Table of Contents

Share this entry

You can’t wait to buy a Cloud Infrastructure Entitlement Management (CIEM) solution.
Yes, we mean you can’t wait as in time is of the essence and critical threats are imminent, but we’ll leave room for the possibility that maybe you’re chomping at the bit.
No introduction needed here – we’ll let the points speak for themselves. Here’s the five reasons you should prioritize a CIEM solution into your cloud security tool stack ASAP.
5 Reasons You Can’t Wait to Buy a CIEM
1) Identity is the number one attack vector in your cloud.
There are numerous ways an attacker can enter your environment. Traditionally, workload or software vulnerabilities and infrastructure misconfigurations are common entry points, but credential compromise and third-party entry are increasing as root causes to cloud breaches.

Regardless of how an attacker finds their way in – be it a vulnerability, third-party, misconfiguration, or by simply logging in – there is one consistent truth: once they’re in, they use identities, access, and permissions to find their way to what they want.
It’s game over once the perimeter is breached.
All it takes is a single compromised cloud identity for damage to be done. This is because there’s a great chance that single identity offers opportunity for privilege escalation or lateral movement – meaning, the attacker can hop from one identity to the next, or assume roles, all in search of their desired end goal: hijacking your cloud, disrupting a business-critical application or stealing your valuable data.
Why is that? Because contemporary cloud identities are typically overprivileged and organizations are running blind to the unintended privilege identities are inheriting through cloud complexity.
How are permissions and access a part of the attack path?
Below, see a visual displaying how an attacker can leverage cloud identities, IAM policies, and roles, to move from a single compromised serverless function in a Sandbox to a data container in Production. Whether it was a vulnerability on a workload or third-party trust that compromised the serverless function, the path getting an attacker from point A (the function) to point B (access to a data container) abuses one thing: cloud permissions.

The writing is on the wall: it’s the era of identity, access and permissions in cloud security. If you are looking for an efficient way to significantly reduce risk across your cloud, focusing on the vector that makes cloud attacks possible in the first place, is your best bet.
2) The identity problem is pervasive and getting worse.
Buying a CIEM sooner rather than later is in your best interest – let us tell you why.
Cloud identities are proliferating. Infrastructure is built with code. Your cloud is built on machine identities. The average enterprise has 45x more machine identities than human users. The nature of development is fast-paced and continuous to accommodate demanding business innovation, which translates into more and more identities every day. Over half of respondents in the Forrester Opportunity Snapshot reported machine identities as ‘out of control’ in their cloud.
Beyond the nature of how the cloud is built, security best practices like Role-Based Access Control (RBAC) and Least Privilege further exacerbate identity proliferation. Both of these protocols believe in more distributed privilege, and a conservative amount of privilege per identity – meaning, more identities need to be created to execute the necessary work.
While identities are proliferating, their privilege grows excessive too. Identities are frequently overprivileged. In more than 95% of accounts, less than 3% of entitlements are actually used, according to Gartner’s Innovation Insight for Cloud Infrastructure Entitlement Management.
Why is that? To accommodate leeway for testing, or avoid slow request processes, or just create ease down the road, sometimes identities are assigned broader privilege than they really need. Or, less intentionally, the complexity of the cloud leads to identities inheriting privilege they shouldn’t have – and no one knows they have.
The result of all of this is an increased and unnecessary attack surface – and that attack surface is growing every day. The sooner you implement a CIEM solution, the sooner you get the cloud chaos under control and keep it that way.

