Table of Contents

Share this entry

The cloud is all about innovation at a speed never before possible. This can often lead to rapid development sprints and a proliferation of identities and infrastructure – and with that, excessive privilege. In large scale enterprises, IAM governance can be difficult. To accommodate this, Amazon Web Services (AWS) created Service Control Policies. The following guide will:
- Define what a Service Control Policy (SCP) is.
- Define its functionality in a larger governance strategy.
- Detail challenges associated with implementing them.
Understanding Service Control Policies in AWS
A service control policy is a set of controls at the organizational unit that restricts the maximum level of permissions that users, roles, and even root users in AWS accounts can hold. They act as guardrails, trumping all other levels of policy to ensure security standards are consistently applied across the organization.
SCPs are particularly important in large-scale enterprises where managing and enforcing consistent policies across numerous accounts is a complex task. This centralized governance model is essential for maintaining a balance between enabling access and enforcing security and compliance across the AWS environment.
SCP benefits include:
- Accommodate enterprise-grade scale and multi account environments.
- Centralized control over privilege governance.
- Help meet regulatory or corporate requirements.
- Helps build custom environments tailored to specific data security or access management needs.
- Inheritance of policy from OU down the hierarchy to accounts means less manual efforts
- More development freedom to manage their own permissions because you’ve set guardrails for them.
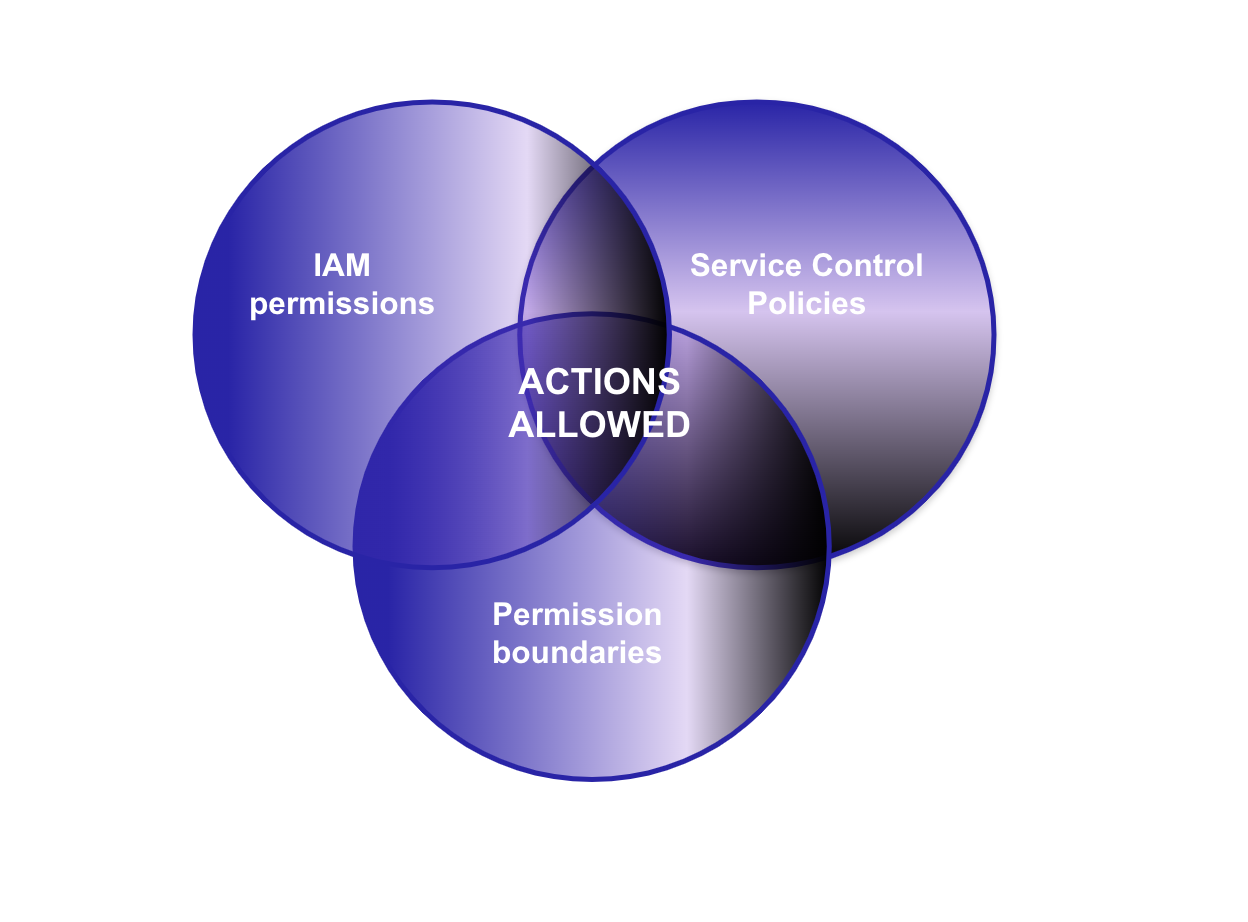
Components of Service Control Policy
Understanding the components of an SCP is the first step before implementing them:
- Statement: The core of the policy, defining permissions or restrictions.
