Table of Contents

Share this entry

Out With Network Security, in with Identity Entitlement Management
The public cloud eliminated traditional network boundaries, so cloud security is based on different strategies, like identity entitlement management. The security boundary of your cloud is your Identities, both person and non-person identities, and they need to be managed accordingly. There can be tens of thousands of non-people identities in your cloud environment, and it is the use cases of these non-people identities make security even more complex.

Identity-based use cases are proliferating dramatically, which brings into question their entitlements. In the cloud, we call these entitlements an Identity’s Effective Permissions, the end-to-end permission of the actions that an Identity can take and the data it can access. CIEM offers the technology to monitor cloud identities and their effective permissions. Gartner explains it this way, “CIEM offerings are specialized identity-centric SaaS solutions focused on managing cloud risk via administration-time controls for the governance of entitlements in hybrid and multi cloud IaaS.”
The goal of CIEM is to define the solutions that answer basic questions surrounding identity: what are my identities, what are my identities’ effective permissions, and within the data context, what data can they access, and what are they doing with the data.
Why Network Security Doesn’t Work in the Cloud
Traditional on-premise identities were stored in a central repository like Active Directory. Entire processes and provisioning defined where the identities were manifest, what groups they were associated with and how they were monitored within the organization. A cycle is developed and maintained for individual identities, and entitlement checks for those identities were performed periodically – maybe every 90 days or once a year. In the cloud world, this approach to Identity governance is not only wrong but dangerous.
There is a fundamental paradigm shift when moving to the cloud, beginning with identity as the boundary. Identity associations are more diverse and widely disseminated across the cloud. And there are just a lot more different groups who have access to the identities in the cloud, such as app teams, DevOps and SecOps, and admins. With all of this activity happening in the cloud, not only are privileges obscured, but they can change quickly and possibly for only short periods of time.
What was a simple model in on-premise identities, even if it wasn’t always easy to manage, is now a complex model in the cloud that is extremely difficult to manage. And the people working in the cloud usually come in with knowledge surrounding only their role, not realizing that there could already be dozens or hundreds of other identities with the same or similar functions.
Organizations need to know what all their identities are, but unfortunately, most struggle to do so. The effective permissions for each and every one of your Identities need to be continuously monitored, not just checked every 90 days or more, and someone needs to be alerted immediately when something changes.
And if you can’t inventory identities and their effective permissions, you can’t have a secure cloud. So the first step toward cloud security is having an inventory of every identity, and CIEM helps that process.
One of the most significant security issues in the cloud is misconfiguration risk; issues like complexity, lack of training for staff responsible for cloud management, lack of visibility, and not enough people to manage security in the cloud. Addressing misconfiguration issues is another area where CIEM adds security through entitlement management.
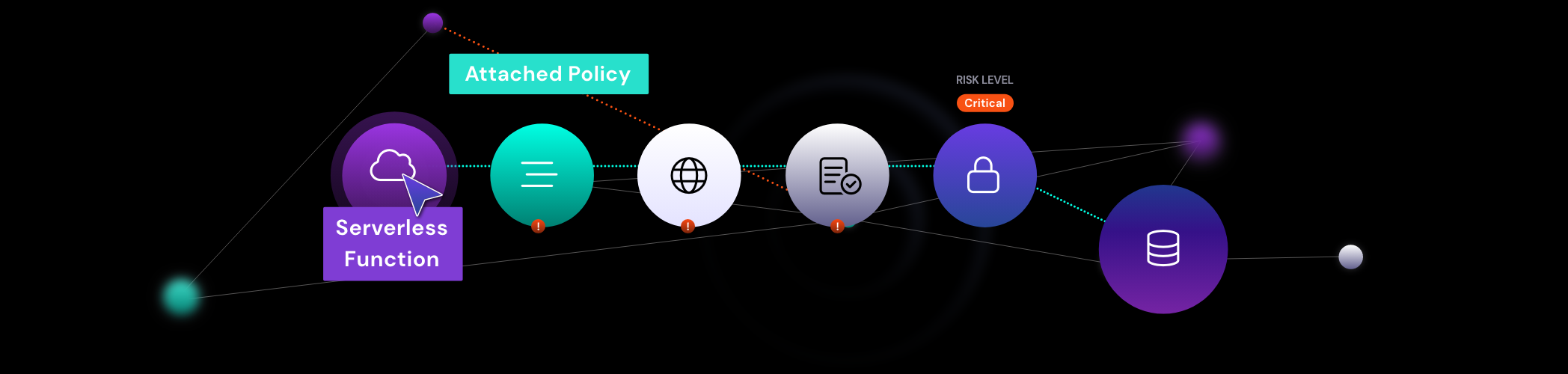
For example, a non-person identity an effective permission of being able to access a sensitive data container, but the identity is not supposed to have this level of permission. This type of misconfiguration is actually quite common, and very concerning. They tend to arise when the full view of the permission is not understood. What might look good on the surface, can actually be a major risk.
How Organizations Use CIEM for Entitlement Management
Discovery and inventory of all the identities in our cloud environment, as well as determining and continuously monitoring their effective permissions, is what stands between good cloud security and serious cyber incidents. CIEM can be used to manage identities in the following ways better:
Separation of Duties. Making sure that permissions are used wisely, i.e., the person who controls the keys to encrypt data can’t decrypt data.

Access Reviews and Monitoring Cloud Service Users. CIEM is used to continuously monitor identities and effective permissions, including whether an entitlement or effective permission had changed.

Designing and Managing Role Assignments. A CIEM monitors the role assignments of each identity and can recognize if a role assignment has been given incorrect permissions or entitlements and correct it.

Identity Confirmation and Oversight. It offers a consolidated view of identity classification and much-needed management of identities.
Sonrai Security’s can help your organization manage cloud security and identities through four main areas:
- Identity Security. This is the heart of the CIEM platform. It offers identity inventory, deep cross-cloud visibility into effective permissions, and continuous monitoring for anomalous behavior and access.
- Data Security. Data is every company’s most valuable asset, and it needs to be protected. Lockdown your data from the inside out and maintain least access. Know where your data is, classify and tag it, who is accessing it, and protect it.
- Intelligent CSPM. This is the foundation of your system, and if the platform is vulnerable, it adds vulnerability to identities and data. Maintain compliance and security posture with platform checks prioritized by context.
- Workload Security. Vulnerability management requires continuous scanning in the cloud, periodic snapshots don’t cut it. Amplify workload vulnerabilities based on blast radius potential.
- Workflow & Automation. Your CIEM needs to scale to your needs and work at the same speed as the cloud. Ensure alert triaging is operationalized by routing them to the right team and prioritizing the most urgent matters.
Keeping your cloud safe requires effective and continuous monitoring of both people and non-people identities in your cloud environment. CIEM offers visibility into entitlements, which lets you manage them more effectively. In the cloud, identities are your boundary, and if you don’t know what your identities are or the effective permissions they are granted, you are leaving the front door open. To learn more about how a CIEM could help your identity entitlement management, see our buyer’s guide.






