Table of Contents

Share this entry
When it comes to insufficient cloud security measures, organizations are unaware of the danger they face. Perhaps their organization migrated to the cloud and brought along the same security tools and data and identity management they used on-premises, because it worked for them there. But the reality is, the cloud brings complex, unknown, and unseen new risks. And at the center of it all is a key player: identity.
We won’t pretend we’re the first to tell you you’ve got a cloud security problem on your hands. The market is flooded with vendors calling out the cloud identity crisis – writing blogs, making ebooks and guides to tell you how important securing cloud identities is. Instead, we wanted to design something that goes beyond telling you just that you have a problem, but actually examines your unique environment, details what your specific problem is and where the problem exists in your cloud. We couldn’t just stop there. We’re taking things even a step further by telling you what you can actually do about those problems. That is why we are now offering The Cloud Identity Diagnostic.
Sonrai’s Cloud Identity Diagnostic
The Cloud Identity Diagnostic is a frictionless assessment of your cloud identity and entitlements management posture. This is a snapshot of your identity, access and permissions risk and is available 48 hours after the analysis begins. Sonrai’s patented technology examines your cloud environment (without disruption) to reveal what risks exist in your environment. The output is a comprehensive and easy to understand report detailing identity posture and hygiene, overall identity risk score, systemic issues that require attention, and immediate actions that could be taken across the cloud environment to reduce risk.
But why did we make this in the first place, and how can your business use it?
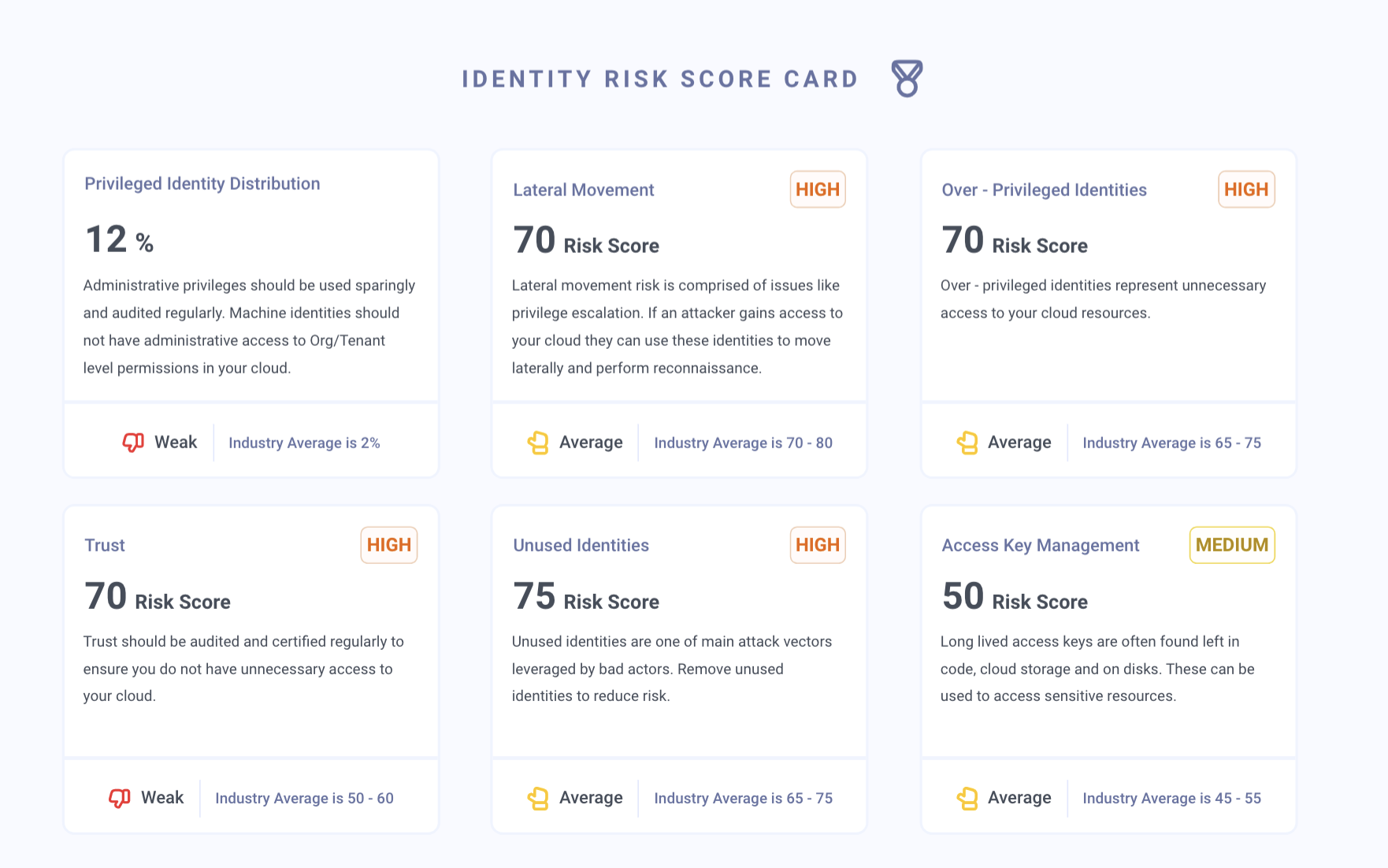
In the Cloud Identity Diagnostic, we examine six criteria in our evaluation because of their significant roles in potentially putting your business at risk. These are concerns that pose the greatest risk or play common roles in bad actor’s finding their way to data access & business disruption. They are:
- Privileged Identity Patterns
Your privileged identities are some of the most valuable entities in your cloud – and often what attackers are looking for during recon. Understanding the systemic patterns around their privilege is critical. How widely are admin privileges used? Are your highly privileged identities mostly machine or person identities? How do they acquire privilege – directly or inherited?
