Table of Contents

Share this entry

Gartner recently published a report titled, “Emerging Tech: CIEM Is Required for Cloud Security and IAM Providers to Compete,” and there are two overarching takeaways you’ll want to note: The first is that IAM vendors will need to incorporate CIEM capabilities to survive in the market; the second is that CIEM providers will only succeed in the market if they incorporate the trends that Gartner goes on to list. Sonrai Security was successfully noted as a ‘Sample Provider’ for CIEM, so we wanted to take a moment to review the significant findings in Gartner’s report and offer advice on how to navigate picking a CIEM provider.

Gartner Report Key Findings
Gartner reports that Cloud Infrastructure Entitlements Management is an evolving technology that many providers in the IAM sphere are adding to their platform, thus increasing the market competition. The report also notes CIEM’s strength as the ability to deliver value across an enterprise, outside of developer-centric use cases. Today, enterprises face emerging threats like supply-chain attacks and exemplify the need for identity threat detection response solutions – CIEM essentially meets these needs. The last major point regarding the widespread adoption of CIEM solutions is Gartner’s proposition that visibility into entitlements and managing permissions are quickly becoming ‘must have’ offerings in CIEM solutions. Sonrai Security would have to agree.
Regarding Gartner’s recommendations to Cloud Native Application Protection Program (CNAPP), Cloud Security Posture Management (CSPM), Identity Governance and Administration (IGA), Cloud Workload Protection Platforms (CWPP), and Security Service Edge (SSE) providers to adopt CIEM capabilities, they specifically note the following needs:
- Must prioritize CIEM capabilities within their roadmap to remain competitive.
- Must gain a further competitive edge in the CIEM market by investing in more-advanced guided remediation capabilities, such as automated downsizing of overprivileged accounts.
- Must appeal to a larger audience beyond cloud security teams by positioning CIEM as part of broader enterprise security controls.
What is CIEM?
CIEM is next-generation cloud security technology that grants, resolves, enforces, revokes, and administers access. CIEMs aim to manage entitlements, remediate cloud access risk, and enforce the principle of least privilege across multi-cloud environments to reduce excessive permissions, access, and cloud infrastructure entitlements.
What to Expect from a CIEM Solution
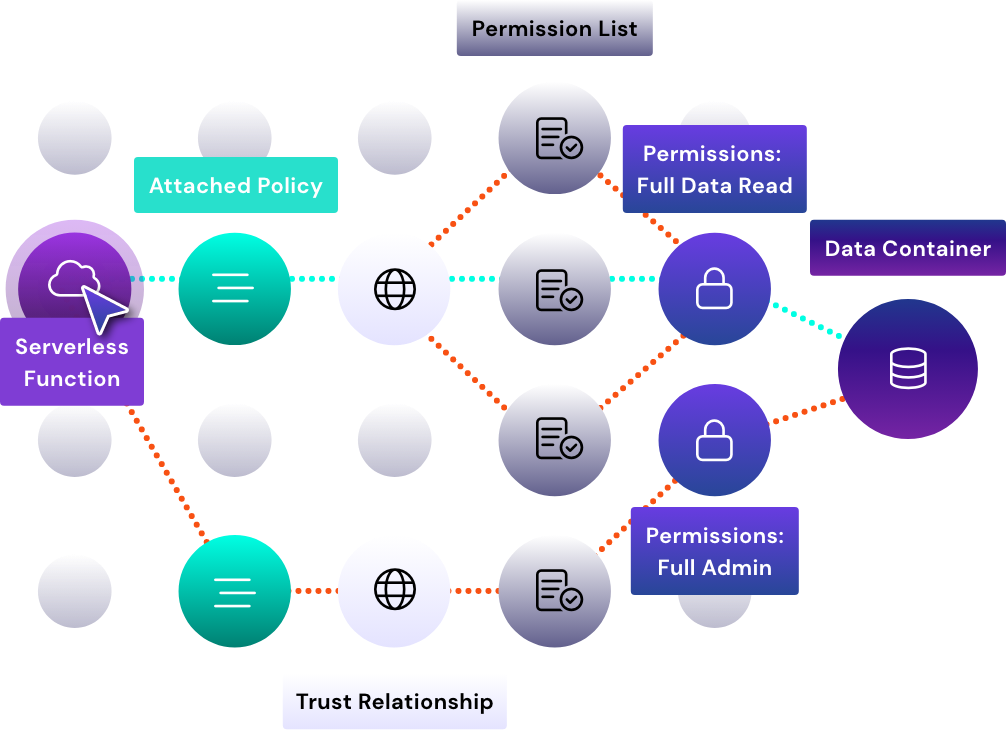
By leveraging a CIEM, enterprise organizations can lock down and secure data at the scale and speed of the cloud. Using the identity inventory and their effective permissions (cloud entitlements) from a CIEM tool, organizations can now determine what data identities can access, how they can access the data, and what they can potentially do with the data. With this continuous visibility, teams can effectively determine where they have risks and then, in turn, manage the risks to ensure that the cloud environment and the data within it stay secure.
