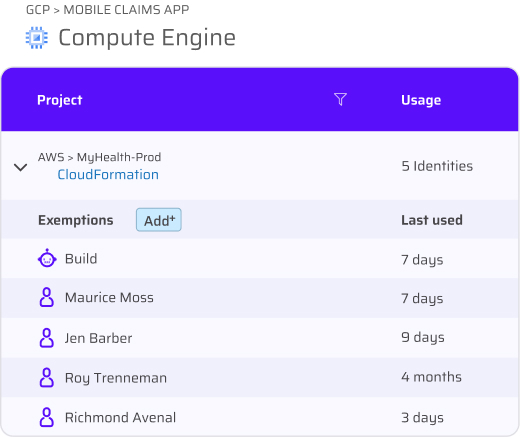
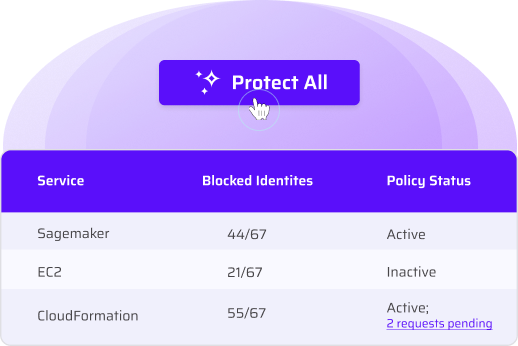
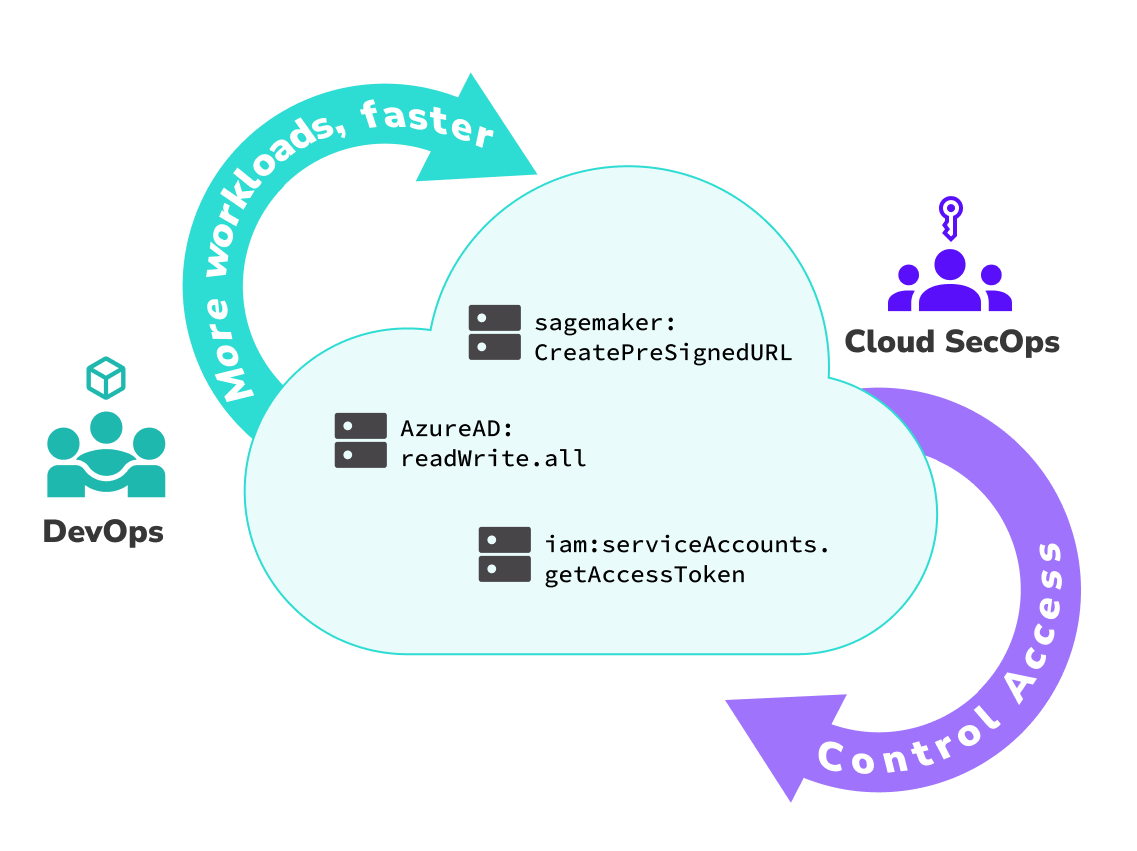
Least privilege is the gold standard for managing identities and reducing risk, but pulling it off at scale is hard. There are 42,000+ possible permissions, so let’s focus on protecting just the most impactful ones.
This least privilege solution strips away unused sensitive permissions and access from every identity not using them – all in one sweeping action.