Table of Contents

Share this entry

Everyone’s goal is the same: protecting enterprise data and resources from malicious attack or exposure. The most efficient way to accomplish that is by managing digital identities and their access rights. Identity security is a broad umbrella term with many solutions in the market.
In this blog, we’ll detail two specific solutions – Identity Governance and Administration and Cloud Infrastructure Entitlement Management and how CIEM vs IGA compare in the overall mission of reducing access risk and protecting businesses.

What is IGA (Identity Governance and Administration)?
IGA tools are policy-based orchestrations of digital identity governance and identity administration. They help security administrators track user access, enforce appropriate access, and streamline the management of permissions, access, and policies. This all helps to protect business assets and inform business access reviews or audits in a more automated fashion.
Initially, they emerged in response to new compliance regulations like Sarbanes-Oxley Act (SOX) and the Health Insurance Portability and Accountability Act (HIPAA.) Organizations needed more transparency into digital identities and their access rights – plus, a better way to automate user provisioning and deprovisioning throughout the entire identity lifecycle.
How does IGA Work?
An IGA tool will integrate with identity directories or internal HR systems – anything that includes identity information like login credentials, contact information, roles, access, etc. – and scans a business environment to gain a sense of present access rights and analyzes user activity. Security admins review this information to certify appropriate or harmful access.
An IGA tool becomes the authoritative source of all things digital identity including roles, access, login credentials and employee contact information and ensures that the right entities have the right access rights to applications, data, or resources.
Advantages of IGA
Simplified identity lifecycle management
Employees come and go, or transition internally at companies – all of this affects their access rights. IGA helps automate identity lifecycle management, relieving manual efforts on Security Admins. These tools have a clear picture of who should, shouldn’t, and can have access to what, making provisioning and deprovisioning access easier.
Logging and reporting for compliance
Logging of user activity helps Admins review what is happening in an environment and detect risks. IGA tools come with easy and centralized reporting streamlining audit processes for compliance regulations.
Scalability for enterprise
Managing digital identities across an entire enterprise is a difficult task to address manually. IGA tools offer a scalable way to track identity governance at an enterprise volume by centralizing where approval processes happen. IGA tools are a great option for managing access to operating systems in on-prem environments.
Drawbacks of IGA
IGA in the Cloud
Identity Governance and Administration solutions do not hold up well in the public cloud. In the public cloud, identity and permissions function more like components of infrastructure rather than single users. Firstly, identities are most often not human, but instead machine identities like roles, service principals, serverless functions, APIs, and more.
These identities are ephemeral and dynamic by nature, sometimes only being ‘in use’ for seconds at a time. IGA tools inherently cannot manage machine identities – especially in the case of roles being accessible by non human entities. This leaves a major gap as machine identities significantly outnumber humans in the cloud.
Beyond just identities themselves, permissions are different in the public cloud. Privilege is what connects everything back to critical resources, applications, and data. There is no network forcefield creating barriers to entry, so there is greater emphasis on securing identity privilege.
IGA tools do not have command into the scope of permissions in the public cloud. That is because they can typically only track directly assigned permissions. However, in the public cloud, most identities hold privileges that were never intended.
This is because identities can move laterally hopping from one identity to the next to assume privileges, or inherit privileges in covert ways via groups, trust relationships, conditional rights, and more. It’s all very complex, but the end result is attack paths to data often unseen to IAM tools, IGA tools, or human eyes.
A real-world example illustrating this gap in insight is an IGA tool that appropriately offboarded a user from Azure Active Directory, yet information on that identity still present in AWS Identity Center – information sitting around able to be leveraged by an attacker. An IGA tool does not have the full scope of insight needed to confirm all traces of a cloud identity are removed.

IGA tools give a great picture of what should be the case regarding identity access – but do not have insight into whether that authoritative stance is actually the case.
All of this begs for a solution filling the gaps in public cloud identity and permission management.

