Table of Contents

Share this entry

Most cloud providers services like Microsoft Azure operate under a shared responsibility model. Azure takes care of the security ‘of’ the cloud while Azure customers are responsible for security ‘in’ the cloud. Because the Azure cloud security framework can be difficult to understand, we’ve broken down some highlights for you in this blog.
Microsoft Azure has made platform security a priority to protect customers’ critical information and applications by taking responsibility for its infrastructure’s security. Azure detects fraud and abuse and responds to incidents by notifying customers. However, the customer is responsible for ensuring their Azure environment is configured securely and data is not inappropriately shared as well as identifying when an identity (people or non-people) misuses Azure, through enforcing compliance and governance policies.
What is Microsoft Azure Shared Responsibility ‘of’ the Cloud?
Azure is focused on the security of the underlying infrastructure, by protecting its computing, storage, networking, and database services against intrusions. Azure is also responsible for the security of the software, hardware, and physical facilities that host Azure services. The Azure cloud security framework takes responsibility for the security configuration of its managed services such as Azure Kubernetes Service (AKS), Container Instances, Cosmos DB, SQL, Data Lake Storage, Blob Storage, and others.

What is the Customer Responsibility ‘in’ Azure?
Azure customers are responsible for the security “in their own cloud, or more simply put, everything that they instantiate, build and/or use. For example, while Azure has built several layers of security features to prevent unauthorized access to Azure, including multi-factor authentication, it is the customer’s responsibility to make sure multi-factor authentication is turned on for users, particularly for those with the most extensive IAM permissions in Azure.
It is worth noting that the default security settings of the Azure cloud security framework services are often the least secure configuration. Enhancing these initial Azure security settings, therefore, is a low-hanging fruit that organizations should prioritize as the first step to fulfill their end of Azure security responsibility. From there, they should examine the services and resources that they are using to determine what the target security levels should be, and then put a plan in place to configure their cloud as such.
The security perimeter has changed, Identity and not firewalls form your security boundaries. As enterprises continue to migrate to or build their custom applications in Azure, the threats they face are no longer isolated like the old world of on-premises applications under this new paradigm Preventing many of these threats falls on the shoulders of the Azure customer. So how are you securing your data?
Below are Azure checklists to help you govern and secure your Azure cloud security framework, including but not limited to the following:
Responsibility of the Public Cloud Checklist
| Responsibility | Customer Responsibility | Azure Responsibility |
|---|---|---|
| Preventing or detecting when an Azure account has been compromised | ✓ | |
| Preventing or detecting a privileged or regular Azure user behaving in an insecure manner | ✓ | |
| Business continuity management (availability, incident response) | ✓ | |
| Protecting against Azure zero-day exploits and other vulnerabilities | ✓ | |
| Providing environmental security assurance against things like mass power outages, earthquakes, floods, and other natural disasters | ✓ | |
| Providing physical access control to hardware/software | ✓ | |
| Configuring Azure Managed Services in a secure manner | ✓ | |
| Ensuring network security (DoS, man-in-the-middle (MITM), port scanning) | ✓ | ✓ |
| Ensuring Azure and custom applications are being used in a manner compliant with internal and external policies | ✓ | ✓ |
| Updating guest operating systems and applying security patches | ✓ | |
| Restricting access to Azure services or custom applications to only those users who require it | ✓ | |
| Configuring Azure services (except Azure Managed Services) in a secure manner | ✓ | |
| Preventing sensitive data from being uploaded to or shared from applications in an inappropriate manner | ✓ | |
| Database patching | ✓ |
Division of Responsibility: Azure Cloud Security Framework
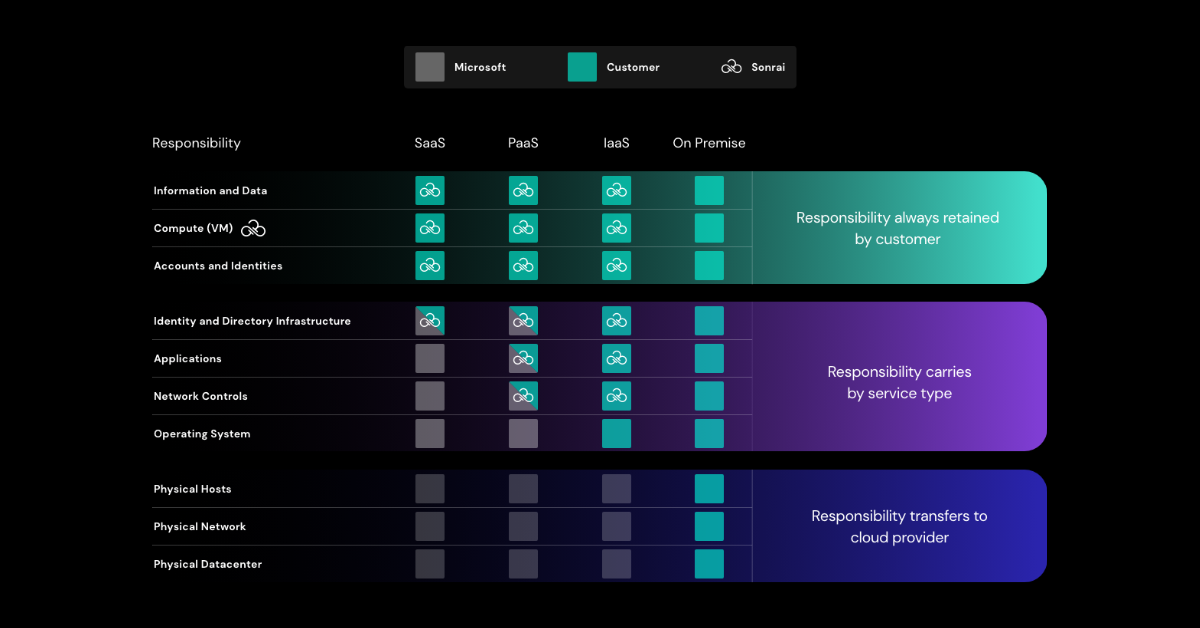
In an on-premises data center, the customer owns the whole stack. As you move to the cloud some responsibilities transfer to Microsoft Azure. The following diagram illustrates the areas of responsibility between the customer and Microsoft, according to the type of deployment of your stack.
For all cloud deployment types, you own your data and identities. You are responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control (which varies by service type).
Regardless of the type of deployment, the following responsibilities are always retained by you, the Azure customer:
- Data
- Endpoints
- Account
- Access management
Are You Ready to Secure Your Azure Environment?
There’s a lot to unpack here, and the truth is these are just a few of the responsibilities you need to understand when using Azure. If you have questions on the division of responsibility, cloud security, privacy ownership, policy enforcement, or how the Azure services work, don’t hesitate to reach out — Sonrai’s technical team of security experts are standing by to help.
Want to learn how we work to secure Azure? Explore our integrations and partnership with Azure.
If you are interested in stepping up your end of the deal securing your Azure environment, check out the Azure Shared Responsibility Model Explained guide.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.







