
Share this entry

You ‘Shifted Left’ off a Cliff
This blog is the second piece of a three-part series. The first blog is available here.
Your organization has shifted left, but it’s shifted your cloud security far too left, and off a cliff. In the majority of the organizations that I work with, security in the cloud is effectively outsourced to the DevOps teams, and the results are concerning. Developers are building our clouds with Infrastructure as Code, but the security procedures haven’t caught up – its all-Dev-no-Ops. Before I proceed, I am compelled to clarify my full support of DevOps and recognize they have found themselves tasked with a responsibility inconsistent with your goals and resources. However, the fact of the matter is that they are not incentivized to prioritize security as they are constantly directed to “get it [code] out the door” faster and faster. In contrast, many DevOps teams play a large role in the success of the organizations I see with strong security. In summary, DevOps teams can have a great impact on an organization’s cloud security, but many do not.

When it comes to the cloud, the Security team is usually in the dark. As we have already discussed, there is rampant underinvestment in training and education for IT teams making the shift from the data center to the cloud, as well as for the DevOps teams who find themselves tasked with cloud security. Security teams also find themselves in the dark when it comes to visibility across their entire cloud and all the risks within it. This lack of visibility combined with a lack of training, results in functioning teams that do not fully understand the cloud, its risks, and what to do about them. For the risks that they do understand, they lack the strategy or tools to accurately detect them.
Sonrai Security’s Research team utilized extensive data sets to gain a better understanding of where enterprise security is. To provide some background on our methodology, Sonrai divides cloud security into 4 primary technical pillars; Platform (CSPM), Identity (CIEM), Data, and Workload Protection (CWPP). Across the pillars, from a governance perspective, we assign Security Maturity levels to cloud workloads / environments that are of importance to the organization, we call these ‘Swimlanes’. The maturity levels start with 0-Exposed and progress through 1-Basic, 2-Moderate, 3-Advanced and finally 4-Resilient. For very specific workloads/environments there is a 5th level of Zero Trust.
Learn More About Sonrai’s Cloud Security Maturity Score.
Our research results, based on actual Sonrai Security product telemetry gathered at initial deployments, left me with three major concerns. First, from an overall risk perspective, A significant portion of all organizations were at the ‘Exposed’ level. To be clear, this isn’t technically a maturity level, but instead a concerning state below the bare minimum. Beyond those organizations at ‘Exposed’, a fair number are at ‘Basic’ and an even smaller percentage have been able to achieve ‘Moderate’. Learning that the majority of a sample of enterprise clouds do not even meet the most basic of cloud security standards leaves no wonder why headlines report a cloud-based data breach every two weeks. In the market today, there are a lot of buzzwords flying around and marketing messaging promising to get your cloud to zero trust or resilient levels – however, it almost sounds tone deaf considering the reality that, first, we just need to help organizations secure ‘Basic’ or ‘Moderate’ maturity.

