Table of Contents

Share this entry


One of the most common security management objectives we hear every day in our advisory work at TAG Cyber involves enterprise teams trying to prevent malicious attackers from “getting into” their cloud services, workloads, and infrastructure. This is driven by the need to support threat prevention, as well as compliance goals.
However, the historical approach to relying on vulnerability scanners to identify risks fails miserably within a cloud environment. Unlike in legacy, data-center-centric infrastructures, servers, applications, and data stores cannot be duplicated, moved, and reused as they can within the cloud. Because cloud environments are so different, we must change the way we look at risk, moving from an ‘outside-in’ approach of scanning for vulnerabilities using external tools, to an ‘inside-out’ approach, starting with data risk and working our way ‘out’ to the workload and application risk.
Is Emphasis on Outside Access Sufficient?
When most organizations consider their risk to web applications and cloud environments, the typical approach is to mimic the approach the attacker would take, i.e., scan for vulnerabilities from the internet and leverage the weaknesses you find to gain access. While there is fundamentally nothing wrong with this approach in legacy infrastructures, it reflects only a small portion of the risks faced with cloud deployments.
Due to the dynamic nature of a cloud environment, inside views are also necessary to maintain proper visibility into the cloud’s security posture. This can include compromised insiders leveraging authorized access to target critical data, systems, applications, and other resources located in the cloud. It can also involve authorized administrators targeting cloud assets.
This implies that security teams should focus on building a holistic view of their cloud security posture – and this requires continuous, automated coverage with a suitable platform. We recommend working with a commercial vendor in this area to ensure that proper technical refresh is being done, since cloud threats and vulnerabilities are changing so quickly.
Are Malicious Actors Gaining Access to Cloud?
Unfortunately, attackers are having considerable success getting into cloud resources from the Internet – not to mention from insider vantage points using authorized access. We noticed for example that one recent report measured 80% of organizations surveyed as having experienced a cloud security breach. This is a striking result.
But such attacker success is consistent with our experience at TAG Cyber as well: While we regularly recommend the diligent application of external attack surface management (EASM) and vulnerability management (VM) for visibility, additional focus on cloud data stores and identity and user access is required to fully understand the overall security and risk posture of your cloud environment.
Unlike legacy data center environments, cloud developers can duplicate data stores, share extract files, and grant access to others all with the click of a button. No longer is your entire customer database stored on some monolithic piece of hardware sitting in a data center. In today’s modern environments, that database is now a virtual device that can be duplicated at will. Truly understanding your cloud risks starts at the data level – from the “inside-out.”
Our advice in such cases has been strongly guided by our work with commercial cybersecurity vendor Sonrai. In particular, we are recommending that so-called “outside-in” cloud security be augmented with complementary “inside-out” security to gain a more comprehensive understanding of your cloud resources.
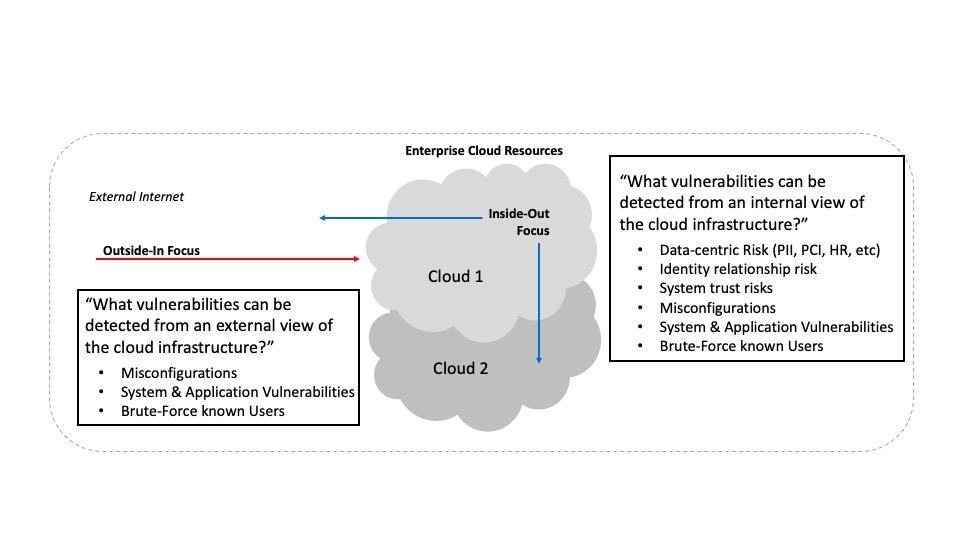
Figure 1. Combining Outside-In with Inside-Out Security for Cloud
We’ve learned that this full posture assessment – with emphasis on external access and internal data management – requires continuous and automated coverage of the cloud surface – and this always begins with the creation and management of an accurate inventory of your devices, users, and data stores, along with a clear understanding of your cloud attack surface.
How Does Sonrai Address the Problem?
The Sonrai platform is designed specifically to offer holistic and continuous visibility into enterprise cloud resources. It does so in a manner consistent with our observation above that coverage should combine outside-in views with inside-out views.
To achieve this level of coverage, Sonrai has taken the approach of including a wide variety of solutions that map to familiar industry concepts such as cloud security posture management (CSPM), cloud workload protection platforms (CWPP), cloud infrastructure entitlement management (CIEM), and Cloud Detection and Response (CDR).
Specific emphasis that supports this holistic inside/outside visibility includes the following capabilities:
- Least Privilege – The Sonrai platform focuses on identifying cloud access paths to data and other resources so that privilege allocation can be optimized. Such attention is done based on permissions (e.g., full data read, full administrative access) rather than inside or outside proximity.
- Data Protection – The Sonrai platform does an effective job locating data in cloud infrastructure so that its access and security attributes can be properly defined using identities. This is also done in the context of data access visibility regardless of where it originates.
- Security Prioritization – The Sonrai platform assists with the prioritization of controls, with emphasis on defining security protections for container images, virtual machines, and other resources. Sonrai Risk Amplifiers and identity graphs highlight vulnerabilities for subsequent prioritization.
Action Plan for Enterprise
Security teams would be wise to immediately review their existing cloud security program to ensure that they are not focused on the outside-in approach that is so typical of existing vulnerability management programs. Instead, a more holistic view is recommended.
The Sonrai Cloud Security Platform should be included in architecture reviews, and teams should leverage its unique features including identity graphs and patented access analytics. Ultimately, the exploitation of misconfigurations is the primary consideration in cloud security. Continuous and holistic visibility is thus imperative.


