Privileged Access Management for cloud.
Automatically protect every identity: human, non-human, and agentic AI.
Quickly Control Privileges and Access In Your Cloud
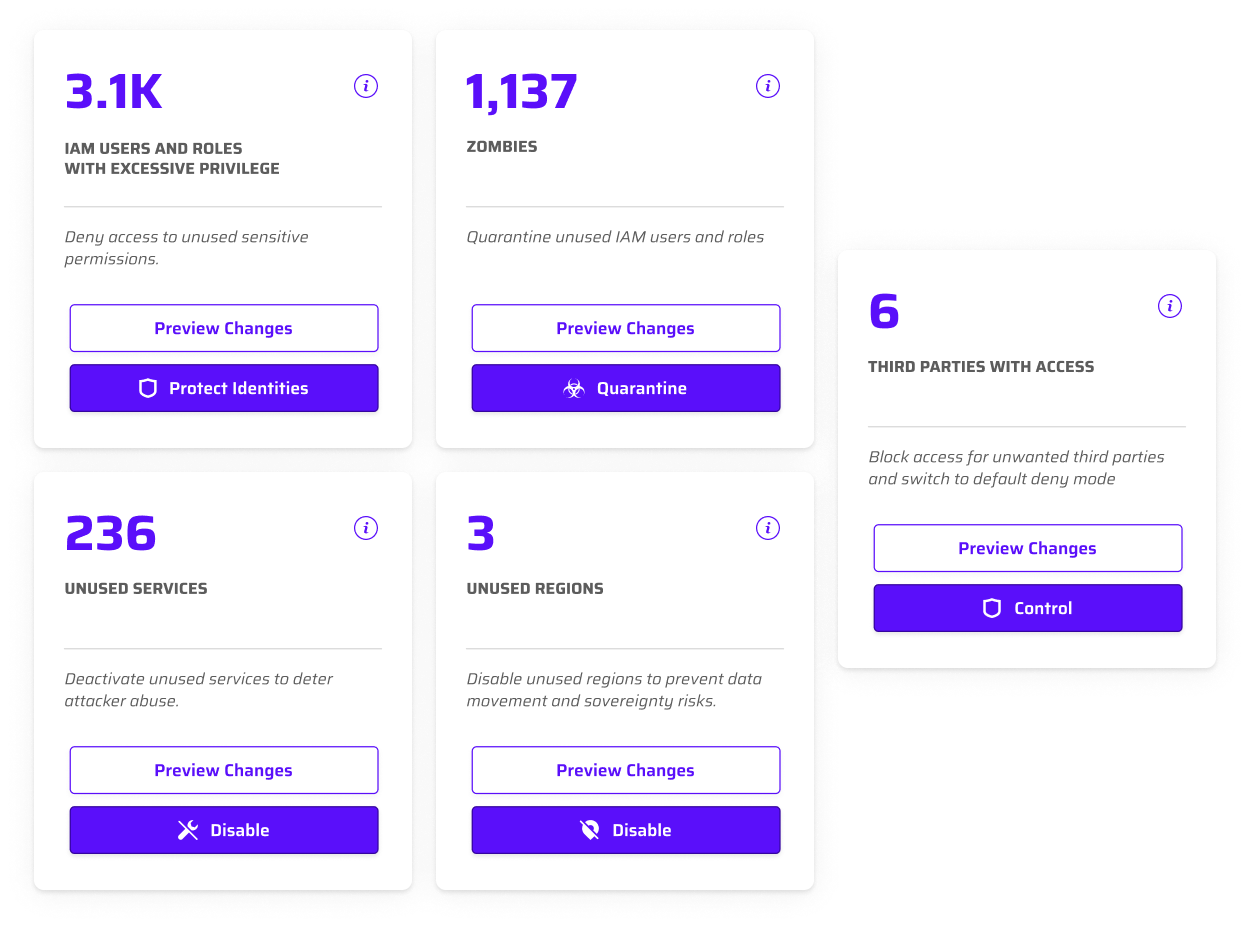
This isn’t just another visibility tool. The Cloud Permissions Firewall automates privilege control, shrinking your attack surface without the manual work of fixing policies. CloudOps can secure access instantly, eliminating excessive privileges and streamlining policy management—all without adding to your workload.
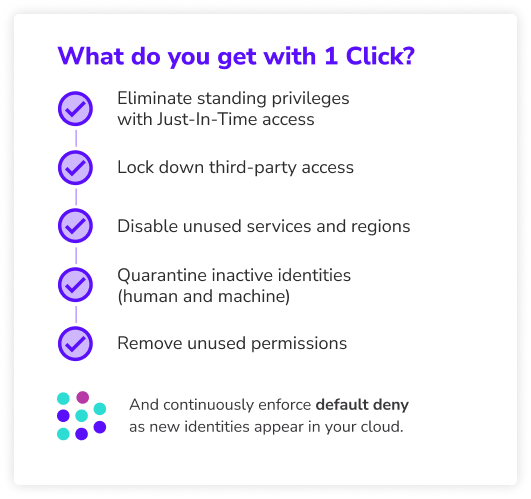
One Click, Months of Work Saved
Tired of mountains of alerts that no one gets to? Get results in days instead of months or years. The Cloud Permissions Firewall analyzes privilege usage across your entire cloud to determine exactly what your team needs. Unused privileges, access, services, and regions are blocked in seconds with automated global policies. Admin access is controlled with just-in-time access–keeping security tight without slowing down critical operations.
Delight Developers with Privilege-On-Demand
When developers need quick access, there’s no need to sacrifice security or slow them down. The Cloud Permissions Firewall restricts only unused privileges, ensuring your teams have uninterrupted access to what they’re already using.
New access requests are resolved in minutes through automated workflows integrated with your preferred ChatOps tools (Slack, Teams, Email), with every action fully tracked for audits. Developers stay focused on their work, while CloudOps teams maintain complete control.
What Our Customers Have to Say
Don’t take our word for it. Here’s what our customers say.