- Statement ID (Sid): A unique identifier for each statement, aiding in policy management and troubleshooting – e.g. DenyAllOutsideEU
- Effect: Determines whether the policy results in an ‘allow’ or ‘deny’ statement.
- Action: Specifies the actions the policy allows or denies – e.g. s3:* for all Amazon S3 actions.
- NotAction: Specifies what is not covered by the policy, useful for broad permissions with specific exceptions.
- Resource: Defines the AWS resources to which the policy applies, using ARNs (Amazon Resource Names).
- Condition: Additional criteria that refine the policy’s application, such as date, time, or user attributes – e.g. aws:SourceIp

How Do AWS Service Control Policies Work?
SCPs are part of the AWS Identity and Access Management (IAM) framework but serve a distinct purpose. Unlike IAM policies that grant permissions, SCPs are used to define limits and restrictions. They do not grant permissions but instead act as a filter over the permissions that can be exercised within an AWS account.
SCPs are applied at the AWS Organization or Organizational Unit (OU) level, affecting all accounts within that scope.
SCP Allow: Sets the boundaries for what actions IAM policies can permit but does not grant permissions itself. For ‘allow’ to work, there must be a statement made at every level from root through each OU to the account you want affected. An SCP is deny-by-default otherwise.
SCP Deny: When an SCP includes a ‘deny’ statement, it explicitly prohibits certain actions, regardless of any other permissions that might be granted elsewhere. In the example below you can see a ‘deny’ statement at the OU level disrupting the ‘allow’ statement at the account level.
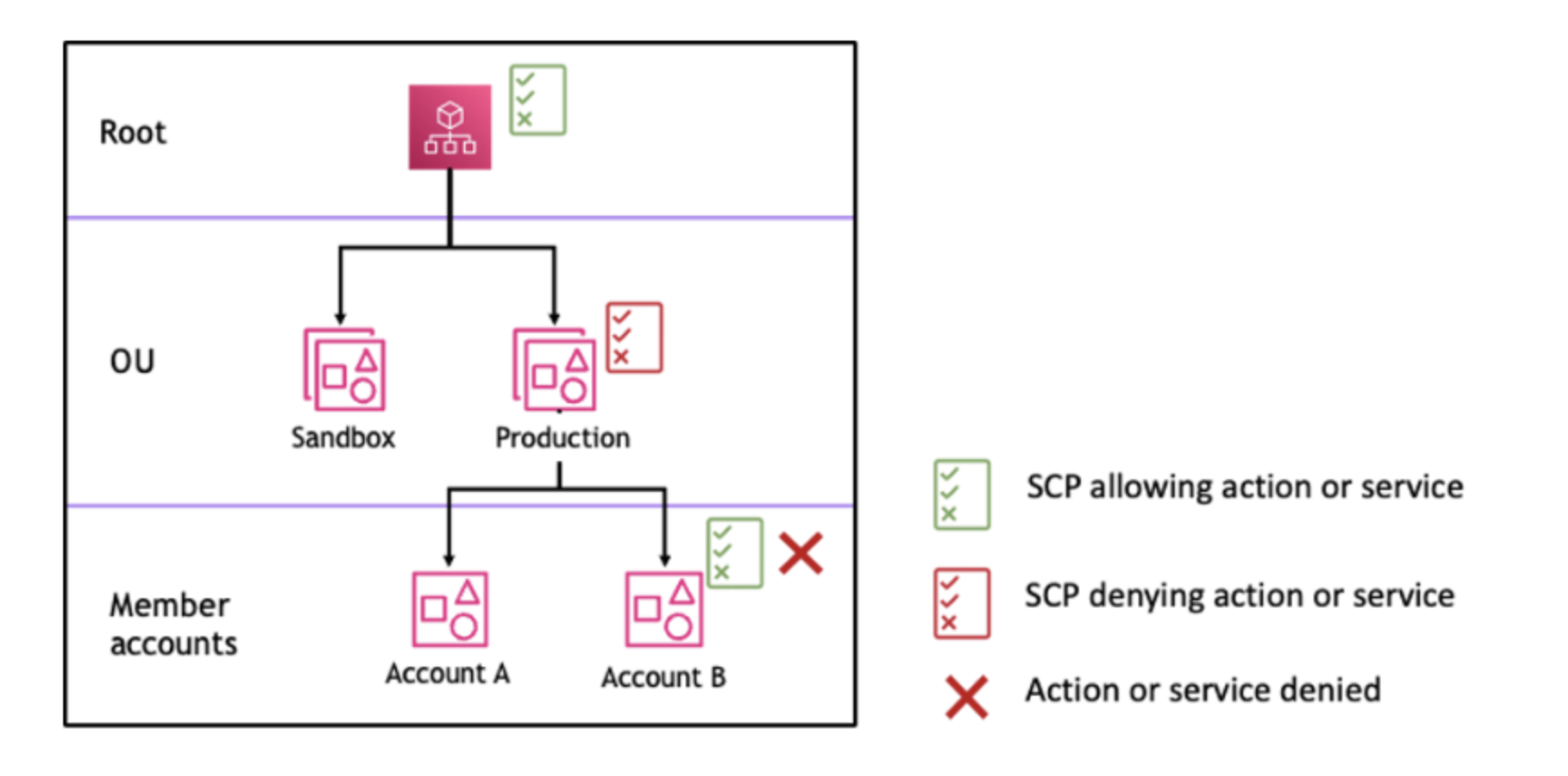
Source: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_scps_evaluation.html#strategy_using_scps
