Table of Contents

Share this entry

The extensive set of AWS services and resources can make it challenging to manage permissions effectively. Given the substantial variations in use cases and necessary permissions across different applications and workloads, AWS users expressed the need to empower their developers to independently create and manage IAM roles and policies, all while maintaining security guardrails to establish upper limits on permissions.
This is where AWS permission boundaries step in, playing a pivotal role in enhancing security. In this blog, we’ll delve into the world of IAM boundaries, helping cloud and security professionals understand what they are, how they work, and why they are essential for securing AWS environments.
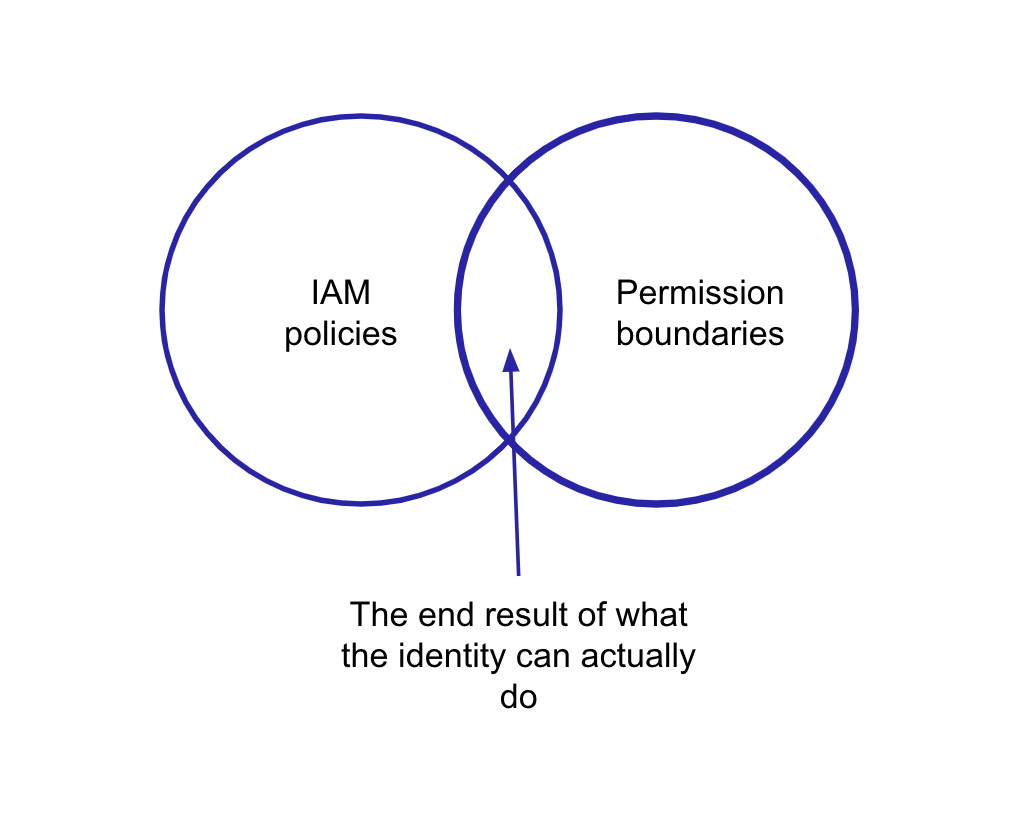
What Are AWS Permission Boundaries?
AWS Permission Boundaries serve as a crucial component of Identity and Access Management (IAM) within AWS. These boundaries act as a tool to set the maximum permissions an identity can have, ultimately ensuring that users have the appropriate level of access while maintaining security safeguards. To put it simply, AWS permission boundaries define the maximum permissions a user or role can have, effectively acting as protection against overprivileged access.

How Do AWS Permission Boundaries Work?
Understanding the mechanics of an AWS permission boundary is essential for effectively implementing them. These boundaries operate by providing an additional layer of control in the AWS IAM system. When policies are attached to an IAM entity, these policies define what actions and resources a user or role can access. However, AWS permission boundaries come into play after the policies are evaluated.