- Lateral Movement
Attackers are looking to move laterally through your environment once they have breached your ‘perimeter.’ The identity relationships that give them this leeway include privilege escalations, toxic combinations of permissions, and permission-chains so long you can’t see them. Uncovering and eliminating these risks, especially the ones that relate back to sensitive data, will reduce lateral movement and significantly improve your overall risk score.
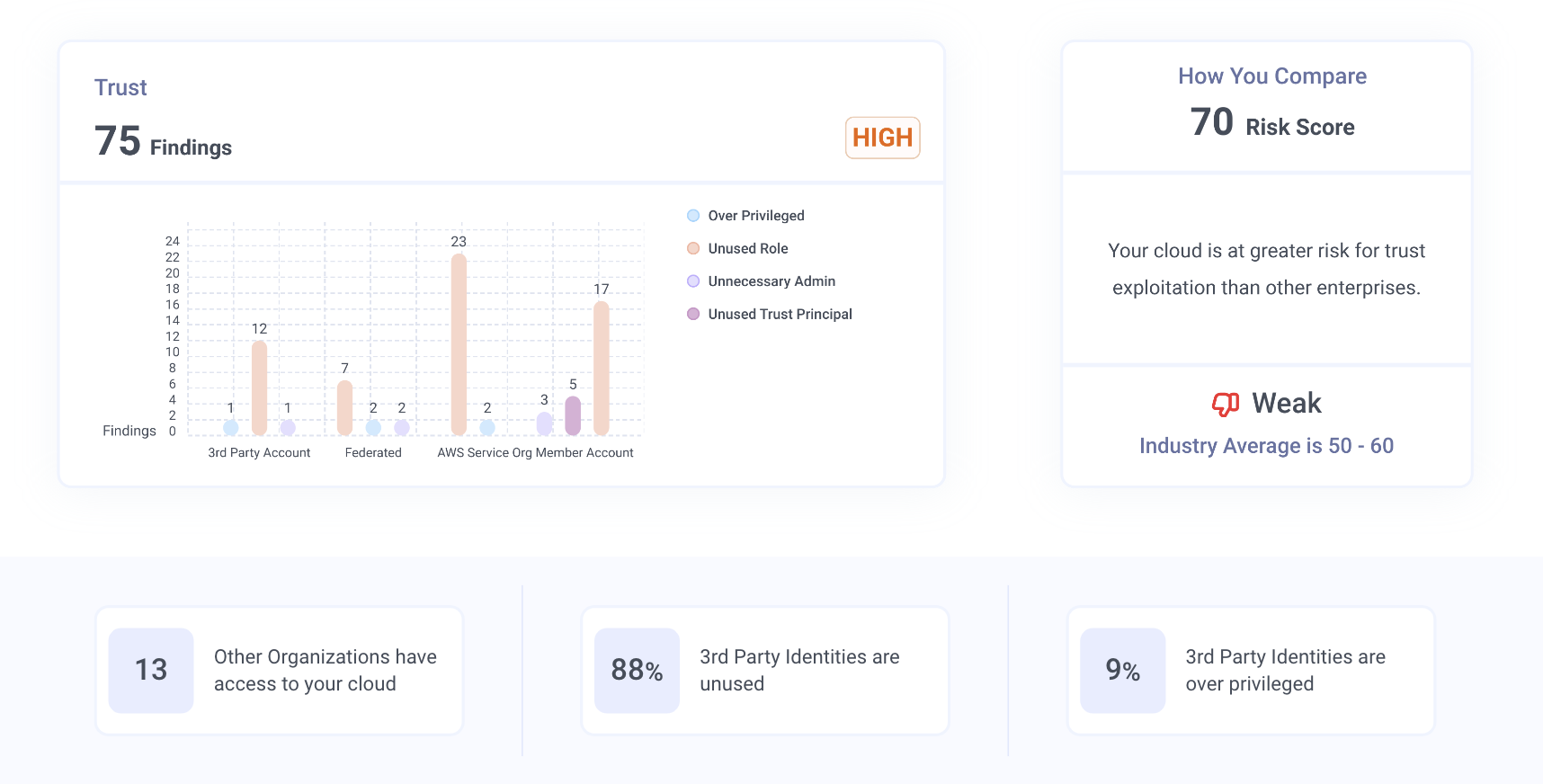
- Trust Relationships
Trust relationships are a complex construct in the cloud where a logical connection is created between accounts, cloud providers, or third parties for the purpose of allowing access to cloud resources. The problem is, these can quickly become overprivileged, and are very hard to have insight into, especially in the case of third-party trust. This trust can be forgotten about, overprivileged with broad access rights assigned, or just hard to track. A great number of data breaches come via third-party access. A safe rule of thumb is that your third-party’s security level is your security level.
- Access Key Hygiene
Access keys serve as credentials for identities to have programmatic access to resources. They are a valuable, and therefore, risky, entity if left unprotected. Think of them as permanent credentials that can always be exploited if they fall into the wrong hands. Access keys are often leaked (think: a developer accidentally leaving them in a public code repository, or being left in a datastore with insufficient authentication process,) and once an attacker has hold of one, they can use all the permissions assigned to the user associated with them. That’s a lot of privilege you don’t want to give away.
- Unused Identities
