Table of Contents

Share this entry

What is Sonrai Dig?
The rapid adoption of cloud technologies has introduced numerous new challenges for Security, Compliance & Audit, and DevOps teams. Although cloud platforms such as AWS, Microsoft Azure and Google Cloud Platform (GCP) introduce substantial operational benefits, they also introduce new challenges for an organization’s ability to secure data in the cloud and meet ever-increasing regulatory burdens. Unfortunately, many legacy data security and access control solutions do not align well with existing and emerging public cloud provider technology stacks. In some cases, they do not align at all. Complicating matters are multi-cloud environments that provide disparate cloud security models. Emerging Identity and Data governance solutions, like the best cloud security platform, Sonrai Dig, solves this challenge via a heterogeneous security and control framework across cloud stacks to ensure critical aspects of data security (including audit, identity and access management, data access, and compliance) are effectively addressed in a single provider cloud or multi-cloud implementation.
Introducing the Sonrai Dig
The Sonrai Dig is built on a sophisticated graph that identifies and monitors every possible relationship between identities and data that exists inside an organization’s public cloud. Dig’s Governance Automation Engine automates workflow, remediation, and prevention capabilities across cloud and security teams to ensure end-to-end security. We believe identity and data controls are central to securing your cloud. Your cloud is flooded with non-people identities, sprawling data, and imminent danger. It’s why Sonrai Dig, built on patented graphing technology, perfectly maps all possible access and activities. This is how you automatically enforce least privilege, monitor access to crown jewel data, and automate intelligent CSPM. You get security far superior to anything possible before.
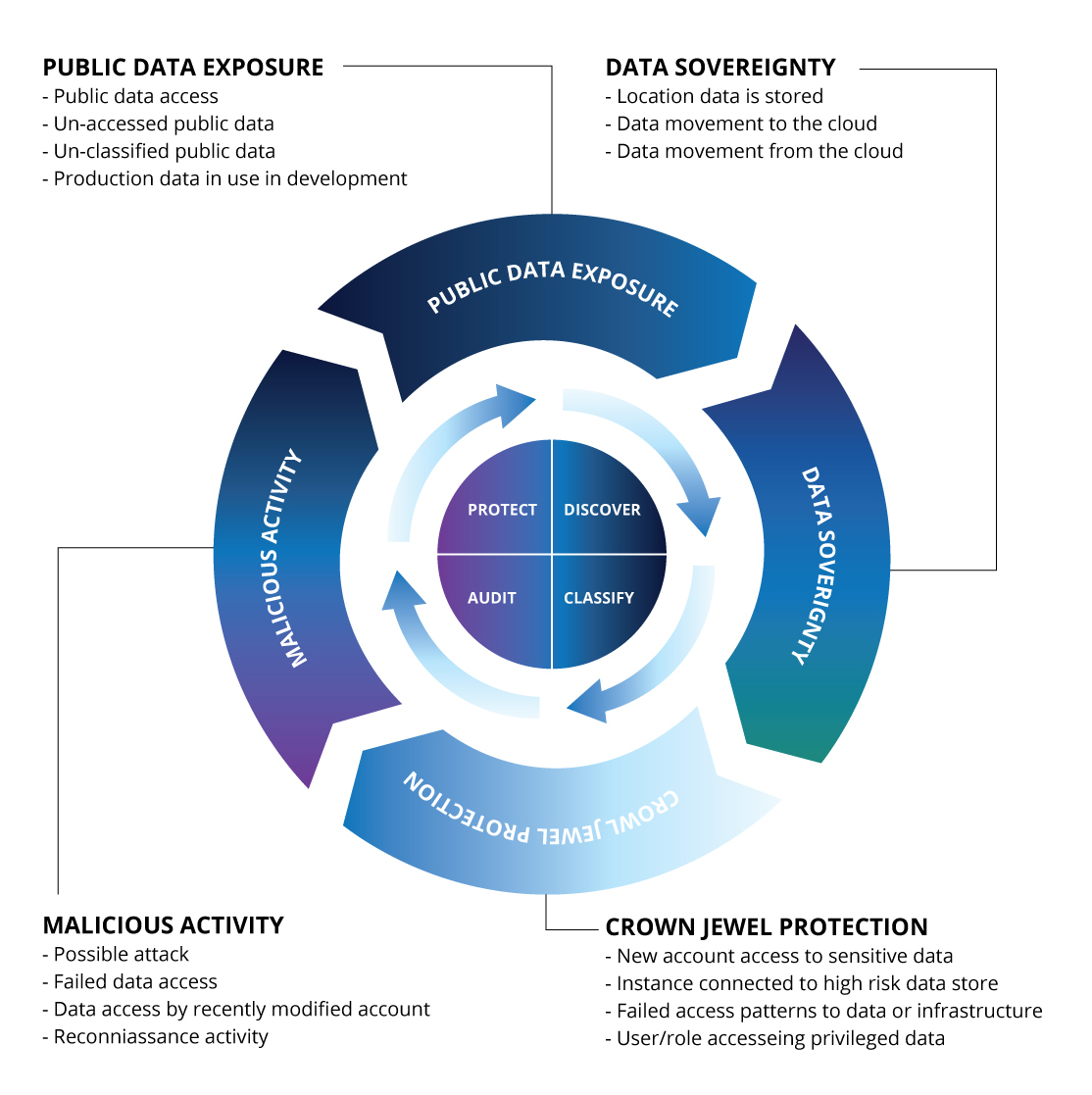
Discover: Automatically, visualize and map identity and data across your clouds
Classify: Leverage machine learning to determine data type, importance, and risk
Audit: Continuously map permissions, configuration, and access to data
Protect: Use behavioral controls to detect and prevent theft
Sonrai Dig helps companies reduce risk, ensure compliance and increase operational efficiencies.