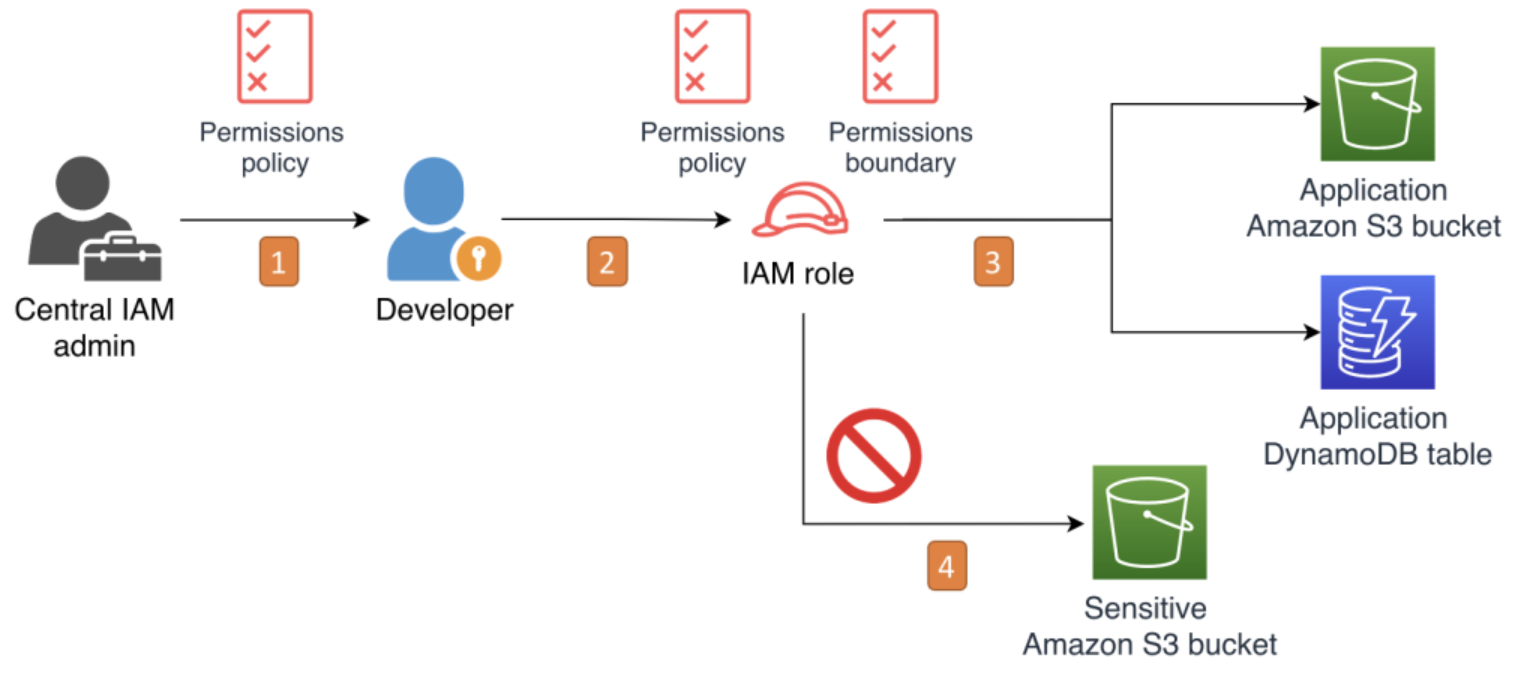
Here’s a simplified breakdown: When a user or role attempts an action, AWS checks not only the policies attached to the user or role but also the permission boundary associated with the user. The permission boundary acts as an upper limit, ensuring that the user or role cannot exceed the permissions defined within the boundary.
