
Share this entry
The leak of 1 billion Chinese nationals’ personal details is just the latest in a series of cloud security data breaches. A misconfigured server has led to this massive leak of citizen’s personal details. “ChinaDan,” an anonymous threat actor, posted an advertisement on a hacker forum selling 23 terabytes of data for ten bitcoin. The data was allegedly stolen from the Shanghai National Police database, which contains PII, including Chinese nationals’ personal details, like names, home addresses, criminal records, and ID and phone numbers.
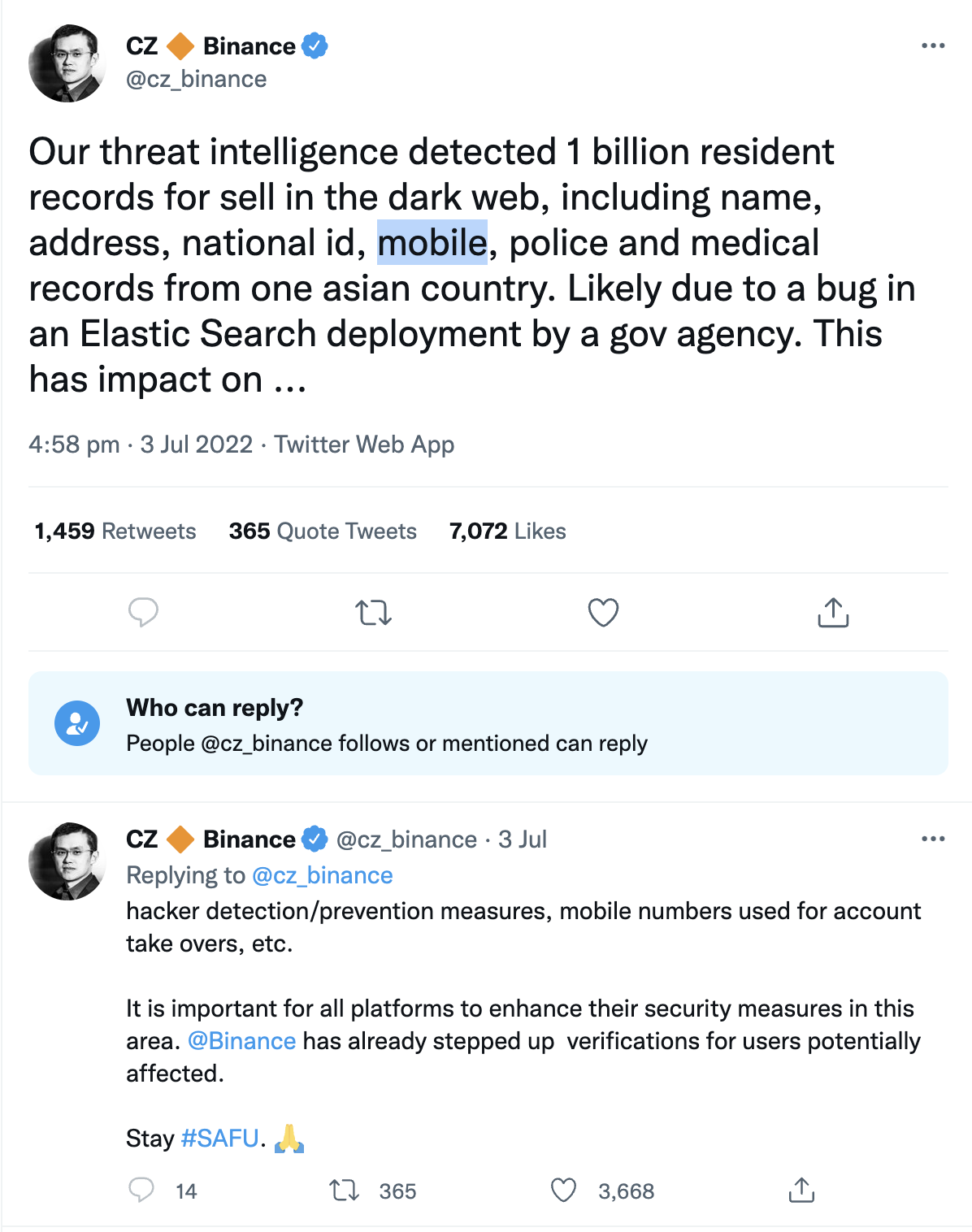
A tweet by Changpeng Zhao, founder and Chief Executive Officer of cryptocurrency exchange Binance, says, “Our threat intelligence detected 1 billion resident records for sale in the dark web, including name, address, national id, mobile, police and medical records from one Asian country. Likely due to a bug in an Elastic Search deployment by a gov agency. This has impact on hacker detection/prevention measures, mobile numbers used for account takeovers, etc.”

ChinaDan shared a sample with 750,000 records containing ID information and police call records as a sample that allows interested buyers to verify the data, according to a report from Bleeping Computer.
ChinaDan confirmed the data was exfiltrated from a local private cloud provided by Aliyun, Alibaba Cloud, part of the Chinese police network, and public security network.
The breach was discovered by Binance CEO, who confirmed that his company’s threat intelligence experts spotted ChinaDan’s claims and said that the leak was likely due to an ElasticSearch database that a Chinese government agency accidentally exposed online.
Unfortunately, while it is a big mistake to leave your environment open to the public internet, it is a common misconfiguration that has led to many high-profile AWS data breaches. Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in AWS, creating a virtual computing environment, also known as instances. These instances are prone to configuration errors, like leaving them publicly accessible or not requiring the proper authentication to access them. It is precisely this type of highly preventable misconfiguration that becomes the Achilles heel of organizations today.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




