Table of Contents

Share this entry

Azure Sentinel from Microsoft is a cloud-based SIEM (Security Information and Event Management) and SOAR (Security Orchestration Automation Response) solution that can be used to gather security information from across an organization and help to identify and remediate security threats. To help continuously secure your cloud environments, Sonrai Security now integrates with Sentinel. This integration allows users to view all the configuration, identity, and data risks of a particular application or the entire cloud environment in Azure Sentinel Console sharing the Azure Sentinel alerts that matter most.
Bring Sonrai insights into Azure Sentinel
The Sonrai Dig Platform runs on a patented graphing technology that continually collects data, applies ML techniques, and finds identity and data risks – and then provides automated (or semi-automated) remediations. The platform then classifies the risks into separate categories. With built-in operationalization features, like maturity modeling, teams see their progress in each security area over time.
A few examples of the risks that will get sent to Azure Sentinel are:
- CSPM (Cloud Security Posture Management) – identifying exposed and overly permissive network configurations.
- CIEM (Cloud Infrastructure & Entitlements Management) – finding over privileged identities, dormant identities, privilege escalation, and toxic combinations.
- CDLP (Cloud DLP) – monitor and alert on changes to critical resource attributes, including encryption status, permissions, public access, and version.
Let’s dive into how Sonrai Dig works with Sentinel, and how you can easily apply the principle of least privilege and least access for a swimlane in your cloud environment – a critical step in improving your cloud security posture.
Solution overview
Sonrai Dig’s integration allows you to view Sonrai tickets in the Sentinel console, as well as generate security alerts for them.
Sonrai uses swimlanes – a logical grouping of cloud assets defined by the end customer, with owners and relevant users associated – to configure your choices with the Sentinel integration. The integration also enables users to see all of their Sonrai alerts within Sentinel with added context, making remediation with Sentinel’s automation & orchestration tools fast and simple.
Here’s what Sonrai brings to Sentinel:
- Generation of Azure Sentinel ticket triggers in Sonrai Dig (i.e., a ticket is opened, closed, snoozed, etc)
