Vulnerability Management
Uncover true impact and severity using a continuous picture of platform, identity, and data information about the host
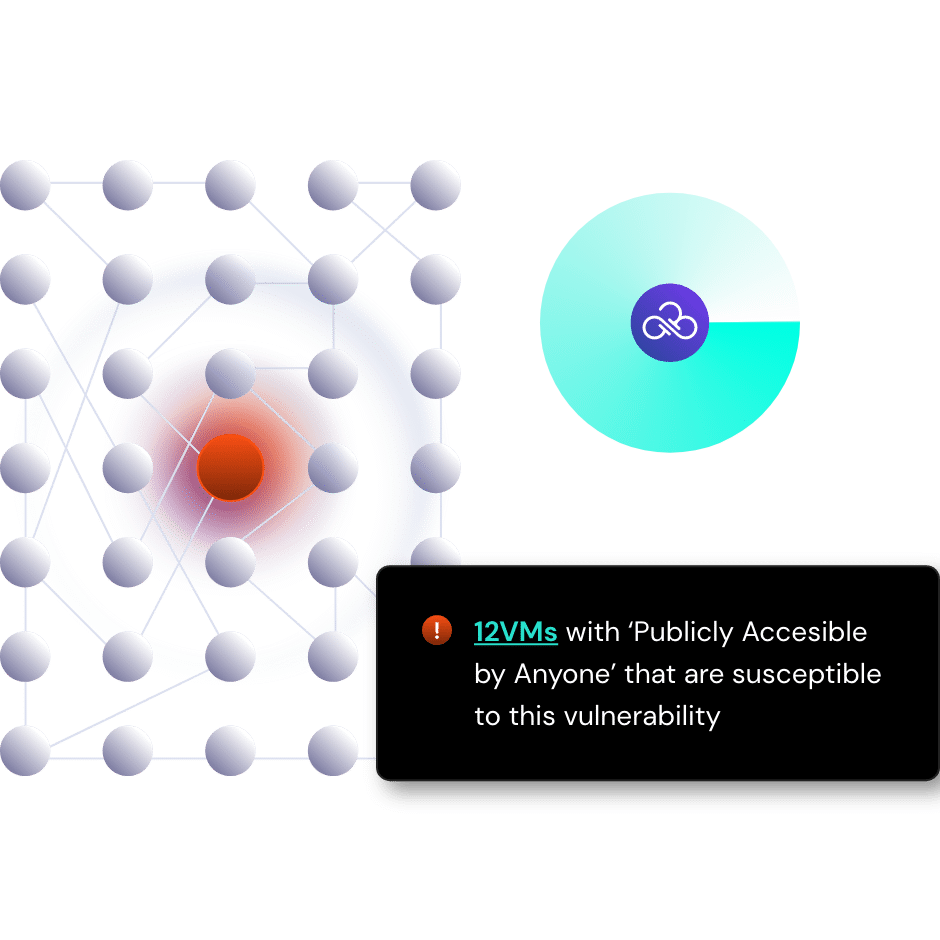
A dynamic cloud requires a dynamic way to see and prioritize vulnerabilities
In cloud, vulnerabilities proliferate at a high rate, with some teams buried in a thousands-long backlog of alerts. In a cloud environment where the perimeter has been redefined and a data-centric security approach is preferable, a vulnerability must be contextualized by its potential impact.