Table of Contents
Privilege escalation in AWS is evolving. Classic IAM issues still matter, but attackers now exploit service-based execution paths, orchestration layers, and new AI-driven services like Bedrock and Bedrock AgentCore. Sonrai Security partnered with Software Secured to exploit a number of known AWS attack vectors documented in a variety of open source capture-the-flag (CTF) style projects. By doing so in both unrestricted and Cloud Permissions Firewall-protected lab environments, we highlight both the ongoing risks associated with excessive privilege in the cloud, and also the efficacy of the Cloud Permissions Firewall in preventing these attack chain scenarios.
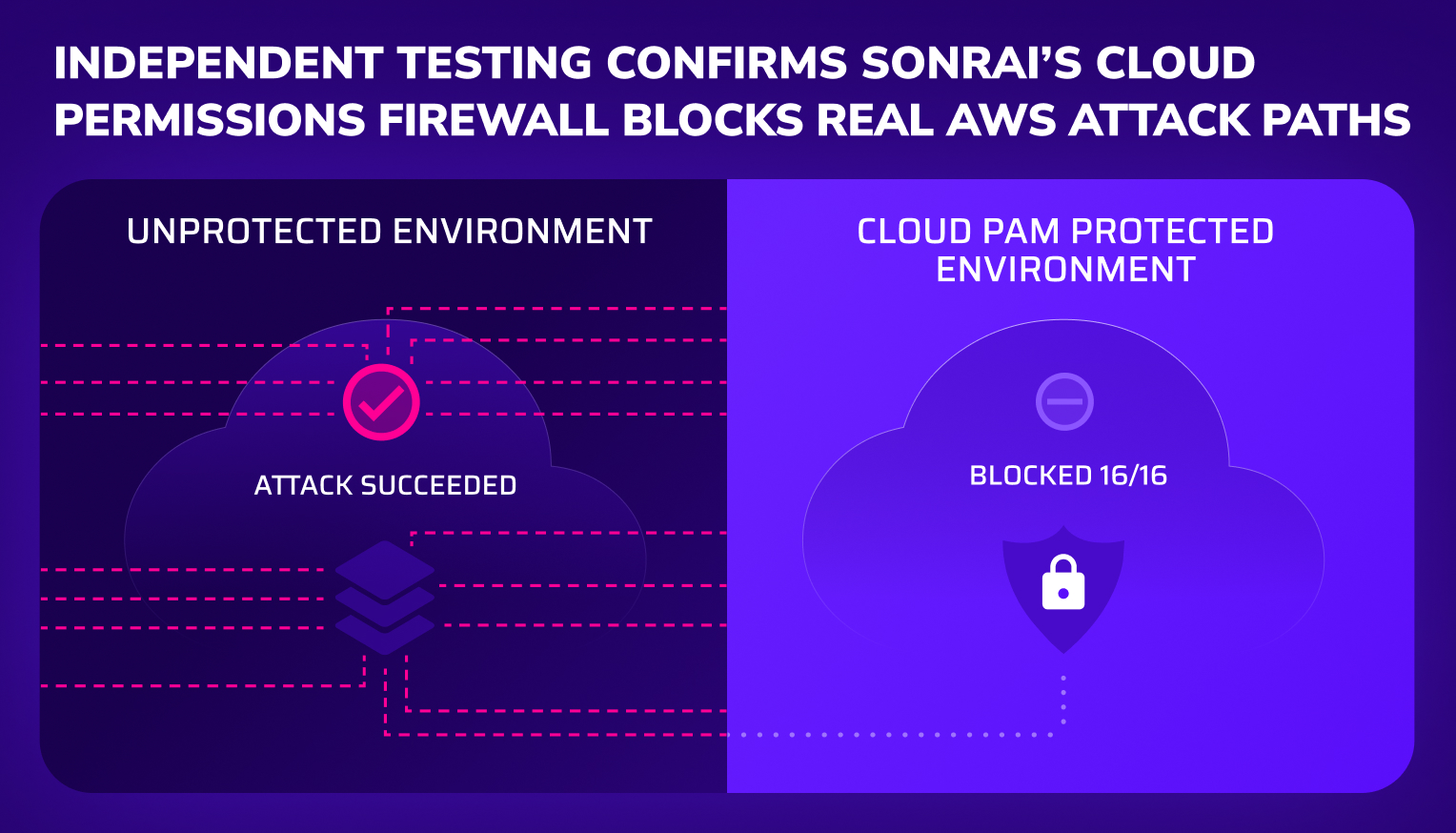
Bottom line: The Cloud Permissions Firewall blocked 16 of the 16 attack paths tested by Software Secured.
