Table of Contents

Share this entry
Organizations are increasingly moving their operations to the cloud and Microsoft Azure is one of the most popular platforms for cloud computing. However, while Azure offers a range of features and tools to help with cloud security management, customers still have a laundry list of possible risks to consider and protect against.
What is Azure cloud security? It is the overall process and procedure for securing cloud infrastructure and all resources, data, identities and everything ‘inside’ the cloud against internal and external threats. The ultimate goal is securing your critical business operations.
By understanding these risks and your Azure cloud security resources, your organization can take steps to mitigate them, but first, let’s review what the CSP offers its customers on their Azure cloud security journey.
Azure Cloud Security Resources
Microsoft Azure arms their customers with knowledge and tools to better utilize their cloud as well as secure it. For example, Azure provides a detailed Well-Architected Framework. This framework is a set of best practices that you can use to improve the security and quality of your workloads in Azure. The framework includes five major pillars: Cost optimization; Operational excellence; Performance efficiency; Reliability; and Security.
Let’s further detail that fifth pillar, security.
British Council Massive Data Breach Exposes 144,000 Student Files; Here's How To Stay Protected https://t.co/1WS4u8fBif #breach
— Neil Notkin (@Notkin) February 7, 2022
There are a variety of security concerns customers may experience working in Azure – storage set-up, credentials or key management, identity and access management, and misconfigurations. Misconfigurations are often behind many Azure data breaches like this document verification platform exposing 30GB of student data or the British Council leaving a Blob wide-open.
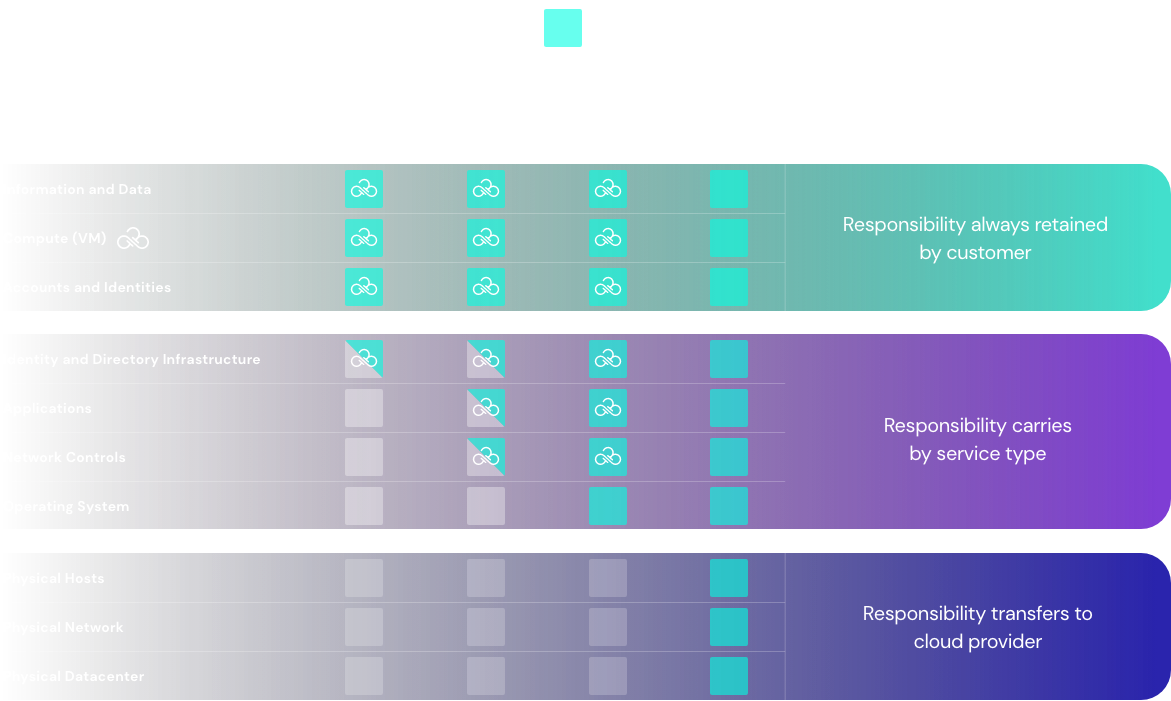
To help protect cloud workloads and your sensitive data, Azure provides customers with both security concepts and security controls and features to help mitigate risk. One guiding principle Azure emphasizes as part of their cloud security strategy is the shared responsibility model. This model outlines the line in the sand of customer vs. cloud service provider responsibility. CSP customers manage things like configurations, identity access, and data governance. Basically, anything going on within your cloud is your organization’s responsibility. Azure, on the other hand, handles infrastructure like physical hosts, data centers and networks, as well as some applications and operating systems.
Azure Cloud Security Tools
Azure contains an extensive list of built-in security offerings that you can use to strengthen your cloud environment. As you explore or expand on the Azure platform, keep these tools in mind.
Sentinel

