Table of Contents

Share this entry

Google Cloud Platform (GCP), like many other cloud providers, recommends operating within the shared responsibility model. This model essentially helps map out what exactly falls under Google’s responsibility, and what the customer is held accountable for in relation to operating within GCP.
Being many organization’s only cloud provider, and one of even more organization’s multiple cloud providers, GCP faces sophisticated security threats and concerns. In fact, Google Cloud’s November 2021 report revealed just how targeted cloud workloads have become. Nearly 75% of intruder attacks came from misconfigurations, third-party access or poor customer security hygiene. So, it is safe to emphasize how important clearly distinguishing between who owns what is.
What is Google’s shared responsibility?
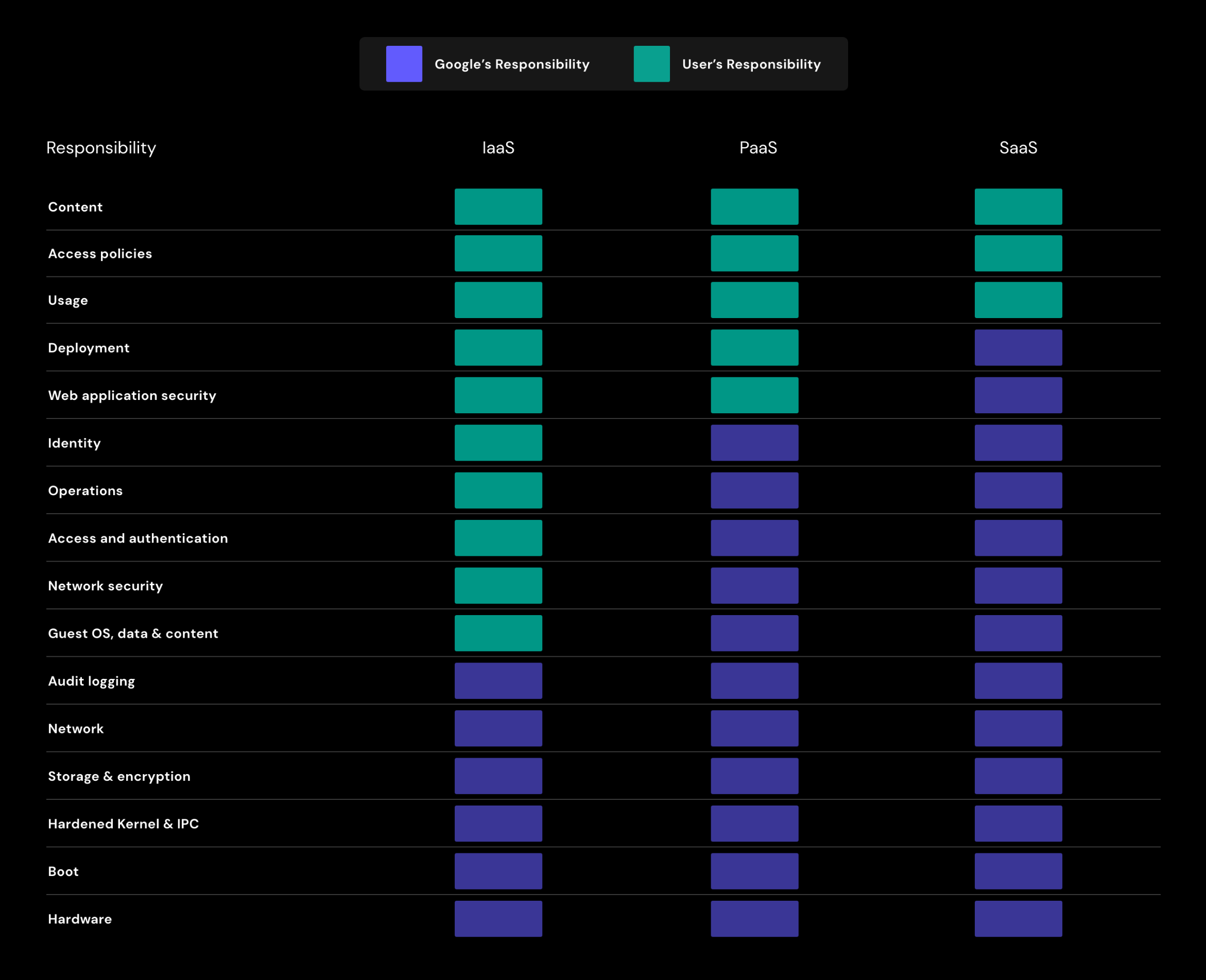
Google and cloud providers in general, are responsible for the security of the cloud. Responsibility allocation depends on a number of things including whether you’re referring to Iaas, PaaS or Saas. Within those different services, Google breaks down the responsibility categories into content, access policies, usage, deployment, web app security, identity, operations, access and authentication, network security, guest OS data, networking, storage and encryption, and finally, audit logging.
When utilizing their software applications (e.g. Microsoft Word), responsibility for security largely falls under Google, with the exception of content, access policies and usage falling under the customer. The responsibility of the customer begins to grow as we move to PaaS usage and then IaaS. When utilizing a platform (e.g. App Engine), Google passes the responsibility of deployment and web app security to the customer in addition to the content, access policies and usage.
Learn How Sonrai Helps You Hold Up Your End of the Deal with Google Cloud.
What is the customer’s shared responsibility?
Customers are said to be responsible for all security within the cloud. An easy guideline to live by is ‘if you can configure it, you are responsible for it.’
It is common for organizations to feel a false sense of security, assuming the CP will handle all security concerns. This is not the reality. It is the customer’s responsibility to address security concerns themselves, or seek a third party security tool to help manage this.
In sum, the customer is responsible for the data and the configuration of access controls that reside in GCP. Furthermore, they are responsible for the configuration of cloud services and granting access to users via permissions. Oftentimes, the default security settings of cloud services are often the least secure. That is why just simply correcting misconfigured GCP security settings is low-hanging fruit that organizations should prioritize.
As previously mentioned, what falls under the customer’s responsibility increases as you utilize their SaaS, PaaS and Iaas. To cover the greatest category of responsibility, IaaS, the customer is responsible for content, access policies, usage, deployment, web app security, identity, operations, access and authentication, network security, and Guest OS, data & content.
For a visual representation of this matrix, see the chart below:
Holding up your end of the deal with Sonrai
The first step is knowing what your organization will be held accountable for. Congratulations, you’re halfway there. The second is evaluating the best way to hold up your end of the GCP shared responsibility model.
Businesses today are often blind to the risks running in their cloud. The opportunities for vulnerabilities, misconfigurations and overprivileged identities leading to data breaches are countless. Consider implementing a security tool to govern your environment so your business can focus on harnessing your new-found power of the cloud.



