Table of Contents

Share this entry

Vulnerability management is nothing new to the cybersecurity world, but the paradigms, practices and solutions built for on-prem management are not holding up in the cloud. This calls for a new approach to vulnerability management.
Where networks once comprised the security barrier to breach in the on-prem days, identity now stands. Infrastructure-as-Code and developers rule the kingdom, meaning AWS services like EC2 instances are building the bones of your environment and taking on roles. These EC2 instances are built new daily, each being spun up and down for seconds or minutes at a time several times a day – making a virtual machine an elusive thing to catch and secure. Each of these instances becomes a machine identity, meaning your environment can have hundreds, if not thousands, of machine identities all coming into contact with your data. This scale can quickly become a problem, when you’re looking to tackle vulnerability management.
Today, businesses need an automatic and continuous way to detect vulnerabilities in their workloads, but also prioritize their remediation based upon greatest risk and business impact. And that measurement of potential business impact can only come from insight into how vulnerabilities tie back to identity and data. When teams are overwhelmed and fatigued, organizations need to focus on the vulnerabilities that offer attack paths to high-value assets first. That insight only comes from the unique ability to see every permission and access right on any given cloud workload. Below, we’ll examine how Sonrai integrates with Amazon Inspector to provide identity insights and prioritize vulnerability findings.
Find Sonrai Security on the Amazon Inspector Partners Page.
Amazon Inspector
Amazon describes Inspector as “an automated vulnerability management service that continually scans Amazon Elastic Compute Cloud (EC2) and container workloads for software vulnerabilities and unintended network exposure.” They continue by listing the following additional benefits of Inspector:
- Automated discovery and continual scanning that delivers near real-time vulnerability findings
- Central management, configuration, and view of findings for all your organizations’ accounts by setting a Delegated Administrator (DA) account
- A highly contextualized and meaningful Inspector risk score for each finding to help you set more accurate response priorities
- An intuitive Amazon Inspector dashboard for coverage metrics, including accounts, EC2 instances, and Amazon Elastic Container Registry (ECR) repositories being actively scanned by Amazon Inspector
- Integration with AWS Security Hub and Amazon EventBridge to automate workflows and ticket routing