CIEM: Cloud Infrastructure Entitlement Management
What is CIEM?
Cloud Infrastructure Entitlements Management solutions emerged to secure public cloud identities by discovering, rightsizing, and enforcing secure cloud entitlements.
CIEM tools inventory all identities – machine and human – and compute the effective permissions of every identity. That is, the true scope of privilege any given identity holds, no matter how many degrees of separation away the identity inherited that privilege.
How CIEM works
CIEM works by inventorying all identities, computing their effective permissions, detecting risky combinations of permissions creating unintended access paths to data, applications, and resources, and then remediating them automatically or via actionable recommendations.
Capabilities
CIEMs offer the following features:
- Continuous identity and entitlements inventory
- Identity and entitlements graphing and visualization
- Activity and access monitoring
- Effective Permission modeling
- Risk identification, prioritization and remediation
- Cross cloud and cross account privilege discovery
- Least Privilege enforcement
- Access anomaly detection
Benefits of CIEM
Cloud Infrastructure Entitlements Management come with great benefits – the first, being that they are inherently built for cloud infrastructure.
As previously mentioned, cloud environments are dynamic and code is ephemeral. CIEM tools are built to accommodate microservices, IaC, and serious identity proliferation. This assures teams have insight into everything in their cloud and every type of identity.
Regarding entitlement management – the right cloud security platform will have the permission analytics to compute the effective permissions of every identity. This ensures a CIEM will pick up on the potentially risky privileges that were never directly assigned to an identity.
There are a number of identity risks present in the cloud from lateral movement opportunities, to unused or orphaned identities, to vulnerable access keys and credentials. CIEM protects against these cloud-specific identity risks.
Finally, CIEM offers continuous protection. Continuous monitoring means you always have an up-to-date picture of who is in your environment and what they can access, and any anomalous activity is detected quickly so risk can be addressed immediately.
CIEM Use Cases
Consider the following real-world use cases a CIEM could detect, secure, or prevent:
- An AWS Lambda in a Dev environment with cross-account access to sensitive data in Prod.
- Excessive permissions: an identity with admin privilege they haven’t used in over 90 days.
- An Azure Nested Group: an identity able to access a permission not directly assigned to it, but inherited via several groups.
- A toxic combination in a multicloud environment allowing an identity to create a new function, pass a role to it, and invoke it.
For more details on real-life CIEM use cases, read our blog, ‘When Would You Use a CIEM?’
Key Differences Between CIEM vs IGA
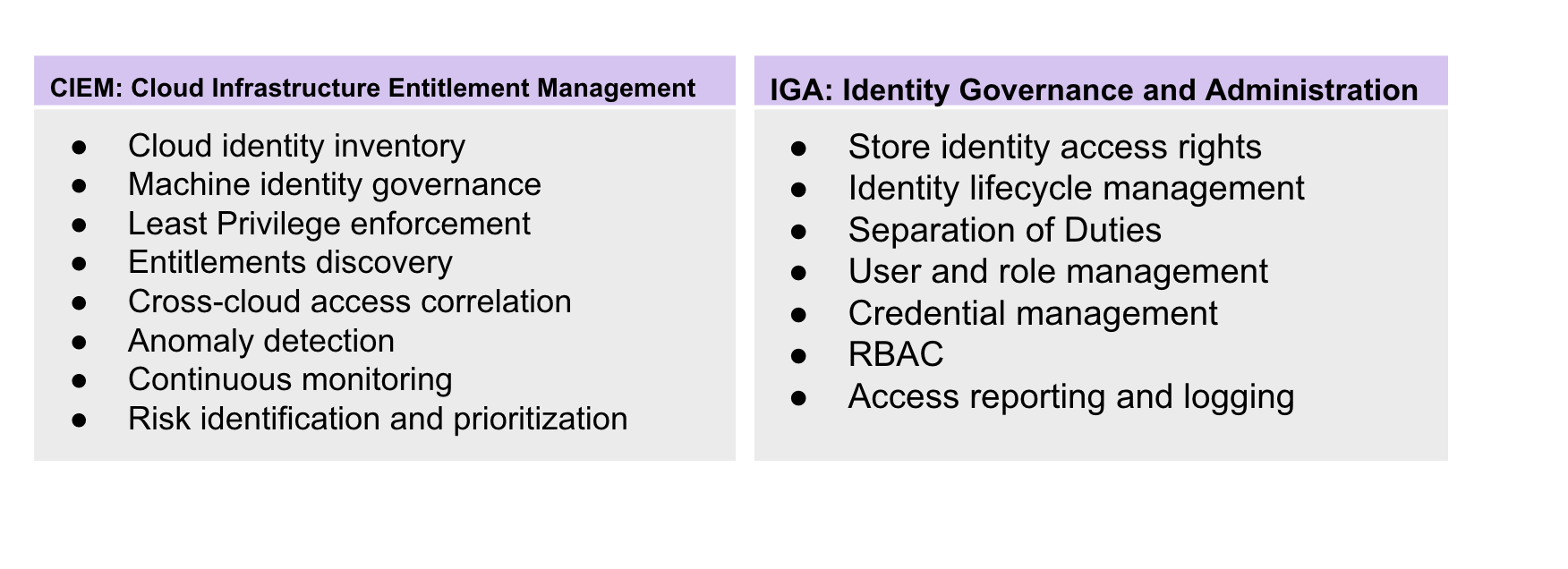
IGA and CIEM tools were built to do different things, yet these identity solutions are often conflated or viewed from the standpoint of picking one over the other. Some of their greatest differences include:
Their environment: IGA tools were built for on-prem infrastructure and are mainly used by IT and security admin professionals. They offer more static coverage, as opposed to CIEMs dynamic and continuous coverage that was built for the public cloud.
