Table of Contents

Share this entry

The cloud security solutions market is growing rapidly and there are many types of solutions to support your specific security needs. Figuring out the right solution, let alone the right tool, can be difficult. Adding to this complication. Cloud native applications present new security challenges at different layers of the application stack. Development, runtime, compliance, security, and other concerns are often addressed in siloes forcing organizations to stitch together point solutions in an effort to address each discrete concern.
What is CNAPP?

The desire for more integrated, efficient, and condensed tooling has grown, and as a result, Cloud-Native Application Protection Platforms (CNAPP) have emerged as the catch-all of cloud security tools. Gartner defines Cloud-Native Application Protection Platforms as an integrated set of security and compliance capabilities designed to help secure and protect cloud-native applications across development and production. With risks knocking on your door, and the point solutions growing, like the Gartner Hype Cycle Workload and Network Security graph suggests, cloud security leaders must adopt a unified security approach and use appropriate technologies to protect their assets.
What’s the hype around Cloud Native Application Protection Platforms?
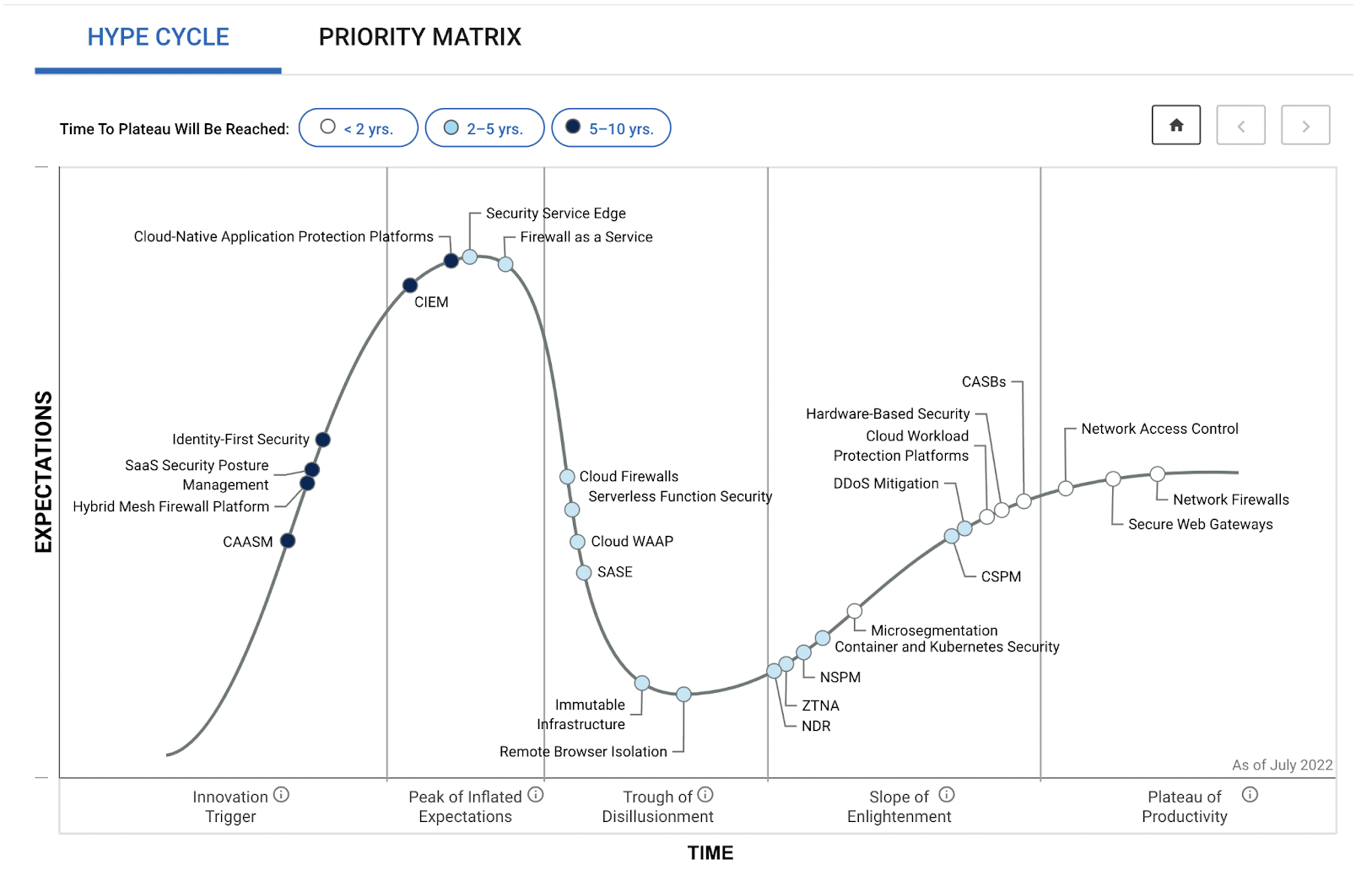
Source: Hype Cycle for Workload and Network Security, 2022, Published 18 July 2022
Why Is It Important to Have a CNAPP?
Organizations reported having on average six different tools in their environment according to the Opportunity Snapshot study by Forrester Research. Yet, they all reported major security incidents in the previous 12 months. Sometimes more tools, doesn’t mean more security.
In the “Innovation Insight for Cloud-Native Application Protection Platforms” report, Gartner notes that optimal cloud-native security requires an integrated approach that begins in development and extends to workload management. The thought process around CNAPP is relatively simple – use tools and security practices that were made for native cloud use from one end of the application lifecycle to the other. Their integrated and cloud-native nature make the solution efficient, cost-effective, consistent, and uniform.
According to Gartner, understanding the real risk of cloud-native applications requires advanced analytics with visibility into different areas — including open source components, applications, cloud infrastructure, and workloads. The report mentions that businesses need to secure cloud-native applications and monitor compliance using a complex set of interconnected tools spanning production and development.
The motivation for use and benefits of Cloud Native Application Protection Platforms are apparent, so what can you expect in terms of capabilities?
CNAPPs have four core pillars:
- Cloud Infrastructure Entitlement Management (CIEM)
- Cloud Security Posture Management (CSPM)
- Cloud Workload Protection Platform (CWPP)
- CI/CD Security
- Infrastructure as code scanning
- Container scanning
Capabilities of Cloud-Native Application Protection Platforms

