Table of Contents

Share this entry

TikTok, a short-form video hosting service owned by Chinese company ByteDance, is no stranger to controversy. Unfortunately, the social media giant finds itself in the news once again because of an alleged data breach. On Monday, several cybersecurity analysts tweeted about the discovery of what was purportedly an insecure server that allows unauthorized access to TikTok’s storage. Evidently, the server allowed access to up to two billion users’ data.
The conversational alleged data breach is highlighted by one user, BlueHornet|AgaisntTheWest, who tweeted the following:
“Who would have thought that @TikTok would decide to store all their internal backend source code on one Alibaba Cloud instance using a trashy password?”
With others claiming to find TikTok user data being sold online. Cybersecurity analyst and security researcher Dominic Alvieri, shared an image of the data set for sale.
Recently, TikTok’s Chief of Security stepped down, while the business started moving American user data over to Oracle Cloud to defend against allegations that Chinese employees were accessing American user data.
Alleged TikTok data leak for sale on the dark web with access via backdoor script.@tiktok_us #cybersecurity #infosec #TikTok pic.twitter.com/oYjJgEWCwR
— Dominic Alvieri (@AlvieriD) September 6, 2022
Only days earlier, Microsoft Corp. said it had found a “high-severity vulnerability” in TikTok’s Android application, “which would have allowed attackers to compromise users’ accounts with a single click.”
The vulnerability identified by Microsoft is a narrower issue that could have affected mobile phones running Android. A TikTok spokesperson said the company had responded quickly to Microsoft’s findings and fixed the security flaw, which was found “in some older versions of the Android app.”
Reps responded to this new security incident by denying the allegations. A spokesperson stated, “the claims of a breach discovered over the weekend were incorrect. Our security team investigated this statement and determined that the code in question is completely unrelated to TikTok’s backend source code.”
This is so far pretty inconclusive; some data matches production info, albeit publicly accessible info. Some data is junk, but it could be non-production or test data. It's a bit of a mixed bag so far.
— Troy Hunt (@troyhunt) September 5, 2022
An Australian web security consultant and creator of the haveibeenpwned data breach site, Troy Hunt, went through some of the data samples listed in the leaked files and found matches between user profiles and videos posted under those IDs. He found details included in the leak were “publicly accessible data that could have been constructed without breach.”
Mr. Hunt expressed concern that the breach data is inconclusive, stating, “this is so far pretty inconclusive; some data matches production info, albeit publicly accessible info. Some data is junk, but it could be non-production or test data,” per his Twitter. “It’s a bit of a mixed bag so far.”
While the controversy continues, the alleged TikTok data breach clearly highlights the concerns of managing data in the public cloud. Whether it’s Google Cloud, Alibaba, Oracle, or any of the other major cloud providers, TikTok appears to have the same cloud strategy as many global organizations.
TikTok’s team is very public with their cloud security and governance strategy working towards better data governance and protection of US data. As recently as July 17, you can read from Albert Calamug, U.S. Security Public Policy of TikTok, highlights of working with Oracle on several measures to better safeguard their app, systems, and the security of US user data. This commitment ‘to a process of continuous innovation and improvement in our user experience and safety controls’ is not much different than those of other global cloud organizations. So what is the shared challenge CISOs of organizations face today? Well it all starts with understanding who is responsible for a data breach.

