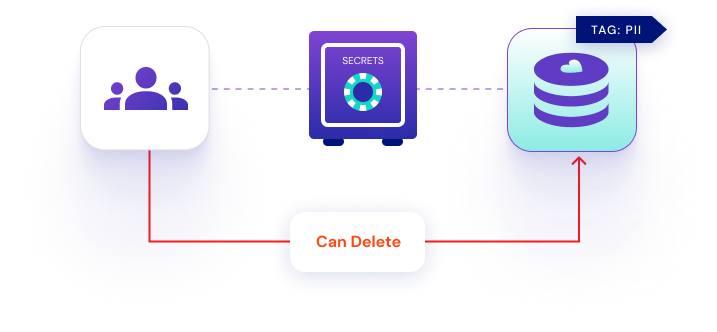
Examples of When to Use CIEM
To help all this new information stick, let’s review some real world use cases.
- An AWS Lambda with cross-account access to sensitive data.
- Excessive permissions: an employee identity with admin privilege they haven’t used in over 90 days.
- An Azure Nested Group: an identity able to use a privilege not directly assigned to it, but inherited via several groups.
- A toxic combination in a multicloud environment.
For more details on real-life CIEM use cases, read our blog, ‘When Would You Use a CIEM?’
How Do I Choose My CIEM Solution?
Every business and organization is unique, so first understanding what your goals and needs are helps you narrow down what you’re looking for. One approach for picking a CIEM solution, is considering if the tool has all the capabilities you need. Some capabilities to consider:
- Automated Identity Inventory: this is the discovery of every and all identities present in your environment.
- Effective Permissions: understanding the true scope of all identities’ abilities, even across-accounts.
- Visualization: an identity graph or analytics is a digestible way to understand your identities and entitlements. See Sonrai’s identity graph here.
- Detection: once your identities and privileges are at a secure baseline, monitoring capabilities can help detect suspicious behavior when an attacker is in your environment.
- Customizable: customizable frameworks and policies so your specific needs are enforced, and customizable remediations like manual or bot-use for when risks are detected.
Get Total Visibility With Sonrai
Sonrai offers a best-of-breed solution to managing identity privilege and access. The patented permission analytics ensures you know every possible action any identity can take. On a nightly basis all attacks paths are calculated so your team can discover and fix pathways to data you didn’t intend for.
Tackle unknown cloud admins, unused identities, excessive privilege, and lateral movement risks with Sonrai’s CIEM solution. Learn more on our solution page.

FAQs
A CIEM should include the following features: entitlement discovery, identity inventory, entitlements optimization, automated remediation, least privilege, audit and compliance, governance.
IAM is identity and access management, and was traditionally an on-premises focused umbrella solution class. Cloud Infrastructure Entitlement Management is dedicated to cloud environments and focuses on computing permissions.
CIEM intends to discover, optimize, and remediate cloud identity entitlements in an effort to secure access to data and applications. CSPM is a monitoring tool used to enforce best practice controls around your cloud and catch misconfigurations.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.