Tools like Amazon Inspector are built to offer continual scanning for vulnerabilities or network exposure in EC2 or container workloads, however the security story does not end with just vulnerability scanning. When risks are detected, how can a business establish a pecking order for remediating these concerns without detailed context into business impact? Consider an EC2 instance with a low-level identity sufficiently at least privilege on it vs. a container with a non-person identity on it that has access to customer information in Production through a trust policy. Both have vulnerabilities, and your scanner detects both – but how do you get this complete picture and prioritize and remediate as needed?
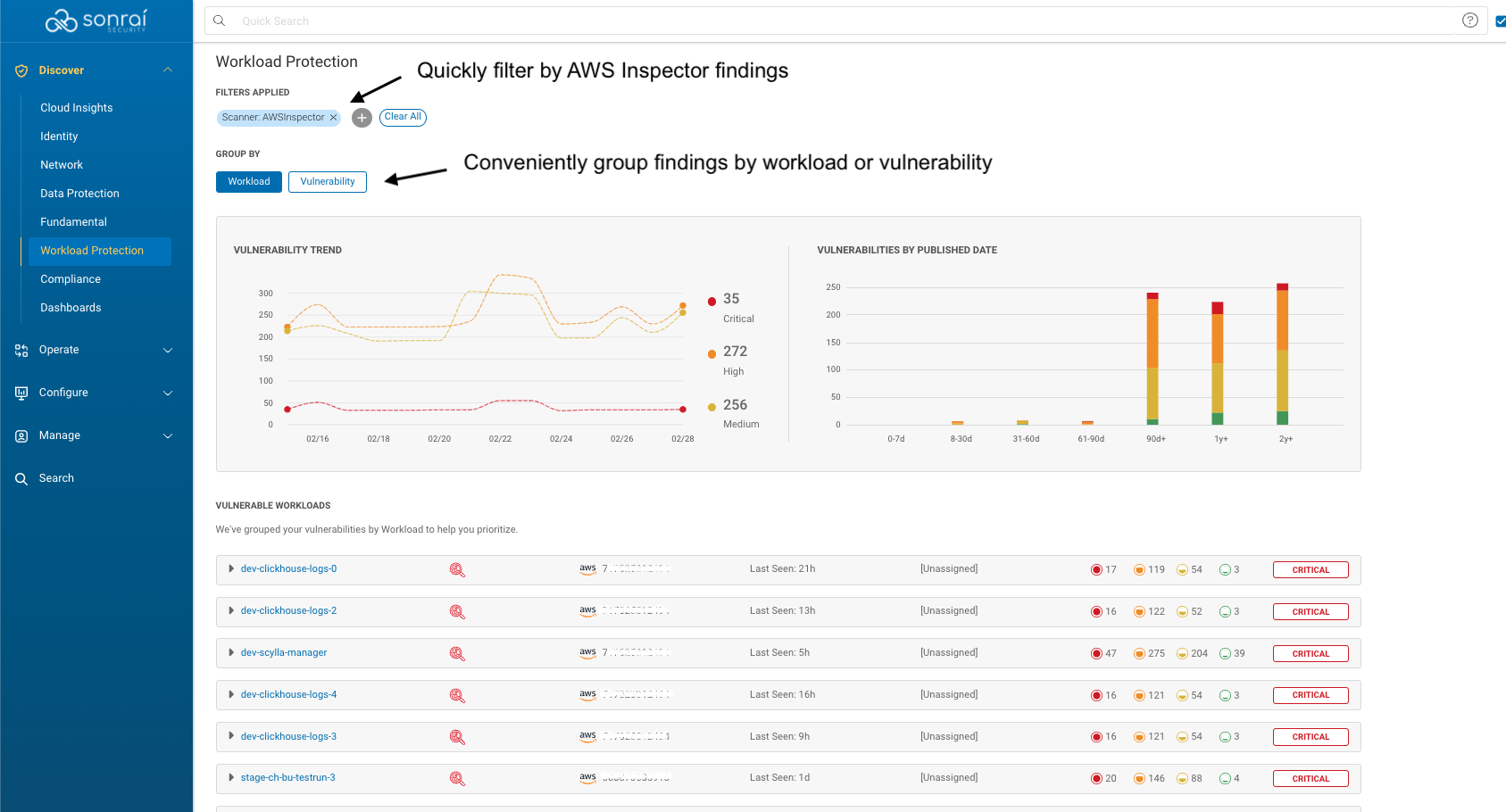
Prioritizing Amazon Inspector Findings with Sonrai Identity Insights
Amazon Inspector Next is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure, with the help of the Sonrai platform.
This integration allows Sonrai to monitor and immediately alert changes to critical resource attributes, including vulnerable packages, encryption status, permissions, public access, and version changes. Sonrai’s integration with Amazon Inspector will push events in near real-time, and these findings will be injected into the Findings database and enhanced with risk amplifiers. This means, your team will have insight into what vulnerability findings are your top priority based on if the workload has access paths to critical data. This capability is backed by Sonrai’s patented identity and data graphing and analytics, providing additional context to the risks found by Inspector, and prioritizing which risks should be tagged for urgent remediation.
All relevant risks to sensitive data – vulnerabilities, platform misconfigurations, privilege escalation capabilities on the host, privilege abuse possibilities – are in a single view, contextualized and prioritized with metadata. In judging the risk level of a vulnerability for prioritization, Sonrai considers “Risk amplifiers” for each host to determine the potential blast radius and rank sensitivity. This ultimately reduces alert fatigue and consolidates multiple processes into one sophisticated ticketing engine.
Once software vulnerabilities and associated host risks are discovered, AWS Inspector customers can use Amazon EventBridge to kick off a workflow to patch. The remediation of the associated identity, platform, and data risks can then be handled with Sonrai’s automated remediation workflow, or integrated with other ticketing systems already in palce. Sonrai’s remediation workflow can be built into customized ‘swimlanes’ so your process reflects the actual team’s in your organization, or addressed with automated bots.
Better Together with AWS

During his keynote at last year’s re:Inforce conference, Amazon CSO, Stephen Schmidt remarked that, ‘we’re stronger together.’ Schmidt refers to Amazon’s partnership with other cloud security providers, like Sonrai – and we’d have to agree.
AWS and Sonrai Security have proven to be stronger together. Sonrai is part of the AWS Advanced Technology Partner Network and strives to assist AWS customers by reducing risk and embracing the cloud.
“Sonrai’s vision of total cloud security benefits from the deep integration and orchestration with all AWS security services,” said Tilak Yalamanchili, Vice President of Business Development at Sonrai Security. “By pursuing integrations with tools like AWS InspectorNext, Guard Duty and AWS Security Hub, Sonrai seamlessly fits into the customer’s tech stack — giving security teams unique context to identify fixes that must be addressed immediately.”
Sonrai worked with AWS to sponsor a Forrester research report titled, “Identity Controls Are Central to Enterprise Plans for Cloud Security.” This survey study focused on the relationships between cloud security and identity controls and found that organizations continue to increase both their usage of public clouds and the number and types of tools they use to secure their data in them. In fact, organizations use on average six tools, yet 56% say that machines and non-people identities are out of control in the cloud. For the complete findings, explore the full report.
AWS nominated Sonrai Security as a recommended provider of privileged identity management in their eBook with the SANS Institute titled, ‘Top 6 Emerging Security Trends.’

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




