Table of Contents

Share this entry
 2022
2022 AWS Security Tools & Services
At the start of 2022, Amazon Web Services held a 33% market share, making it the most used enterprise cloud platform. However, with greater use also comes greater opportunity for risk (AWS customers have found themselves in the midst of many data breaches over the past years.)
AWS enables enterprises to innovate and distribute data with unmatched effectiveness, but all that data — and the applications holding it — need sufficient protection.
This is why AWS works hard to ensure secure hardware and infrastructure to secure their platform and to safeguard things like customer information and allow business continuity. However, AWS operates under a Shared Responsibility Model, meaning the customer is responsible for securing everything within their cloud. This includes many services and customizable configurations to use your cloud intelligently.
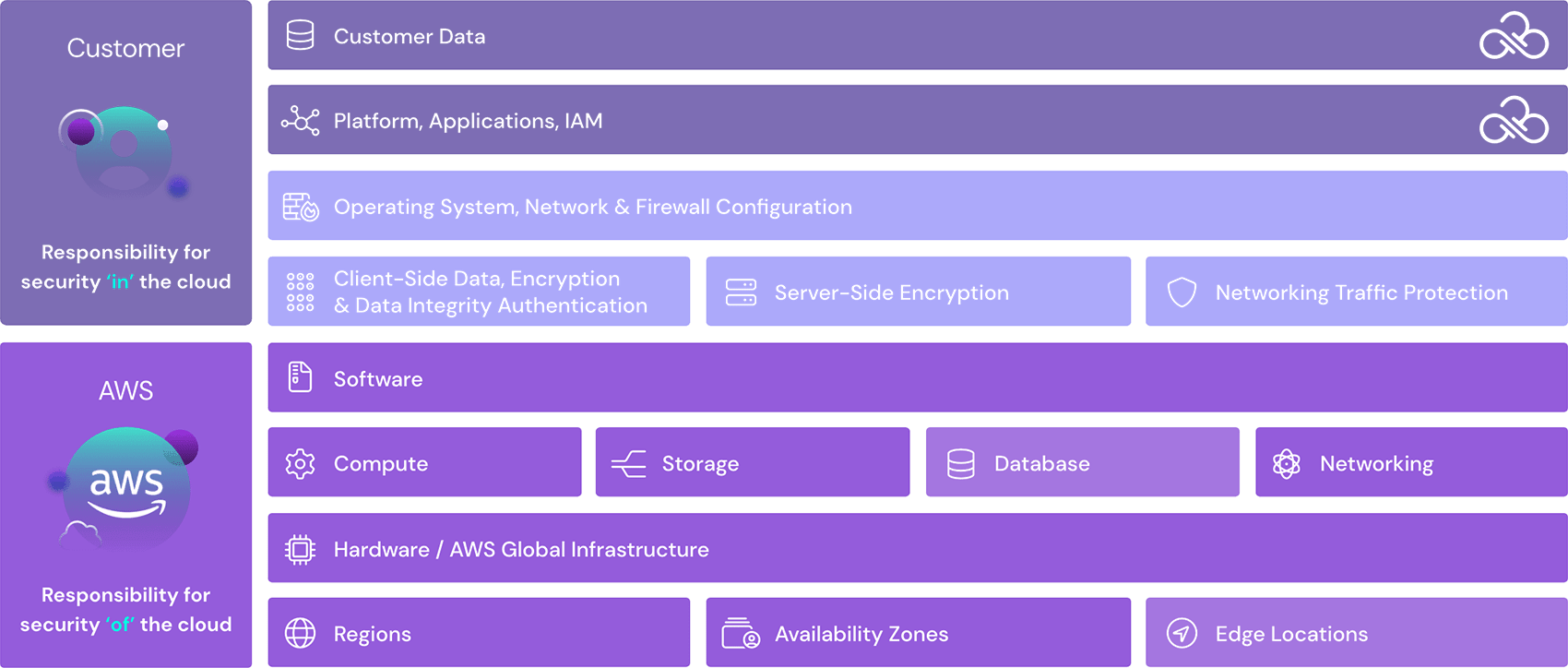
AWS provides a number of security tools and services to help make your life easier when it comes to securing your cloud. In this blog we’ll introduce some AWS security services, tools, and solutions that you can leverage as a customer.
