Table of Contents

Share this entry

Don’t know where to start? Feeling stuck in your goal to secure cloud identities?
We have a simple strategy we guide customers through at Sonrai. It is built to reduce cloud identity and access risk in the most efficient way possible. The strategy is centered around addressing the top four greatest identity risks in your cloud.
- Unknown Admins
- Unused Identities
- Overprivileged Identities
- Lateral Movement
Why are these the greatest identity risks?
Below, we will walk through the four steps you can take to reduce attack paths to enterprise assets, opportunities for cloud hijacking, and potential for business disruption.
We recommend addressing these risks in this particular order. This is a compounding strategy where the order of risk removal is intentional for maximum impact with minimal effort. Starting by remediating unknown inherited admins and removing unused identities has trickle down effects that reduce the occurrence of overprivileged identities and lateral movement opportunities.
Let’s begin!
Step 1: Discover and certify all admins
Getting visibility into your privileged identities sounds easier than it is. That is because we choose our admin identities, right?
Not quite in the cloud. The reality is a significant number of identities with admin-level privilege are unknown to you. They were never explicitly assigned administrative rights. Instead, they inherited privilege through other means. This is especially prevalent among machine identities. Privileged Access Management (PAM), Governance tools (IGA), and cloud-native directories will not see these admins.
Unknown admins means unprotected admins.
These unknown privileged identities host all sorts of problems like unintended access to data, overprivileged identities, opportunities for privilege escalation, privilege gathering, and so on. As we know, admins rule the tenant, organization, and environment. If adversaries get their hands on them it is likely disastrous.
How to fix it