- A configurable integration down to each specific Sonrai swimlane, allowing customers to choose which triggers in which environments create alerts.
- A Sonrai Solution Wizard that deploys analytic rules to display the custom logs table in alerts that fit the user’s existing nomenclature
- A solution content package that will enable customers to consume Sonrai Dig notifications easier, and in more useful ways.
- The ability to monitor and resolve Sonrai’s unique tickets on identity and data from Sentinel’s automation & orchestration tools faster
How it works
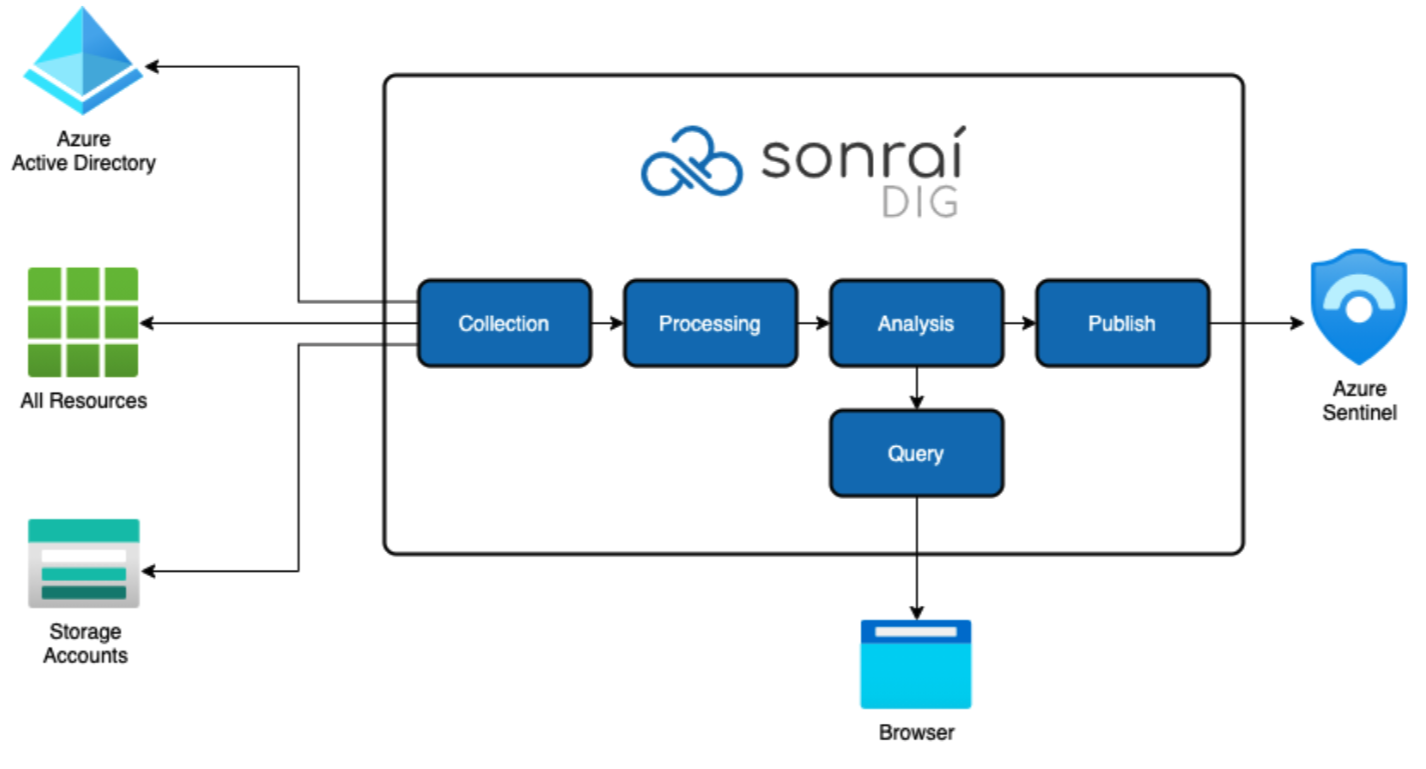
The above architecture diagram shows a high-level representation of the meta-data flow from Azure Cloud Environment. When you configure the integration for Sonrai Dig and Azure Sentinel, the integration process looks like this:
- The Sonrai Dig collector (AKS Cluster) collect data from cloud deployments.
- After going through Processing and Analysis, Sonrai Dig generates security tickets about potential security risks in your deployment.
- Sonrai then creates notifications about actions taken for those security tickets.
- Sonrai sends those notification logs to Azure Sentinel based on the triggers configured for the integration that were chosen during setup.
Prerequisites
To run this solution, you must have the following prerequisites:
- Azure Sentinel deployed in your Azure environment. If you haven’t already Azure Sentinel, see the Microsoft documentation for getting started with Azure Sentinel.
- A Sonrai Dig account. You must be an existing customer with a Sonrai Tenant, or request trial access from the Sonrai website.
- Sonrai Dig deployed and configured in your Azure environment. To configure Sonrai collectors, navigate to Collectors.
Configuration
- From the Azure Sentinel console, navigate to the Solutions option and search for Sonrai Security.
- Select the Sonrai Security Solution from the available options and follow the instructions in the Solution wizard for configuring the integration in Azure Sentinel.
- Open the Sonrai Dig security console and navigate to the Integrations tab, then select the Azure Sentinel option and click ‘Add Azure Sentinel’.
- Fill out the form with the information provided by the Azure Sentinel Solution deployment wizard and submit the form.
- Navigate to the Swimlanes tab in Sonrai Dig console and select a swimlane you’d like to send notifications for to Azure Sentinel.
- Navigate to the integrations tab and add the integration you created, selecting which triggers you’d like to send notifications to Azure Sentinel.