What are AWS Security Tools and Services?
First, what are AWS security tools and services? They are a variety of services provided by AWS that sprawl across several realms of security including data protection, identity and access management, infrastructure security, and threat detection and continuous monitoring.
Data protection. AWS recognizes the importance of securing data and making sure it is not lost in transfer. Their services help you meet core security, confidentiality, and compliance requirements. Features include things encryption, data duplication and data monitoring. An example of a data protection service provided by AWS is Amazon Macie.
Identity & Access Management. AWS recognizes the need for managing Identities so they provide an extensive list of tools and services to help you manage identity in the cloud. Overall, the goal is to control the resources and actions identities can use and manipulate.
Infrastructure Protection. Infrastructure protection is a critical component of information security and helps ensure that everything within your workload is safe from vulnerability exploitation or unintended access. While infrastructure is largely managed by AWS itself, they also provide some additional resources for managing the security of configurable infrastructure, e.g. AWS WAF.
Threat Detection. When in the cloud, you need constant reassurance that your security posture is strong and you have all the right configurations in place to optimize security. AWS provides services that increase visibility into your deployment and operations and also monitor identity behavior to help detect threats. An example is Amazon GuardDuty.
Account vs. Application vs. Service Security on AWS
One thing to note about AWS services and tools is that there are differences in what these resources are helping to protect. AWS differentiates between account security and application and service security.
Account: Securing an identity, be it a person or non-person identity requires a different approach to security. This is where cloud IAM practices shine, as AWS encourages controlling identities’ ability to access sensitive data or manipulate privileges. This can help prevent concerns like privilege escalation, excessive permissions, or poor hygiene around admin users. An example would be AWS IAM, a service providing security practices like SSO or MFA and assigning and managing the permissions of identities in your cloud.
Application & Service: Applications and services within AWS are susceptible to threats like external attacks from bad-actors or even vulnerabilities existing from the development process, so they require their own breed of security resources. An example would be Amazon Inspector, a service intended for vulnerability management of applications deployed on EC2.
Now that we’ve reviewed the different purposes of AWS security tools and the different types, let’s apply that information and explore the top services and features customers can use today.
Top 14 AWS Security Tools
AWS Security Hub
Detection & Monitoring. AWS Security Hub is a cloud security posture management service that performs automated, continuous security best practice checks against your AWS resources. It aggregates your security alerts (findings) in a standardized format so that you can easily take action. Security Hub makes it simple to understand and improve your security posture with automated integrations to AWS partner products. Many roles may find themselves tasked with managing secure use of the cloud, but in particular this may be used by Cloud Security Analysts.

Amazon GuardDuty
Detection and Monitoring. Amazon GuardDuty protects stored data, AWS accounts, and workloads by monitoring DNS logs, event logs, and other data. Data is analyzed to detect anomalous behavior and present it in a centralized location. Security & SecurityOps teams would use this service.
AWS Config
Detection and & Monitoring. AWS Config will constantly evaluate your cloud configurations and detect changes that fall out of policy. This is extremely useful when making configuration changes to resources and ensuring opportunities don’t appear for data breaches. Security Analysts and Cloud Security teams would be the target audience.
AWS Inspector
Detection and Monitoring. AWS Inspector is an assessment service for apps deployed on EC2 instances. The security assessments include CIS benchmarks, possible exposures or vulnerabilities (CVEs), or just general security best practices like disabling root logins for SSH. This is useful for DevSecOps teams or Security Analysts.

