Table of Contents

Share this entry
AWS Security Hub is a cloud security posture management service that performs automated, continuous security best practice checks against your AWS resources. It aggregates your security alerts (findings) in a standardized format so that you can easily take action. Security Hub makes it simple to understand and improve your security posture with automated integrations to AWS partner products.
Now you can bring Sonrai’s unique insights into Security Hub. This integration enables organizations to monitor assets and send alerts on resource configurations, compliance violations, network security risks, and anomalous user activities across AWS environments.
What Sonrai Brings to Security Hub
The Sonrai Dig Platform runs on a patented graphing technology that continually collects data and finds identity and data risks – and then provides automated (or semi-automated) remediations. The platform then classifies the risks in separate categories. With built in operationalization features, like maturity modeling, teams see their progress in each security area over time.
A few examples of the risks that will get sent to AWS Security Hub are:
- CSPM (Cloud Security Posture Management) – identifying exposed and overly permissive network configurations.
- CIEM (Cloud Infrastructure & Entitlements Management) – finding over privileged identities, dormant identities, privilege escalation, and toxic combinations.
- CDLP (Cloud DLP) – monitor and alert on changes to critical resource attributes, including encryption status, permissions, public access, and version.
Let’s dive into how Sonrai Dig works with AWS Security Hub, and how you can monitor privilege escalation for a swimlane in your cloud environment – a critical step in improving your cloud security posture.
Solution Overview
Sonrai Dig’s integration with AWS Security Hub allows you to view Sonrai tickets in the Security Hub console.
Sonrai uses swimlanes – logical groupings of cloud assets defined by the end customer, with owners and relevant users associated – to configure your choices with the Security Hub integration. The integration also enables users to see all of their Sonrai alerts within Security Hub with added context, including when findings have been solved within Sonrai, giving you a comprehensive log of activity across your cloud.
Here’s what Sonrai brings to the table:
- Generation of Security Hub findings via ticket triggers in Sonrai Dig.
- A configurable integration down to each specific Sonrai swimlane, allowing customers to control which findings appear in Security Hub.
- The ability to monitor, review details, and resolve Sonrai’s findings on identity and data from Security Hub and plug in to EventBridge remediation workflows.
How it works

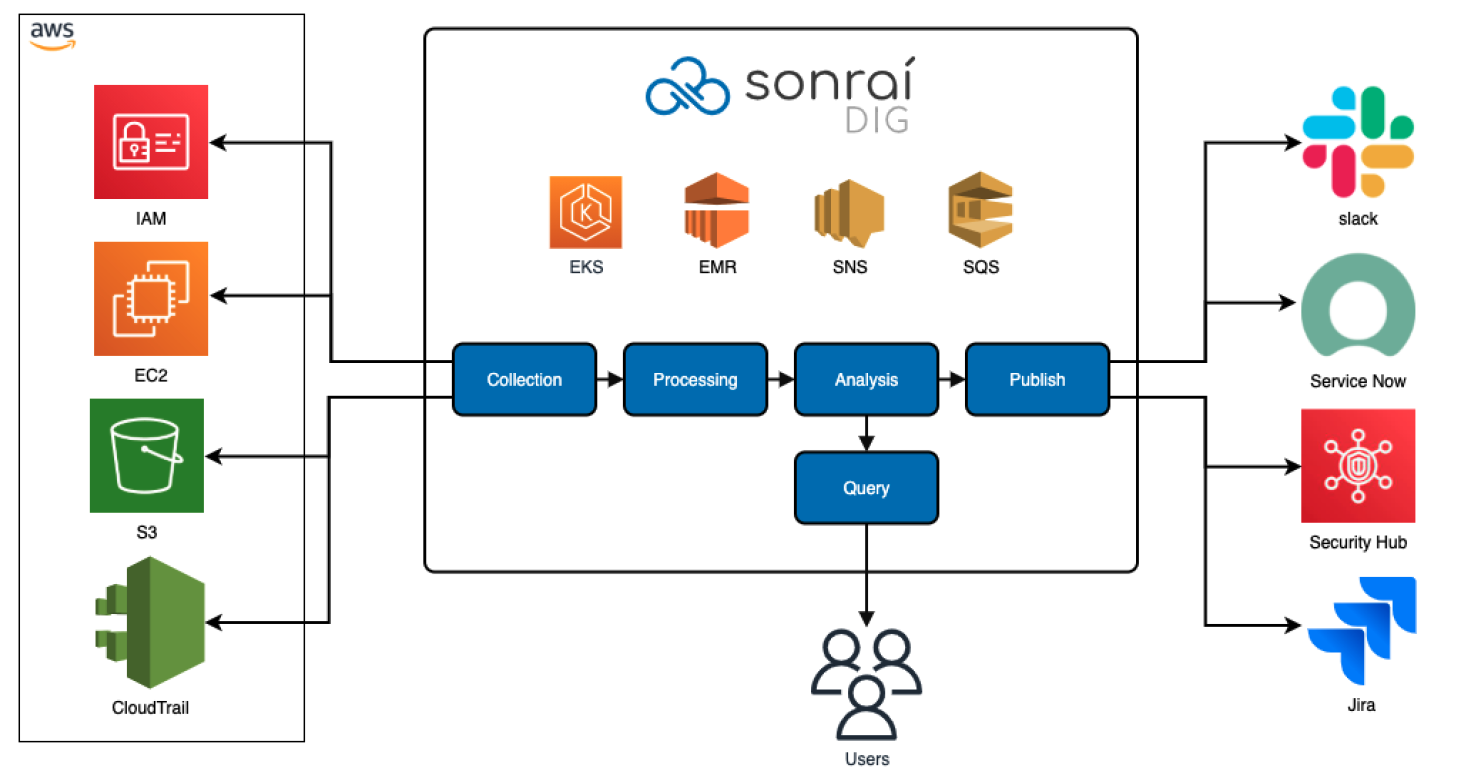
Sonrai Dig gathers logs and audit data from multiple AWS sources, applies patented analytics to determine risks, and sends findings to AWS Security Hub.