Who is responsible when a data breach occurs?
Gartner Research predicted through 2022, at least 95% of cloud security failures would be the customer’s fault, and TikTok, just like any other business, could have fallen prey to the statistic. This story exemplifies the confusion between who is actually at fault when it comes to cloud breaches quite well. The major cloud providers, like AWS, Azure, GCP, and Oracle operate on a Shared Responsibility Model.
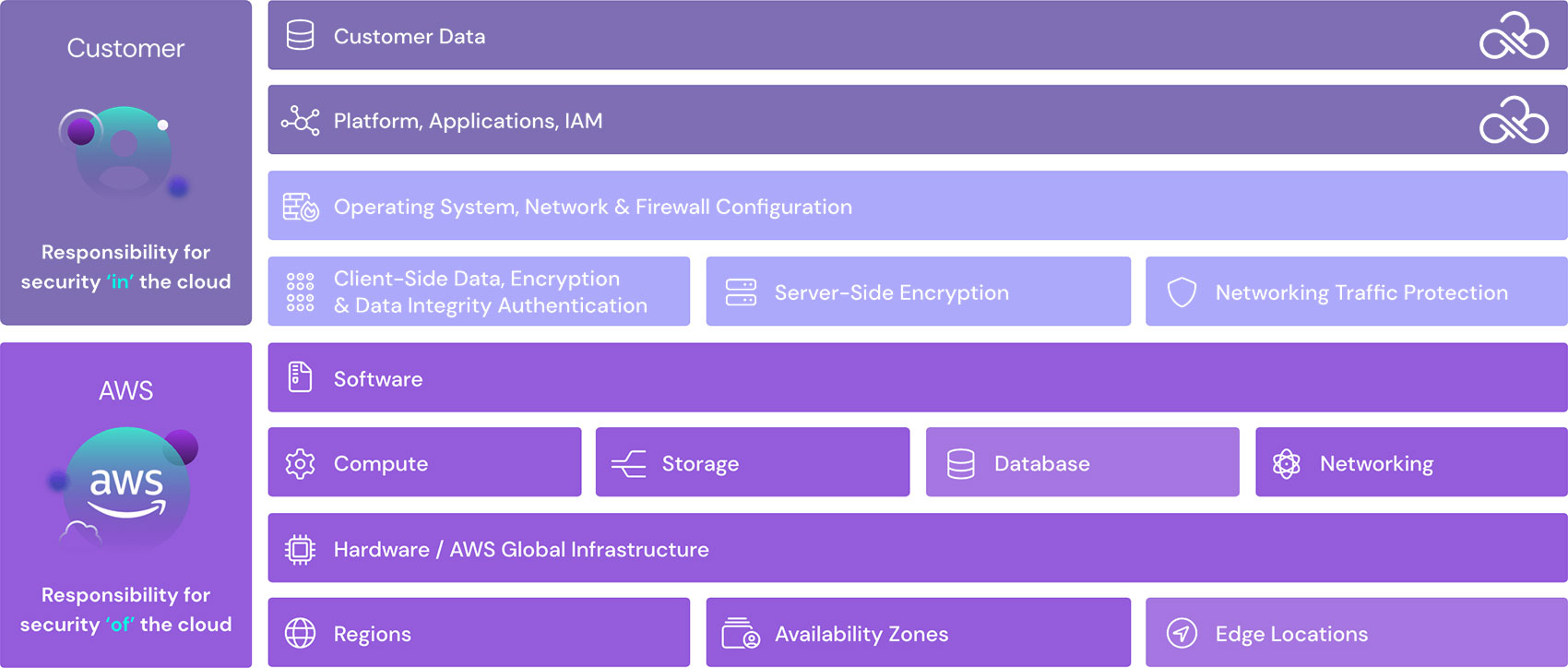
The model details that cloud service providers are responsible for the security ‘of’ the cloud, like basic infrastructure, while customers must protect everything ‘in’ the cloud – like data, identities, and basic configurations. Just simply being in the cloud does not guarantee protection.
The organizations themselves, data owners, are held responsible for data security. For this reason, they are usually considered liable for breaches, even under a shared responsibility model. There may be proof that the data holder had compromised its own security by implementing a faulty update or giving a third party excessive access – for example, the engineer whose tinkering left data exposed.
When it comes to cloud security breaches, most examples reveal that those storing data in the cloud are the most at-risk. Usually, investigators rule the data owner –the organization– to be at fault. Most companies now have data security policies and procedures in place. The mistake many make is that these on-prem approaches do not extend to the cloud.
Defense in depth was dominated by network controls and they rely on traditional network security controls. This dependence to manage the cloud as a traditional environment is a huge mistake in cloud security strategies. The foundation of information security in the public cloud should focus on identity security that controls access to cloud resources and data. Security professionals recognize that “identity is the new perimeter” for securing data in public clouds, and consequently, proper identity security is crucial to managing access-related errors.
Each machine, server, user, VM and piece of compute can carry its own unique identity, these identities become the new “perimeter”. By refusing access to any machine or process that fails to offer an identity with the correct permissions, the organization can prevent unauthorized access, while allowing business processes to continue enforcing least privilege.
Finding a solution
Whichever way the TikTok breach allegations shake out, our message is the same: protect your cloud with total cloud security. The best platform security includes context from every pillar of your cloud – identity, data, or workload
Being aware of the shared responsibility, and better yet, being ready to take steps towards reducing risk in your cloud environment, is half the battle. If your organization is looking to better ensure your cloud is configured safely at the most foundational level, there is a solution.
Sonrai Security offers a total public cloud security solution for Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Oracle Cloud. Sonrai identifies and monitors all relationships between workloads, identities, and data stores that exist within your various cloud platforms to provide security teams a continuous view of all risks, unusual activity and automated remediations. With identity and data at the core of our solution, you can protect against cloud risks, like data breaches, unauthorized access, and more.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.







