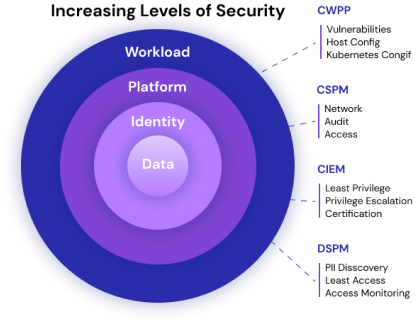
Cloud security is inundated with new tools and platforms; it’s tough to keep up on what does what. Sonrai and Wiz both offer cloud security solutions to enterprises globally. Both claim to be CNAPP, CSPM, CWPP, CIEM, and other acronyms. Wiz has innovated an agentless, scanning-based workload protection approach to the cloud, growing out of the CWP vulnerability management space. Sonrai invented an analytics engine that discovers and decodes permissions across the entire cloud, starting from the identity & data security area. Many customers use some or both products, with some overlapping competencies. There are pros and cons of the Sonrai identity-centric approach to cloud security versus the Wiz vulnerability-centric approach.
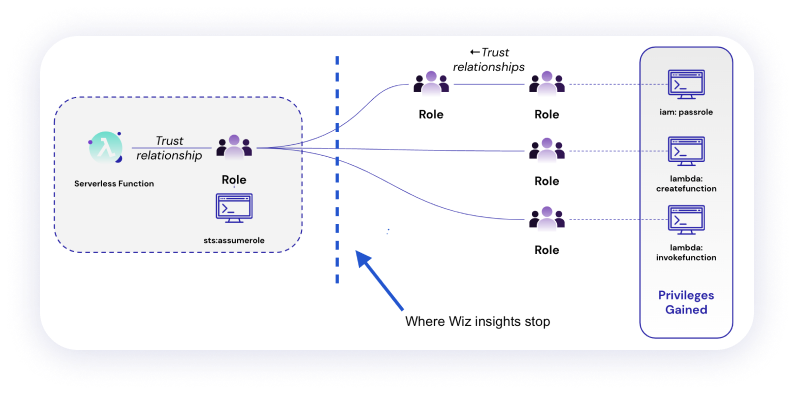
When an enterprise has deployed Wiz, they often seek out Sonrai for identity and entitlement use cases, including audit and compliance. We provide deeper visibility into complex cloud identity based attack paths. You can find out how we can offer this visibility in your environment by administering a Cloud Identity Diagnostic. It takes a few minutes to set up and run.
Comparing Cloud Identity Security Capabilities
| Feature |  |  | Why This Matters |
|---|---|---|---|
| Least Access | Yes | No | Least Privilege policies limit identities to their previous permissions usage; Least Access reverses that dynamic, monitoring sensitive asset access and limiting it to set boundaries. |
| Identity, Access and Permissions Visibility | More than 40,000 permissions analyzed including boundary conditions and nested groups | Directly attached permissions only | The resulting access from intertwined permissions from organization, IAM, and resource layers of the cloud requires advanced analytics to decode. |
| Least Privilege | Yes, enforcement based on potential access & asset sensitivity | Yes, enforcement based on previous permissions usage. | Least Privilege is often only based on limiting identities to permissions previously used. Smarter enforcement factors in the risk factor of unique actions and asset access. |
| Decode wildcard permissions | Yes | No | “*” means ‘all resources’ but must be decoded to its individually granted actions to reconcile it with other permission controls |
| Dormant identities & key rotation | Yes | Yes | Secrets attached to orphaned identities are extremely valuable & sought by hackers to initiate attacks |
| Classify unique actions | Yes; all | No | 40k+ unique actions in cloud have esoteric implications for ability to delete, edit, create, etc – this affects their potential impact in a breach |
| Map cross-account access | Yes, beyond account boundary through trust relationships, including cross-cloud | Single-hop view only | Lateral movement cross-account is widespread; understanding full trust implications is necessary for prioritization |
| SIEM & ticketing integration | Yes | Yes | Being extensible and sharing data to enrich context of other tools is essential for incident response |
| Compliance frameworks | Yes, full customizability | Yes | Framework, powered by customizable controls, make auditing easier and refocus the team on day-to-day defense |
| Critical privilege change detection | Yes, identifies and datastores, for potential access changes and anomalous activity | For access history paired with misconfiguration, not potential access | Seeing risky changes to potential access, not risky access itself, is necessary to stop attacks before they happen |
| Prioritization engine | Based on workload sensitivity, exploitability, and potential access to sensitive privileges or data | Based on exploitability, privileged identities, or access to sensitive data | The highest value remediation efforts start with data blast radius, or privileges that when combined can take down your infrastructure – not just your data. |
See Sonrai In Action
Check out our interactive tour to see how security leaders secure their cloud, manage identities, and protect their data with Sonrai.
What security leaders say about Sonrai
“Sonrai offers full visibility into effective permissions and the identity chain – giving my team value insight to identify, root cause and remediate identity risks.”

“Sonrai is one of the leaders in this space, both from a product maturity perspective, and the thought leadership.”

“We bought Wiz to hunt workload vulnerabilities in the cloud. To get the full context of what vulnerabilities could hurt us, we needed Sonrai’s intel on lateral movement and data impact.”
You Just Bought Wiz, Here’s What’s Next
Uncover what Wiz brings to the table, and where to head next to secure your cloud identity and data.
See How Sonrai Compares to Wiz
See the Sonrai technology in action with a comprehensive view of where your cloud identity risks are - delivered in just 24 hours. This comprehensive report includes specific next steps and is a valuable opportunity to compare findings from other solutions.