Frequently Asked Questions
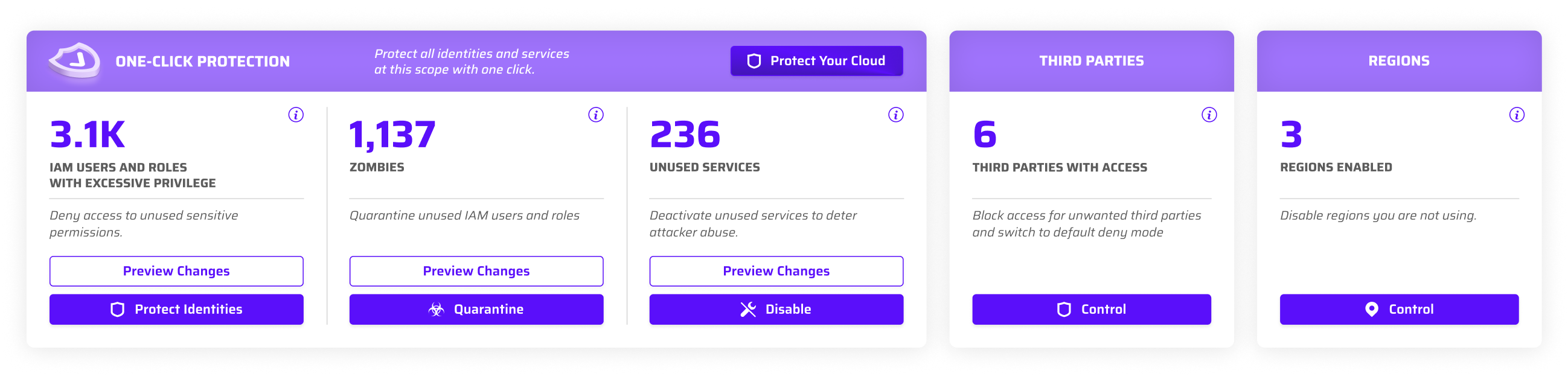
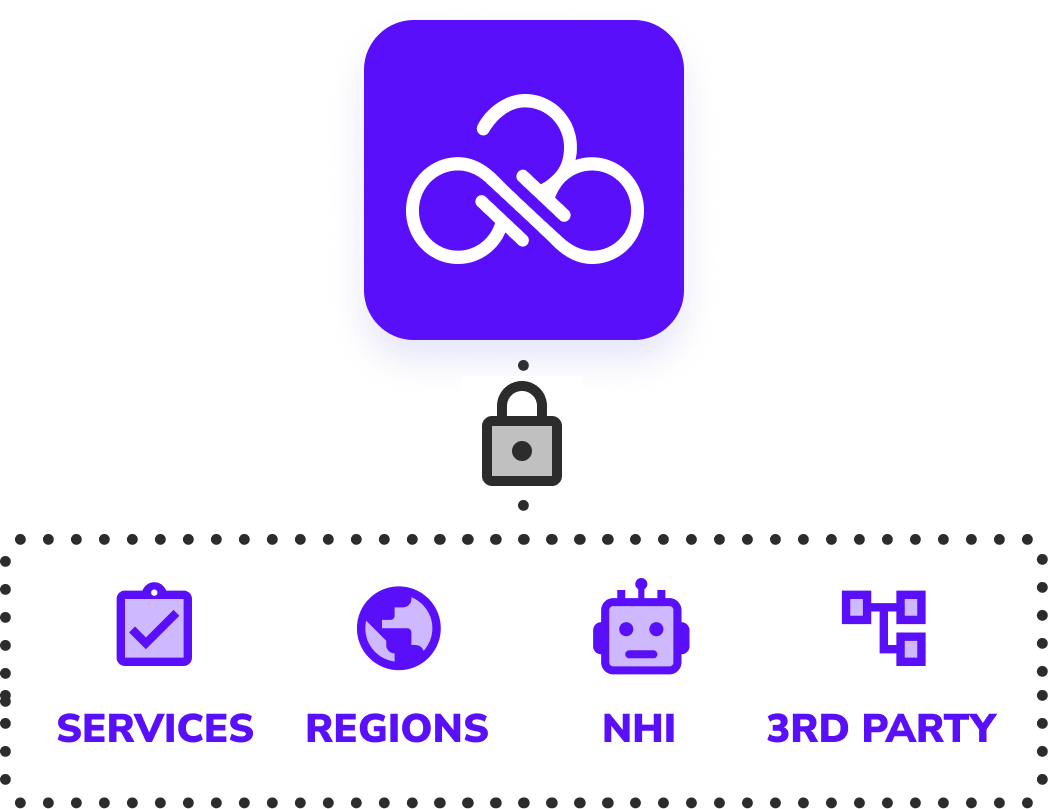
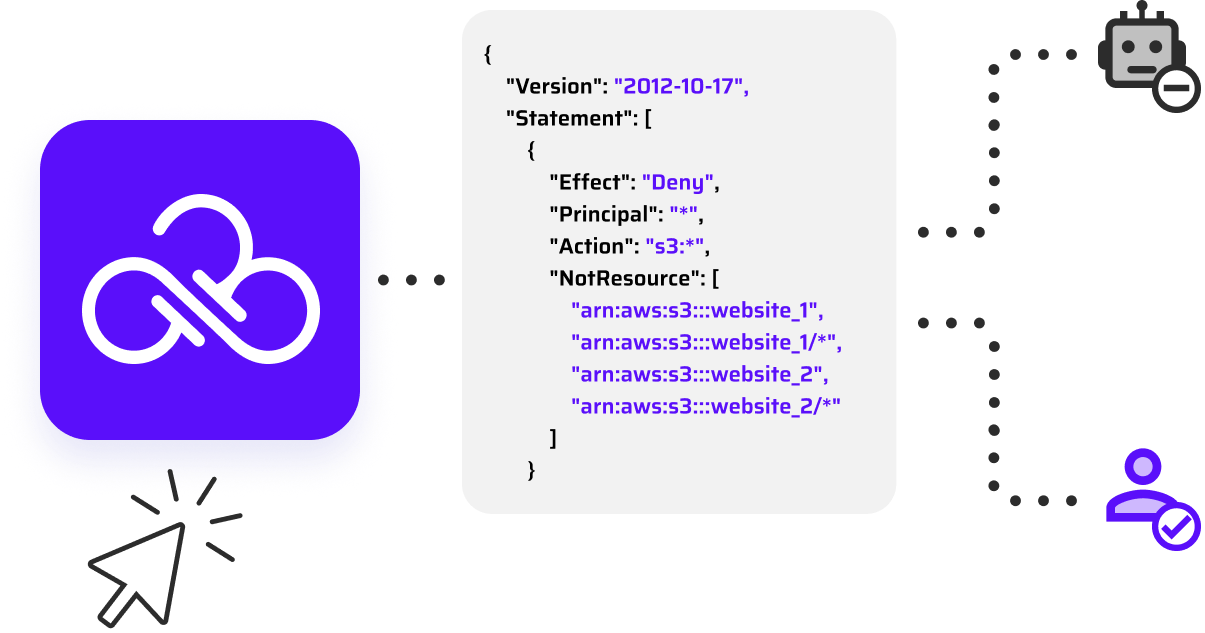
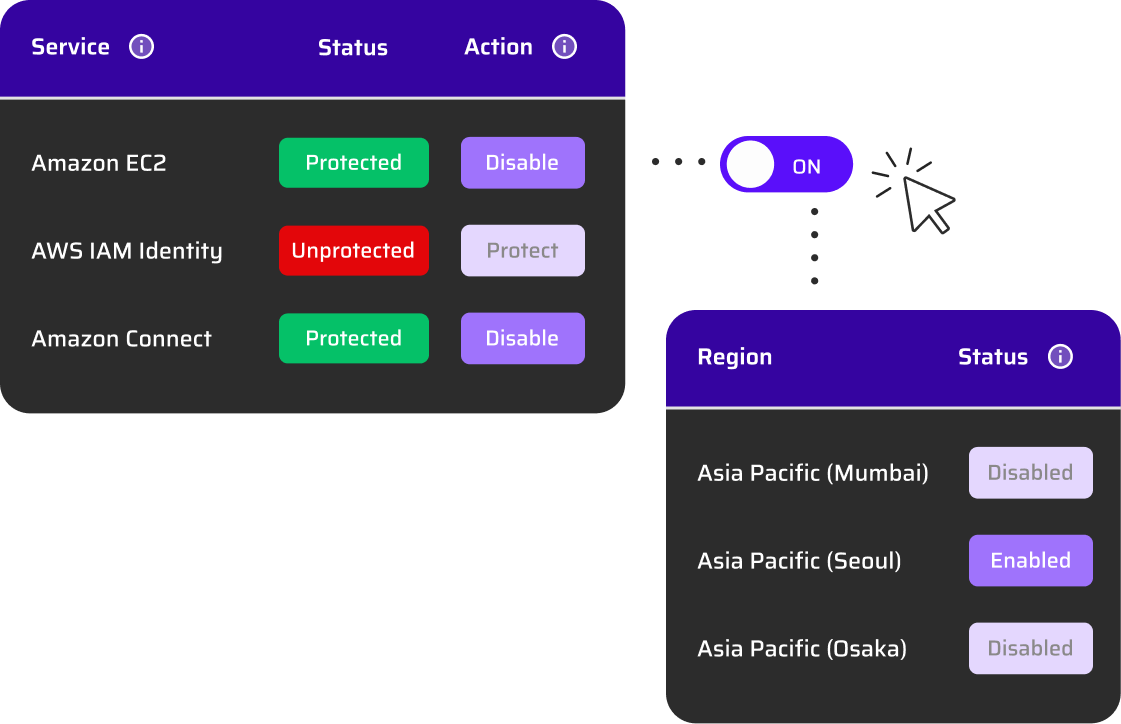
The Cloud Permissions Firewall continuously analyzes real permission usage across