Table of Contents

Share this entry

As your organization grows, so does your reliance on cloud services. But with that growth comes the risk of cloud sprawl — when too many cloud services are added without proper planning and oversight, leading to security and compliance risks. How do you know if your cloud is in danger? And how can you address the problem before it becomes unmanageable?
Business growth is usually an excellent indicator of success. The accompanying cloud growth often fulfills business needs to result in positive outcomes; however, the unstoppable forces of an ephemeral cloud and agile development are driving momentous changes in how enterprises secure applications. These shifts have many implications, among them is cloud sprawl. In fact, according to research by the Cloud Security Alliance, cloud sprawl is one of the top security threats organizations face today.
What is Cloud Sprawl?
According to Stephen J. Bigelow, Senior Technology Editor of TechTarget, “Cloud sprawl is the uncontrolled proliferation of an organization’s cloud instances, services or providers. Cloud sprawl typically occurs when an organization lacks visibility into or control over its cloud computing resources.” An organization using multiple cloud platforms, and hosting hundreds, if not thousands of identities and data instances, is easily prone to losing visibility into what’s happening in their cloud. Cloud sprawl leads to not knowing where your data is, who has access to it, or what they’re doing with that access. Plus, the nature of the cloud and the nature of agile development, leads to a constant flow of new applications or workloads being made, and then possibly forgotten about and left to accumulate.
Cloud sprawl is a common problem faced by growing organizations today.
We’ve seen first hand with our customer, World Fuel Services, that growing organizations are shifting their tech stack by replacing their data centers with public cloud service providers. As predicted by Gartner, more organizations are making efforts to shift to cloud-centric infrastructure and applications.

Adoption of the public cloud means more organizations will need to have visibility and control over their cloud platforms, accounts, instances, identities, services and more. Stretched, underfunded, and rapidly changing, internal teams are forced to keep up with insane workloads that leave plenty of room for error – resulting in three types of sprawl.
Cloud Sprawl Areas: Platform, Data & Identity
Let’s consider three areas that create cloud sprawl: platform, data, and identity.

Platform Sprawl
Appealing to convenience and immediate need, developers can usually order computing power and storage without any oversight, planning, and direction of security. Building in the cloud, adding features to existing cloud structures, adding roles, and spinning up pieces of compute are all simple tasks. However, the ease of creating new identities and data stores while recreating an application, often leads to abandoned, unneeded, or forgotten workloads, users, pieces of compute, roles and more. These identities, whether they relate to a person or non-person, are left dormant in the environment. Not only adding wasteful costs, but these dormant identities create a hidden risk to your organization.
This lack of governance means that visibility into the cloud is myopic at best, with rogue cloud resources that may never see decommissioning or align with the organization objectives. Platform sprawl is then created as the organization reaches a point where administrators can no longer manage the environment effectively. Unfortunately, because of this, it’s common to find development servers that are built, but dormant and that are compromised from a security standpoint without anyone realizing it. Even dormant, segregated, or devoid of active data, these circumstances carry significant risks.
Now all this platform sprawl is just within one cloud. Imagine an organization leveraging multiple cloud providers. According to an Osterman Research Paper, 80% of the companies in the cloud have adopted a multi-cloud strategy using multiple providers such as Amazon, Microsoft, Google, IBM, Oracle, and Alibaba. This multi cloud strategy comes with a decentralized view and lack of visibility across your entire environment.

Data Sprawl
Data Sprawl happens when organizations can no longer effectively manage how they collect, process, and store data, making it increasingly harder for them to control what data they have, where it is located, and who has access to it. It’s self-evident that new corporate infrastructures no longer have a physical or logical concept of a ‘data center’ This makes data in the cloud elusive, intangible, and hard to keep track of, especially when you’re working across multiple clouds and without the proper cloud security tooling.
Not only is it difficult to monitor and control data stored in many disparate environments, but it also makes it harder for devs to quickly and accurately retrieve the information they need. To make matters worse, a lot of the data we store is duplicate or ROT (Redundant, Obsolete, and Trivial), which also leads to excessive utilization of resources. On top of development needs, securing data that you can’t keep track of or classify appropriately becomes a challenge.

Identity Sprawl
Identity sprawl refers to the growth of many separate identities a user or piece of compute creates to access other identities. As the number of identities increases, the identity is said to spread, scatter, or “sprawl” almost needlessly. A more unified approach would do the opposite, by consolidating identities, their roles, and their entitlements to the most conservative business needs.
The ease and benefits of creating cloud accounts has made having many AWS and GCP cloud accounts or Azure subscriptions the norm. It is not unusual for enterprises to have hundreds (and in some cases thousands) of cloud accounts.