The Cloud Permissions Firewall
Sonrai Security’s Cloud Permissions Firewall was designed to enforce least-privilege at scale in the cloud, doing so in a variety of ways:
- Blocking unused services
- Disabling unused regions
- Restricting over-provisioned privileged permissions
- Quarantining zombie identities – removing all privileges from unused principals
- Removing standing privilege by implementing Just-in-Time SSO cloud access
Instead of simply reporting over-permissioning, CPF actively reduces the attack surface in a cloud environment through centralized cloud-native guardrails.
Protecting Used Services
Many of these control types are fairly intuitive; if you’re not using something in the cloud, disable it and your attack surface decreases. But what do we do about services, privileges, and identities that are in use?
Our solution is Permissions-on-Demand: just-in-time access to the privileged permissions in a given service. These are the permissions that, on their own, enable attack chain components like privilege escalation, establishing persistence mechanisms, exfiltrating data, pivoting to new systems, etc.
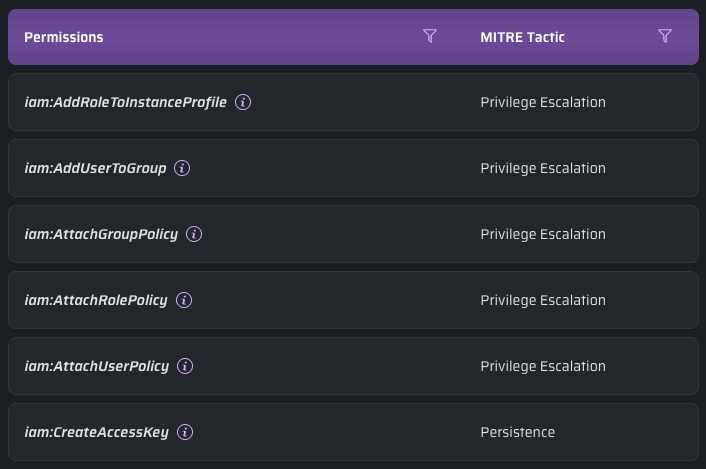
Sample list of privileged IAM permissions in the Cloud Permissions Firewall.
These controls are implemented under the hood primarily using Service Control Policies (SCPs), using research gathered by Sonrai Security to identify which permissions are risky enough to require approval.
Testing CPF Against Privilege Abuse Scenarios
When considering our approach to permissions-on-demand as a solution to the over-provisioning of privileged permissions, two questions naturally arise:
- How accurately do we classify privileged permissions?
- How effective are the firewall’s cloud-native controls in stopping actual attacks?
To answer these questions, we put the product to the test in live scenarios.
There are many available CTF platforms that catalog known attack vectors into collections of deployable scenarios. Projects like CloudGoat, CloudFoxable, and IAM Vulnerable enable security enthusiasts and professionals to play in vulnerable-by-design environments and conduct these attacks themselves in order to better understand how to prevent them.
Software Secured used their expertise to simulate attacks against a cross-section of these scenarios in controlled lab environments. For each chosen scenario, the attack was successfully conducted by a pentester in an unrestricted lab environment, then replicated in an environment with Cloud Permissions Firewall controls applied. In doing so, they were able to evaluate both the legitimacy of these scenarios, and the efficacy of the Cloud Permissions Firewall in using cloud-native controls to disrupt them.
Testing Results
The full analysis from Software Secured (including a categorization of the types of scenarios tested, the efficacy of IAM and resource policies in preventing attacks, detailed results), can be found here: Full Report
Chosen Scenarios
Software Secured selected 16 scenarios to test. These included:
- 12 Privilege Escalation & Persistence techniques found in IAM Vulnerable
- 1 EBS Secrets Exposure scenario from CloudGoat
- 1 Bastion Host Lateral Movement scenario from CloudFoxable
- 2 Proposed Bedrock/Bedrock AgentCore privilege escalation techniques CloudGoat
In the aim of transparency, it should be noted that the Bedrock and Bedrock AgentCore scenarios are based on previous research conducted by Sonrai Security. [1][2]
Results
In all 16 test cases, the tested attack scenarios were successfully exploited in the unrestricted environment. The attack chain components leveraging legitimate AWS control plane API actions the scenarios represent are still exploitable today by a bad actor with the right privileges.
In the CPF-protected environment, all 16 attacks were successfully prevented by adding protection controls to various AWS services.
