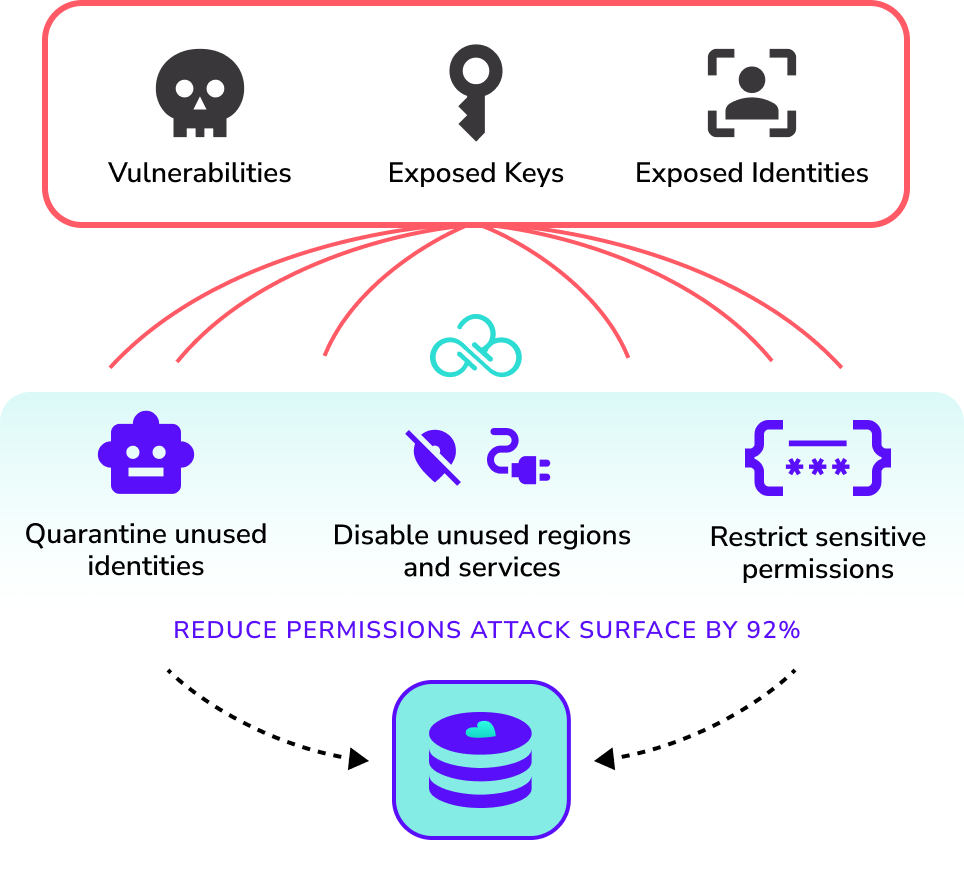
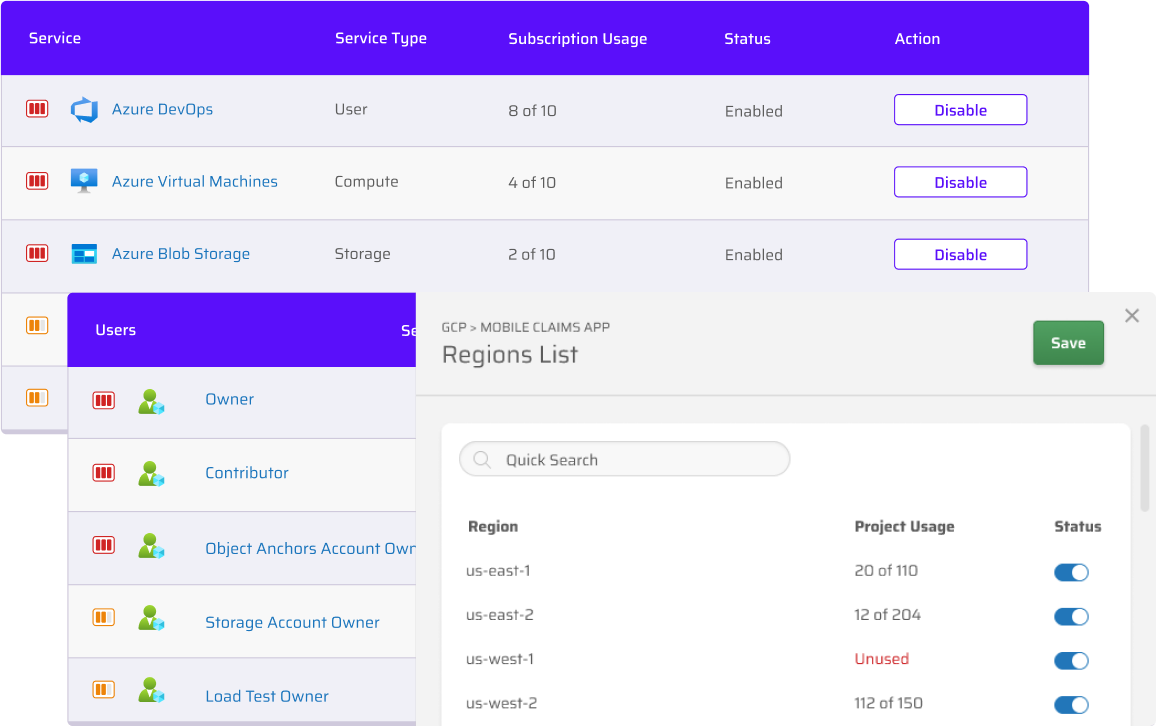
Sweeping least privilege that eliminates over-permissioned identities and protects unused services, identities, and cloud regions.