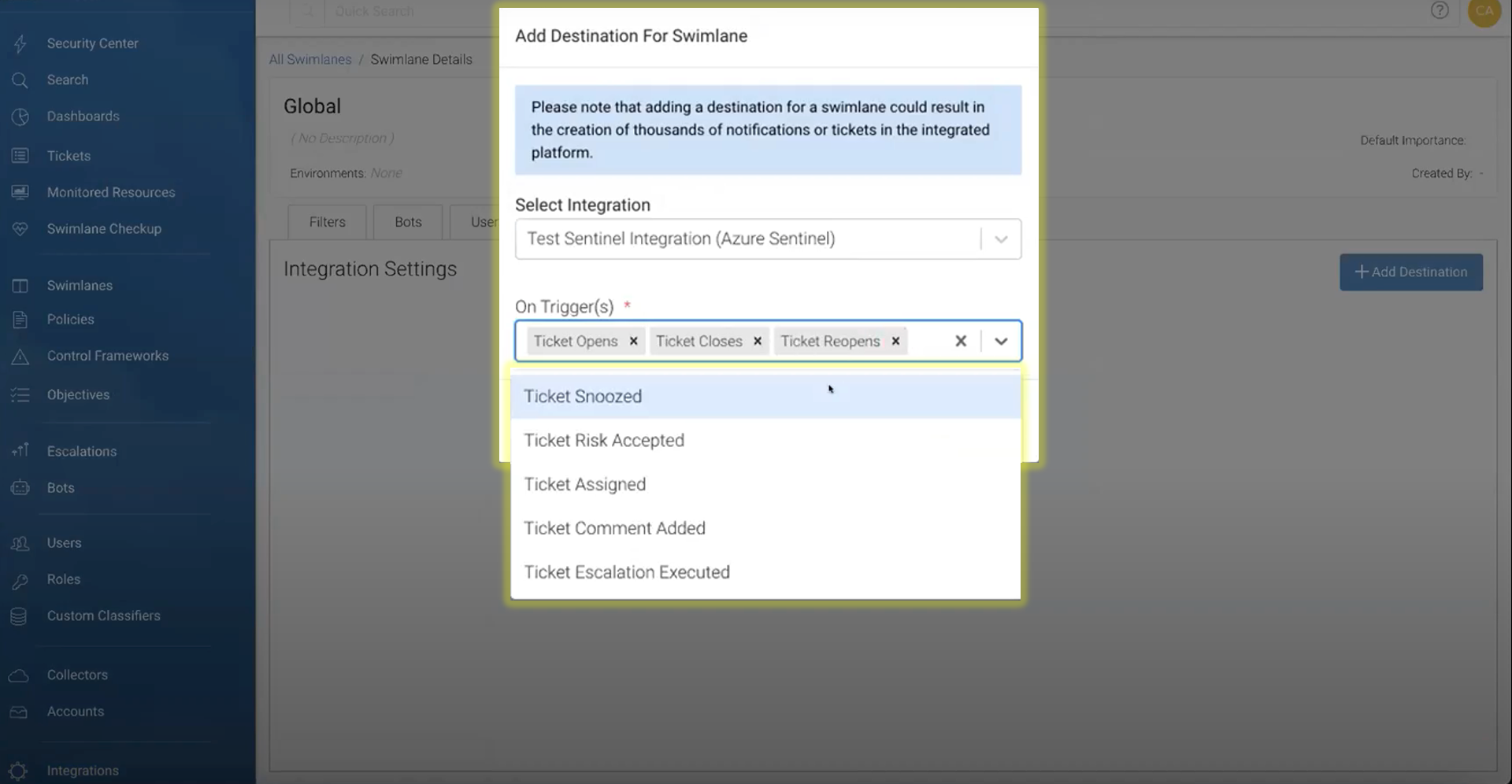
Now you’ve configured your integration between Sonrai Security and Microsoft Azure Sentinel. If you want to add more swimlanes to your integration, you only need to select another swimlane and repeat steps 5-6.
Apply Least Privilege from within Sentinel
The principle of Least Privilege demands you limit identities to only the actions they need to complete their everyday tasks. Given the proliferation of non-people identities and ephemeral compute, this requires constant monitoring.