all identities and automatically blocks unused privileges using cloud-native, org-level policies. Permissions become dynamic and on-demand, ensuring identities only have access when they actively need it — without manual intervention.
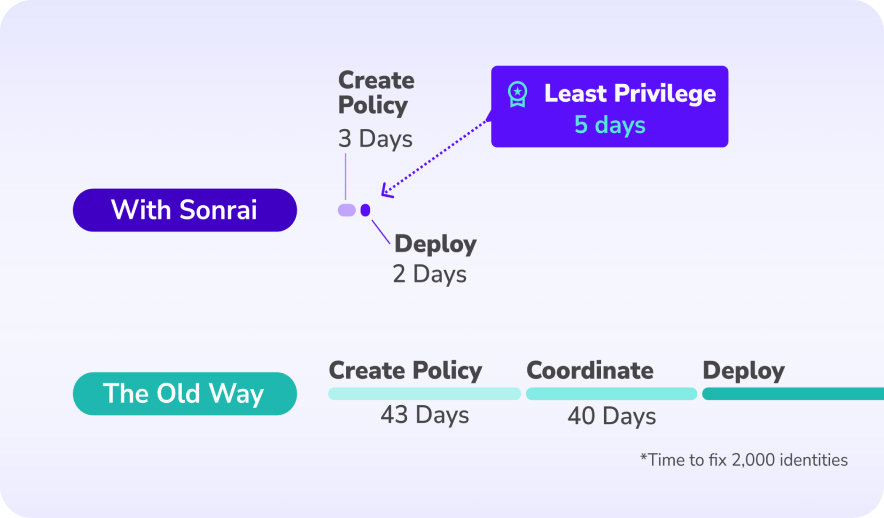
Traditional CIEM tools focus on visibility and reporting, leaving remediation manual and hard to scale. The Cloud Permissions Firewall actively enforces least privilege in real time, automatically reducing standing access without breaking production workloads.