Certifying that admin identities should or shouldn’t have privilege is the easy part. The difficult part is discovering those unknown admins. Luckily, this is the beauty of Sonrai’s technology. The patented analytics compute all possible privileges – especially the kind your teams never directly assigned. So it is THAT easy to just see ALL your admins.
Just navigate to the ‘Identity Inventory’ and filter by ‘Admin’ (1) – there is a complete list. We handle the backend computing for you.
Investigate each admin (2) and determine if privilege is authorized or not with our certification process. Certification is critical so you don’t accidentally remove a break glass or unused required admin in the next step. If not, click-through to our remediation steps (3) – either prescriptive manual instructions or automated bot remediation.
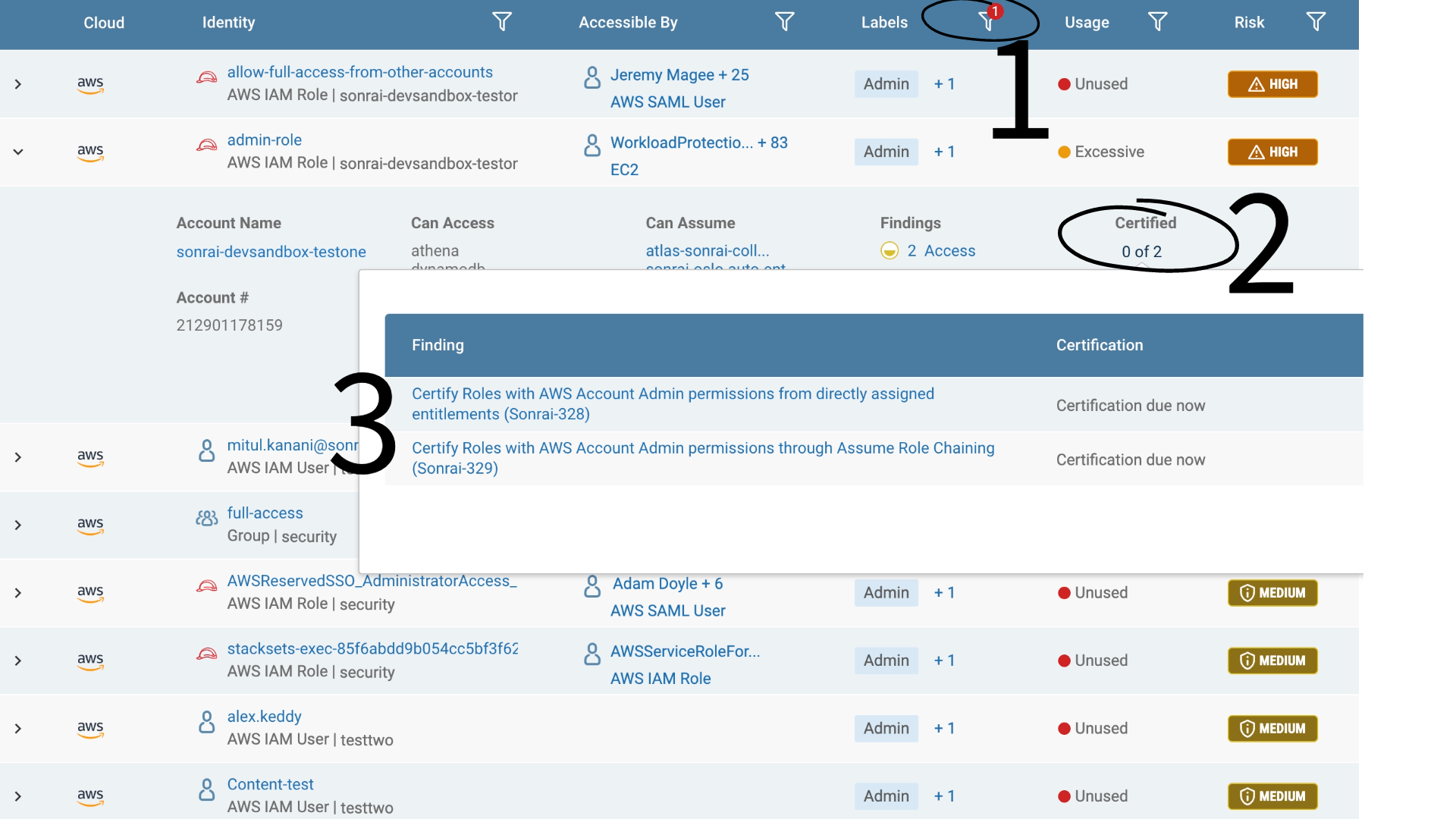
This first step alone, is a BIG one to take towards significantly reducing your overall access risks.
Step 2: Remove unused identities
Dormant identities come about in many ways. Maybe they were created in testing environments, maybe they were part of a project that ended, or they are from third-party vendors you no longer use. They are often forgotten about, or if they are known, there is hesitancy around removing them in fear that it could break something.
Identity and privilege are undeniably weaponized in cloud breaches. They are a pivotal tool attackers exploit to get what they want. The logical answer is to minimize that attack surface as much as you possibly can. That means removing unused identities.
How to fix it
The first step is visibility into all your unused identities. Luckily, Sonrai’s Identity Inventory makes this quite easy. Filter by ‘unused’ in the usage section and see a list of every identity with dormant activity for 30+ days (1).
From here, you can investigate individual identities and their ‘unused’ findings (2) and if deemed appropriate, delete them easily with Sonrai’s step-by-step instructions or bots (3). Sonrai also allows you to leverage automated bots to mass-delete unused identities per environment if certain conditions you specify are met. This is immediate and swift risk reduction.