Unused identities are unnecessary avenues by which an attacker can gain access to your data. Identity represents a significant attack surface in the cloud, so ensuring only those that are used exist in your cloud is important. However, it is difficult to ‘see’ all identities, let alone the unused ones, specifically considering machine identities. Unused identities can get lost across accounts or clouds, or even become orphaned (e.g. a developer you’re governing in Active Directory creates machine identities in the cloud, and then leaves the organization and is removed from AD, but the cloud identities they created remain. These orphaned identities now have no owner and are not tied back to AD leaving them with no oversight.
- Overprivileged Identities
Overprivileged identities are one of the most known risks, yet never ceases to pose as a challenge to secure. Just as identities are considered an attack surface, their permissions are too –and excessive privilege is an unnecessary increase in attack surface. More privileges assigned is just more privileges to be used maliciously, and more opportunity for lateral movement. The issue is, it’s not always easy to tell what the threshold is for being ‘over privileged’ nor which identities actually are.
The Sonrai Cloud Identity Diagnostic analyzes your unique cloud in each of the six areas above and reports out findings including the number of issues, where they exist, how your findings compare to industry benchmarks, specific top concerns and suggestions for what to do to fix.
What Pain Points Does Cloud Identity Diagnostic Solve?
For the Practitioner:
Cloud, IAM, and Operational teams: You know your cloud environment best. You build it every day and you know it’s ins and outs. Sometimes communicating that you see potential security risks higher up the chain of command is difficult. The Sonrai Cloud Identity Diagnostic can serve as a tangible report you hand in to leadership to exemplify serious identity and access risks, without having to find out the hard way. Cloud Identity Diagnostic gives you a similar output to a proof-of-concept without the burden of your effort and time.
