Table of Contents

Share this entry
TechTarget’s Enterprise Strategy Group released a new report detailing why proper management of identity and access is critical to reducing cloud security risk. The report includes recent market research data on identity-based cloud risks combined with effective approaches for risk reduction. You can find the full report available here, but for now, we’ll summarize the main findings from the research.

1. The inherent nature of the cloud is leading to identity and entitlement risk.
More and more enterprises migrate to the cloud to reap the benefits of increased agility, scalability, and innovation. Developers rely on microservices and infrastructure as code to build applications, but with this comes an increase in machine identities and a proliferation of entitlements allowing these entities to all communicate. Identities are often overprivileged and given more access than necessary for the sake of ease, but this introduces serious risk.
2. Cloud-based security teams are struggling to manage overly permissive identities.
ESG’s research suggests that managing cloud identities and their entitlements is a top challenge for security teams. Of the respondents from cloud-based organizations, 73% reported that overly permissive service accounts introduce security and compliance risks, and 65% reported concern over developers with highly privileged service accounts due to the risk of credential theft.
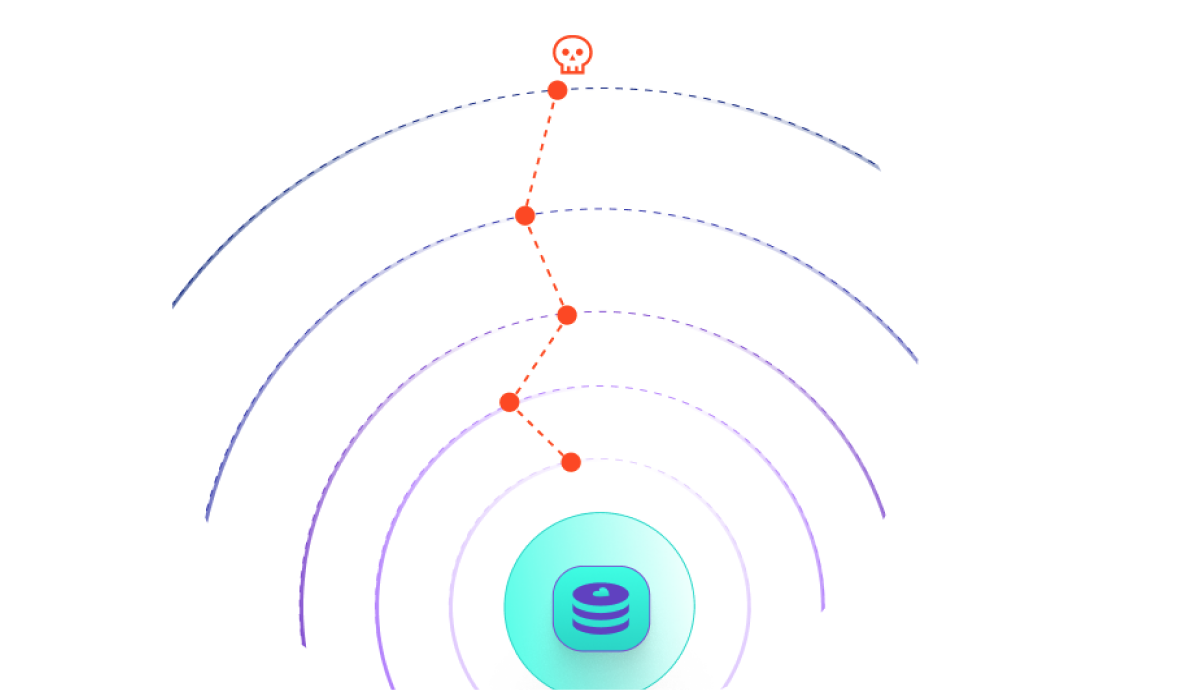
Driving all of this home, the research found that 99% of the organizations who experienced a security breach recognized identity credentials played a role in the breach – with over half of those stating it was a critical role.
Credentials can be a potential way into a cloud environment for attackers, but regardless, once a cloud ‘perimeter’ is breached, it is identities and their permissions that create the opportunities for attackers to move laterally.
3. Insufficient identity and access control leads to data & compliance consequences.
The sheer volume –and resulting complexity – of cloud entitlements make it extremely difficult to have insight into who and what holds access to critical applications, resources, and most importantly data.
One thing all enterprises face is responsibility to meeting compliance and regulatory requirements. Most of these requirements relate back to proper access control and data protection. The result of insufficient insight into identity entitlements is unintended data access and a violation of business or customer privacy.
Read more about audit & compliance in the cloud here.
ESG found just under 40% of respondents failing a compliance audit due to cloud entitlements with unmanaged, unneeded access permissions. Failing audits translates into hefty monetary fines, and more work and time on your internal resources to reach a compliant state.
4. Cloud and traditional tools are failing to address identity and access risks.
Many organizations may feel their cloud is properly secured because they already have IAM solutions in place that worked for them before their migration, or they leverage the cloud-native services offered by AWS, Azure and GCP, or even have implemented a Cloud Security Posture Management tool. The reality is, none of these solutions fully address the access risks we’re discussing.
Traditional IAM solutions were never built to address microservices, infrastructure as code, or machine identities. This results in major blindspots in monitoring or governance efforts. IAM tools were sufficient in monolithic and on-premises environments where security was more cut and dry with a clear perimeter of network controls to protect the environment. Now, there is no clear boundary, and identities are actually the stepping stones attackers leverage to create attack paths. Identity security goes beyond just an inventory of your identities and governance over them. IAM tools do not reveal the potential attack paths to data created from compounding permission.
Cloud Security Posture Management (CSPM) tools serve as an excellent means to uphold platform best practices and ensure all the necessary configurations are in place to properly secure your cloud. This includes checking that logging & encryption are enabled, MFA is enabled, data stores and workloads are not publicly accessible, and more. What these solutions do not address is identity inventorying, insight into entitlements and access, and the risks resulting from these privileges.
68% of the respondents in the study reported robust CSPM capabilities, yet the majority still faced security incidents, often involving identity and access issues. CSPM tools are not enough alone.
5. An inside-out and identity-first cloud security strategy is the path forward
Previously, taking an outside-in approach to security was a sufficient means of securing on-premises infrastructure. This meant securing your perimeter with network controls to then secure your data and identities. The transition to the cloud is calling for a new approach to security – an inside-out one.
This strategy starts at the heart of what’s important to business – critical data and applications, and works outwards to discover every possible attack path created via misconfigured identities, platform controls, and workloads.
This approach also offers a defence in depth plan. Posture management, network controls, and vulnerability management on workloads are a great first line of defence to prevent cloud entry, but they can offer nothing once that perimeter is breached. Identity and access controls are the only way to stop opportunities for lateral movement towards valuable assets.
Enjoyed the summary? You can find the full report created by TechTarget’s Enterprise Strategy Group available here.