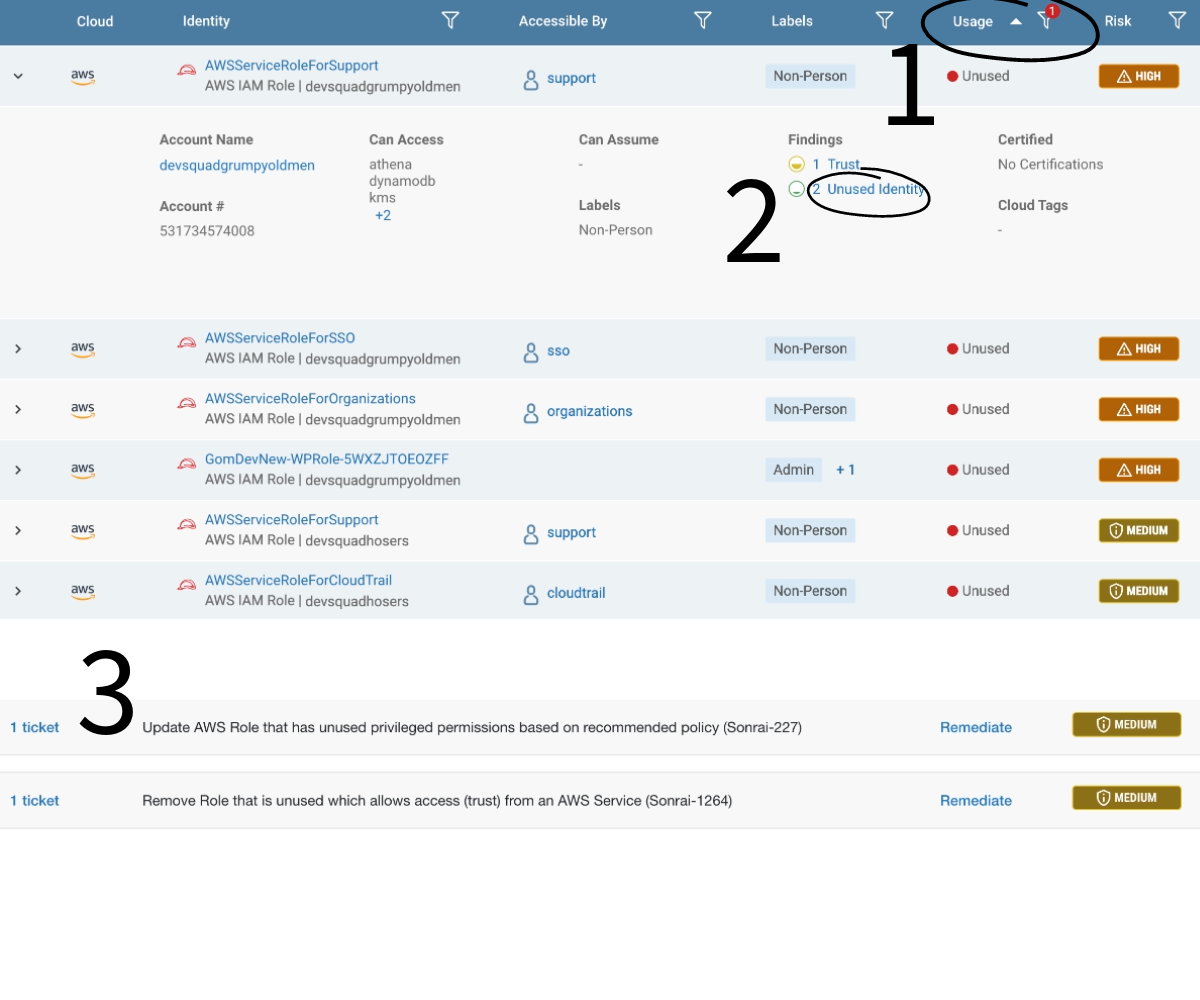
At this point, cleaning up unknown admins and unused identities has significantly improved your risk score, better protected your applications and data, and even made steps 3-4 easier.
Step 3: Implement least privilege policies
Now that your unknown admins and unused identities are removed, you are left with your necessary identities – but they are likely overprivileged for their duties. This is when you enforce least privilege policy.
How to fix it
Sonrai offers pre-built least privilege policies that can also be customized for your needs.
Once your policy is in place, anything in violation will fire a ticket. You can check into your overprivileged identity risks in the ‘Identity Insights’ dashboard with the overprivileged identity widget (1). From there, you can pursue the individual findings and remediate as needed (2). Sonrai’s remediation options include a recommendation for a better suited policy or removing the policy entirely.
