Cloud Detection
& Response (CDR)
Analyze cloud data to quickly detect hidden malicious activity in your cloud and mitigate threats.
Analyze cloud data to quickly detect hidden malicious activity in your cloud and mitigate threats.
Reducing risk in your cloud and protecting high-value assets from compromise is the foundation of every cloud security strategy. But with the dynamic nature of clouds and the persistent nature of threats, you must assume that attackers are going to get in. Once that happens, monitoring and detecting threats is the best course of action to mitigate damage to your business.
The Sonrai CDR solution aggregates your entire cloud footprint including all privilege, access, workload and configuration activity and analyzes it to detect new risks or threat activity. Continuous monitoring of audit logs surfaces any unusual access history or changes to cloud entitlements. Findings posing the greatest risk are then prioritized to keep your teams focused on preventing business disruption.
It is the unique capability of tying identity entitlements to sensitive resources that empowers security teams to quickly find the root cause of unusual activity and respond effectively.
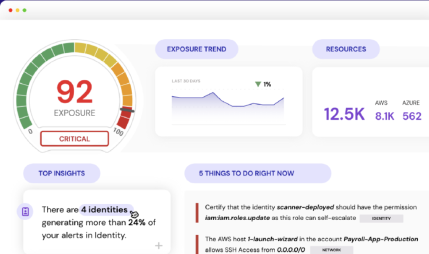
Detecting incidents requires vigilance and understanding of early indicators. Sonrai gets your cloud to a secure baseline and monitors for deviations indicating malicious activity, including unusual access to critical assets, changes to access and permissions, unusual behavior of critical identities and configuration changes. Findings are then prioritized based on business risk, allowing you to remediate top risks before an attacker has the chance to exploit them.
Sonrai can interpret 40,000+ unique actions (e.g. read, write, delete) across all major clouds so you can understand how complex permissions are causing risk in your cloud. Understanding identity effective permissions and access history offers a comprehensive view of incidents. Teams can also use historical data to understand the extent of an incident – data exposure, multiple access activities and connection to other activities. This investigation helps inform the context we use to prioritize the alerts that pose the greatest risk to your business. No more chasing deadends first.
Take action on alerts from Sonrai with a range of remediation options – automated bots or prescriptive instructions and execute in a customized workflow able to integrate with existing security tools like ticketing systems, communication tools and SIEMs. These options enable collaboration across teams as well as comprehensive tracking and reporting for audits.
Context-Aware Detection and Remediation
“Since automation unlocks an anomaly-centric alert model, there are far fewer controls than an average large financial enterprise – meaning less alerts, less false positives, and more time on threat investigation.”

Unified security for identities, data, workloads and cloud configurations powered by the Sonrai Identity Graph.

Enforce, report and automate compliance with over 1000 policies mapped to every major compliance framework including NIST, CIS, HIPAA, SOC2, PCI, GDPR, HITRUST, and CSA STAR.

Continuously monitor activity logs, cloud assets, and configuration to stay ahead of cloud risks in real time. Detect when cloud posture is drifting and send alerts to the right team for immediate action.

Discover, monitor and secure critical data. Know who can access your critical assets and secure them. Monitor key vaults and databases to alert on changes and inform least access policies.

Prioritize vulnerabilities with agentless scanning combined with real risk context based on privileges, access to sensitive data, or external exposure. Save time and minimize risk with quarantining risky hosts with bots.

Enforce, report and automate compliance with over 1000 policies mapped to every major compliance framework including NIST, CIS, HIPAA, SOC2, PCI, GDPR, HITRUST, and CSA STAR.

Read how to detect and prevent a cloud breach
Learn how to analyze insights and remediate

CIEM helps SOC teams find risk
Get a personalized demo to see how Sonrai Security detects security events
and empowers teams to respond effectively.