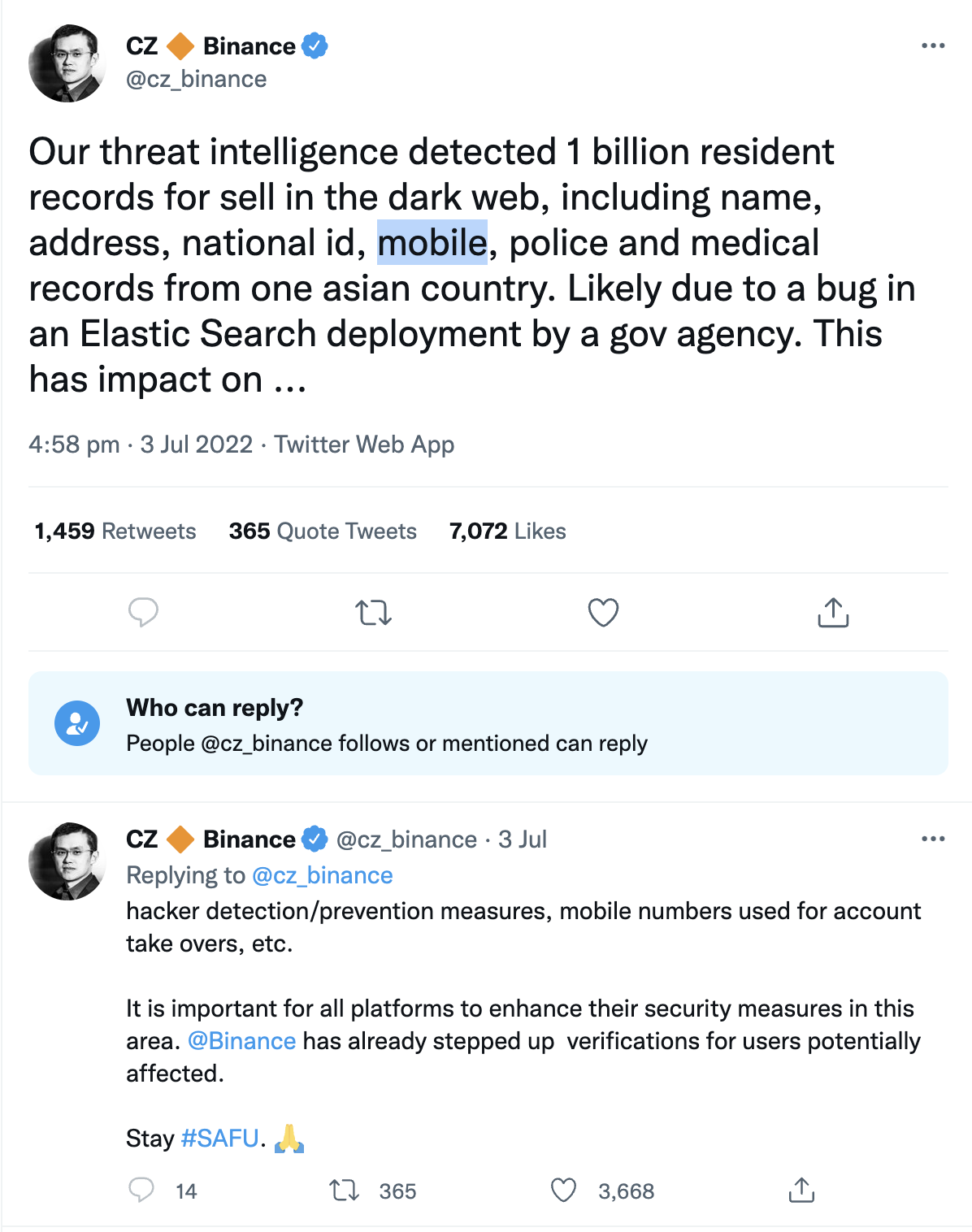
Share this entry

The Shanghai Police has potentially had its most significant known data breach in the country’s history. The prevailing theory about how the information wound up for sale online is that the police database, hosted by a third-party cloud service provider, had simply been left unsecured, without a username and password. If the Shanghai Police can’t prevent a simple cloud misconfiguration, why do you think you can?
Cloud misconfigurations can be insidious and are the reason behind massive breaches in recent years. According to one report, cloud misconfiguration breaches cost companies almost US$5 trillion. Why aren’t you doing more to prevent this from happening to your organization?
In the case of the Shanghai Police data breach last week, Bob Diachenko, from the cyber research site Security Discovery, said he stumbled upon the open dataset months ago. Begging the question of how many others may have accessed the 23 terabytes treasure trove of sensitive information, including names, ID numbers, addresses, and even detailed criminal case information. It seems the data had been exposed more or less since last year, all from what appears to be a simple, and very well-known, misconfiguration. Unfortunately, for reasons unknown, Shanghai authorities did not prevent it or remediate it.
This is a wake-up call to security professionals, operations teams, and decision-makers. Ensuring data security in the cloud requires a much different approach to cybersecurity than traditional on-premise environments, and you can not do it without the right tools. Swift cloud adoptions could lead to mistakes brought on by oversights, errors, or ill-informed cloud service configuration choices. While it’s perfectly understandable to be wary of complex security threats in the cloud, organizations should also be on the lookout for simple misconfigurations that could ultimately lead to the unintended exposure of mission-critical information and assets.
Misconfigurations might seem straightforward and avoidable, but they are the most significant risks to cloud environments. Under the hood, the cloud comprises many settings, policies, trust relationships, and interconnected services and resources that make it a sophisticated, and daunting, environment to fully understand and adequately set up securely. Unfortunately, organizations start using any new technology without fully understanding its many intricacies.
Misconfigurations may be the leading cause of data breaches and exposures, but they’re quickly identified and resolved with mature cloud security posture management (CSPM) tools. According to Gartner, through 2024, implementing a CSPM offering and extending this into development will reduce cloud-related security incidents due to misconfiguration by 80%.
So what exactly do CSPM tools do? Aside from identifying your cloud environment footprint, monitoring for new instances, ensuring consistent enforcement across multiple cloud providers, setting your security baseline, and much more, an intelligent CSPM tool scans your environment continuously for misconfigurations and improper settings that could leave your organization at risk. In a nutshell: They help organizations address and mitigate the accidental cybersecurity risks facing cloud data.
No one wants to shell out more money than necessary when conducting business, especially when it’s something that’s avoidable with the assistance of tools and vendors. Consider your options and the expert sources available to you when migrating, managing, and storing data in the cloud.
It’s always easier and cheaper to employ security proactively vs. remediating a data breach or exposure after the fact. Contact us today to learn how Sonrai Security can help you stay ahead of the game with CSPM and prevent misconfigurations.