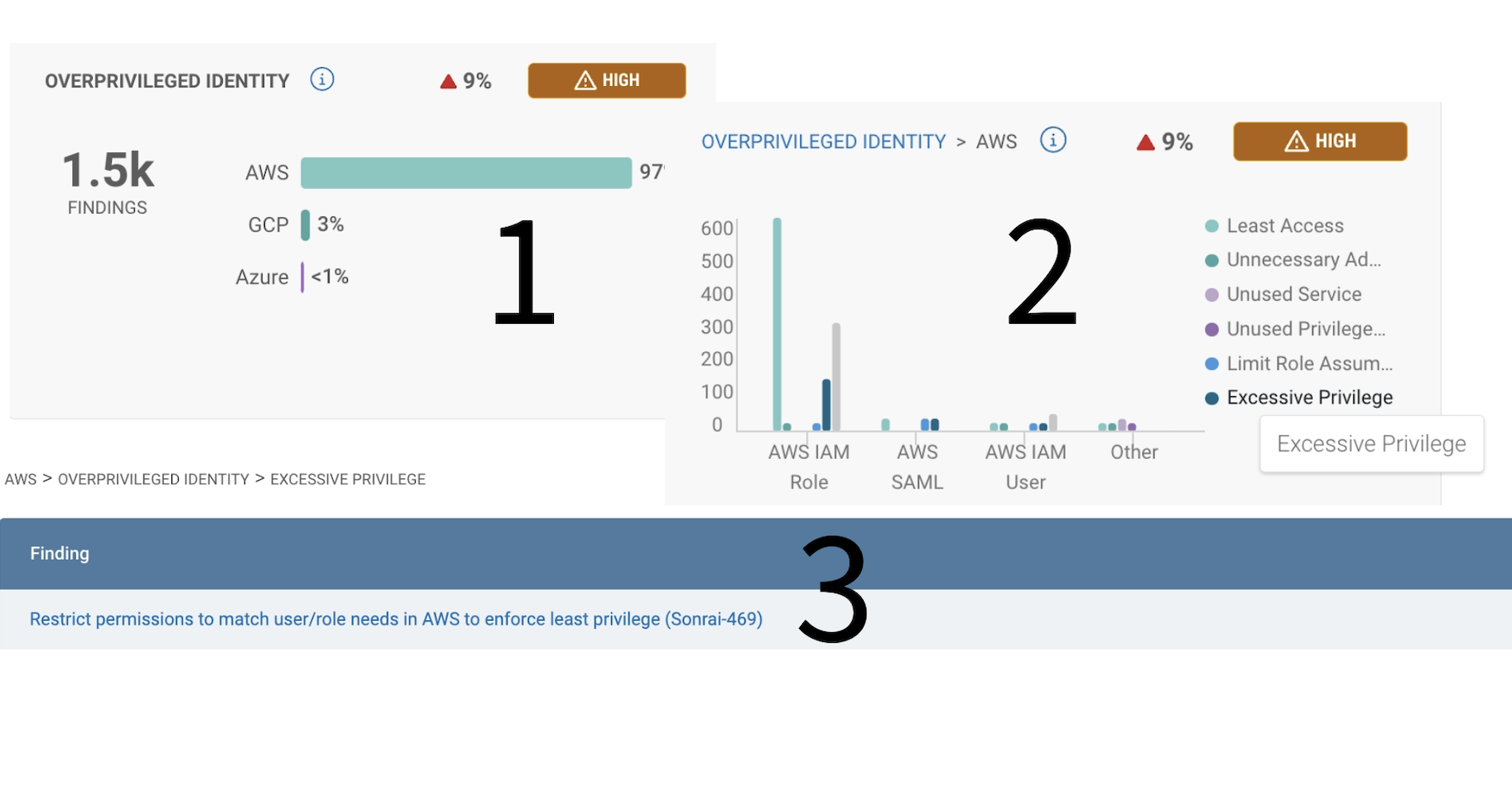
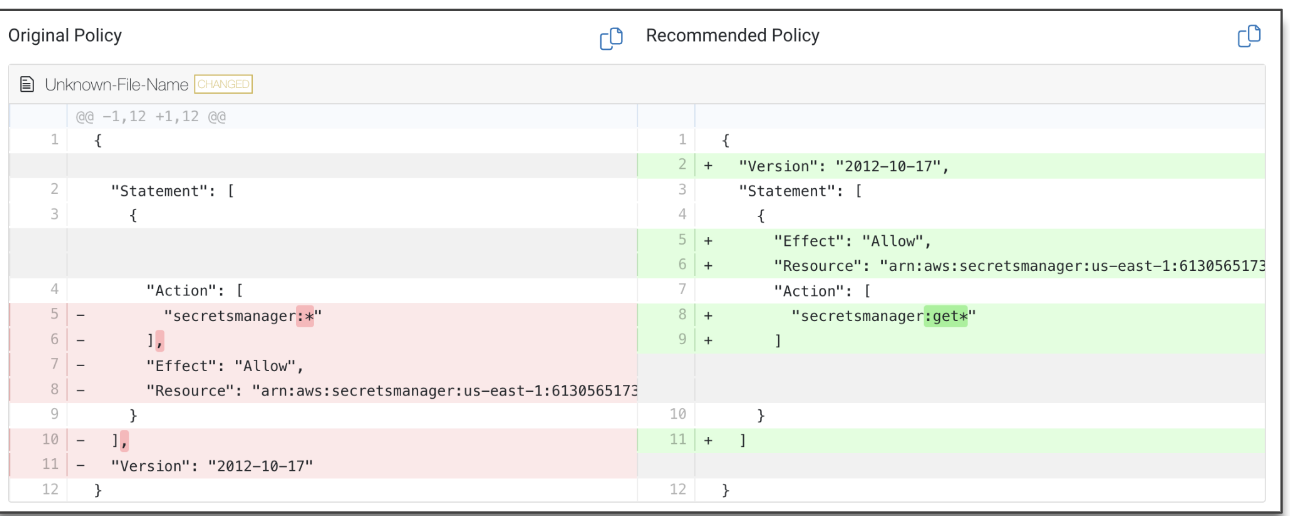
Least privilege is not a destination, but a continuous process. Sonrai continuously monitors for any permission changes so you can continuously enforce your least privilege policy. Implementing this policy and leveraging automated remediation means you can ‘hands-free’ be assured your identities have nothing more than what they need.
Step 4: Disrupt lateral movement
Even with least privilege policies in place you can have unwanted paths to data. That’s right, least privilege is not the end-all-be-all of identity security. That is because it only accounts for directly assigned permissions.
As we know at this point, privilege is more complex than that in the cloud. There are multiple tiers of privilege – organizational policies like guardrails, policies at the identity level, policies applied to resources, and so on. This makes seeing the net result of privilege difficult.
Additionally, privilege can be inherited or assumed via ‘permission-chaining.’ This makes privilege a little more diluted. Consider an identity that can assume a role, then that original identity can access all the privilege the role held. Now consider 5 more role assumptions, each unlocking more privilege.
These opportunities are considered lateral movement. They are pathways attackers can find to hop from one identity to the next in search of the right culmination of privilege, or the right privileged identity to execute their attack.
This is the final and ultimate battle to secure cloud identities and access; Gaining visibility into these covert opportunities and removing the policies creating them.
How to fix it
Sonrai’s patented permission analytics are able to ‘see’ all layers of policy (think: org policies, IAM policies, resource policies, trust relationships, IAM groups, conditional access, etc.) and compute the end result to illustrate how they create pathways to data.
Sonrai will detect any time covert pathways to data are detected – i.e. any time lateral movement or privilege escalation is possible.
Navigate to the lateral movement widget in the Identity Insights dashboard (1)’ where you can address any direct or indirect privilege escalations or unintended lateral movement violations.
To follow one example – let’s explore ‘indirect escalation’ findings (2). Here, there’s an access policy finding for unintended lateral movement – we can see a suggested remediation of removing a role to break the pathway. Navigating into the finding, your team can select from multiple options for remediation steps (3).