The above architecture diagram shows a high-level representation of the meta-data flow from the AWS Cloud Environment. When you configure the integration for Sonrai Dig and Azure Sentinel, the process looks like this:
- The Sonrai Dig collectors aggregate data from cloud deployments.
- After going through Processing and Analysis, Sonrai Dig generates security alerts and tickets about potential security risks in your deployment.
- Sonrai then creates notifications about actions taken for those security tickets.
- Sonrai sends those findings to AWS Security Hub based on the integration setup for the selected swimlane.
Prerequisites
To run this solution, you must have the following prerequisites:
- AWS Security deployed in your AWS environment. If you haven’t already enabled AWS Security in your account, see the AWS documentation for setting up AWS Security Hub.
- A Sonrai Dig account. If you don’t have a Sonrai Dig subscription, visit the Sonrai Security website for more information to obtain one.
- Sonrai Dig deployed and configured in your AWS environment. To add AWS accounts to Sonrai Dig, navigate to Accounts.
Configuration
- From the Security Hub console, navigate to Integrations and search for Sonrai Security.
- Select the Sonrai Security Solution from the available options and select ‘Accept Findings’. This will bring up a summary of the policy you’re adding to obtain tickets from Sonrai.
- Open the Sonrai Dig security console and navigate to the Integrations tab, select the AWS Security Hub option and click ‘Add Security Hub’.
- Add the Security Hub settings in the required fields:
- Title – name of the integration
- Description – additional details to describe the integration
- Account ID – this is AWS account ID which has Security Hub provisioned
- Region – this is the AWS region which has Security Hub provisioned
- Click ‘Validate’ to generate a validation code in Sonrai. A sample finding will be sent to Security Hub, which will include the same validation code.
- Check to ensure the codes match and then click the ‘Add’ button in Sonrai to create the integration.
- Navigate to the Swimlanes tab in Sonrai Dig console and select a swimlane you’d like to send notifications from to AWS Security Hub.
- Click the ‘Integrations’ tab and click ‘Add Destination’.
- Select the Security Hub integration from the drop menu and click ‘Add’.
- Repeat steps 7-9 to add additional swimlanes.
- Click ‘Manage Integration’ within Integrations In Sonrai Dig to make changes to the swimlanes you have added or to update your integration settings.
Monitor Privilege Escalation from within Security Hub
Given the sheer amount of identities (people and non-people) in a typical AWS deployment, evaluating privilege escalation risk is challenging. There are myriad factors: Service control policies, permission boundaries, allow/deny statements, notPrincipal, notAction, resource statements, conditions, assumed roles, group membership, SSO users with multiple roles and resource policies (S3, KMS, etc.) – all making it hard to understand the effective permissions of an individual identity. It’s a problem that cannot be solved by evaluating a single policy or calling an AWS API.
Understanding escalation risk requires modeling trust relationships that allow an identity, resource (compute, container, serverless function), identity provider (SSO, Hashicorp Vault), or AWS Service to assume a role. In Sonrai, these models are created by the graph. Analytics are then run across the graph to calculate all effective permissions of an identity. The resulting records include the chain of identities allowing permission, what account the permission is applicable in, when the permission was last used, and how many times it has been used.