It’s important to note that a boundary trumps other IAM policies. Consider a developer with access to the S3 service and to AWS cloud watch via a role with a policy attached to it. If you add a permission boundary to that role setting their max permissions to the S3 service alone, they won’t be able to access CloudWatch–even if the IAM policy says so.
Here’s a visual representation of how these boundaries work in the larger flowchart process of determining access in AWS:
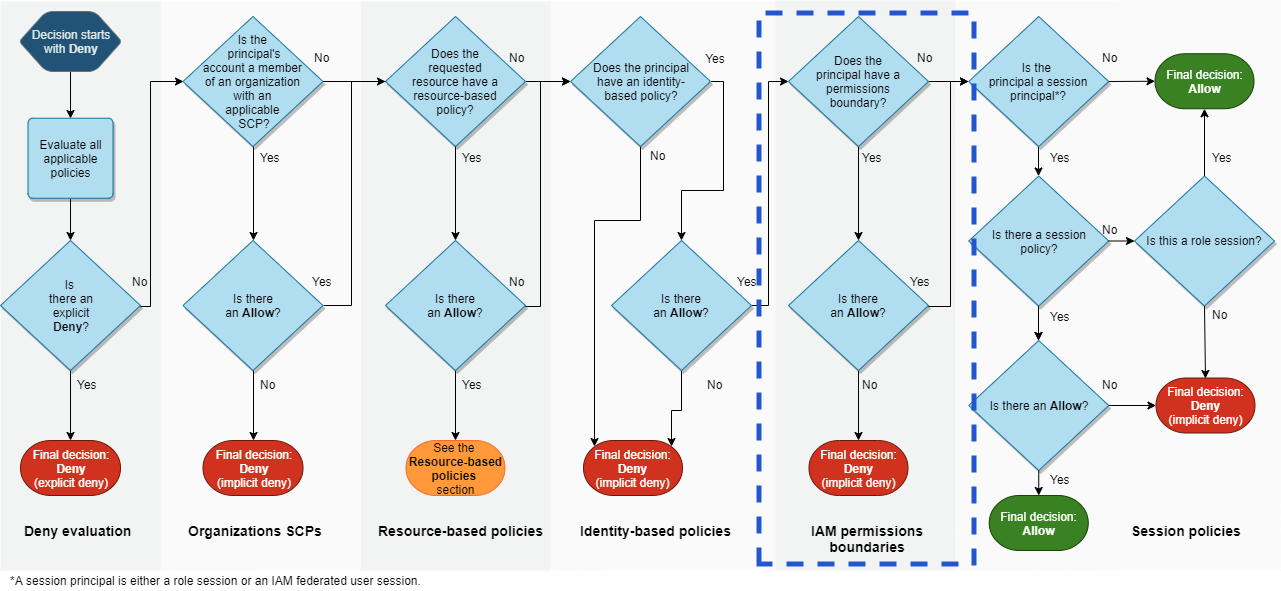
Learn more about AWS resource-based policies and identity-based policies.
5 Key Benefits of Using AWS Permission Boundaries
Now that we understand the basics, let’s explore the five key benefits of using AWS permission boundaries for access control:
1. Granular Access Control
AWS permission boundaries allow for precise control over permissions, ensuring that users or roles are granted only the permissions necessary for their specific tasks. This granular control reduces the risk of unauthorized access to critical resources.
2. Prevention of Over Privileged Users
By setting strict upper limits on permissions, AWS permission boundaries help prevent overprivileged users or roles, reducing the chances of accidental data exposure or security breaches.
3. Improved Compliance and Governance
AWS permission boundaries are a valuable tool for maintaining compliance with industry regulations and internal governance policies. They provide clear boundaries that align with compliance requirements.
4. Simplified Access & Policy Management
Managing permissions and policies becomes more straightforward with AWS permission boundaries. Instead of complex policies, you can rely on well-defined boundaries, making it easier to understand and audit permissions.
5. Scalable Permissions
As your AWS environment grows, IAM boundaries help scale with it. You can consistently enforce access control, whether you have a handful of users or a large, complex organization.