Cloud Infrastructure Entitlement Management (CIEM)
The main purpose of a CIEM solution is to manage identities and their end-to-end entitlements. CIEM solutions will inventory all identities, person and non-person, and reveal all effective permissions, illuminating potential attack paths. This allows your business to strip excessive permissions and work towards policies like least privilege. CIEM solutions will keep you at least privilege with continuous monitoring to notify you of any out-of-policy changes.

Cloud Security Posture Management (CSPM)
CSPM helps companies discover misconfigurations, network risks, cloud drift, or lack of compliance. CSPM will ensure your cloud has all the necessary basic controls in place to secure its amorphous ‘foundation’. It works by establishing a secure baseline, using out-of-the-box policies and frameworks from your vendor, or customized ones, and monitoring the environment to detect deviations. This could mean ensuring databases are not publicly accessible or that you have logging enabled.

Cloud Workload Protection Platforms (CWPP)
CWPPs monitor workloads in the cloud, scan for vulnerabilities, and provide context regarding those vulnerabilities. CWPP, Gartner says, can help gain control and visibility into virtual and physical infrastructure, serverless workloads, and containers. While vulnerability management is a part of CWPP, workload security, a more cloud-native focus, is the heart of the solution. CWPPs detect vulnerabilities through, ideally, continuous scanning, and help organizations prioritize based on business impact and severity.
According to Gartner, “There is synergy in combining CWPP and CSPM capabilities, and multiple vendors are pursuing this strategy. The combination will create a new category of Cloud-Native Application Protection Platform (CNAPPs) that scan workloads and configurations in development and protect workloads and configurations at runtime.”

CI/CD Security
With more organizations leveraging microservices and containers, applications are being developed faster than ever. Integrating security into the CI/CD pipeline from the start makes it easier to detect and resolve security issues early and efficiently, long before they go into production. As a result, more organizations are adopting the DevSecOps concept, which integrates security processes into the pipeline and encourages collaborative efforts to expand beyond IT and development and include security professionals.
CI/CD security involves continuous scanning of source code, including Source Composition Analysis (SCA) techniques to help identify potential issues connected to third-party libraries or code. Additionally, it involves security testing alongside performance testing, prior to deployment, to help detect vulnerabilities. Lastly, ideally ongoing runtime security monitoring for production threats.
For more information on all these security acronyms, read our blog.
CNAPP Benefits
CNAPP comes to the great benefit of DevOps teams. DevOps is all about more secure application building, with more efficiency and speed, and less burden. The earlier security issues are flagged, the sooner developers can remediate the concerns.
Additionally, security teams utilizing different tools for different concerns results in more effort on the development side as they stitch together different solutions or remediate concerns in different workflows. The right CNAPP will provide an integrated experience with insight into risks across identity, data, workload and platform configuration, all with one operationalized remediation workflow. Working out of one central, uniform, and automated solution unites DevOps, IAM, Security and Cloud Teams that can otherwise be siloed. Having visibility and protection of the end-to-end lifecycle results in a smoother process and saves time.
Cloud-Native Application Protection Platforms with Context
The true defining characteristic of CNAPP is its ability to take into context cloud-native. If it can scan containers for vulnerabilities, but runs totally oblivious to how that ties back to identity or posture management, it’s not a true CNAPP.
Gartner encourages businesses to take an integrated platform approach when implementing cloud-native application security by using either a CNAPP or a cloud-native security platform. With the help of a CNAPP, you can cover multiple security best practices in one single platform. As a result, you can tighten control and gain deeper visibility for comprehensive threat detection and management. Sonrai Security was actually named a ‘Representative Vendor’ by Gartner for CNAPP. If you’re interested in learning more about our total cloud security solution, consider a demo.