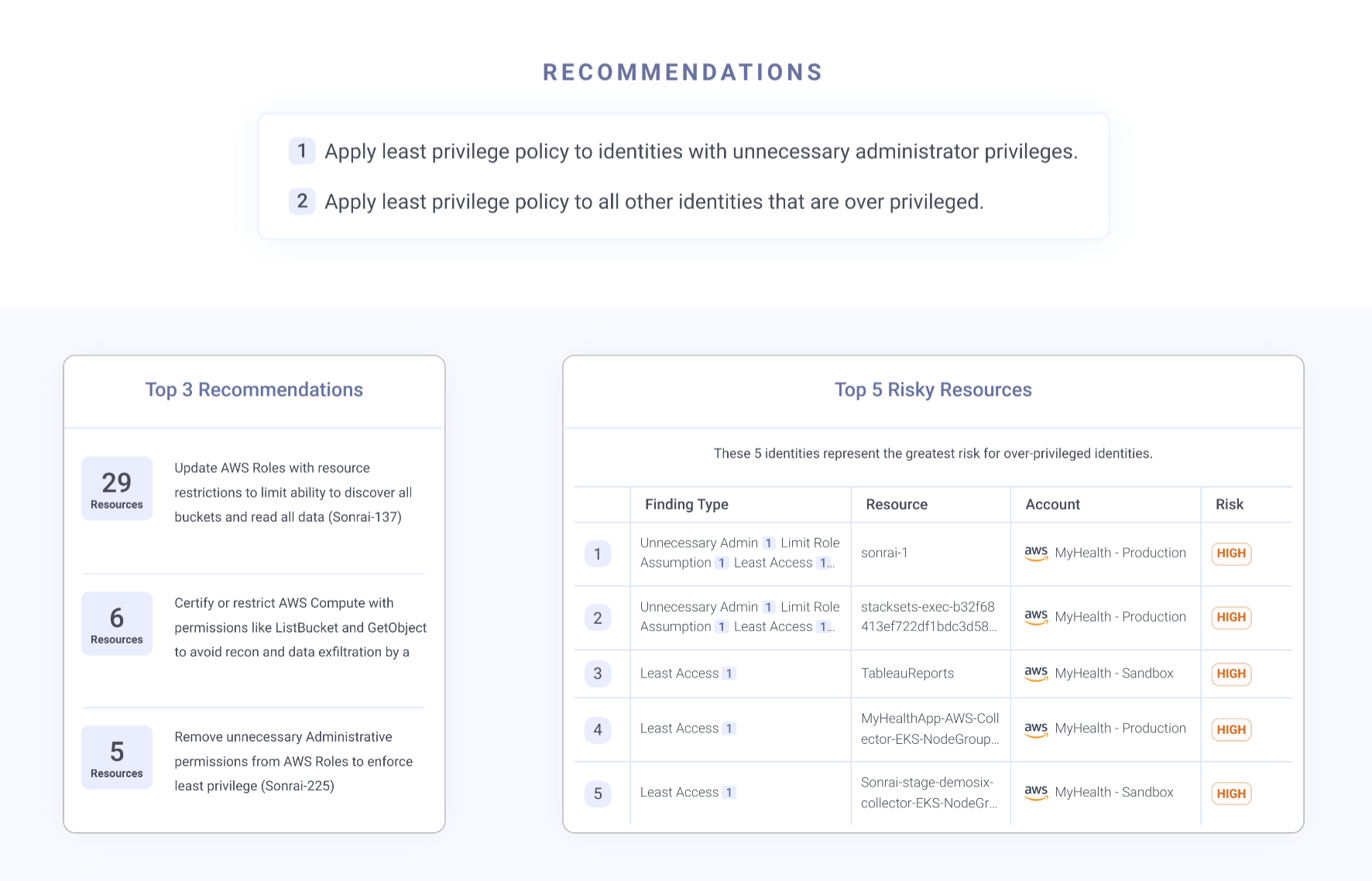
It’s not helpful to just have security blindspots and risks pointed out with no follow up. You can use the report to receive technical findings that give specific action items to tick off your list. This includes the ‘Top 3 Recommendations’ and ‘Top 5 Risky Resources’ with specific names, accounts, and Sonrai policy violations.
For Leadership:
Receive an executive summary for highest risk areas, industry benchmarking, and high level strategic recommendations.
Integrating and implementing a new solution, let alone purchasing one, is a big decision. Especially if you are potentially replacing pre-existing tools. Clear assurance that this is really a necessary purchase gives peace of mind. The Cloud Identity Diagnostic can be used as confirmation that your cloud (and business) is at risk, and you do really need a solution.
In the Executive Summary, you’ll receive clear risk assessment scores and benchmarks against peers in your industry and best practices, all to give you an idea of the state of your cloud. This is an easy-to-share summary that can be used in any discussions & negotiations around taking next steps in implementing a new solution.
As far as actually tackling the problems in your cloud – it can be overwhelming and confusing to know where to start. The report offers unique insight tailored to your specific environment with clear high-level recommendations that can help define what your security strategy should look like. It offers a clear answer to what your biggest risks are so you know where to prioritize resources and time.
Know the Unknown: Diagnosing Cloud Identity Risks
Awareness raising and thought leadership can only go so far. What is the next step once the market has told you you’ve got a cloud identity problem? The next step is getting your cloud identity diagnosis. Know what your greatest identity risks are, where they are, and what to do about them. Sign up for a free Cloud Identity Diagnostic and walk away with a tangible report offering immediate value without a lengthy proof-of-concept process.