Setting Up AWS Permission Boundaries: 8 Best Practices
Implementing AWS permission boundaries effectively requires careful planning and adherence to best practices. Here are eight essential guidelines to consider:
1. Apply Permissions Boundaries to IAM Roles, Not Developers
Attach AWS permission boundaries to IAM roles rather than individual developers. This ensures consistent control over permissions across teams and simplifies management.
2. Use IAM Identity Policies and AWS Organizations SCPs
Complement AWS permission boundaries with IAM identity policies and AWS Organizations Service Control Policies (SCPs) to create a robust access control strategy.
3. Avoid Replicating Developer Policy Space to Permissions Boundaries
Setting a permission boundary should not replicate the policies developers already have. Instead, they should restrict access beyond what those policies grant.
4. Group Permissions Boundaries into Categories
Organize maximum permissions into categories based on teams or functions, making it easier to manage and track access control.
5. Adapt Boundaries to Common Business Purposes
Customize permission boundaries according to your organization’s specific needs and business processes to optimize security and efficiency.
6. Apply the Least Privilege Principle
Always adhere to the principle of least privilege, granting the minimum permissions necessary for users or roles to perform their tasks.
7. Be Conscious of Cross-Account Access
Consider the implications of cross-account access when defining AWS permission boundaries. Be vigilant in managing permissions across accounts.
8. Document and Label Accordingly
Thoroughly document your AWS permission boundaries and use clear labels to ensure proper understanding and easy maintenance.
Examples of AWS Permission Boundaries
Let’s take a look at some practical examples of AWS permission boundaries in action.
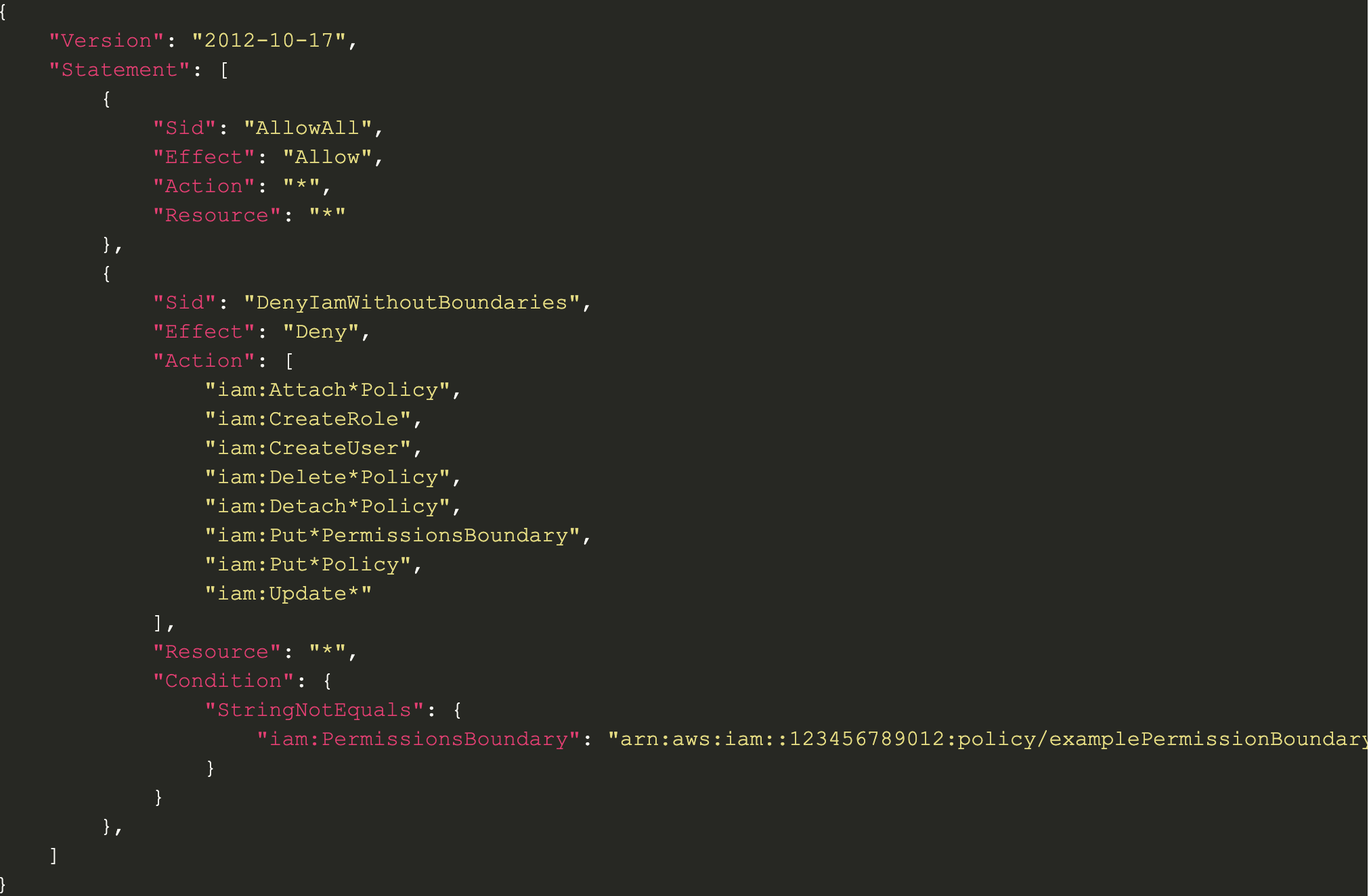
The image below captures a permission boundary that only allows new identities or roles to be made if they have permission boundaries attached to them. This is a great way to ensure new roles have controls to prevent them from being overprivileged or unrestricted.
Next let’s consider an example from AWS documentation. For example, you want to limit a user to only specific resources. You can create the following permission boundary to limit the user to CloudWatch, S3 and EC2. Any other identity-based policies offering further access would be voided. Again, a great way to limit the scope of any given identity’s access.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:*",