Microsoft Sentinel is a cloud-native solution for security information and event monitoring (SIEM.) Sentinel offers threat intelligence and security analytics and empowers security teams to act with greater speed and responsiveness using a single dashboard.
Defender for Cloud

Defender for Cloud is a powerful cloud security posture management (CSPM) tool. Its main purpose is to identify cloud vulnerabilities and help businesses handle evolving threats. This tool also lets you remediate security issues from a central location, which saves time and effort for team members.
Application Insights

Application Insights is an extensible application performance management (APM) solution. Using this tool, you can monitor live web applications and discover performance issues. It also provides analytics and performance anomaly detection.
Resource Manager

Resource Manager is a system deployment and management service that you can use to create and manage Azure assets. Resource Manager also offers template-based deployments, which can replace manual deployments and reduce configuration errors.
Azure Monitor

Azure Monitor provides ongoing security alerts for events that arise from Azure and activity logs. This tool supports data querying, routing, and visualization.
Web Application Firewall (WAF)

Microsoft provides a secure WAF component in the Azure Application Gateway. WAF helps protect applications from threats like session hijacking and SQL injection.
Azure provides a strong suite of cloud-native management tools. But in order to develop a secure, mature cloud environment in Azure, your team will have to take ownership and develop its own management policies.
Azure makes it easy to manage your environment and track your progress. The platform is highly flexible and capable of integrating with third-party platforms. As such, it’s definitely worth expanding beyond the Azure cloud security framework and incorporating your preferred security tools.
Azure Cloud Security with Sonrai Security
Microsoft Azure services integrate with security providers to provide comprehensive options so decision makers can select the best tools for their clouds. As a member of the Microsoft Intelligent Security Association (MISA) ecosystem, Sonrai Security integrates our cloud security platform with Microsoft’s security technology to better defend against a world of increasing threats. MISA members are top experts from across the cybersecurity industry with the shared goal of improving customer security. To date, Sonrai is able to integrate with hundreds of Azure services, including but not limited to, following:
Advanced Data Security
Sonrai Dig integrates with Advanced Data Security (ADS), which is a unified package for advanced SQL security capabilities. Dig with ADS includes functionality for discovering and classifying sensitive data, surfacing and mitigating potential database vulnerabilities through over privileged identities, and detecting anomalous activities that could indicate a threat to your database. The combined integration provides a single goto location for managing and governing these activities including data classification, drift detection, and more.
Azure Sentinel
If you’re an Azure Sentinel user, Dig sends alerts to Azure Sentinel, bringing insights around configuration, identity, and data risks of a particular application or the entire cloud environment within the Sentinel Console. Ticket activities in Dig, like remediations and snoozes, can be configured to appear in Sentinel to give a comprehensive picture of security event management. Sentinel users can also run automation & orchestration playbooks off of Sonrai alerts.
Active Directory
Organizations that already use on-premise Active Directory can synchronize their identities with Azure AD to provide seamless integration between on-premise and cloud resources. While this might seem easy, migrating workloads from on-prem to the cloud can be a major identity and data security challenge for enterprises.
Achieving Total Azure Security
If your organization uses Azure, we recommend strategizing your cloud security program around four major pillars: identity, data, platform, and workload. While built-in Azure offerings like Active Directory (identity), Purview (data), Azure Monitor (platform), or Defender (workload) are a great start to building a robust program, many organizations seek third-party cloud security providers to gain deeper visibility into identity entitlements, more context into vulnerabilities, actionable security posture checks, and detailed data activity across all cloud environments.For a complete guide to securing Azure, download our Azure Security 2022 Checklist.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.