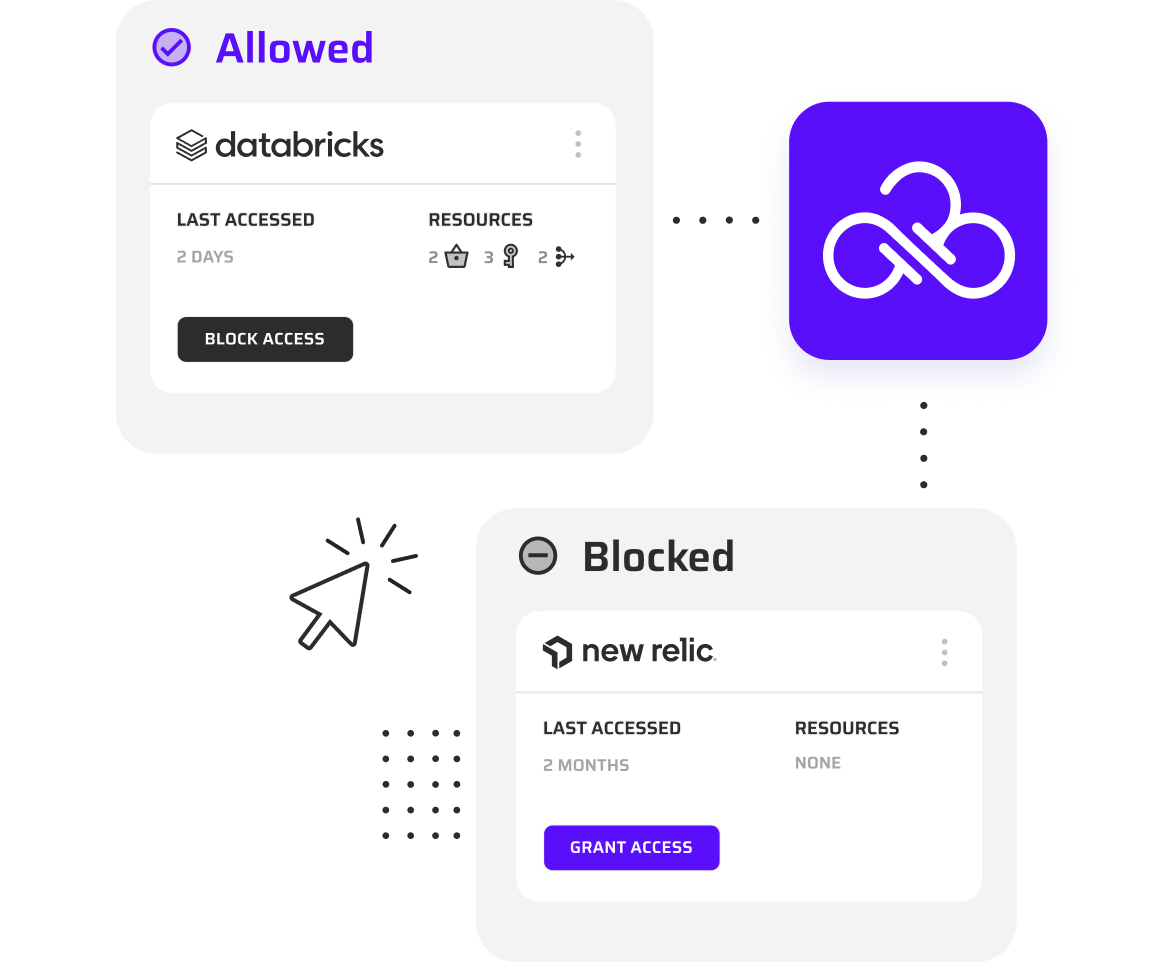
Yes. Cloud Permissions Firewall natively supports AWS and GCP, providing consistent, automated permission enforcement across multi-cloud environments from a single platform.
No. The Cloud Permissions Firewall only blocks permissions that are unused, while allowing actively used privileges to remain available, avoiding downtime and operational disruption.
Yes. The Cloud Permissions Firewall safely protects unused identities by dynamically restricting excess permissions without deleting accounts, preserving operational integrity while eliminating unnecessary risk.