In the modern public cloud, expanded dynamic infrastructure capabilities make least privilege a challenge. A short-lived serverless function can abuse privilege escalation capabilities and violate Least Privilege before registering an anomaly with identity management software. Users find public credentials to an identity with no apparent access to sensitive data but can chain together group permissions to access a blob with PII. From both data permission configuration and identity management, there are too many combinations of variables for traditional IAM solutions to understand when Least Privilege is violated
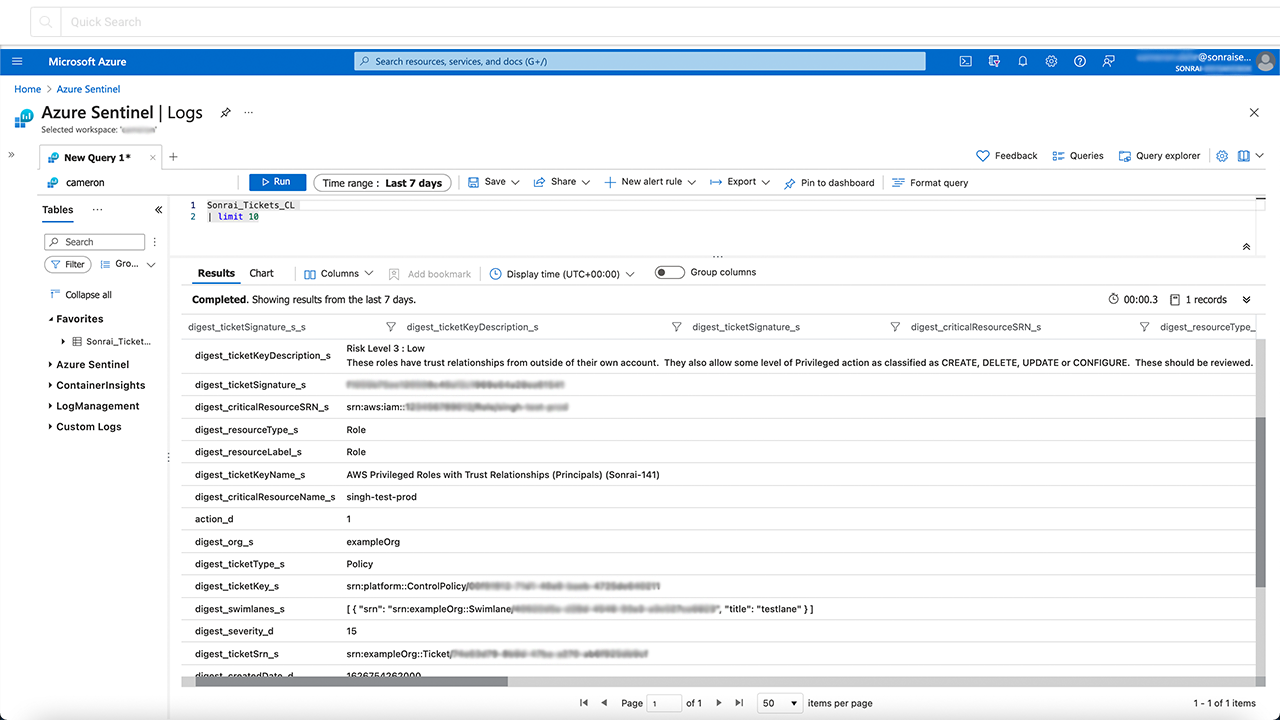
Sonrai’s infrastructure & entitlement monitoring shows every path to data from every identity. Complex permission chaining is visible to the Sonrai graphing technology, allowing Sonrai to ‘see’ an identity’s ‘effective permissions’ that are not always visible within identity management. In Sentinel, Sonrai surfaces issues like ‘Unnecessary Administrative Assignment for Service Principals or Azure Users.’ Or for an Azure KeyVault, Sonrai can detect separation of duties failures when an identity can perform management actions, or has the ability to encrypt/decrypt data. Ideally, the ones who manage the vaults should not be able handle the data. These are just a few of the least privilege controls for Azure within Sonrai.
Once Sonrai identifies these issues blocking least privilege, they can be surfaced to Sentinel for resolution via the Automation & Orchestration tools, or Sonrai can handle remediation with its own prebuilt bots and routines. For example: if a routine has been established to ignore or ‘snooze’ a certain ticket from a certain environment or swimlane, that can be ignored by Sentinel, or brought into Sentinel for record keeping.