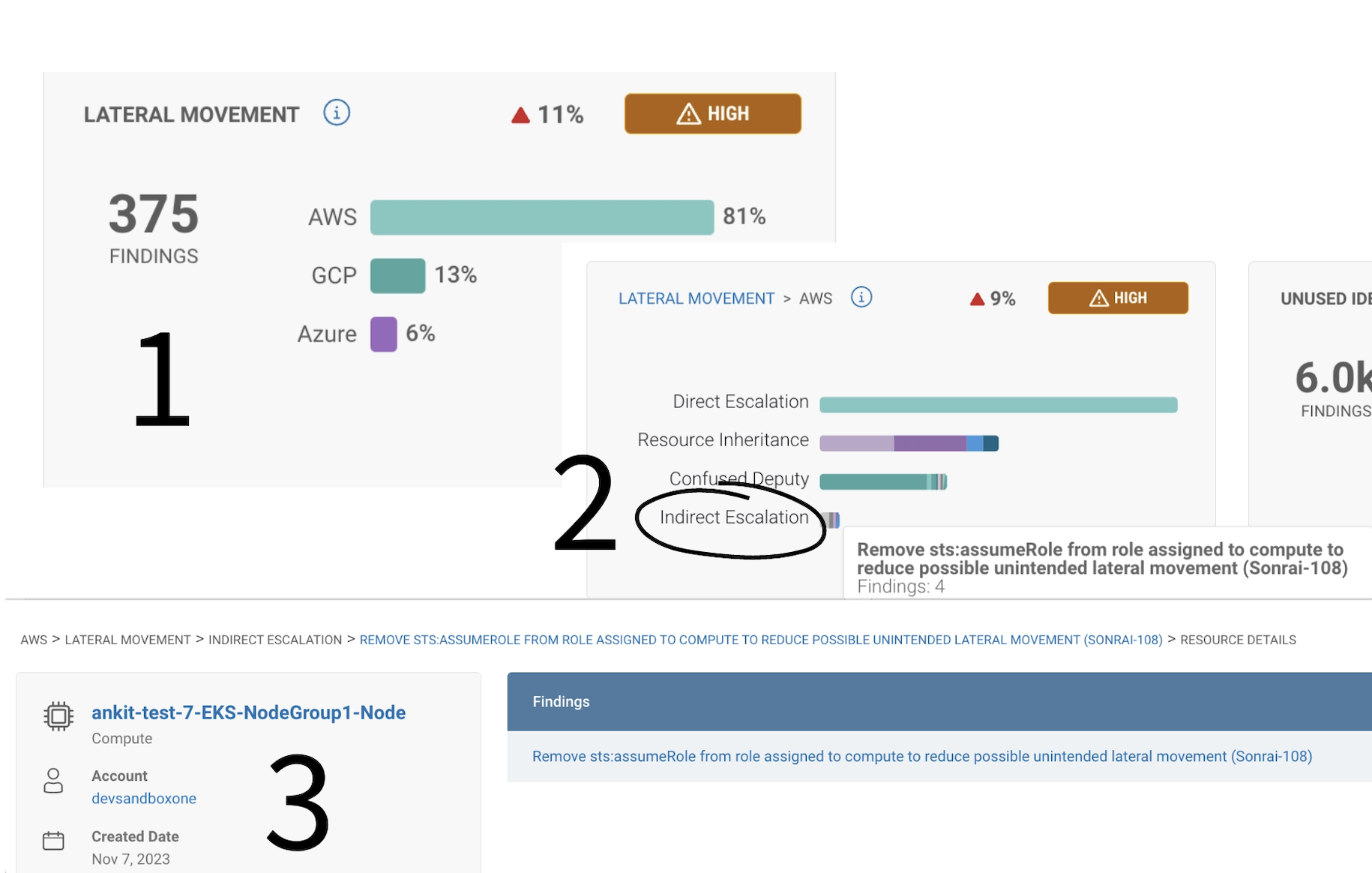
Security as easy as 1, 2, 3! (4)
There are a lot of strategies and solutions out there to help tackle cloud IAM. We have an approach that is simple, doable, and focused on fixing issues with the greatest impact on reducing risk.
There is no magic strategy to protecting cloud assets and managing privilege, but if you take these four steps we guarantee you will see significant results.
If you’re curious how your cloud estate fares in regards to the four major identity risks, you can request a free Cloud Identity Diagnostic. The result is a PDF report detailing a risk score, how you compare to peers, where your weak points are, and how to fix them. If you want help fixing them, we’re here for that too.

Sonrai cloud security platform, products and services are covered by U.S. Patent Nos. 10,728,307 and 11,134,085, together with other domestic and international patents pending. All rights reserved.