"cloudwatch:*",
"ec2:*"
],
"Resource": "*"
}
]
}
Use Cases: When Should You Use Them?
AWS permission boundaries are incredibly versatile and can be applied in various scenarios to enhance cloud security:
Multi-Tenant Environments
In multi-tenant environments, where multiple tenants share AWS resources, AWS permission boundaries help isolate and protect each tenant’s data and resources.
Third-Party and Cross Account Access
When granting third-party vendors or partners access to your AWS environment, permission boundaries ensure they can only access the resources necessary for their specific tasks.
Complex IAM Policies
In organizations with complex IAM policies, AWS permission boundaries simplify policy management and provide an additional layer of security.
Regulatory Compliance Requirements
For industries with stringent regulatory compliance requirements, AWS permission boundaries facilitate compliance by clearly defining access controls.
Resource-Level Access Control
When fine-grained control over resource access is essential, permission boundaries enable precise management and auditing of permissions.
Take Your AWS Identity Security to the Next Level with Sonrai Security
Sonrai Security provides a comprehensive cloud identity and access solution to:
- Ensure secure access control in complex AWS environments.
- Identify and remediate security risks.
- Monitor and audit permissions effectively.
- Enhance compliance with industry regulations.
Computing the net result of different permission levels – organizational guardrails, permission boundaries, IAM policies, resource-based policies, and more – is extremely complex. Sonrai’s patented permission analytics automatically computes the net privilege of every identity in your environment — taking into account every AWS permission boundary, policy, or org guardrail. The Toxic Permissions Analyzer then reveals the dangerous permissions creating unintended attack paths so your teams can break the chains and protect business critical assets. Sonrai Security integrates with other AWS security tools.
Ready to see it in action? Request a personalized or on-demand demo to see how we secure AWS.

THE ARCHITECT
The Newsletter for Cloud Security Leaders. 1x a month.
Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