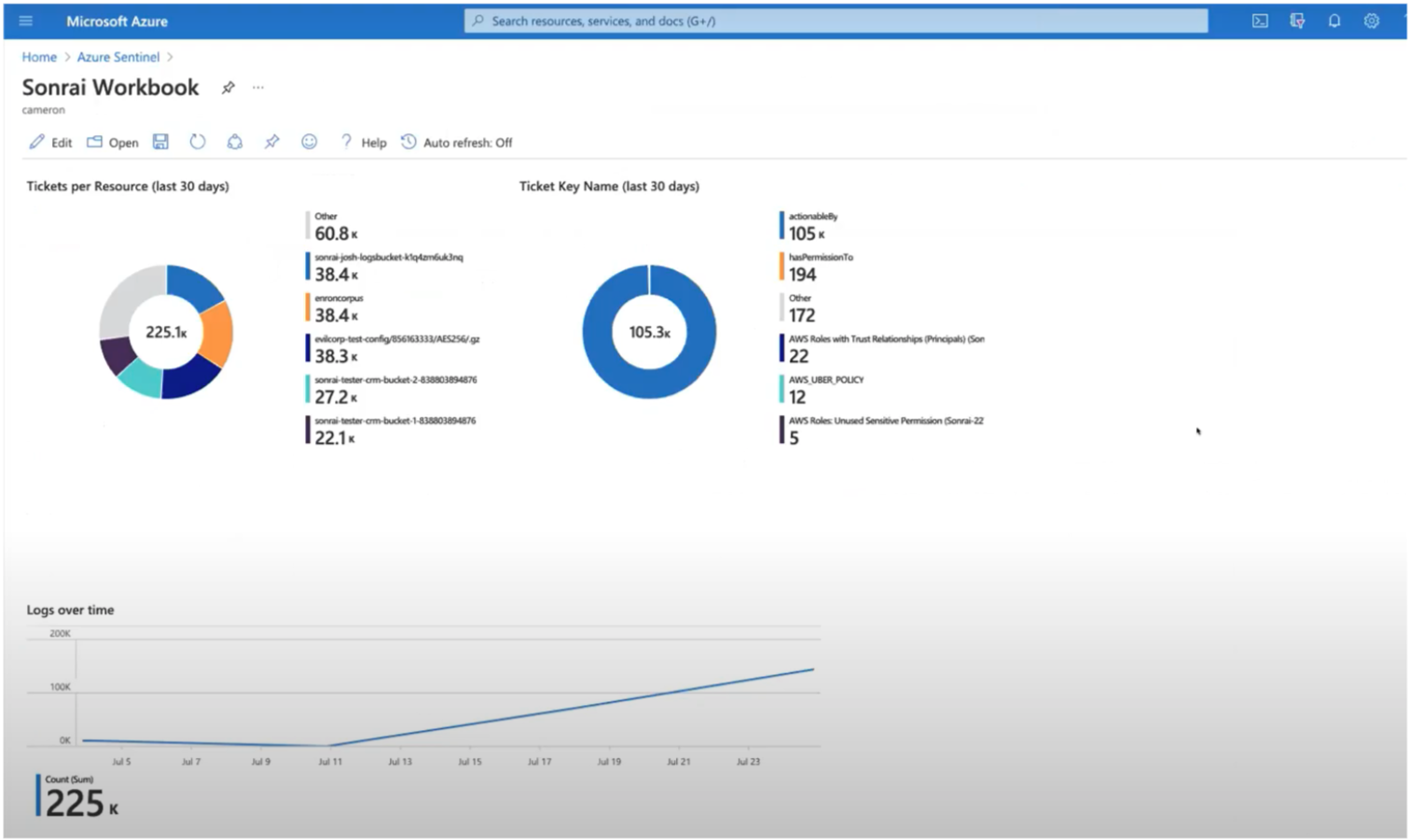
Supercharging Azure Cloud Security Service
If Sentinel is your command center for Azure and other public cloud providers, Sonrai can enrich and enable remediation in all your environments. Sonrai digests all cloud logs and metadata in a unified format, allowing Sentinel to understand everything happening over your organization’s entire cloud footprint.
Sonrai and Sentinel are a powerful combination. They create a unified control center of all public cloud security issues with deep context into identity & data access. Enforcing Least Privilege, Zero Trust, and other security best practices is only achieved with complete knowledge of data access issues without overwhelming the system with alerts. Context is key to cutting through to the most important issues brought into Azure Sentinel – and that’s where Sonrai delivers.
For more information about Azure Sentinel solutions, see the Microsoft documentation here. For more information about the Sonrai platform, navigate to the platform section of our website.





