Table of Contents

Share this entry

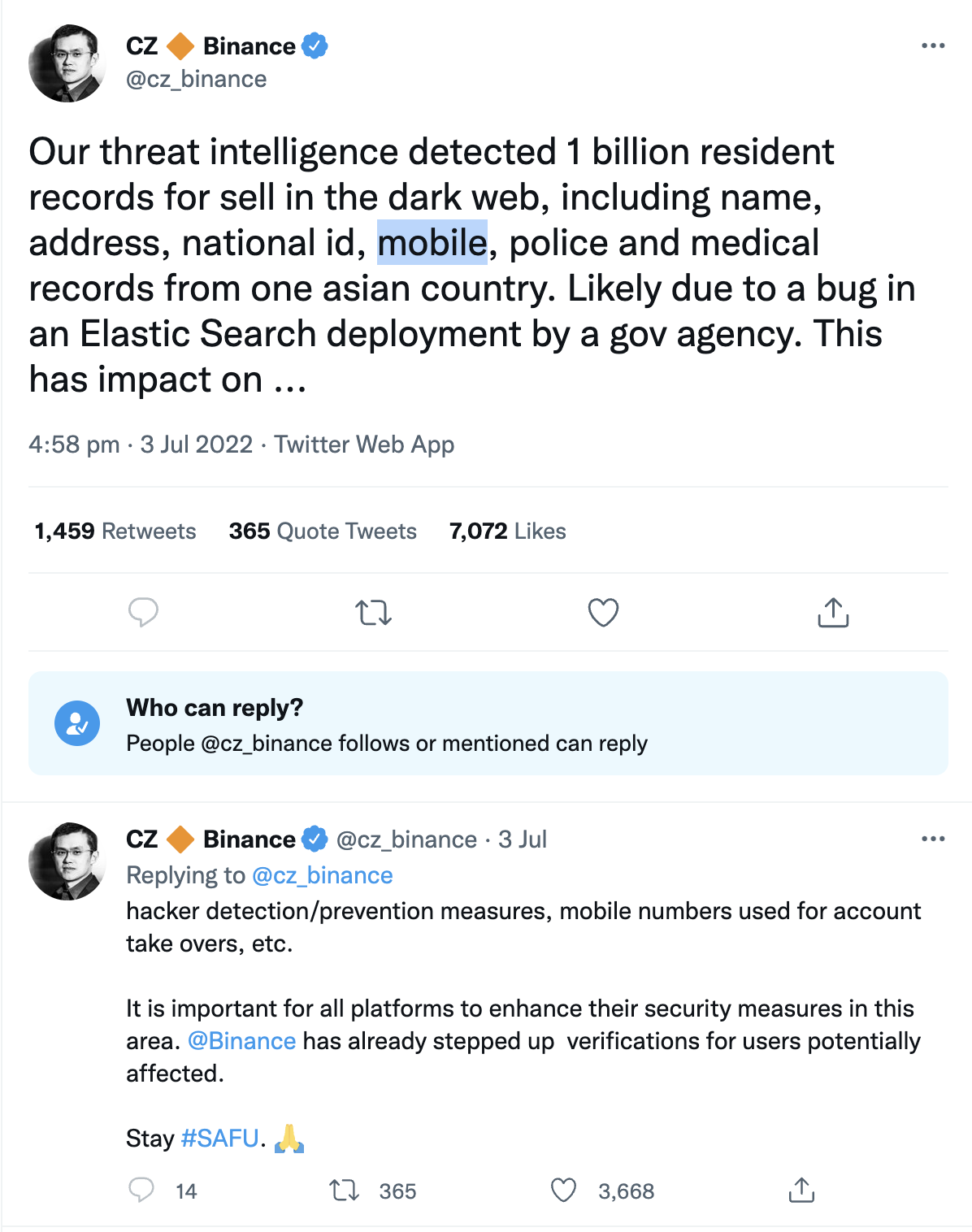
Recently, a dating app dedicated to pairing up anti-vaccination individuals experienced massive data exposure due to an alleged ‘hasty set-up’ and absence of basic security protocols. The dating app, Unjected, allowed access to the admin dashboard, which had been left entirely unsecured and in debug mode. As a result, the researchers got incredible access, including the ability to view and modify private account details, edit posts, and access backups without administrator authentication. The discovery was made after GeopJr noticed that Unjected’s web application framework had been left in debug mode, allowing them to learn pertinent information “that someone with malicious intent could abuse.”
That’s right, all it took was a few minutes before security researchers could take advantage of a misconfiguration to escalate privileges. This massive misconfiguration was first noted by The Daily Dot and even confirmed by a researcher under the name ‘GeopJr.’ The researcher created an account and discovered the admin feature required no authentication, meaning GeopJr could access any user’s profile, edit their information, or steal it. Administrative privileges are reserved for basic maintenance and oversight of the app, so GeopJr’s test account was able to “reply to and delete help center tickets and reported posts.” GeopJr could gain access to data, such as the site’s backups, and gain permissions, like downloading or deleting the data. GeopJr was able to give away $15 per month subscriptions to Unjected. The harmful possibilities are endless when the wrong person discovers a cloud misconfiguration.
This is a wake-up call to other organizations that have critical assets on cloud services.
A Criminal’s Golden Ticket
Admin privileges are the golden ticket. They are comparable to ‘owner’ permissions or * permission. The previous all have one thing in common: they allow an identity to have free reign over an environment. Unjected is not the first and certainly not the last organization to run into danger with a misconfiguration leading to excessive = privileges. Whether it is a lack of authentication to adopt these types of privileges or an organization ignorantly, yet intentionally, offering up the blanket privilege to an identity for the sake of ease, many organizations get themselves into trouble this way. It is not difficult for an attacker to infiltrate your environment and find the right role or identity that will give them the access they want.
While not requiring authentication to access admin privileges is a simple misconfiguration, its impact is truly one of the most dangerous. Such a simple mistake can cost your organization.
In fact, it may not be a new source of threat, but it has emerged as one of the most widespread: Nine out of 10 organizations are vulnerable to cloud misconfiguration-linked breaches. These breaches cost enterprises $3.18 trillion annually, with 21.2 billion records exposed. Keep in mind that these numbers are extremely conservative as 99% of all misconfigurations in the public cloud go unreported. Add to this the fact that 74% of data breaches start with abuse of access. Governance over these kinds of mistakes can be a tall order, especially at scale, hence the increasing adoption of cloud-focused identity solutions.
This misconfiguration is really a nightmare for the organization and its clients.
Identifying the risks in your cloud
Misconfigurations are one of the primary challenges faced by organizations leading to data breaches like this one. As we’ve learned over the years that even the most sophisticated and well-funded organizations have had their issues.
Organizations can minimize risk by first identifying the misconfigurations leading to unauthorized privileges. It is essential for not just data owners but also cloud operations, security, and audit teams, to recognize these risks to maximize their control, security and governance. If your organization doesn’t have complete and continuous visibility of the identities and data in your cloud and their entitlements, then how can you effectively protect the data that resides within it?
Identity and data security should take root in the center of any cloud security strategy, but total cloud security doesn’t end there. The four major pillars relating to the cloud, identity, data, platform, and workload, do not function in isolation. In fact, they all influence and connect to each other, so your security program should consider the context of how they relate to each other when building a security strategy. If you’re interested in learning more about total cloud security, explore our platform, or read more about managing misconfigured identities in our dedicated blog.