Specifically, the following services were protected:
- Identity & Access Management (iam)
- Systems Manager (ssm)
- Lambda (lambda)
- Bedrock AgentCore (bedrock-agentcore)
These scenarios were prevented by requiring approval for use of the following high-risk permissions:
- iam:CreatePolicyVersion
- iam:CreateAccessKey
- iam:CreateLoginProfile
- iam:UpdateLoginProfile
- iam:AddUserToGroup
- iam:AttachGroupPolicy
- iam:AttachRolePolicy
- iam:AttachUserPolicy
- iam:PutUserPolicy
- iam:PutGroupPolicy
- iam:PutRolePolicy
- iam:UpdateAssumeRolePolicy
- ssm:StartSession
- lambda:UpdateFunctionCode
- bedrock-agentcore:CreateCodeInterpreter
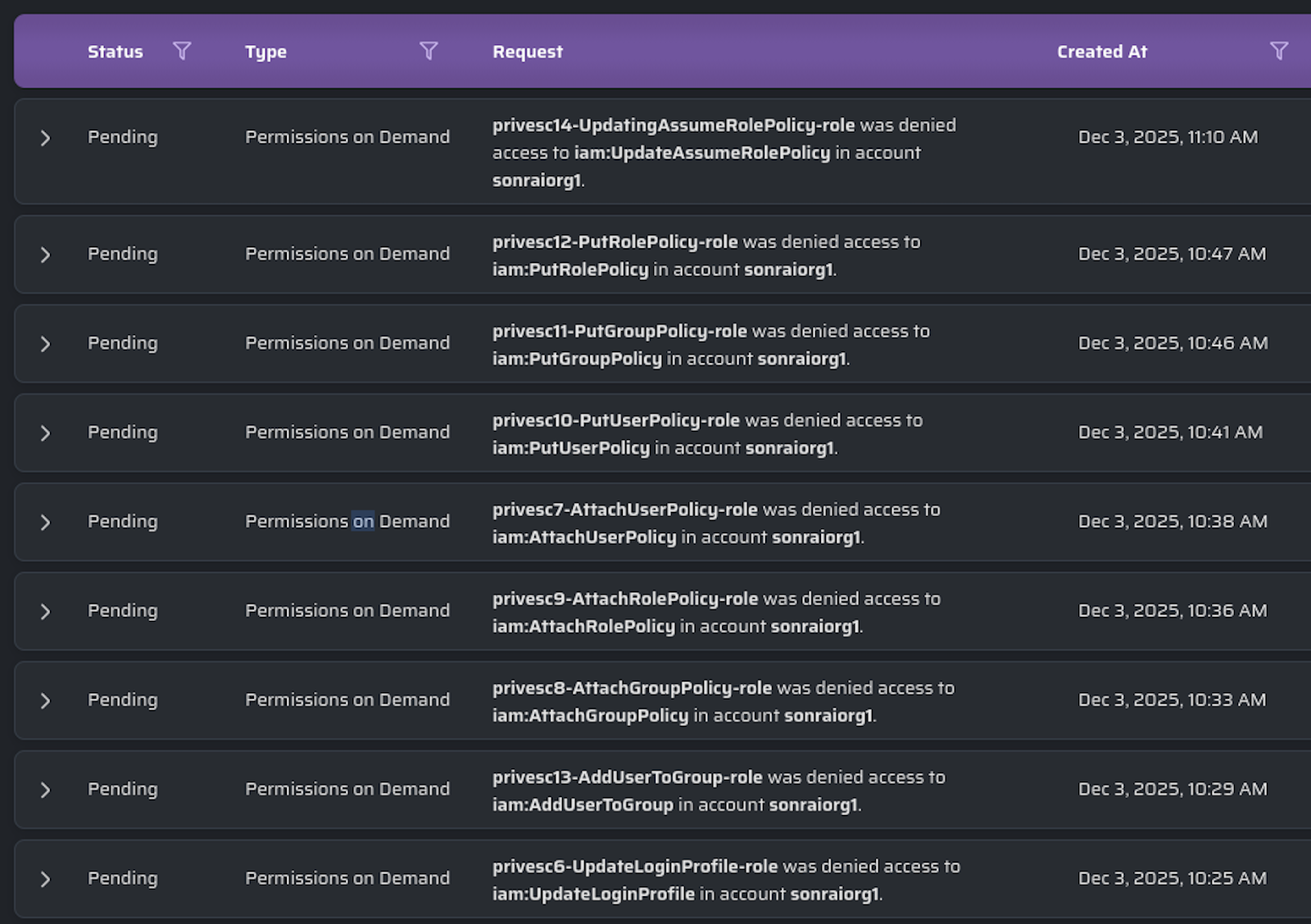
Permissions-on-Demand requests in the Cloud Permissions Firewall during testing. Requests and approvals can also be executed through Slack and Teams.
Conclusion
There are many tools that provide visibility into over privilege and the threats associated with high-risk permissions. While actionable intelligence can be extremely valuable, implementation takes time. The Cloud Permissions Firewall places real controls in place that will prevent attacks like those simulated in the tested scenarios.
But don’t take our word for it; sign up for a free trial and test CPF for yourself. Spin up a sandbox AWS environment, put some service protections in place, and give some IAM Vulnerable challenges a try yourself to see firsthand how the firewall protects you.