That’s just addressing accounts – within those accounts are a proliferation of identities, person and non-person entities. In fact, organizations between $1M – $10M in public cloud investments have an average of 1,750 identities and 325 data stores in their environment, and organizations with over $100M in cloud investments see upwards of 7,750 identities and 3,750 data stores.
The increased use of non-person identities exacerbates this proliferation as entities like roles, service accounts, functions and VMs play critical roles in day-to-day operations and app development.
Existing Tools Fall Short with Cloud Sprawl
Now that we’ve laid the groundwork and challenges of cloud sprawl, Is it any wonder nearly half of surveyed businesses experienced a cloud data breach or failed an audit according to a 2022 Thales Cloud Security Report? The flexibility, agility and power of the cloud is amazing for innovation and business, but it poses serious risks if your cloud is not under control. Specifically, controlling identity and data access.
Let’s face it, traditional data center and network management tools are stuck in the past. Practitioner-focused cloud provider tooling is also not up to snuff. There are native data and identity solutions in AWS, Azure and GCP, but they’re markedly different and only work for the platform they’re hosted in. This becomes an issue for the many enterprises working multi cloud.
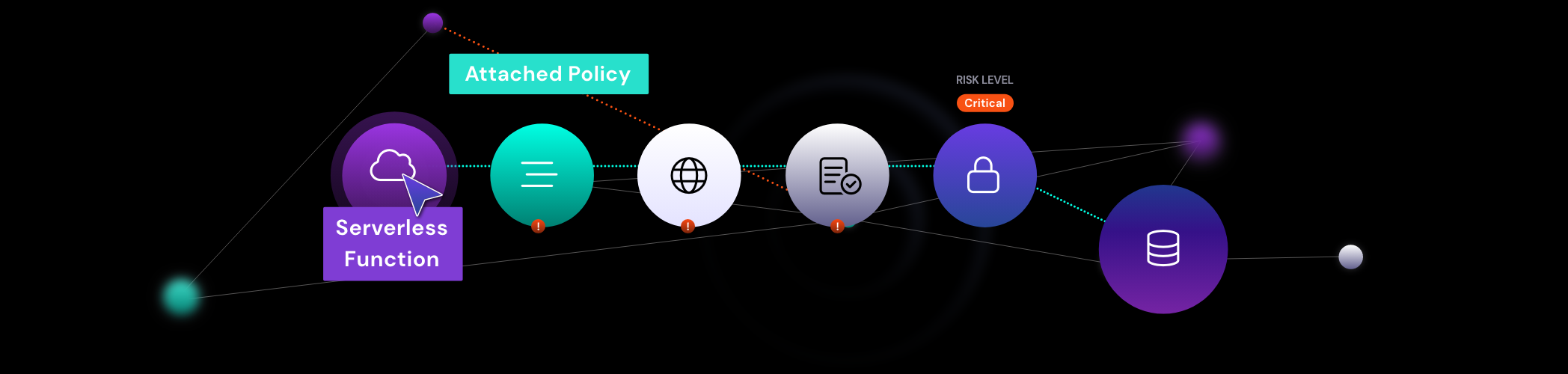
The paths between identity and data are extremely complex and sometimes covert. Access control lists, inline policies, group inline policies, role inline policies, assumed roles, switched roles federation, and managed policies all influence access to critical data. There needs to be a way for organizations to gain visibility into multiple cloud provider identity and data models and also track access to third-party data stores used within the major AWS, GCP and Azure cloud platforms. Where can a company turn when it needs to track data access and movement across multiple clouds, tons of cloud accounts and thousands of data stores?
Strategies for Fighting Cloud Sprawl
A growing cloud is an ideal indicator of a thriving business. When used securely and efficiently, everybody wins. However, when cloud pieces are being spawned all over the place, problems start to mount, creating inefficiencies that will quickly impact the organization negatively, so you want to address sprawl promptly.
The best way for an organization to manage cloud sprawl is to make sure that their cloud applications and environments don’t take on a life of their own. Organizations must proactively determine how the cloud is being used across the board. Some organizations create a Cloud Center of Excellence CCoE to help design a full lifecycle with a future-proof outlook that will keep cloud usage in check, ensuring that growth continues without security risks.
Another way to manage cloud sprawl is to build a company-wide cloud strategy that includes all stakeholders. The cloud strategy should include policies on using and managing the cloud, migration efforts, and identity controls and access. Automation of the right tools is recommended as part of a holistic strategy to contain and avoid potential sprawl.
Constantly monitoring and managing the cloud throughout a business can be a time-consuming and expensive ongoing process. While cloud sprawl can lead to out-of-control spending and unnecessary risk, the effort required to reign it in may feel even more cumbersome or even impossible if done manually. By working with a cloud security platform, your organization can enlist the help of cloud security experts to receive the end-to-end visibility, insights, controls, and support needed to effectively and affordably deploy any cloud strategy.
What to Solutions to Include in Your Strategy

CSPM
To tackle your overall platform security risks, you’ll want a CSPM (Cloud Security Posture Management) solution. CSPM tools assess anomalous activity, compliance cloud drift and your overall security posture before a security threat comes around. CSPM will continuously monitor the cloud environments in real-time for threat detection and automatically assess your security posture by comparing the current state to a secure baseline. This level of visibility helps you gain visibility and control over your entire platform. This is the foundation of your cloud.

CIEM
The best solution to tackle identity sprawl is a Cloud Infrastructure Entitlement Management (CIEM) tool. CIEM will offer you a full identity inventory and insight into the effective permissions of those identities, allowing your organization to terminate dangerous access controls and reach least privilege. Finally, CIEM includes continuous monitoring of identity concerns so you not only reach the least privilege, but stay there.

CDLP
Data Loss Prevention allows you to not only know where your data is, but know its movement and access history. Finding your data is just the first step, but a necessary one in order to classify and tag your data so you know exactly what it is. From there you can achieve Least Access and monitor who and what can access your data.
While you can buy each of these solutions individually, we do recommend using one uniform platform, to get a true picture of your cloud’s security state, as platform, data, identity and workload security does not work in isolation. Consider exploring our Cloud Security Platform to see if it will help with your cloud sprawl.
—
This article was first published on Security Magazine. See the original publication here.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Read the latest news and insights
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.