3) Your current tools are not working – alone.
CSPM/CWPP
A Cloud Security Posture Management tool was all the rage about five years ago. They are foundational solutions to keep your security hygiene intact and ensure all the right configurations are in place. A CSPM tool helps protect against cloud drift and misconfigurations that could leave your ‘platform’ open to attacker entry (e.g. data storage without proper authentication to access it, a publicly accessible port on the internet, etc.)
Cloud Workload Protection Platforms similarly help prevent attacker entry by detecting vulnerabilities on cloud workloads.
These are strong solutions to leverage – but the reality is, no CWPP or CSPM tool is 100% effective. Attackers will and are finding their way into enterprise clouds – in fact, vulnerabilities are frequent (IBM reports a six-fold increase in new cloud vulnerabilities in the past six months), misconfigurations are common, and human will remain susceptible to social engineering (Verizon’s 2023 Data Breach Investigations Report notes 82% of breaches involving human-related factors.)
68% of respondents reported robust CSPM capabilities, yet the majority still faced security incidents, often involving identity and access issues.
The Need to Focus on Identities and Access to Reduce Critical Cloud Security Risk
Once they’re in, it’s game over – unless you’ve built a strategy protecting your identities and their access. CSPM and CWPP tools are not enough to sufficiently protect your business assets and they do nothing for solving the identity and access problem once an attacker is in.
IAM Tools
IAM tools are a broad bucket. Within this falls Identity Governance and Administration (IGA) tools, Privileged Access Management (PAM) tools, and cloud-native services from Cloud Service Providers. The reality is these tools are not built to address cloud-specific identity challenges. They hold limited insight into the true privilege cloud identities hold. This is because in the cloud, privilege is often inherited or the result of complex permission-chains including trust relationships, groups, and conditional access rights.
Traditional solutions can only see directly attached privilege. Additionally, the permissions they can see can be hard to interpret. A CIEM solution is able to translate over 42,000+ unique permissions into categorical action buckets so you know exactly what an identity can do (e.g. ‘read’, ‘write’, ‘edit’, ‘deploy’, etc.)
This lack of insight translates into you not knowing what your identities are truly capable of (you can’t protect what you don’t see!)
Beyond the limited insight into effective permissions, traditional IAM tools are not built to address the inherent nature of the cloud. The cloud is run on microservices, Infrastructure as Code, and ultimately, an army of machine identities with ephemeral activity. They significantly outnumber human users and can only be properly managed by a CIEM tool. There are machine identities present in your cloud that your PAM, IGA, and cloud-native directory do not see.
A Forrester Opportunity Snapshot commissioned by AWS and Sonrai Security found ‘legacy tools that are unable to understand short-lived identities in the cloud’ to be the number one reported challenge cloud-based enterprises faced.
The takeaway? No cloud tool can solve this problem except for the one built to manage dynamic machine identities, short-lived access, and the complexity of cloud permissions – a CIEM.
4) Speaking of tools, a CIEM enhances your current investments.
Most enterprises have already invested in some sort of cloud security whether that be a CSPM tool managing your platform, workload security, or data security solution. Buying a CIEM adds value to those preexisting investments.
The insight into toxic permission-chains that create lateral movement opportunities and attack paths to your most critical assets is context that can help prioritize work across platform, workload, and data security efforts. Think of a CIEM as 1 stone helping to kill 4 birds (identity, data, platform, and workload security) with more accuracy.
When protecting your workloads and applications, patching by CVSS scores is not enough. Likely, your teams face hundreds of 9.8 rated vulnerabilities – how does this help alert fatigue? With a CIEM that rates severity based upon the violation itself, the sensitivity of the environment it’s in (sandbox vs prod), and how sensitive the data is that is tied to the alert, your teams have more granular prioritization.
Sonrai gives us insight into effective permission mapping, Separation Of Duties and privilege escalation risks with recommendations on remediation steps. Give us context on cloud vulnerabilities and misconfigurations.
G2 Reviews
The same logic applies to a CSPM alert – consider an open port or publicly accessible object storage. Knowing when the alert leads to a deadend in a testing environment with zero sensitive data vs. the alert involves a permission-chain that somehow leads to a production account where your customer credit cards are stored is critical context.
Knowing which security issues have critical business impact (tie back to your sensitive data, applications, and environments) informs your current solutions with prioritization criteria. Investing in a CIEM addresses the identity management and access control use case AND works with your preexisting toolstack.
5) Your current operations and workflows are not efficient enough.
Every security and cloud team can benefit from saving time and resources, increased efficiency, and more organization. A CIEM brings all three.
A CIEM can provide insight into root causes creating broad problems across your estate. For example, detecting unused or abandoned identities in your cloud. Tackling these unused identities by removing them has massive trickle down effects in reducing risk. In the average Sonrai customer environment, about 25% of identities are unused. About 35% of those unused identities are actually third-parties. If you remove those identities, over a quarter of lateral movement risk goes away – this translates into closed tickets and alerts, just by removing one identity. Talk about efficient risk reduction and a bang for your buck.
A big pain point in managing security is often those creating identities (interpret: creating new risks) are not the same people responsible for managing security. This silo creates gaps where incidents and best practices can slip through the cracks. This is especially true in the cloud. Developers and DevOps are creating identities and managing entitlements, but they are not responsible for auditing or securing them.
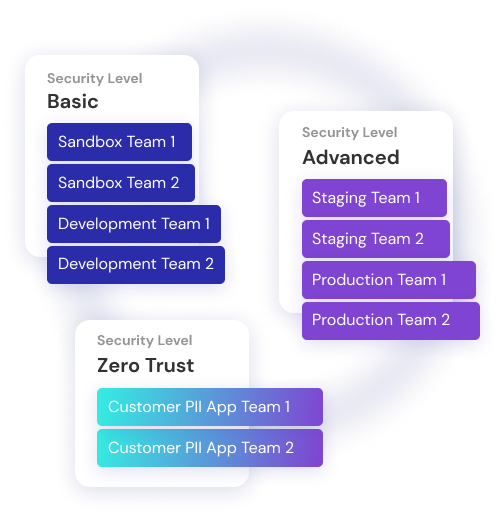
A CIEM addresses this problem with intelligent workflows and automation. Enterprises can be organized by accounts, projects, environments and teams. Alerts are routed directly to the people best suited to address them. This type of on-demand workflow allows developers to double check if what they just deployed actually worked how they imagined it, or if it created any new issues.
Cloud Infrastructure Entitlement Management solutions leverage automation to make your workflows and remediation efforts more efficient and operationalized. Whether it’s finding root cause issues and prioritizing the most pressing risks, or organizing remediation workflows, the end result is a more efficient operation for your teams.
Sonrai offers full visibility into effective permissions and the identity chain – giving my team value insight to identify, root cause and remediate identity risks. The tool has enabled us to identify weaknesses in our access model via continuous monitoring and insights to help us secure our cloud environment.
G2 Reviews
Feel Good BONUS: It is achievable to properly secure cloud identities.
Working in cybersecurity can often feel as if you’ve got a hovering storm cloud following you around. There’s a lot of talk about risks, concerns, alerts, issues, penalties, and security breaches – but this doesn’t need to end that way.
Implementing a CIEM is an achievable way to tackle so many of the challenges cloud and security practitioners face. Gaps in identity inventory, lack of permission insight, manual or inefficient processes, lack of scalability, and insufficient access controls CAN all be solved.
A CIEM offers you visibility into who is truly in your cloud, the prioritization of risks based on how they tie back to your most critical assets, and a way to operationalize your identity and access management – in a way that is built for the cloud and unifies your teams. Learn about Sonrai CIEM below:

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