AWS CloudTrail
Detection and Monitoring. CloudTrail monitors all behavior in your environment. This includes any action an Identity takes and all API calls. This helps you review and detect any inappropriate or suspicious behavior. There is an additional AWS CloudTrail Insights you can add-on to receive alerts when abnormal activity is detected.
AWS CloudWatch
Detection and Monitoring. Similar to CloudTrail in its monitoring services, CloudWatch observes resources and application activity. It collects logs and event data to help detect any anomalous behavior, improve operationalization, or help with performance monitoring.
AWS Shield
Infrastructure Protection. AWS Shield protects all your applications running on AWS from DDoS attacks, or Denial-of-Service attacks. This essentials protects the perimeter of your application. The audience for this service includes DevSecOps and cloud admins.
AWS Web Application Firewall
Infrastructure Protection. AWS WAF helps protect against web applications being exposed to the internet and therefore vulnerable to exploit. It will detect and mitigate attacks like SQL injections. It comes with default rules, but your team can also customize your own settings. Recommended for Cloud, Network or Security Admins.
AWS Identity Access Management (IAM)
Identity & Access Management. AWS IAM provides identity and access controls across the environment. Specifically, it offers granular control over what identities (person and non-person) can access and perform. Typical users of this may be IT Managers or Cloud Admins.
Learn where AWS IAM stops and a CIEM takes over.
AWS IAM Analyzer
Identity & Access Management. Building off of the insights and controls AWS IAM provides, the complexities of managing the permissions of identities can get unruly. IAM Analyzer allows for a clearer picture of these access patterns to help remove excessive privileges and work towards least privilege.
Amazon Cognito
Identity and Access Management. Amazon Cognito helps manage customer access in web and mobile applications at scale. The offerings include identity federation, user sign-in features, and access controls. Some use cases include giving customers flexible sign-ins or role-based access to AWS resources.
Amazon Macie
Data Protection. Amazon Macie helps secure Amazon S3 buckets. It uses machine learning and pattern matching to detect sensitive data in S3 buckets. This alerts you to things like lack of encryption or publicly accessible data. This would be particularly useful to anyone responsible for compliance.
AWS Secrets Manager
Data Protection. Secrets Manager will help you better protect sensitive information or secrets that allow access to services and databases in your environment. If you need to access a secret, you can create an API call to retrieve the information from the Secrets Manager API. This tool would be useful to Development Teams or Admins.
AWS Artifact
Compliance. AWS Artifact is a go-to location for all things compliance related information. This includes receiving on-demand compliance reports from AWS and third-parties, as well as managing or accepting and regulations. An excellent use case would be assisting in the auditing process.
Enhance AWS Security Tools with Sonrai Security
Amazon Web Services has put out extensive services and tools to help your teams secure your cloud. That being said, AWS is a cloud provider, not a security provider. At this point in time it is widely accepted that leaning on 3rd party cloud security platforms is the best way to elevate your cloud security past the limitations that native-tooling provides.
Sonrai Security starts at the core of your business — your most sensitive applications and data – and works outwards to secure it my managing cloud identities and their entitlements. The patented identity and permission analytics can compute the end-to-end permissions of every identity — even the ones you can’t see because they’re indirectly inherited via complex identity chains.
This insight, matched with AWS services makes an unbeatable team for reducing cloud risk and remediating threats.
Interested in seeing the Sonrai platform in action? Watch an on-demand demo, or request a personalized one for your needs.
Here’s a list of AWS vulnerabilities by CVE. One specific risk to look out for is Amazon S3 bucket vulnerabilities.
AWS offers a wide range of security tools and services. For IAM solutions you can look into Amazon Cognito, AWS IAM Analyzer, and AWS IAM; For data protection look into Amazon Macie & Amazon Secrets Manager; For detection and response look into Amazon CloudTrail and CloudWatch. For a complete list, see our blog.
Yes, Amazon security tools integrate with most other Amazon services, but additionally other third-party cloud security platforms, like Sonrai Security. See how Sonrai works with Amazon Control Tower and Amazon Inspector