Risk and security monitoring
Identity configuration risks, public data exposure, and excess privilege are reported across cloud providers, accounts, countries, teams, and applications.
Compliance Enforcement
Frameworks covering regulations and industry recognized controls provides you with the ability to create your own frameworks to meet the exact needs of your organization.
Cloud identity and data compliance
Data sovereignty, data movement, and identity relationships are all monitored and reported to ensure conformance to sovereign, GDPR, HIPAA, and other compliance mandates.
Drift Detection
Detect drift on an identity, data store or a particular resource to ensure compliance is baselined, monitored, and continuously met.
DevOps multi-cloud efficiency
Cloud provider management models are normalized with centralized analytics and views of data across hundreds of AWS Accounts, GCP Projects, and Azure Subscriptions.
Misconfiguration Prevention
All changes implemented (via console, provisioning tools, or programmatically) are detected and continuously monitored for configuration mistakes.
Sonrai Tracks Data Access Within a Cloud Provider and Across Clouds
Implementing controls around what has access to data is fundamental to any data security and compliance program. Although each unique cloud provider delivers services and APIs to manage identity and access to data for their stack, they are not standardized across all the stacks available (e.g., Amazon, Google, and Microsoft), do not address third-party data stores, and often require use of low-level tools and APIs. Sonrai Dig resolves this problem through normalized views and control of cloud identity and data access. Use cases supported by continuous monitoring of access include:
| User Configuration Risk | Suspicious User Activity | Identity & Access Risk |
- Account password policy violations
- MFA not enabled
- Trust relationships – ability to escalate privilege
- Credential/key/role lifespan
- Separation of duty violations
- Interactive shell and API using same credential
- Failed escalation attempts
- Admin user created account with alternative access
- Account/role created with excessive privilege
- Over permissioned identities that never execute actions allowed
- Assume role and switch role functions that allow privilege escalation if compromised
- VPC with open access
- Host or instance with open access
Sonrai Dig Reduces Identity Risk
Sonrai Dig is focused on reducing the risk of cloud breach and compliance violations through the introduction of cloud-specific identity risk management workflow across the following important categories:
- Least Privilege: Sonrai Dig graphically maps all of your identities and determines their effective permissions allowing you to get to and maintain least privilege across all of your clouds.
- Separation of Duties: Sonrai ensures data is not stored or accessed from geographies that are outside security or compliance policy. Sonrai ensures that separation of duties is baseline, continuously monitored and maintained based not only on industry standards but also your own.
- Toxic Combinations: Sonrai aligns identity and access security policies with business risk to ensure the protection of crown jewel data is managed.
- Activity Monitoring: With continuous (24/7/365) monitoring, Sonrai provides monitoring and analysis of all identities in your cloud giving you end-to-end visibility to detect and respond to nefarious activity.
Sonrai Dig Ensures Compliance to Key Mandates
Data sovereignty, data movement and identity relationships are all monitored to ensure conformance to sovereign, GDPR, HIPAA and other compliance mandates. Compliance capabilities include:
- GDPR compliance: Geographic sovereignty is confirmed and data asset discovery is supported. PII data movement is monitored.
- NIST, ISO, HIPAA, PCI and other compliance reporting: Mandate specific reporting and continuous audit of all identity, developer and privilege access to regulated data assets.
- Data sovereignty monitoring: Data classification and location is determined. Movement between geographies and access from alternate geographies is monitored.
- Data asset inventory: Unreported data assets will be found, identified and monitored across cloud accounts and developer teams.
- Continuous monitoring of configuration data: Cloud configuration data, identity, data access, and data movement are collected, normalized, and available for compliance and audit teams.
- Configurable frameworks for your company and industry: Out-of-the-box support is available for major government and industry regulations. Frameworks can be easily customized for unique company requirements.
- Flexible third-party data connectors: Out-of-the-box support is available for industry leading cloud providers (e.g., AWS, Azure, and GCP) and data stores (e.g., Aurora, Cassandra,Gremlin, MongoDB, MSQL, MySQL, Oracle, Postgres SQL, SQL, SQL Server, etc.)
Sonrai Dig Increases DevOps and Security Efficiency
Sonrai cloud provider management models are normalized with centralized analytics and views across hundreds of AWS or GCP accounts and Azure subscriptions/resource groups to streamline governance for DevOps and Security teams. Operational capabilities include:
- Centralized model of identity and data. Sonrai models all activity and relationships across cloud vendors, accounts and third party data stores. All views pivot on cloud provider, country, cloud accounts, application, or data store.
- Cloud-native query. Cloud Query Language (CQL) provides rapid interrogation of the complete and centralized model of all data and identity relationships.
- User and asset reports. User reports show all privileges and data to which a particular identity has access. Similarly, data reports show all those entities with access and history.
- DevOps and security personas. DevOps and DevSecOps team leaders pivot all functions across teams, applications and data. CISOs pivot on geography, provider, and compliance mandates.
- API’s and customization. API’s provide access to data and reporting functionality.
Summary
The Sonrai Dig has been developed to help businesses improve security, ensure compliance and increase operational efficiencies for their AWS, Azure, GCP and other cloud platforms. Core to the platform is the ability to gain a centralized and consistent view into cloud identity and data relationships, activity, and data movement across cloud accounts, cloud providers, and third-party data stores. Request a demo of the Sonrai Security cloud security platform to see if this solution is right for your cloud environment.






