Get Your FREE E-Book
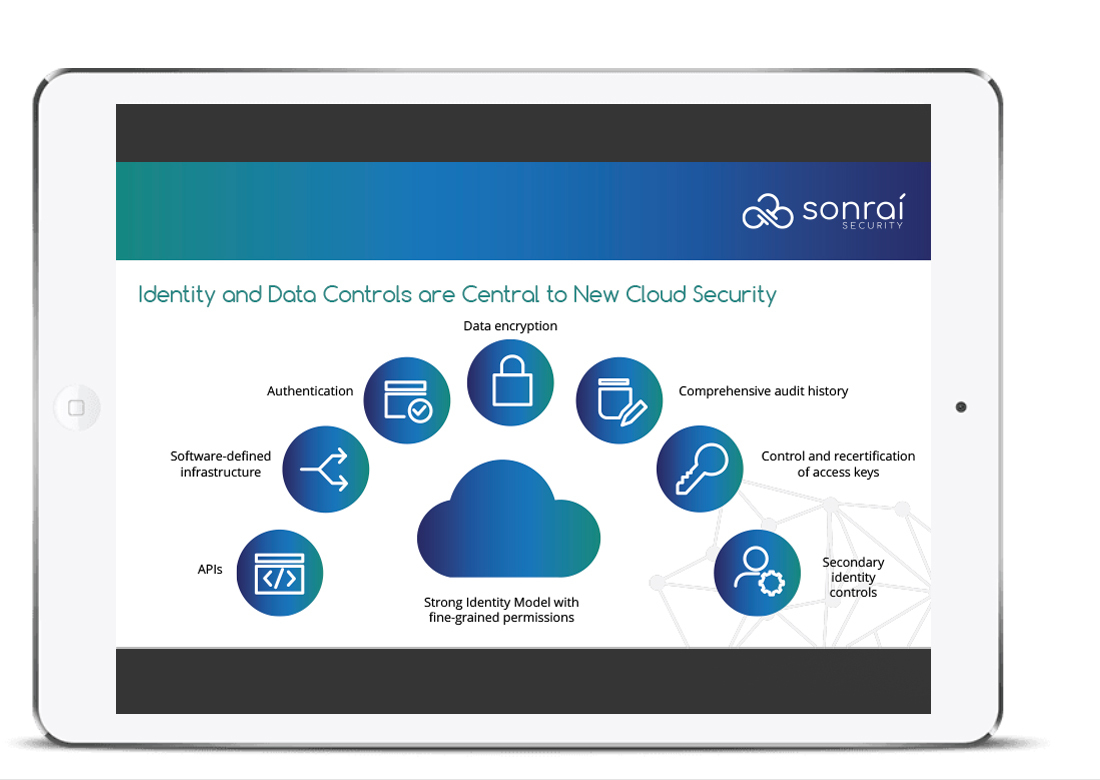
Most enterprises recognize that value can be found with the public cloud, but many still struggle with identity and data security. What can you do to ensure you’re not among those organizations making common mistakes in Microsoft Azure? Too many companies make the same mistakes when configuring their cloud-based IAM strategy, resulting in unnecessary vulnerabilities. If your organization uses Microsoft’s Azure, then you’ll want to avoid making the Azure configuration errors that are most common among like-minded users.
Our Avoiding Common Azure Configuration Errors eBook is designed to discuss some of the common Azure data and identity mistakes including practical real-world scenarios. Our eBook details the missteps enterprise orgs may make — and how others avoid them to ensure security across their public cloud.
In our eBook, you’ll learn about
- Data Security Errors
- Data Optimization Errors
- Expensing Errors