AWS SCP vs IAM Policy: Key Differences
With so many variations of policies in AWS, it can get difficult to keep track. Here are how SCPs and IAM policies compare:
- Scope: SCPs apply at the organization or OU level, while IAM policies are applied at the user, group, or role level within an individual AWS account. Within IAM policies there are identity-based and resource-based policies in AWS.
- Permissions Granting: IAM policies grant permissions, whereas SCPs only restrict or filter permissions.
- Hierarchy: SCPs are at the top of the permission hierarchy in AWS. Even if an IAM policy grants a permission, an SCP can override this by denying it.
Setting Up a Service Control Policy
Before actually implementing an SCP in AWS, your team will likely follow a process similar to the following: 1) Pitching the use case for one 2) Requesting usage 3) Security Team or equivalent team analysis of the SCP use case 4) Map possible usage scenarios and necessary testing. Finally, you’ll be ready to actually execute building one out.
To set up SCPs in AWS, follow these steps:
- Create an AWS Organization: Establish your AWS Organization for centralized management.
- Enable Service Control Policies: Activate SCPs within your organization settings.
- Create an AWS SCP: Define your SCP, specifying the allowed or denied actions and resources.
- Choose Your Statement: Decide between ‘Allow’ and ‘Deny’ statements based on your requirements.
- Add Conditions (Optional): Specify conditions for more granular control.
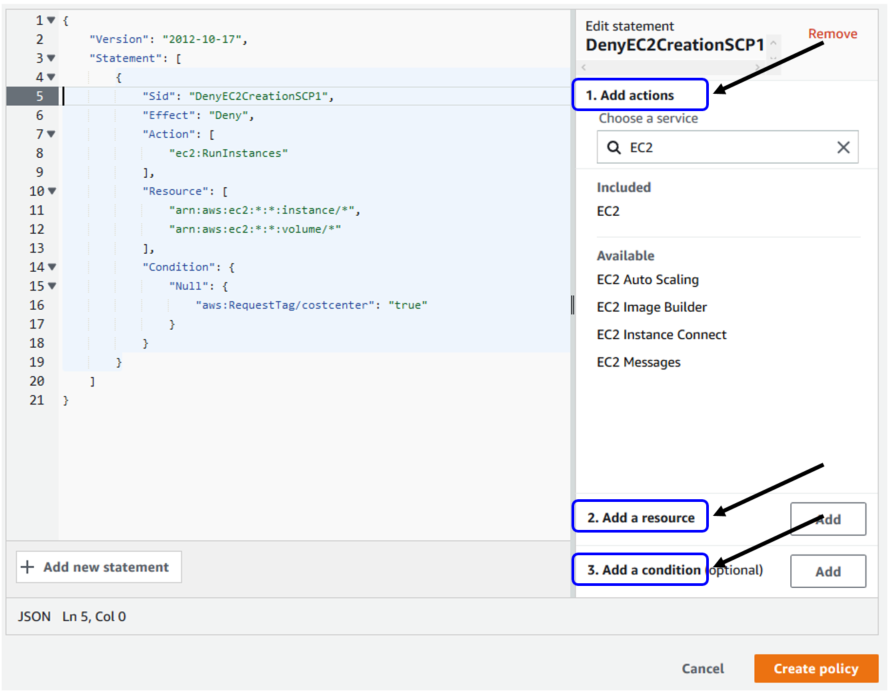
Source: https://aws.amazon.com/blogs/mt/implement-aws-resource-tagging-strategy-using-aws-tag-policies-and-service-control-policies-scps/
3 AWS SCP Best Practices and Tips
- Use the management account judiciously: Reserve the management account for administrative tasks only and apply SCPs primarily at the OU level.