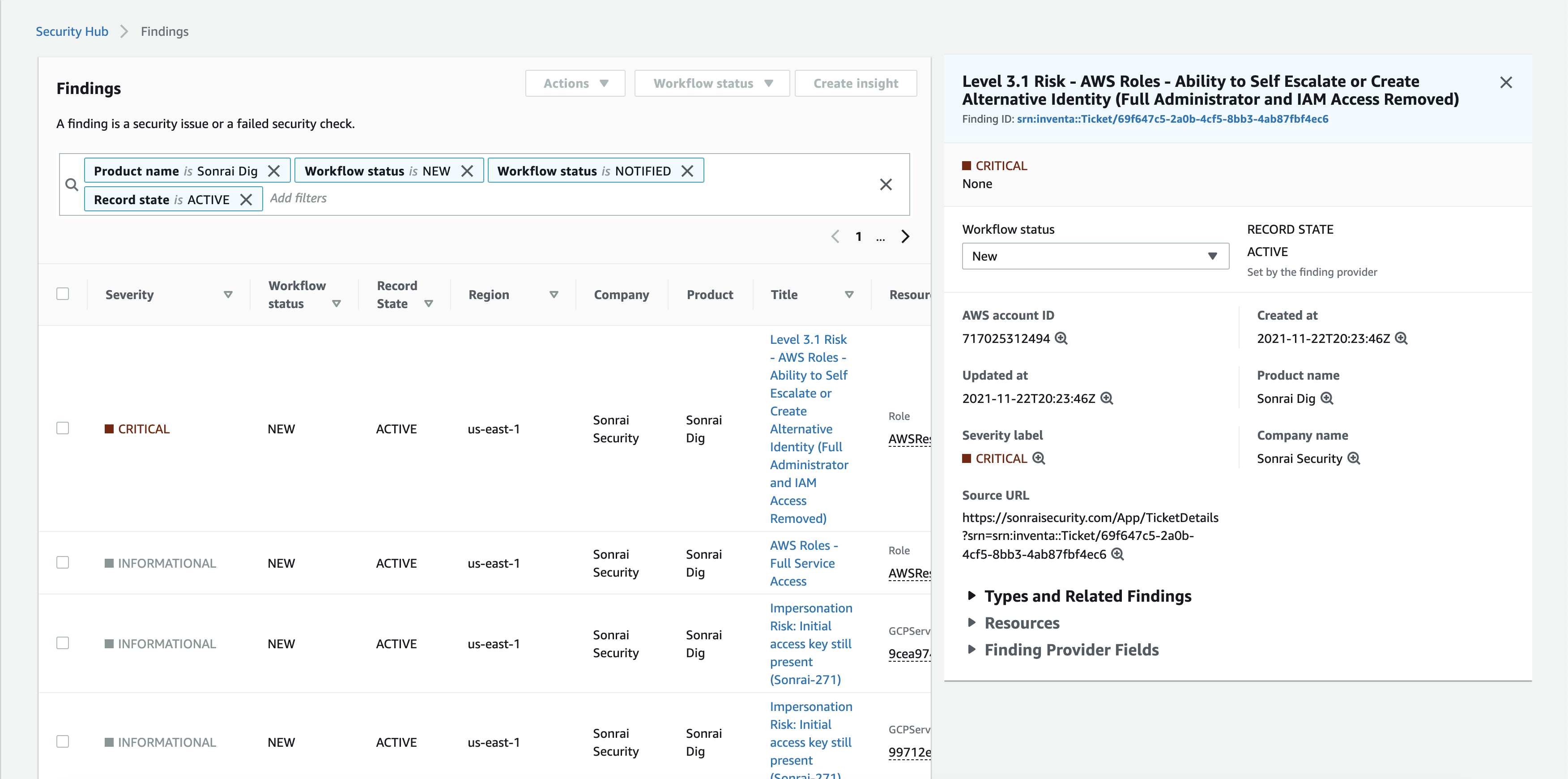
When the Sonrai analytics determine an entity’s effective permissions via privilege escalation violate the policies you have in place, an alert is generated in the Sonrai system. Depending on your remediation setup, this may be resolved in Sonrai and the record of remediation will appear within Security Hub, or the alert will appear as a finding for further processing. Either way, the Sonrai graphing technology has unearthed another hidden path to policy violation that can’t be seen in traditional identity management tools.
Supercharging Security Hub for Your Entire Cloud
Sonrai enriches and extends Security Hub’s view of your security posture. We all want a clear picture of everything happening across our entire AWS footprint. By digesting all cloud logs and metadata in a unified format, Sonrai enables a much richer view of identity & data risk.
Monitoring issues like privilege escalation & remediating issues fast requires a full graph of access paths, as well as the frame of reference for the environment to reduce false positives. Sonrai completes the Security Hub vision of a singular command center for platform, identity, and data security.
For more information, see the AWS documentation here. For more information about how the Sonrai platform works with AWS cyber security solutions, navigate to the platform section of our website.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.