The right CIEM needs to not only be able to inventory your people and non-people identities and determine their effective permissions, but also work at the scale and speed of your cloud. CIEM proves to be incredibly important in modern cloud deployments by providing teams with the capability to keep up with rapid identity growth – whether it’s growth of your employee pool as your company scales, or an expanding number of non-person identities like roles or virtual machines.
How to Select a CIEM Provider
Adopting a CIEM solution can be overwhelming as the market is quickly becoming saturated (as supported by Gartner.) To help accommodate this process we’ve listed some recommendations on what features to consider when evaluating a provider:
Entitlements Protection
Your solution should be able to detect changes within any and all managed cloud infrastructure environments so you can remediate concerns.
Account and Entitlements Discovery
Your CIEM solution should be able to take an inventory of identities and entitlements across your enterprise’s cloud infrastructure. Continuous, event-based discovery, identification, and management of all identity types (people and non-people,) analyzing all access policies, and discovery of any federated and native cloud identities.
Entitlements Optimization
Your solution should determine least privilege entitlement assignments through usage data generated by privileged operations across cloud infrastructure combined with entitlement data.
Graphing and Visualization
Ideally your solution should be able to graph and visualize your real-time inventory and all entitlements as the magnitude and complexity of cloud makes table-driven visualization unfeasible.
Prevention
If there is a misconfiguration or any other kind of risk in the environment, it will be inherited by all instances provisioned and deployed unless your CIEM provider can inspect and assess the security posture impact of the identity, prior to deployment.
Granular Visibility
Your solution should offer deep and centralized visibility that is integrated with all environments and entities across your infrastructure. The more granular the better – you want to be able to see every connection between identity and data.
Continuous Compliance
Sporadic or periodic compliance checks are not sufficient due to continuous integration and the nature of cloud’s ephemeral resources like containers, serverless functions, and microservices. Your CIEM solution should offer continuous monitoring.
Customizable & Flexible
Every business is unique, so your cloud security configurations should be too. Ideally you can utilize out-of-the-box CIEM features, but also be able to customize settings to your business needs.
Reporting
Your CIEM solution provider must allow you to easily query data and identities in order to gain meaningful insight into the different aspects of your organization’s security status. It should provide a toolbox of out-of-the-box yet customizable reports.
Cross-cloud Capabilities
Many organizations are working in multiple cloud platforms, so your CIEM solution should be able to correlate identity management across multiple clouds for one consistent and centralized view.
Remediation
Your CIEM platform needs to have the ability to detect cloud infrastructure threats and respond to those events by remediating or alerting the correct team at the right time with a sense of urgency.
This list is not exhaustive, and for a more in-depth review and checklist, you can explore our CIEM Buyer’s Guide.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