- Test your SCPs before application: Implement SCPs in a controlled environment before rolling them out organization-wide to avoid disrupting or breaking other processes.
- Give your policy a name and description that will make it easily recognizable and understandable, e.g. ‘DenyChangestoS3.’
AWS SCP Example
Sensitive data protection.
Here’s an example of an SCP used for sensitive data protection. It denies users from deleting S3 buckets or objects:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Action”: [
“s3:DeleteBucket”,
“s3:DeleteBucketPolicy”,
“s3:DeleteObject”,
“s3:DeleteObjectVersion”,
“s3:DeleteObjectTagging”,
“s3:DeleteObjectVersionTagging”
],
“Resource”: [
“arn:aws:s3:::[BUCKET_TO_PROTECT]”,
“arn:aws:s3:::[BUCKET_TO_PROTECT]/*”
]
}
]
}
Denying Root User
This example enforces a security best practice – denying any usage from the root user. See below:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “RestrictEC2ForRoot”,
“Effect”: “Deny”,
“Action”: [
“ec2:*”
],
“Resource”: [
“*”
],
“Condition”: {
“StringLike”: {
“aws:PrincipalArn”: [
“arn:aws:iam::*:root”
]
}
}
}
]
}
Service Control Policy Use Cases
As we know, SCPs are used to enforce organizational guardrails and uphold security. Some more specific use cases for them include:
Denying changes to security services: AWS offers security monitoring and detection services that help keep an eye on your environment and alert to threats. You can use guardrails to ensure no accounts can alter these services and disrupt protection.
Privileged access controls: If your organization has certain privilege or access standards you want maintained across the org, you can use an SCP to limit maximum permissions.
Regional controls: In multi-account environments, you can inhibit usage within certain regions.
Data security and protection: To protect data, you can use an AWS SCP to ensure only specified identities are accessing specific data or enforce that no members can change configurations on data services like S3.
AWS SCPs: Addressing the Challenge
Visibility
The complexity of managing multiple overlapping policies, including SCPs and IAM policies, can lead to a lack of visibility and control. It’s essential to have a clear understanding of the cumulative effect of these policies on your AWS environment, otherwise potential challenges arise.
Without proper visibility your identities can end up with access you never authorized. As we know, privilege can easily be inherited in the cloud, making it harder to see ‘on paper.’ This type of unseen privilege can result in opportunities for lateral movement. That lateral movement can be exploited by malicious attackers.
On the contrary, implementing too conservative of a strategy with hefty denial via Service Control Policies, you end up with development interruption and inefficient request processes.
Responsibility
Cloud security generally faces a confusing distribution of responsibility because it is a new frontier. There is discrepancy between who builds the cloud (and consequentially influences the security of it) and who manages security and IAM. Defining who owns Service Control Policies is up to the discretion of an enterprise (e.g. DevOps vs. Security teams vs. Governance teams) but this lack of definition can lead to gaps, confusion and not using the feature to its full potential.
The answer is a solution with both the technology to compute effective permissions – the logical intersection of how all these IAM policies and SCPs interact with each other — and operationalized workflows for building and remediating.
Protect Sensitive Permissions With Sonrai
Frustrated working with SCPs? Don’t know where to start, but know you want to set up org-wide guardrails? Sonrai’s Cloud Permissions Firewall works top-down to protect your most sensitive permissions. Anything your identities don’t need is restricted from use, with exceptions made to those who do need it. New access is granted on the fly with a permissions-on-demand workflow integrated into your ChatOps tool. Sound good?

FAQ
- How do AWS Service Control Policies (SCP) impact the cost and efficiency of AWS resource utilization in an organization? AWS Service Control Policies (SCP) can significantly influence both the cost and efficiency of AWS resource utilization within an organization. By enabling administrators to set permissions that limit the actions users and roles can perform, SCPs help prevent unauthorized access or inadvertent expenses by restricting resource deployment in unauthorized regions or the use of high-cost services.
- Can AWS SCPs be integrated with third-party security and compliance monitoring tools, and if so, how? While AWS SCPs are designed to work within the AWS environment, integrating them with third-party security and compliance monitoring tools is possible through the use of AWS APIs and other intermediary software solutions that bridge AWS configurations with external systems. This integration allows for enhanced monitoring, reporting, and compliance management across both AWS and non-AWS resources.
- What are the specific challenges or limitations when migrating existing IAM policies to SCPs within large, complex AWS environments? Migrating existing IAM policies to SCPs in large, complex AWS environments presents specific challenges, including the need to comprehensively understand the existing permissions landscape, ensuring that SCPs do not inadvertently block critical business operations, and managing the hierarchical nature of SCPs to effectively apply the principle of least privilege. This process requires careful planning, testing, and gradual implementation to avoid disruption.
THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