The scope of coverage: IGA tools are great for tracking human digital identities, but do not have the same ability to sufficiently govern machine identities in public cloud. CIEM was built for the public cloud – where microservices, IaC, and machine identities are the foundation of operations.
Their purpose: IGA is intended to centralize and automate the orchestration of identity governance and lifecycle management. CIEM is built to secure enterprise assets by inventorying public cloud identities and analyzing their entitlements to detect risky access and then remediate toxic permissions.
These two solutions do not need to compete with CIEM vs IGA, instead, they can actually work together to better secure your business.
How Do They Complement Each Other?
If your business operates solely with legacy infrastructure, IGA is your option. However if your business is in the public cloud at all, leveraging a CIEM is critical. A CIEM will actually better inform your IGA tool by detecting entitlements risks and policy violations an IGA tool would miss. This then sends over remediation insights and recommendations to implement.
IGA intends to be the centralized go-to place for identity access best practice (i.e. who should and shouldn’t hold access.) A CIEM tool gives a continuous and accurate picture of public cloud access and permissions – this insight in combination with IGA, leaves you with all your bases covered. IGA alone is not enough if you are in the public cloud.
Consider the following use case involving both tools: Your IAM team uses an IGA tool to deprovision all access for an identity and remove them from directories upon their departure. You think all traces of access and information are clear, but there are lingering concerns. The team can use a CIEM (like Sonrai) to query for any given identity name, any labels like ‘admin’ or ‘non human’ and any resources or assets you want to ensure cannot be accessed anymore. This gives teams a chance to confirm that what they intended to do with an IGA tool actually happened.
Identity Solutions Built for the Cloud
Identity Governance and Administration tools serve a great purpose in lifecycle management and defining who should and shouldn’t have access in an organization. However, that skill set does not translate entirely to the public cloud. Instead, organizations can leverage a CIEM tool to fill the security gaps left by an IGA tool, strengthening your overall identity.
Sonrai Security aims to eliminate any blindspots in access to cloud assets by identities. The patented analytics model can compute every possible permission accessible to all identities whether directly assigned or inherited indirectly via groups, policies, trust relationships and more. The end result is a more accurate picture of who can access business critical resources and discovering access risks with prompt remediation.
Explore Sonrai’s CIEM Solution.
FAQs
IGA tools are best for on-prem environments, managing access for human users, and for identity lifecycle management, whereas CIEM is best for cloud environments, managing machine identities, and securing cloud entitlements.
CIEM addresses several challenges or gaps an IGA tool may leave including, the lack of visibility into machine identities, cross-cloud access, and lateral movement opportunities.
Sonrai offers the capabilities of an IGA tool, but with the added benefit of CIEM and patented identity and permission analytics.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