The second concern is how little risk is being addressed. Again for Sonrai background, our platform provides you ‘Swimlanes’; their purpose is to enable you to logically organize your cloud by how you view it in your company. The most common example is by application, where each Swimlane represents an application regardless of how it is composed in your cloud. For each Swimlane, security controls are evaluated, with an overall risk rating (High, Med, Low) and a Security Maturity Level (Expose, Basic, etc.) being calculated. For every control failure we generate a risk finding, which goes to the Swimlane owner, who is almost always the DevOps team accountable for the application.
We found that only 43% of the detected risks are being addressed. That means that across the average cloud, almost 60% of all risks are not being managed. You don’t need a dedicated research team to tell you that, if almost 60% of the risks in the average cloud are not being addressed, then the state of cloud security is struggling. Only further emphasizing this point, our data shows us that the ‘Overall Risk Level’ for each of the 4 pillars (CSPM, CIEM, Data & CWPP) is ‘High’. There were some areas where a few customers were at a ‘Medium’ Level. None were at low risk.
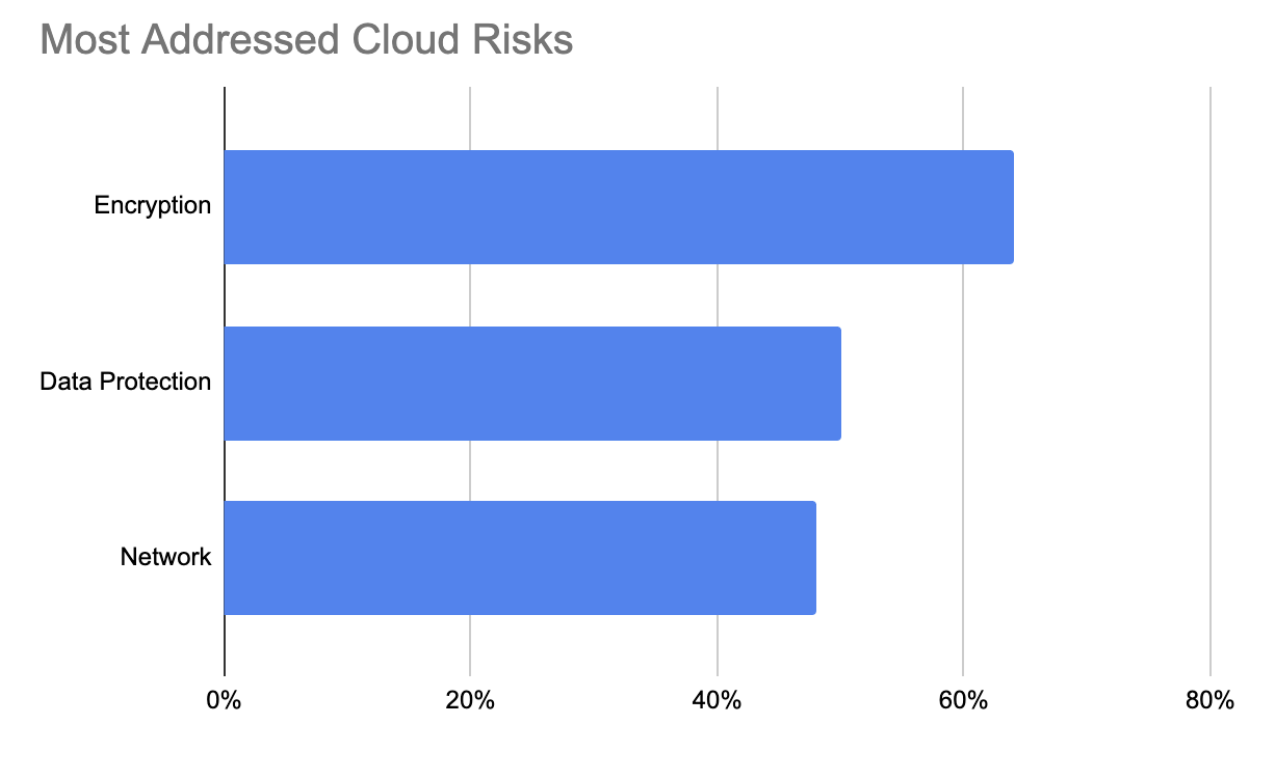
My final concern from the research relates to the most and least addressed control failures (risks). Of the 43% of the risk findings (aka: tickets) being addressed, the report found the Top 3 are Encryption (64%), Data Protection (50%) and Network (48%). Across the Top 3, just over half of the risks are being addressed (54%). The concern grows when you recognize that all three risks are from the same Security Pillar (Platform – CSPM). None of the other Security Pillars showed up in a meaningful way. There is a clear and reported lack of focus on Identity, Data, and Workload.
Flipping the perspective, the research considered the Bottom 3, where we see the least addressed risks being: Audit (31%), Least Privilege (30%) and Credentials (24%). The ‘Audit Security Area’ isn’t the lowest of the three, it should tell you something very interesting (read: concerning.) The purpose of the controls in the ‘Audit Security Area’ is to ensure that your cloud has the necessary auditing and logging enabled in your cloud. What this means is, most organizations are missing critical logs and audit findings. This simple misconfiguration is involved in many of the cloud data breaches in the media headlines as organizations had no idea their environment was compromised. What makes it worse is, even if they were to identify the exposed data store, without the proper Audit logs you are unable to determine who/what accessed it and what they might have done with it.
Further considering the research findings, when we look at the other two of the Bottom 3 (Least Privilege and Credentials), we see that they both relate to securing Identities on the cloud. This is concerning as Identity has replaced networks as the boundary for security in the cloud. To reiterate, what the industry perceives as the ‘boundaries’ of cloud security is the risk factor that is being addressed the least. There is a dangerous gap here.
In the final-part of this blog series, I’ll walk through the repercussions of insufficient focus on Cloud Identity risk.