Secure Without DevOps Friction
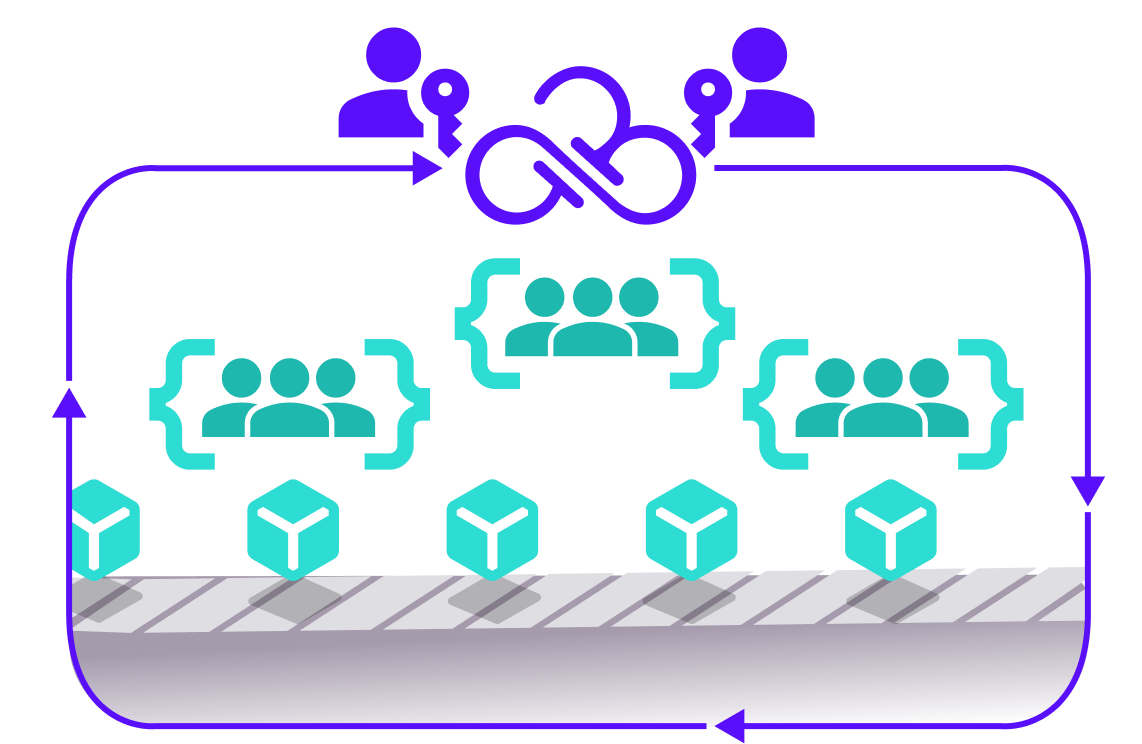
Security, Cloud Operations, and DevOps teams are juggling collaboration with their own unique initiatives – it’s a recipe for friction.
The Cloud Permissions Firewall provides a solution every team is on board with. Security gets the least privilege protection, operations gets the automated policy management and scalability, and developers get to develop without concern or uncalled-for denied access. Who says good security has to come with a price?
Report and Audit With Confidence
Rich analytics, intelligence, and dashboards empower you to see the current state of your cloud in real time. How many roles are over-permissioned? How many have been right sized? Is there any data in a region that conflicts with compliance requirements? Are you meeting requirements for least privilege? Get instant answers.
Auditing season is easy with insight into who can do what and tracked permissions-on-demand approvals. The Cloud Permissions Firewall gives you instant action with security and auditing insights on the side.
Ready to Instantly Reduce Access Risk?
Start a free trial or get a demo with our cloud experts to see how security teams can reduce risk without slowing down business.