Cole Horsman
AVP, Security Operations“Sonrai helped us do in days what would’ve taken months—automating identity management and achieving least privilege across AWS.”


Preetam Sirur
Chief InformationSecurity Officer
“The challenge with deleting unused identities or enforcing least privilege is that we know it’s the ‘right’ thing to do, but everyone’s afraid it’ll break something or interrupt our development cycles. We don’t have to worry anymore.”


Brendan Putek
Director of DevOps“Within five minutes I had disabled regions that were unused across my entire AWS organization.”


Kenneth Milcetich
Director of Cyber and InfoSec“Sonrai not only identified the over permissive actions granted to our identities, but also provides a least effective access policy based on the identities usage...All of this boils down to a significant increase in our cloud security posture.”


Josh McLean
Chief Information Officer“Our transition from tedious, weeks-long tasks to accomplishing Least Privilege outcomes in just a few days has been remarkable. This approach has saved us a tremendous amount of time while also guaranteeing the security of all critical permissions.”


Chad Lorenc
Security Delivery Manager“Sonrai is one of the top tools to quickly scale when you're trying to do privileged management in the cloud.”

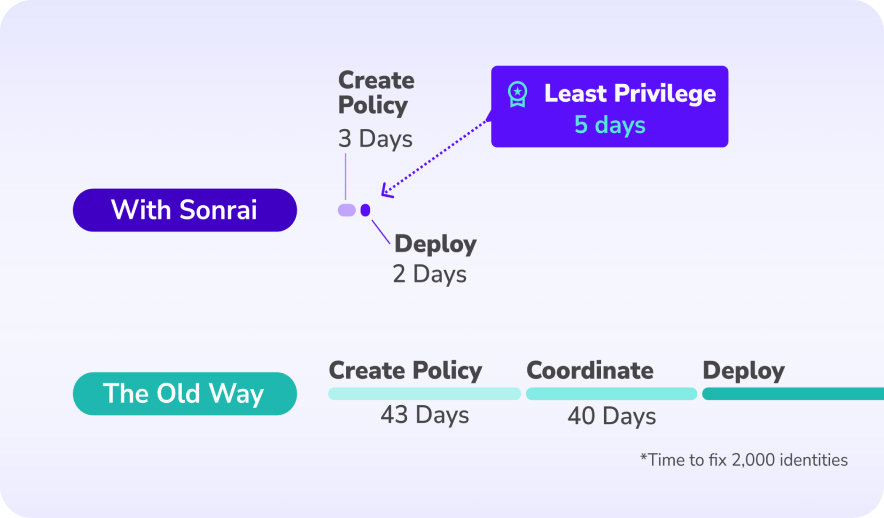
Achieve Least Privilege in 5 Days
Save your Operations team 97% of their time getting to least privilege with the Cloud Permissions Firewall.
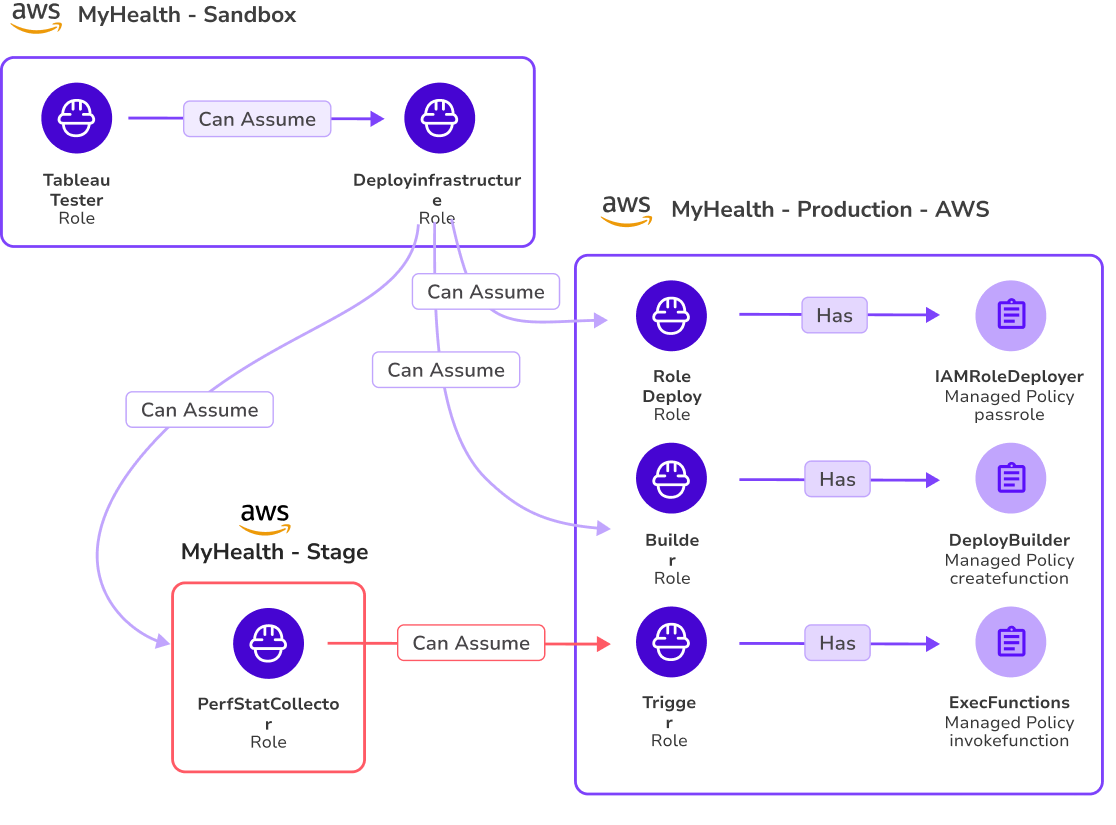
Disrupt Hidden Attack Paths with Sonrai CIEM+
Enhance the Cloud Permissions Firewall with additional layers of protection. Our Cloud Infrastructure and Entitlements Management (CIEM+) solution identifies and disrupts covert attack paths formed by toxic permission combinations across multi-cloud environments. Sonrai’s patented analytics reveal hidden identity chains and security gaps, providing added protection to secure your cloud against sophisticated threats.
Discover how CIEM+ uncovers hidden risks and strengthens your cloud defenses.
Ready to See It in Action?
Start a 14-day free trial and see results in two hours. Click below to see how Sonrai delivers one-click protection with zero disruption in your cloud.